Cybersecurity is no longer just a battle between attackers and defenders—it requires a collaborative approach. This article explores the role of the purple team, how purple teaming improves security operations, and compares red, blue, and purple team responsibilities in detail.
Table of Contents
What is purple teaming and how can it strengthen your cybersecurity?
Purple teaming is a collaborative cybersecurity approach that combines the offensive strategies of red teams with the defensive expertise of blue teams to strengthen an organization’s security posture.
A report by Cybersecurity Ventures estimates that global cybercrime costs will reach $10.6 trillion annually by 2025, underlining the urgency for businesses to adopt collaborative security approaches like red, blue, and purple teaming. The purpose of the Purple Team is to improve an organization's security by fostering real-time collaboration between red and blue teams.
- It enhances security testing by conducting penetration tests, simulating cyber threats, and refining security controls through team exercises.
- Incident response and threat mitigation improve as teams identify vulnerabilities, exploit attack scenarios, and develop effective security measures.
- Security operations become more proactive, allowing organizations to continuously assess, refine, and implement better security practices.
- Organizations that adopt purple teaming benefit from faster threat detection, stronger defenses, and improved overall security resilience.
- By fostering red and blue team collaboration, purple teaming enables security teams to stay ahead of cyber threats and optimize security frameworks. A 2022 SANS Institute survey found that organizations using purple teaming reduced security gaps by 40% compared to those relying solely on red and blue teams.
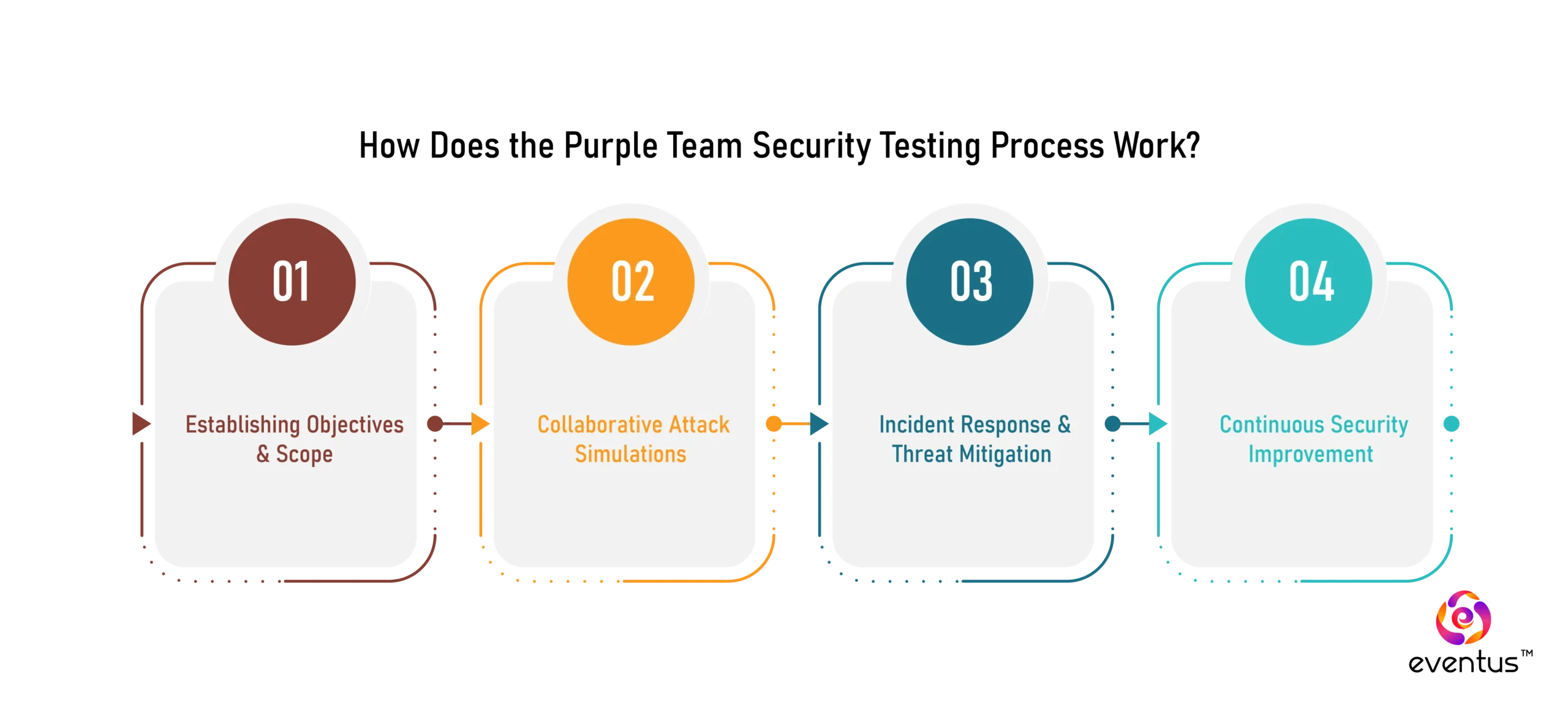
How Does the Purple Team Security Testing Process Work?
The purple team combines the skills of both, facilitating real-time feedback and strategic improvement of security measures.
1. Establishing Objectives and Scope
The purple team exercises begin with defining team functions and security objectives:
- Understanding security vulnerabilities: The team identifies potential weaknesses in the organization’s infrastructure. Unauthorized access attempts dropped by 80% in a hospital network reducing the risk of data breaches.
- Defining test parameters: The scope includes penetration testing, simulated cyberattacks, and incident response exercises.
- Aligning security strategy: Red team activities (offensive security tactics) and blue team members (defensive security specialists) align their approaches to maximize security effectiveness.
2. Collaborative Attack Simulations
In this phase, the red and blue team collaboration is tested through simulated cyberattacks:
- Red team exploits vulnerabilities: Using offensive security techniques, they attempt to penetrate defenses and uncover weaknesses in security systems.
- Blue team defends and responds: The security incident response team actively counters attacks, detecting and mitigating threats.
- Immediate feedback loop: Unlike traditional methods, the purple team is a group that brings together both offensive and defensive teams to evaluate effectiveness in real time.
3. Incident Response and Threat Mitigation
- Security operations are assessed based on real-time incidents to evaluate the effectiveness of security controls.
- The blue team’s defensive strategies are refined based on the red team’s offensive insights.
- Security measures such as firewall rules, access control policies, and detection capabilities are improved for better security.
4. Continuous Security Improvement
- Purple teaming offers an iterative approach where security professionals refine their defenses continuously.
- The process involves updating cybersecurity frameworks, improving security capabilities, and implementing best security practices.
- Security personnel apply purple teaming defined methodologies to strengthen the organization's overall security posture. Amazon Web Services (AWS) uses purple teaming to enhance identity and access management (IAM) security, reducing cloud misconfigurations that could lead to data leaks.
How to Overcome Barriers to Effective Purple Team Exercises
- Clearly define and communicate Purple Team functions to distinguish them from Red and Blue Team responsibilities.
- Encourage Red and Blue Team collaboration to share insights, security incidents, and threat intelligence.
- Invest in Purple Team expertise through ongoing cybersecurity training and offensive security certifications.
- Conduct structured Purple Team exercises, including penetration testing and vulnerability assessments, to improve security posture.
- Develop streamlined communication and reporting processes to ensure security vulnerabilities are promptly addressed.
- Implement advanced security tools for threat simulations, incident response, and security operations.
- Secure leadership support to obtain necessary funding for Purple Teaming initiatives.
- Continuously monitor emerging cyber threats and adapt security frameworks to enhance cyber defenses. Tech giants like Microsoft and Google integrate purple teaming into their Zero Trust security frameworks to validate identity access controls and prevent lateral movement in networks.
What are the differences between Red Team, Blue team and Purple Team?
Each team plays a unique role in cybersecurity frameworks
| Aspect | Red Team | Blue Team | Purple Team |
| Purpose | Simulates real-world cyberattacks to identify weaknesses. | Defends against cyberattacks by detecting and mitigating threats. | Bridges the gap between red and blue teams to improve security collaboration. |
| Primary Role | Ethical hackers who test security by attacking systems. | Cybersecurity defenders who monitor and respond to threats. | Security experts who ensure red and blue teams work together effectively. |
| Tactics | Uses ethical hacking, penetration testing, and social engineering to find vulnerabilities. | Uses threat monitoring, detection, and incident response to strengthen security. | Combines red team offensive tactics with blue team defensive strategies. |
| Approach | Adversarial – focuses on identifying and exploiting security gaps. | Defensive – strengthens security by preventing and mitigating attacks. | Cooperative – ensures continuous improvement through teamwork. |
| Collaboration | Works separately from the blue team and does not typically share findings in real time. | Works separately from the red team, reacting to their simulated attacks. | Actively collaborates with both teams to enhance overall security. |
| Security Improvement | Finds vulnerabilities but does not fix them. | Identifies and mitigates threats but may not anticipate all attack methods. | Improves security posture by integrating red team attack insights with blue team defenses. |
| Team Responsibilities | Simulates cyberattacks, tests security resilience, and uncovers weaknesses. | Monitors systems, analyzes threats, and enhances security defenses. | Conducts joint security exercises, enhances team collaboration, and implements proactive security fixes. |