Eventus Security’s intelligent Managed SOC services and how its AI-driven SOCaaS improves security outcomes. It outlines the Eventus Platform’s visibility and analytics, integrated threat intelligence and proactive hunting, and automation with SOAR to reduce MTTD/MTTR.
Table of Contents
It contrasts intelligent services with conventional SOCs, details global follow-the-sun coverage, and shows how the platform unifies endpoint, network, and cloud telemetry. It also summarizes compliance and secure architecture practices, enterprise cyber resilience measures, and the reasons global enterprises select Eventus for managed SOC services.
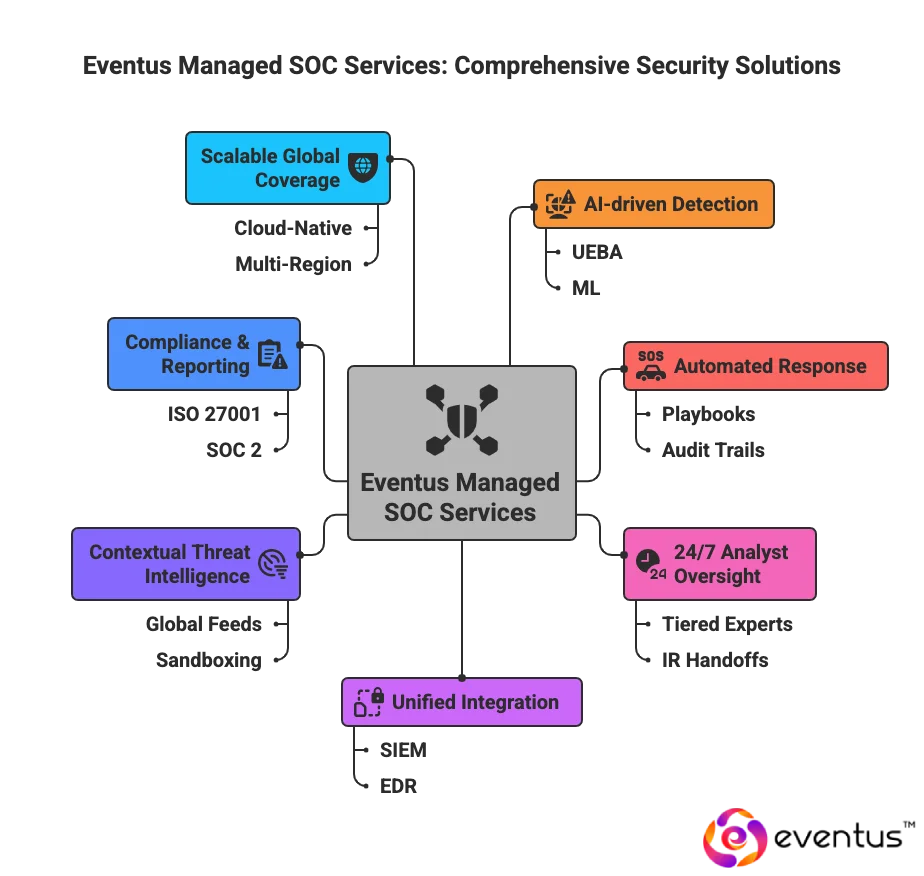
How Eventus Delivers Intelligent Managed SOC Services for Global Enterprises
Here’s how:
- AI-driven detection: UEBA and ML baseline behavior across endpoints, networks, identities, and cloud environments to detect lateral movement, insider threats, and zero-day patterns within seconds. This advanced capability positions Eventus among the best SOC as a service provider globally.
- Automated response (SOAR): Playbooks quarantine hosts, revoke tokens, and block IOCs, cutting MTTD/MTTR from hours to minutes with full audit trails.
- 24/7 analyst oversight: Tiered SOC experts validate alerts, run hunts, and manage complex investigations with clear IR handoffs.
- Unified integration: Connectors for SIEM, EDR, CSPM, IAM, and ITSM normalize telemetry for a single incident view.
- Contextual threat intelligence: Correlates global feeds and sandboxing with asset criticality to prioritize highest-impact risks.
- Compliance & reporting: Evidence automation and control mapping for ISO 27001, SOC 2, HIPAA, PCI DSS, GDPR; auditor-ready reports.
- Scalable global coverage: Cloud-native pipeline supports multi-region, hybrid environments and peak loads without degradation.
How Do Intelligent SOC Services Differ From Conventional Security Operations Centers?
| Aspect | Conventional Security Operations Centers (SOCs) | Intelligent SOC Services by Eventus Security |
| Approach | Primarily reactive; responds to alerts after detection. | Proactive model that predicts and prevents advanced threats using continuous monitoring and AI analytics. |
| Technology Base | Relies on rule-based systems and manual processes. | Built on an AI-driven security operations platform with automation, XDR, and threat intelligence integration. |
| Threat Detection and Response | Limited to predefined indicators and static correlation rules. | Uses AI, machine learning, and advanced threat intelligence for real-time threat detection and response. |
| Incident Management | Manual investigation and delayed response cycles. | Automated playbooks and SOAR workflows reduce MTTD/MTTR, enabling rapid incident response. |
| Scalability | Requires extensive infrastructure and large in-house teams. | Delivered as SOC as a Service (SOCaaS) — scalable, cloud-native, and managed by the global Eventus SOC team. |
| Intelligence Integration | Minimal external threat intelligence or behavioral analytics. | Merges cyber threat intelligence, red team insights, and proactive threat hunting for comprehensive coverage. |
| Incident Readiness | Focuses on post-incident recovery. | Embeds incident readiness and response aligned with industry best practices to reduce downtime and impact. |
| Automation | Manual triage and repetitive workflows dominate operations. | Automates security workflows through SOAR, allowing analysts to focus on strategic investigations. |
| Human + AI Collaboration | Heavily human-dependent, often overburdened by alert volume. | Balanced human–AI collaboration, combining automation with the Eventus team’s extensive experience for precise action. |
| Adaptability | Static configurations, slow to update against new threats. | Continuously evolves with the evolving threat landscape, ensuring next-gen security and cyber resilience. |
| Outcome | Limited visibility, slower detection, and higher operational cost. | Enhanced security posture, measurable cyber resilience, and real-time defense against evolving cyber threats. |
This elevated capability is why Eventus is often compared with the best SOC provider companies worldwide.
How Does Eventus Deliver Global Managed SOC Coverage?
Here’s how:
- Follow-the-sun SOCaaS: Eventus Security’s global model provides 24/7 monitoring to detect and respond to security incidents across time zones.
- Regional SOC hubs: SOC hubs across Asia, Middle East, and other regions ensure:
- Localized compliance
- Lower latency
- Faster response
- Managed XDR visibility: Eventus aggregates and correlates:
- Endpoint data
- Cloud logs
- Network telemetry
- IAM signals
This forms a unified threat intelligence layer.
- Automation at scale: Orchestrated workflows and security tools accelerate triage and containment, minimizing dwell time against security threats.
- Intelligence-led defense: Eventus Red and Eventus TechSol feed proactive risk management, IOC sweeps, and threat hunting.
- Expert coverage: The Eventus team augments enterprises with mature cybersecurity services, incident readiness, soc as a service providers and end to end managed soc solutions.
- Outcome: Globally consistent cyber resilience services from a leader in managed security services, aligned to evolving cybersecurity needs.
How Does the Eventus Platform Unify Visibility Across Endpoints, Networks, and Clouds?
Here’s how:
- Unified Security Architecture: Consolidates telemetry across:
- Endpoints
- Networks
- Cloud workloads
- SaaS applications
- Centralized Data Correlation: It aggregates events and logs from distributed systems into a unified security strategy, allowing analysts to trace threat paths across multiple layers of the enterprise infrastructure.
- AI-Powered Correlation Engine: Through Eventus SOCaaS, AI models analyze vast data streams in real time, detecting patterns that indicate emerging or hidden threats across hybrid environments.
- Dynamic Dashboards: Unified dashboards show:
- Active threats
- MITRE ATT&CK mapping
- Exposure metrics
- Incident readiness status
- Integrated Threat Hunting: Features like threat hunting allow analysts to proactively search for adversarial behavior across endpoints and cloud workloads, strengthening resilience against cyber threats.
- Security Automation: Automated enrichment, prioritization, and workflow orchestration streamline detection, ensuring that the Eventus team can deliver cutting-edge cybersecurity services with greater accuracy and speed.
- Scalable Cloud Integration: The architecture scales seamlessly across public and private clouds, meeting enterprise security needs without compromising visibility or performance.
- Leadership and Innovation: Under the direction of the CTO of Eventus Security, a 24/7 managed soc services platform continuously evolves through applied AI, analytics, and security awareness initiatives to enhance cyber resilience services globally.
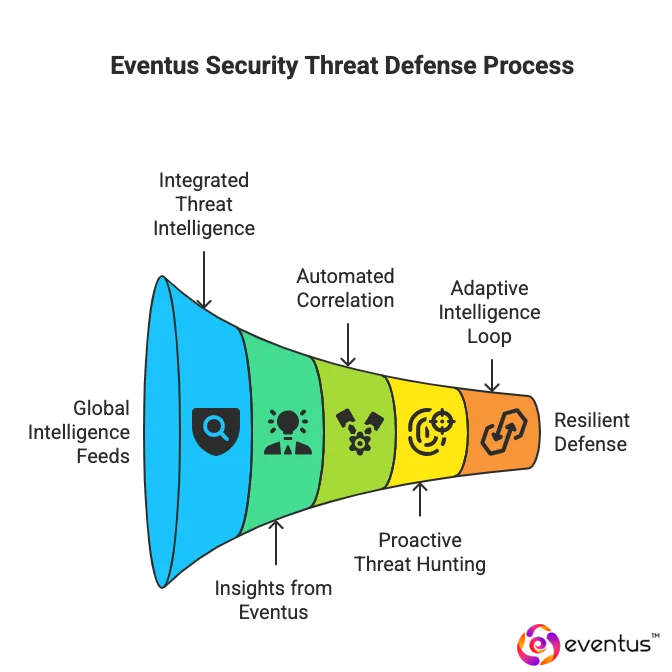
How Does Eventus Use Threat Intelligence and Threat Hunting?
Here’s how:
- Integrated Threat Intelligence: Eventus Security combines multiple global intelligence feeds with in-house research to continuously map evolving threat patterns and attack infrastructures.
- Insights from Eventus: Real-time intelligence derived from ongoing investigations enables precise correlation of indicators, enhancing detection accuracy and accelerating response.
- Automated Correlation: The platform integrates curated threat data into its analytics engine, allowing automated enrichment of alerts and faster identification of high-risk activities.
- Proactive Threat Hunting: Expert analysts conduct hypothesis-driven investigations to uncover undetected intrusions, insider threats, and lateral movements before impact.
- Adaptive Intelligence Loop: Each hunt feeds new findings back into the intelligence ecosystem, strengthening Eventus’s managed services and security strategy over time.
- Advanced Tooling: The hunting framework leverages behavioral analytics, machine learning, and signature-based indicators to detect sophisticated attacker behaviors.
- Enterprise Value: Through unified intelligence and continuous hunting, Eventus Security has rapidly built a reputation for delivering precise, predictive, and resilient defense across client ecosystems.
How Does Eventus Automate and Orchestrate Incident Response?
Here’s how:
- AI-Driven Automation: The Eventus Platform leverages ai driven soc as a service and machine learning to automate repetitive security actions such as alert triage, correlation, and prioritization—reducing analyst fatigue and accelerating detection.
- SOAR Playbooks: Built-in Security Orchestration, Automation, and Response (SOAR) playbooks standardize workflows for containment, eradication, and recovery, ensuring consistent and error-free incident handling.
- Real-Time Orchestration: Eventus integrates diverse security tools—SIEM, XDR, endpoint, and network defense—within a unified orchestration layer to coordinate real-time incident response across environments.
- Contextual Enrichment: Automation engines gather contextual data from threat feeds, user behavior, and asset inventories to enhance decision accuracy and prioritize high-impact security incidents.
- Human-in-the-Loop Efficiency: While automation handles routine events, complex cases are escalated to Eventus analysts, who oversee strategic actions and validate responses.
- Reduced Response Time: Streamlined automation minimizes Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR), ensuring faster containment of breaches and advanced attacks.
- Continuous Optimization: Eventus continually refines orchestration workflows based on post-incident analytics, enhancing resilience and maintaining alignment with evolving cyber threats.
How Does Eventus Ensure Compliance and Secure Architecture?
Here’s how:
- Aligned frameworks: Architecture mapped to HIPAA, PCI DSS, ISO 27001, and GDPR for verifiable compliance.
- Tenant isolation: Segregated, per-customer environments on the Eventus Platform to protect data privacy and integrity.
- Encryption everywhere: Strong cryptography for data in transit and at rest, with managed key controls.
- Least privilege: RBAC, MFA, and continuous audit logs to govern access and prove accountability.
- Automated evidence: Continuous control monitoring with auto-generated reports for audits and governance.
- Zero-Trust controls: Authenticate and authorize every user/device; restrict lateral movement.
- Hardened by design: Secure configurations and continuous posture checks across network, app, and data layers.
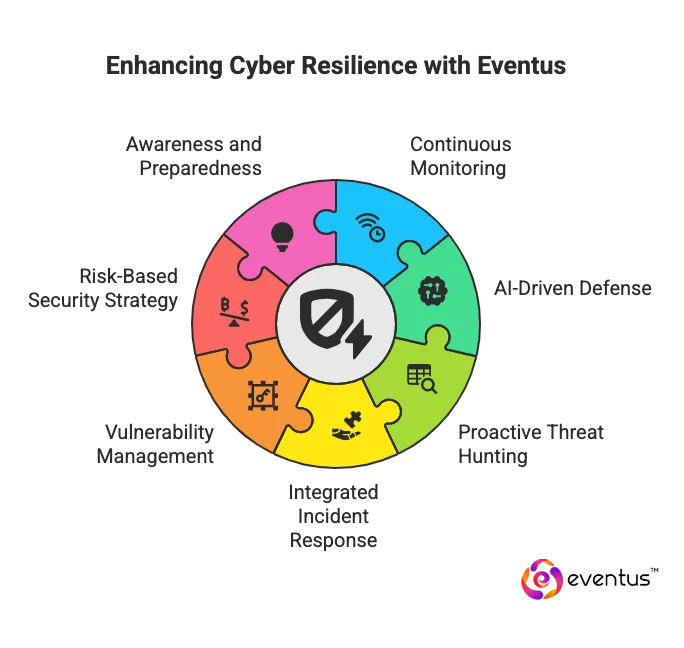
How Does Eventus Strengthen Enterprise Cyber Resilience?
Here’s how:
- Continuous Monitoring: Eventus Security provides 24/7 threat detection and response through its global SOC infrastructure, ensuring early identification and containment of potential risks.
- AI-Driven Defense: Advanced analytics and automation within the Eventus Platform strengthen defense mechanisms, reducing exposure to evolving cyber threats.
- Proactive Threat Hunting: Dedicated analysts conduct continuous hunts for stealth attacks, enhancing resilience and maintaining enterprise operational stability.
- Integrated Incident Response: Unified workflows streamline containment, eradication, and recovery, minimizing downtime after a breach or disruption.
- Vulnerability Management: Automated scanning and prioritization address exploitable weaknesses before adversaries can exploit them.
- Risk-Based Security Strategy: Eventus aligns cyber resilience services with business impact assessments, ensuring that critical assets receive top defense priority.
- Awareness and Preparedness: Ongoing security awareness and simulation exercises empower internal teams to react swiftly under real attack conditions.
- Outcome: Through automation, intelligence, and human expertise, Eventus Security reinforces enterprise resilience against modern cyber threats while ensuring continuity and long-term protection.
Why Do Global Enterprises Choose Eventus for Managed SOC Services?
Here’s why:
- AI-driven platform: The proprietary Eventus Platform—powered by managed XDR, SOAR automation, and real-time analytics—enables faster threat detection and response. This core capability highlights major benefits of AI driven SOC as a service, including reduced false positives and accelerated decision-making.
- 24/7 coverage: Follow-the-sun SOCaaS with continuous monitoring and rapid escalation across regions.
- Proactive defense: Integrated threat intelligence and continuous threat hunting to stop attacks pre-impact.
- Measured speed: SOAR playbooks cut MTTD/MTTR and standardize containment and recovery.
- Compliance built-in: Evidence-ready reporting aligned to HIPAA, PCI DSS, ISO 27001, and GDPR.
- Seamless fit: Flexible managed soc providers that augment in-house teams and existing tools.
- Resilience outcomes: Demonstrable uplift in security posture and business continuity at enterprise scale.
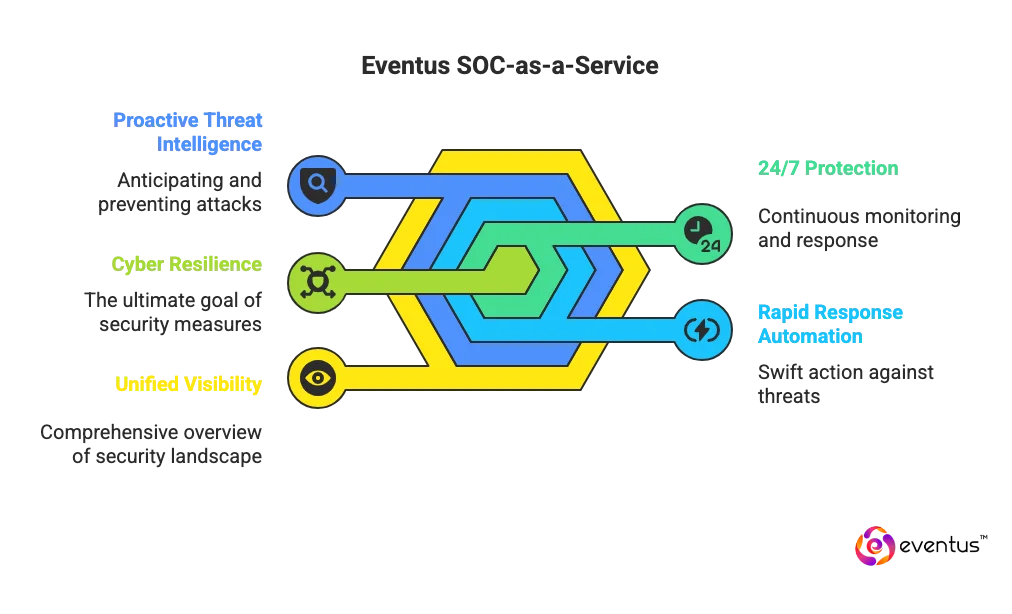
Secure Your Business with Eventus SOC-as-a-Service
Eventus delivers a powerful blend of AI, automation, analytics, global coverage, and expert human oversight to protect enterprises from advanced cyber threats. With unified visibility, proactive threat intelligence, rapid response automation, and continuous 24/7 protection, Eventus helps businesses build cyber resilience in an increasingly hostile digital world.
Talk To Our Expert Today: https://eventussecurity.com/contact-us/
FAQs
Q1. How does Eventus integrate with existing enterprise IT and security tools?
Eventus Security’s platform includes open APIs and pre-built connectors for SIEM, EDR, IAM, CSPM, and ITSM solutions. This interoperability enables seamless data normalization, unified incident visibility, and coordinated response actions across the enterprise’s existing technology stack—without forcing tool replacement or vendor lock-in.
Q2. What role does human expertise play in Eventus’s AI-driven SOC model?
While automation handles repetitive triage and enrichment, Eventus maintains a “human-in-the-loop” approach. Experienced Tier-1 to Tier-3 analysts validate alerts, conduct deep forensic analysis, and apply contextual judgment that AI models cannot replicate. This balance ensures accuracy, faster containment, and minimized false positives.
Q3. How does Eventus measure the effectiveness of its Managed SOC services?
Eventus tracks measurable KPIs such as Mean Time to Detect (MTTD), Mean Time to Respond (MTTR), incident volume reduction, and alert accuracy. Continuous analytics and reporting dashboards allow clients to benchmark performance improvements, demonstrating tangible ROI and enhanced cyber resilience.
Q4. How does Eventus maintain data sovereignty and privacy for global clients?
To comply with regional regulations, Eventus deploys localized SOC hubs and ensures data residency within each jurisdiction. Data is encrypted in transit and at rest, while tenant isolation prevents cross-customer data access—meeting privacy requirements across the EU, Middle East, and Asia.
Q5. How does Eventus support incident recovery and post-breach analysis?
Beyond detection and containment, Eventus assists enterprises with digital forensics, root-cause analysis, and post-incident reporting. Automated evidence collection and audit trails accelerate recovery while informing strategic improvements in defense posture and compliance alignment.