In today's digital age, organizations inadvertently expose themselves to various cybersecurity threats as they expand their online operations. The landscape of cyber risks is constantly evolving, necessitating organizations to adopt a dynamic approach to safeguard their digital assets. This document delves into the crux of cyber security risk management, illuminating the roles, responsibilities, and strategies that play a pivotal role in fostering a resilient digital ecosystem. From understanding the role of Chief Information Security Officers (CISOs) to the significance of cross-departmental collaboration, executive oversight, and the steps in conducting a comprehensive risk assessment, this guide offers a holistic overview of creating a robust cybersecurity framework tailored to an organization's needs.
Table of Contents
What is Cyber Risk?
Cyber risk encompasses the potential dangers of digital activities, which could interfere with or damage an organization's operations or reputation. With the rise of digitalization, businesses are more exposed to cyber risk than ever. Factors like data breaches, cyber-attacks, and system vulnerabilities can lead to financial loss and damage to an organization's reputation.
Cybersecurity risk is the risk of harm due to information being stolen, misused, or disrupted by unauthorized digital actions. It embodies the convergence of the cyber threat landscape and the vulnerabilities of an organization's cyber infrastructure. Managing and understanding cyber security risk is pivotal in today's world, where risk constantly evolves.
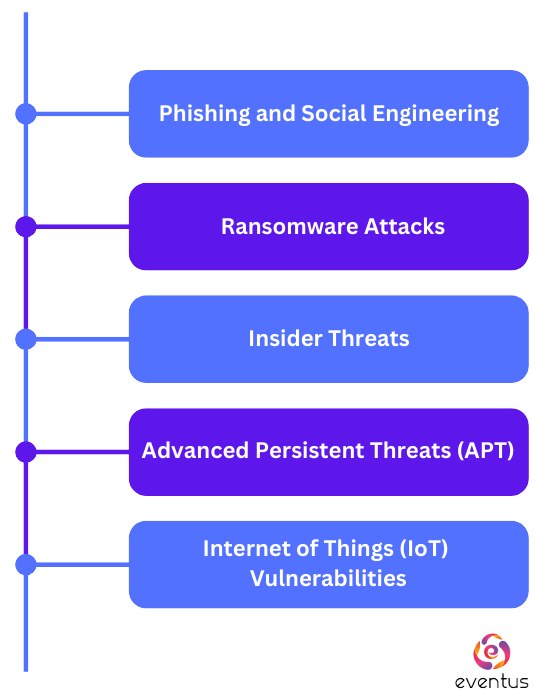
What are the types of Cybersecurity Risks?
- Phishing and Social Engineering: This involves tricking individuals into divulging sensitive information or taking specific actions. A common method is a phishing attack, where cybercriminals use deceptive emails or messages.
- Ransomware Attacks: These attacks encrypt a victim's data, demanding a ransom for decryption. They can cause significant breakdowns and lead to data loss or financial implications.
- Insider Threats: Not all threats come from the outside. Internal risk includes employees or other stakeholders who might misuse information or intentionally harm the organization.
- Advanced Persistent Threats (APT): Cybercriminals aim to steal, spy, or disrupt through these prolonged, targeted attacks. They're usually highly sophisticated and can infiltrate organizations unnoticed for extended periods.
- Internet of Things (IoT) Vulnerabilities: With the increasing connectivity of devices, the IoT presents unique challenges. Many IoT devices lack strong security measures, making them a potential entry point for attackers.
How Cyber Risks Differ from Other Business Risks?
Cyber risks are often less tangible or easily quantifiable compared to traditional business risks. Their impact can be instantaneous and widespread, and their nature is ever-evolving. Whereas most risks might be anticipated through historical data, cyber risk grows and changes as technology advances. Furthermore, a cyber incident can quickly lead to direct losses (like financial hits) and indirect consequences (like reputational harm). Therefore, a comprehensive cybersecurity risk management strategy is crucial.
What are the Key Cyber Risks and Security Threats?
Key cyber risks include:
- Phishing and Social Engineering: Cybercriminals exploit human psychology, targeting employees or the public to extract valuable data or access.
- Ransomware Attacks: The Allianz Risk Barometer reports ransomware is one of the biggest cyber risks today. It can paralyze operations and extract huge sums from businesses.
- Insider Threats: They pose a unique challenge as they come from within the organization, exploiting internal IT risk vulnerabilities.
- Advanced Persistent Threats (APT): These are sophisticated attacks that penetrate security protocols over extended periods, often state-sponsored or backed by large criminal networks.
- Internet of Things (IoT) Vulnerabilities: As the world becomes more connected, so does the risk profile of organizations. IoT devices often lack the security measures of traditional IT systems, amplifying the risks.
What is the Business Impact of Cyber Attacks?
The impact of cyber attacks on businesses is profound and multifaceted. From immediate financial hit to long-term damage to reputation, companies must recognize the risks associated with cybersecurity threats to implement effective cybersecurity risk management protocols.
Financial Repercussions
- Data breach costs: Companies may face significant expenses in managing a breach, from notifying affected parties to paying for identity protection services for victims.
- Compensation: Businesses might need to compensate affected customers or partners.
- Cyber insurance premiums: After a major incident, insurance premiums can surge, increasing operational costs.
Reputational Damage
- Loss of trust: Customers might lose faith in a company after a cybersecurity incident, affecting loyalty and sales.
- Damage to the reputation: This can deter potential partners or investors, impacting growth prospects.
- Companies must often invest in PR campaigns to restore public trust.
Operational Disruptions
- Disruption or damage: A cyber attack can halt business operations, from shutting down online platforms to stopping production lines.
- Ransomware attacks can lock out essential data, causing operational standstills until victims pay ransom or restore systems.
- Resource redirection: Employees might be pulled from their regular tasks to deal with the aftermath of a cyber breach, affecting productivity.
Legal and Compliance Implications
- Fines and penalties: Regulatory bodies can levy substantial fines on companies failing to protect customer data adequately.
- Legal fees: Litigation costs can mount if customers or partners take legal action.
- Compliance overhaul: Companies may need to invest in new systems or processes to meet updated regulatory requirements.
What is the Cost of a Cyberattack?
Understanding the cost of a cyberattack is essential for risk assessment and risk management. While the immediate financial repercussions are evident, hidden costs can persist for years.
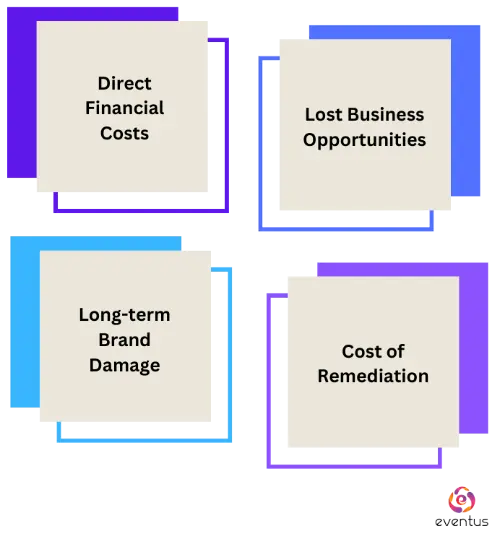
Direct Financial Costs
- Understanding the cost of a cyberattack is essential for risk assessment and risk management. While the immediate financial repercussions are evident, hidden costs can persist for years.
- Extortion fees: If faced with ransomware or other cyber extortion, companies might pay to regain access to their systems.
Lost Business Opportunities
- Downtime: Outages can mean missed sales or opportunities.
- Damaged partnerships: Trust is hard to rebuild, and some partners might choose to sever ties after a significant breach.
Long-term Brand Damage
- Decreased market value: A high-profile cyber event might tie an organization's reputation to its stock value, which could cause its stock value to suffer.
- Lost customer trust: It takes time and effort to rebuild trust; some customers might never return.
Cost of Remediation
- System overhaul: Post-incident, companies might need to invest in entirely new systems to prevent future breaches.
- Training and cyber hygiene practices: Ensuring that employees are well-informed is crucial to prevent future incidents.
- Continuous risk monitoring: Organizations must continually monitor their cyber risk exposure to anticipate and prevent future attacks.
Why Do Businesses Need to Plan for Cybersecurity Risks?
In today's digital age, businesses must prioritize planning for cyber risks. As threats become increasingly sophisticated, reactive measures are insufficient. Organizations need to adopt a proactive stance to ensure sustained business operations, protect customer data, and maintain their reputation.
The Changing Cyber Landscape
- Endlessly adapting threats: Cyber criminals devise new methods to exploit security gaps with each technological advancement.
- Emerging risks: As the IoT becomes more integrated into business processes, new threat vectors arise, increasing cyber risk exposure.
- External and internal cyber risks: Whether it is internal or external cyber risk, both are extremely harmful.
The Cost of Inaction
- Financial loss: A significant cyber breach can have substantial immediate and long-term financial implications.
- Reputational damage: A cyber event can irreparably harm an organization's reputation, resulting in lost business and trust.
- Operational disruptions: Data breaches or ransomware attacks can halt operations, causing loss of revenue and customer trust.
Benefits of Proactive Cybersecurity Planning
- Risk reduction: By identifying and addressing vulnerabilities, businesses can substantially reduce the likelihood of a successful cyber attack.
- Financial savings: By preventing data breaches and other incidents, companies can avoid the associated costs.
- Enhanced trust: Customers and partners have more confidence in organizations that prioritize cybersecurity, leading to stronger business relationships.
What are the Best Practices for Cyber Risk Management?
- Comprehensive Risk Assessments: Conduct thorough risk assessments regularly to identify vulnerabilities and threats. This process should involve evaluating internal and external factors that could impact cybersecurity.
- Robust Cybersecurity Frameworks: Implement and tailor recognized cybersecurity frameworks like NIST or ISO 27001. These frameworks provide structured approaches to managing and mitigating cyber risks.
- Employee Training and Awareness: Regularly train employees on cybersecurity best practices and emerging threats. A well-informed workforce is critical in preventing security breaches.
- Advanced Security Technologies: Invest in advanced technologies such as AI and machine learning for proactive threat detection and response. These tools can significantly improve your organization’s ability to anticipate and mitigate cyber-attacks.
- Integrating a Security Operations Center (SOC): This process is crucial for continuous monitoring and management of cybersecurity risks. SOCs provide specialized surveillance and rapid response capabilities to address potential cyber threats effectively.
- Incident Response and Recovery Plans: Develop comprehensive incident response and recovery plans. These plans should include clear procedures for addressing security breaches and minimizing their impact.
- Regular Policy Updates and Compliance Checks: Ensure cybersecurity policies are updated regularly to reflect new threats and tech changes. Regular compliance checks are essential for maintaining the effectiveness of these policies.
- Data Encryption and Backup Strategies: Implement strong encryption for sensitive data and establish robust data backup strategies. This approach is essential for maintaining the security and accessibility of data in the event of a cybersecurity incident.
Is Your Business Prepared for the New Cybersecurity Risks?
To determine if your business is prepared for new cybersecurity risks, assess current preparedness against the rise of new cyber threat vectors and ensure you have an adaptive cybersecurity strategy in place to respond effectively.
The Rise of New Cyber Threat Vectors
- Novel threats: Cyber criminals are devising advanced techniques to breach defences with the growing integration of AI and other technologies.
- External risks: As businesses expand their digital footprint, they become exposed to a broader range of threats.
Assessing Your Current Preparedness
- Digital Threat Evaluation: Regularly evaluate the organization's defenses against the risk landscape.
- Identify gaps: Understand areas where the current cybersecurity program might be lacking and prioritize them for improvement.
Implementing an Adaptive Cybersecurity Strategy
- Evolve with the landscape: As the cyber realm is ever evolving, so should the organization's approach to security.
- Collaborate: Engage with industry peers, regulatory bodies, and cybersecurity experts to stay abreast of best practices and emerging threats.
How Eventus Helps with Cyber Risk Identification, Prioritization, and Remediation
In addressing cyber risk, Eventus stands as a pivotal ally, offering expertise in Cyber Risk Identification, Prioritization, and Remediation. Their approach involves advanced analytics to detect and evaluate potential cyber threats, followed by a strategic prioritization process to focus on the most critical risks. Eventus tailors its remediation solutions to address prioritized cyber risks effectively, employing state-of-the-art technologies and best practices to strengthen cyber defenses. Their integrated services provide a comprehensive shield against evolving cyber threats, ensuring robust protection for their clients' digital assets.