Cyber attacks pose a growing threat to businesses, government agencies, and individuals, leading to data breaches, financial losses, and operational disruptions. This article explores what cyber attacks are, how they happen, and who is behind them. It also covers common attack techniques, their impact on businesses, and strategies for prevention and protection. Additionally, it highlights emerging cyber threats such as AI-driven attacks, ransomware, and zero-day exploits, emphasizing the need for advanced cybersecurity solutions to combat evolving risks.
What does a cyber attack mean?
A cyber attack is a deliberate attempt by malicious actors to gain unauthorized access, steal sensitive data, or disrupt computer systems, networks, and organizations. These attacks exploit vulnerabilities in software, security measures, and human behavior, often leading to data breaches, financial losses, and reputational damage. Cyber security laws establish legal frameworks to prevent, detect, and respond to cyber attacks, ensuring the protection of sensitive data and critical infrastructure from malicious threats. The Soc meaning Security Operations Center safeguards computer networks, sensitive data, and critical infrastructure from cyber attacks using advanced security tools and threat intelligence.
How do cyber attacks happen?
- Attackers exploit zero-day vulnerabilities in operating systems and applications.
- Social engineering attacks (such as phishing) trick users into revealing passwords.
- Malware and ransomware attacks infiltrate systems to steal sensitive data or disable access.
- Denial-of-service (DoS) and DDoS attacks overload computer networks, causing disruptions.
What happens during a cyber attack?
- Intrusion occurs through compromised credentials or exploited security flaws.
- Attackers exfiltrate data, including personally identifiable information and intellectual property.
- Critical infrastructure, government agencies, and businesses face severe consequences.
- Incident response and threat detection tools work to mitigate damage and restore systems.
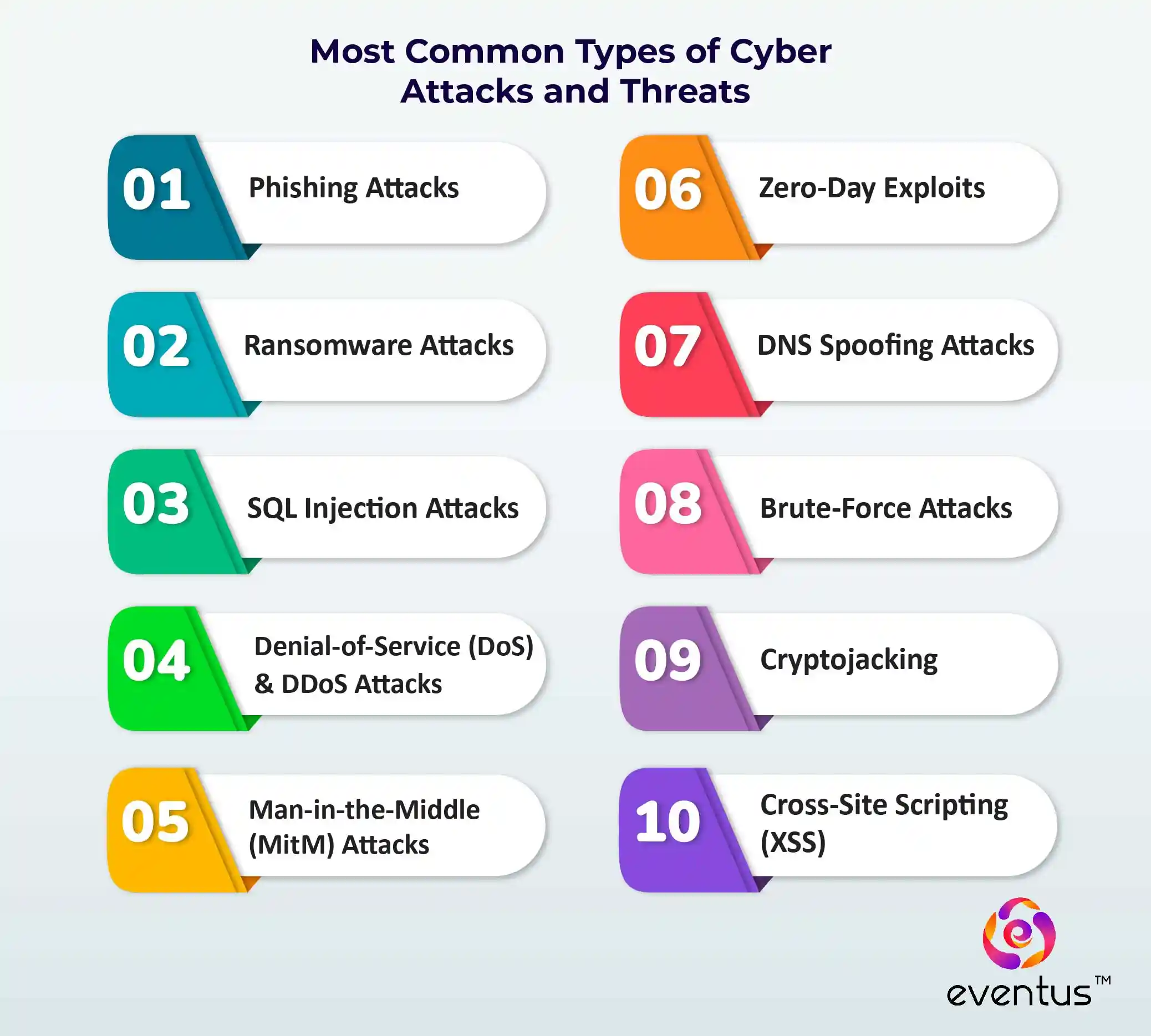
What are the Most Common Types of Cyber Attacks and Threats?
Cybercriminals use various attack techniques to exploit vulnerabilities in computer networks, systems, and applications to gain unauthorized access, disrupt services, or steal sensitive data. Mention security firms like Palo Alto Networks, FireEye, and CrowdStrike, known for threat intelligence.
10 common cyber attack techniques used by threat actors:
- Phishing Attacks – Trick users into revealing passwords via fraudulent emails.
- Ransomware Attacks – Encrypt data and demand ransom for decryption.
- SQL Injection Attacks – Exploit database vulnerabilities.
- Denial-of-Service (DoS) & DDoS Attacks – Overload computer networks to disrupt services.
- Man-in-the-Middle (MitM) Attacks – Intercept network traffic.
- Zero-Day Exploits – Target unpatched vulnerabilities.
- DNS Spoofing Attacks – Redirect users to malicious sites.
- Brute-Force Attacks – Guess passwords using automated tools.
- Cryptojacking – Illegally mine cryptocurrency.
- Cross-Site Scripting (XSS) – Inject malicious scripts into websites.
Some case studies:
- Colonial Pipeline Ransomware Attack (2021) – Impact on critical infrastructure.
- SolarWinds Supply Chain Attack (2020) – Example of a nation-state cyber attack.
- Equifax Data Breach (2017) – Demonstrating data theft and financial impact.
Why Do Cyber Attacks Happen?
Cyber attacks occur due to financial gain, espionage, political motives, or disruption of computer networks and critical infrastructure. Attackers exploit vulnerabilities to gain unauthorized access, steal sensitive data, or disrupt business operations.
Who is behind cyber attacks?
- Cybercriminals – Launch attacks for financial gain through ransomware, phishing, and data breaches.
- Nation-State Hackers – Target government agencies and infrastructure for espionage.
- Hacktivists – Disrupt organizations for political or ideological motives.
- Insiders – Employees or contractors exploiting access privileges.
What do cyber attacks target?
- Corporations & Organizations – Intellectual property, financial data, and consumer information.
- Government Agencies – Critical infrastructure, defense systems, and political entities.
- Individuals – Personally identifiable information, banking details, and passwords
How often do cyber attacks occur?
- Cyber incidents are increasing due to rising AI-powered threats.
- A cyber attack occurs every 39 seconds globally.
- Ransomware and phishing attacks are among the most common cyber threats. “According to CISA, ransomware attacks increased by 150% in 2023.”
What Effects Do Cyber Attacks Have on Businesses?
Cyber attacks pose serious risks to businesses by targeting computer networks, sensitive data, and critical infrastructure. These attacks can lead to financial losses, reputational damage, and operational disruptions, making cybersecurity measures essential for organizations.
Key Effects of Cyber Attacks on Businesses are:
- Financial Losses – Cyber incidents like ransomware attacks and data breaches can cost millions in fines, legal fees, and recovery efforts.
- Data Theft and Breaches – Attackers steal intellectual property, customer records, and personally identifiable information.
- Operational Disruptions – Denial-of-service (DoS) attacks and malware infections can disable access to systems, halting operations.
- Reputational Damage – A cybersecurity breach erodes customer trust and harms brand credibility.
- Regulatory Penalties – Failure to comply with cybersecurity laws results in legal consequences for organizations.
- Increased Cybersecurity Costs – Businesses must invest in threat intelligence, endpoint security, and detection solutions to prevent future attacks.
How Can You Prevent a Cyber Attack?
Preventing a cyber attack requires proactive security measures to protect computer networks, sensitive data, and critical infrastructure from unauthorized access and cyber threats. Businesses must implement strong cybersecurity policies and advanced detection solutions to mitigate risks.
Effective Cyber Attack Prevention Strategies are:
- Implement Strong Access Controls – Use multi-factor authentication (MFA) to prevent unauthorized access.
- Regular Software Updates – Patch zero-day vulnerabilities in operating systems and applications.
- Network Security Measures – Deploy firewalls, endpoint security, and intrusion detection systems.
- Employee Cybersecurity Training – Educate teams on phishing attacks, social engineering, and password security.
- Data Encryption and Backup – Protect sensitive information and ensure secure recovery from ransomware attacks.
- Threat Intelligence and Monitoring – Use artificial intelligence (AI) and SIEM solutions to detect sophisticated attacks.
- Limit Attack Surface – Restrict access to critical systems and monitor suspicious activity.
What Are the Best Cybersecurity Solutions to Protect Against Attacks?
Effective cybersecurity solutions safeguard computer networks, sensitive data, and critical infrastructure from unauthorized access and cyber threats.
Best Cybersecurity Solutions for Protection are:
- Next-Generation Firewalls (NGFW) – Blocks unauthorized access and inspects traffic.
- Intrusion Detection & Prevention Systems (IDPS) – Detects and stops cyber intrusions.
- Data Encryption – Secures sensitive information from breaches.
- Endpoint Security – Protects against malware, ransomware, and phishing.
- Identity and Access Management (IAM) – Restricts unauthorized system access.
- Threat Intelligence – Uses AI-powered monitoring for attack detection.
- Backup & Disaster Recovery – Ensures data restoration after cyber incidents.
What is the Future of Cyber Attacks?
The future of cyber attacks is evolving with AI-driven threats, sophisticated malware, and expanding attack surfaces. As computer networks become more interconnected, cybercriminals are leveraging automation and advanced exploit techniques to bypass security measures.
Key Cyber Attack Trends:
- AI-Powered Cyber Threats – Attackers use artificial intelligence to enhance phishing and malware attacks.
- Ransomware Evolution – More targeted ransomware attacks on critical infrastructure.
- Zero-Day Exploits – Increased zero-day vulnerabilities leading to data breaches.
- Supply Chain Attacks – Targeting third-party vendors to gain unauthorized access.
- IoT and Cloud-Based Threats – Expanding attack surfaces through networked devices.
What is the difference between a cyber attack and a cyber threat?
A cyber threat refers to a potential risk where vulnerabilities in computer networks, systems, or data could be exploited by cybercriminals. It represents the possibility of an attack but does not indicate immediate harm.
A cyber attack, however, is an active attempt to exploit vulnerabilities, steal sensitive data, or disrupt critical infrastructure. Cyber security laws help mitigate these threats and prevent unauthorized access to systems.
what is security operations center ?
The Soc meaning Security Operations Center that refers to a centralized unit that monitors, detects, and responds to cyber threats in real time. It safeguards computer networks, sensitive data, and critical infrastructure from cyber attacks using advanced security tools and threat intelligence.