This article explains how managed SOC services enhance threat detection and incident response by combining advanced technology, skilled teams, and structured processes. It covers what managed SOCs are, how they monitor telemetry at scale, and their methods for detecting advanced threats.
Table of Contents
What is a managed SOC and how does it enhance threat detection and response?
A managed SOC is a security operation delivered by a specialized SOC provider that focuses on real-time monitoring, threat detection, and incident response. Unlike an in-house SOC, a managed security operations center combines advanced technology, skilled SOC teams, and structured processes to enhance threat detection and response capabilities.
By using security information and event management (SIEM) systems, integrated threat intelligence, and automated response workflows, Ai driven SOC service improves visibility and response times across the entire threat landscape. This operational model helps organizations detect and respond to potential threats before they escalate into a breach.
Keyways they enhances threat detection and response:
- Comprehensive threat detection: Uses SIEM, analytics, and threat intelligence to detect cyber threats and potential threats across endpoints, networks, and cloud environments.
- Rapid response capabilities: Delivers faster threat containment and recovery through automated response actions and structured escalation paths.
- Proactive threat monitoring: Provides continuous, real-time coverage to identify operational risks and prevent breaches before they impact sensitive data.
- Improved security posture: Enhances an organization’s ability to detect and respond effectively to cyber threats by leveraging managed security operations and specialized SOC services.
- Cost and expertise advantage: Offers access to a skilled 24/7 SOC team and advanced technology without the overhead of running an in-house SOC.
How Soc provider monitor and analyze security telemetry at scale?
Managed SOC as a service use advanced technology, expert analysts, and continuous processes to detect and respond to threats across diverse environments. They collect, normalize, and correlate security data at scale, enabling proactive monitoring and rapid incident response.
Key methods include:
- Data collection: Real-time ingestion of logs from endpoints, networks, cloud workloads, and applications.
- SIEM analysis: Centralized aggregation and correlation to identify suspicious activity.
- Threat intelligence: Integration of curated feeds to detect emerging threats.
- Enrichment and correlation: Context added around users, devices, and applications for accuracy.
- Scalable response: Automation and playbooks speed up response and reduce workload.
- Continuous monitoring: 24×7 detection and response for uninterrupted protection.
By leveraging AI driven SOC as a service, organizations strengthen security posture with expert monitoring, automated response, and scalable capabilities—without the overhead of running an in-house SOC.
How do they detect advanced threats reliably?
Managed SOCs detect advanced threats by combining continuous monitoring, contextual intelligence, and expert teams. They go beyond signature-based detection, using analytics, threat intelligence, and automation to identify threats that bypass traditional tools.
Key methods include:
- Behavioral and anomaly detection: Identifying unusual user or system activity.
- Threat intelligence feeds: Enriching SIEM data for real-time detection.
- Telemetry correlation: Linking logs across endpoints, networks, and cloud.
- Proactive hunting: Hypothesis-driven searches for hidden adversaries.
- Rule tuning: Updating detections as threats evolve.
- Deception tools: Using canaries and honey tokens to trap attackers.
- Automated response: Containing threats quickly with playbooks.
This combination delivers reliable detection and faster response, strengthening security beyond typical in-house SOC capabilities.
How is threat intelligence integrated into managed SOC operations?
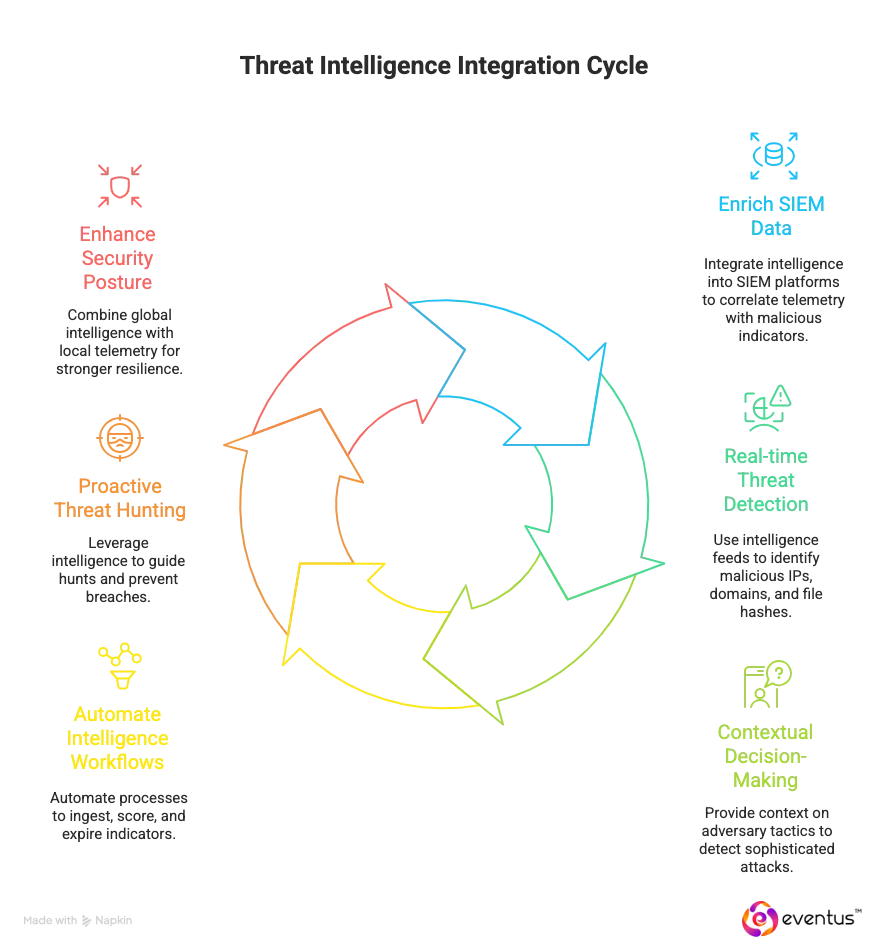
Threat intelligence is integrated into managed SOC operations to improve the accuracy, speed, and effectiveness of threat detection and incident response. A managed security services soc uses structured intelligence feeds, contextual enrichment, and operational workflows to ensure that the 24/7 SOC team can detect and respond to cyber threats in real-time with greater precision.
Key ways threat intelligence is integrated into SOC services:
- Enrichment of SIEM data: Managed SOC providers embed threat intelligence into security information and event management platforms, helping analysts detect potential threats by correlating telemetry with known malicious indicators.
- Real-time detection of cyber threats: Threat intelligence feeds enhance managed security operations centres by identifying malicious IPs, domains, and file hashes, allowing SOC teams to respond faster.
- Contextual decision-making: Intelligence provides context on adversary tactics, techniques, and procedures, enabling managed SOC services to detect and respond to sophisticated attack patterns across the threat landscape.
- Automation of intelligence workflows: Automated response capabilities ingest, score, and expire indicators, ensuring the managed SOC service remains current and reduces noise from stale data.
- Proactive threat hunting: 24/7 managed SOC teams leverage intelligence to guide hunts, detect advanced persistent threats, and prevent breaches that target sensitive data.
- Operational response capabilities: Managed SOC providers integrate curated intelligence into response playbooks, improving response times and ensuring consistent containment actions.
- Enhancing security posture: By combining global intelligence with local telemetry, SOC services provide organizations with faster threat detection and stronger resilience against emerging cyber threats.
How do they perform proactive threat hunting?
Managed security services soc conduct proactive threat hunting through hypothesis-driven investigations across enterprise telemetry to uncover threats that bypass alerts. They combine skilled teams, SIEM analytics, and threat intelligence to detect stealthy activity early and improve response.
Key practices include:
- Defining hunt hypotheses aligned with attacker tactics and sensitive targets.
- Collecting high-value data from endpoints, identities, networks, DNS, cloud, and SaaS.
- Enriching telemetry with intelligence, context, and behavioral baselines.
- Correlating anomalies such as credential misuse, lateral movement, or rare processes.
- Using temporal analysis to link low-signal events into multi-stage campaigns.
- Validating findings with playbooks to minimize false positives.
- Turning confirmed threats into new rules and automated responses.
- Measuring outcomes like reduced dwell time and improved detection precision.
These methods make threat hunting systematic, strengthening detection and response beyond typical in-house SOC capabilities.
How do they execute incident response actions?
Managed SOCs execute incident response actions through predefined playbooks that coordinate people, process, and technology to detect and respond in real time. A managed security operations center uses SIEM, threat intelligence, and automated response to contain a breach quickly and protect sensitive data.
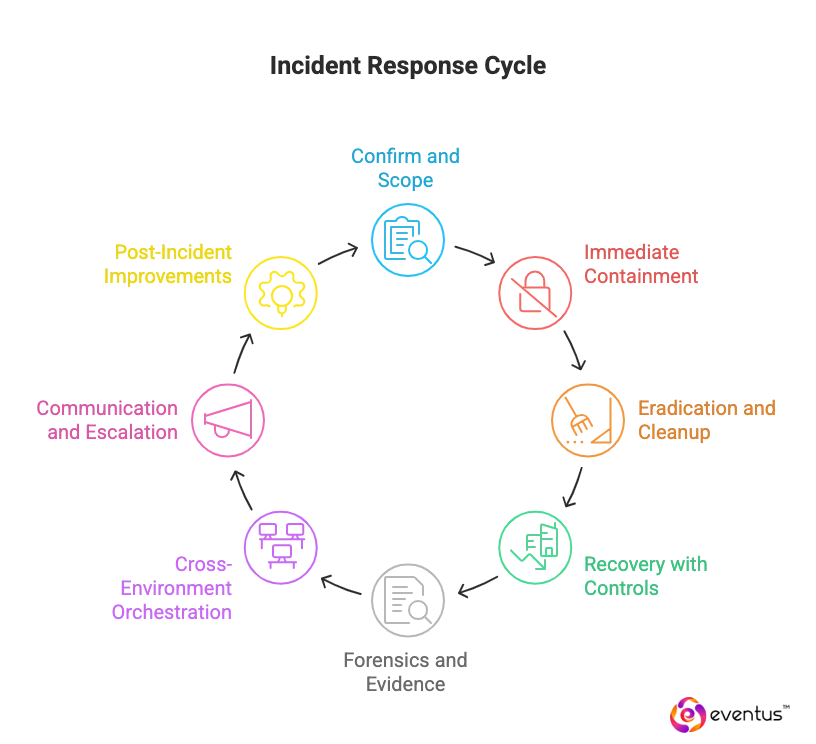
- Confirm and scope the incident: 24/7 SOC team validates alerts in SIEM, enriches with threat intelligence, and defines affected users, hosts, and cloud assets to guide targeted action.
- Immediate containment: Execute automated response steps such as endpoint isolation, account disablement, MFA resets, key and token rotation, and network blocks to stop attacker movement and data loss.
- Eradication and cleanup: Remove malware and tooling, revoke persistence mechanisms, patch exploited vulnerabilities, and reimage compromised systems where required.
- Recovery with controls: Restore services from trusted backups, reintroduce assets in stages, and enforce hardening baselines so systems return with a stronger security posture.
- Forensics and evidence handling: Preserve volatile and disk artifacts, maintain chain of custody, and document actions inside the managed SOC service case record for legal or audit use.
- Cross-environment orchestration: Coordinate actions across endpoints, identity providers, email, firewalls, and cloud platforms so the 24/7 SOC service can detect and respond consistently across hybrid estates.
- Communication and escalation: Inform stakeholders with time-stamped updates, engage the service provider’s incident commanders, and align internal IT and leadership on decisions.
- Post-incident improvements: Run a lessons-learned review, convert findings into new detections and playbooks, and tune response capabilities to reduce future response times.
How do they strengthen endpoint and identity defenses?
24/7 Managed SOCs enhance endpoint and identity security through continuous monitoring, analytics, and automated response. They focus on reducing attacker dwell time, detecting identity misuse, and protecting sensitive data.
Key methods include:
- EDR visibility: Detecting malware, lateral movement, and persistence.
- Identity monitoring: Tracking logins, privilege escalations, and anomalies.
- Privileged account control: Oversight of admin accounts to reduce abuse.
- Proactive hardening: Baselines, patching, and least-privilege enforcement.
- Automated response: Isolating endpoints or disabling accounts instantly.
- Threat intelligence: Enriching telemetry for advanced detection.
- Rapid response: Coordinated containment of endpoint or identity attacks.
How do they secure cloud and hybrid environments?
Managed SOCs secure cloud based soc and hybrid environments by extending visibility, correlation, and response across on-premises, multi-cloud, and SaaS systems. They provide real-time monitoring and response to protect workloads and sensitive data wherever they reside.
Key practices include:
- Telemetry collection: Logs from cloud, SaaS, containers, and on-prem unified in SIEM.
- Misconfiguration detection: Monitoring policy drift, privilege misuse, and abnormal API calls.
- Threat intelligence: Correlating hybrid telemetry with curated intelligence.
- Threat hunting: Proactive analysis to detect stealthy attacks.
- Automated response: Orchestration to isolate workloads, block traffic, or disable accounts.
- Operational consistency: Standardized response across platforms.
- Compliance and resilience: Continuous monitoring strengthens overall security posture.
This ensures cohesive defense and faster threat containment in complex hybrid architectures.
How do they govern data quality and tuning?
Managed SOCs govern data quality and tuning by applying structured processes that ensure telemetry is accurate, relevant, and optimized for effective threat detection and incident response. A managed security operations center combines SIEM, threat intelligence, and analyst feedback loops to enhance precision and reduce noise in security operations.
Key practices include:
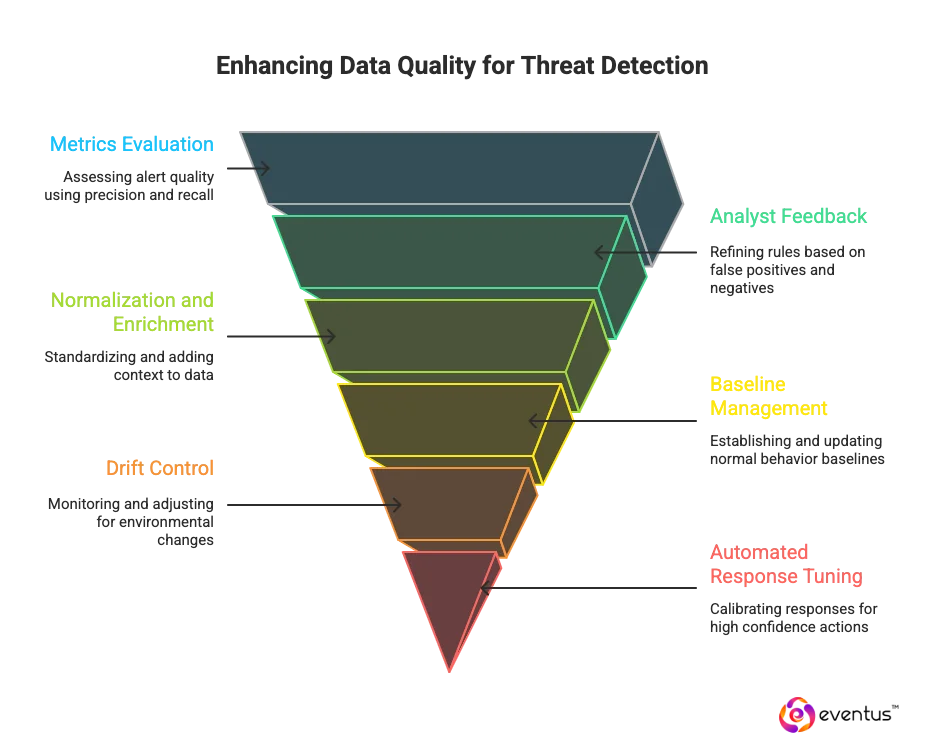
- Metrics-driven evaluation: 24/7 Managed security service provider use measurable indicators such as precision, recall, and coverage to assess the quality of alerts and ensure they detect real cyber threats.
- Analyst feedback loops: SOC teams continuously refine rules and detection logic by reviewing false positives and false negatives, improving operational accuracy.
- Normalization and enrichment: Managed security operations centres process telemetry to standardize formats and enrich data with contextual details, enabling more effective threat detection and response.
- Baseline management: AI driven SOC providers establish and update baselines for normal behavior across endpoints, identities, and networks to detect anomalies more reliably.
- Drift control: Managed SOC providers monitor for environmental or technology changes that might degrade detection quality, adjusting rules and models proactively.
- Automated response tuning: Automated response workflows are calibrated to act only when confidence levels are high, ensuring faster threat containment without unnecessary disruption.
- Proactive threat validation: SOC services include ongoing validation of detection rules against emerging cyber threats in the threat landscape to enhance resilience and prevent breaches.
By governing data quality and tuning in this way, managed SOC providers improve response times, strengthen security posture, and ensure that security services deliver reliable protection against potential threats while safeguarding sensitive data.
How is performance measured and improved in programs?
managed SOC services provider programs measure performance with outcome-focused, time-bound KPIs and improve it through continuous engineering across people, process, and technology.
Performance is measured by:
- MTTD / MTTR: Speed of detection, response, and containment.
- Dwell Time: Duration from compromise to eradication.
- Alert Quality: Precision, recall, and false positives.
- Coverage: % of critical assets and workloads monitored.
- Automation Rate: Share of incidents resolved with playbooks.
- SLA Adherence: Escalation and triage times against contracts.
- Throughput/Backlog: Analyst caseload and open investigations.
- Control Efficacy: Accuracy of block/allow decisions.
- Compliance Readiness: Audit evidence completeness.
Performance is improved by:
- Detection engineering: Refining SIEM rules from incident reviews.
- Playbook optimization: Automating high-confidence steps.
- Hunt-to-detect conversion: Turning hunt findings into durable detections.
- Data governance: Enriching telemetry, focusing on critical systems.
- Adversary emulation: Purple-team testing against current threats.
- Capacity planning: Adjusting staffing and tools to avoid backlogs.
- Executive reporting: Aligning security investments with measurable posture gains.
How do they support compliance and audit readiness?
Managed security service provider support compliance and audit readiness by embedding monitoring, documentation, and reporting into daily operations. They integrate detection, response, and evidence collection so organizations can meet regulatory requirements while maintaining strong security.
Key enablers include:
- Centralized logging: Retaining logs across systems to meet data mandates.
- Evidence-ready reporting: Audit trails aligned with ISO 27001, HIPAA, PCI DSS.
- Threat intelligence integration: Proactive defense proof for auditors.
- Consistent documentation: Case records of incidents and remediation.
- Automated enforcement: Policies and response actions triggered instantly.
- Regulatory alignment: Mapping SOC processes to compliance controls.
- Post-incident reviews: Linking responses to compliance evidence.
This ensures measurable, auditable security operations and continuous readiness for evolving regulations
How do operating models and service levels work?
Managed SOC services provider use defined operating models and service levels to deliver consistent monitoring, detection, and incident response while aligning with business risk and compliance needs. They provide structured commitments for coverage, response, and reporting—often more cost-effective and scalable than in-house SOCs.
Operating models include:
- Service delivery: Managed services or SOC as a Service with provider-owned infrastructure.
- Shared responsibility: SOC manages detection and response, clients handle business context and access.
- Integrated workflows: Seamless alignment with ITSM, SIEM, and detection tools.
- Scalable coverage: 24/7 monitoring, global SOCs, multi-tenant or dedicated setups.
- Tech enhancement: Advanced analytics and ML for improved detection.
Service levels include:
- Defined SLAs: Measurable commitments for detection, escalation, and response.
- Tiered options: From basic log monitoring to full detection and response.
- Response commitments: Clear timelines for critical incident handling.
- Reporting & improvement: Regular reports, compliance evidence, and reviews.
- Benefits: Predictability, transparency, and stronger security posture.
Which managed SOC use cases and scenarios are most impactful?
- Ransomware precursors and containment : Detect privilege escalation, lateral movement, and data staging; isolate endpoints and revoke credentials to cut dwell time and prevent encryption at scale.
- Business email compromise and account takeover: Correlate identity anomalies, impossible travel, MFA resets, and payment-rule edits; enforce step-up auth and mailbox rules cleanup to stop wire-fraud attempts.
- Phishing campaigns with credential theft: Tie email telemetry to endpoint and identity signals; auto-quarantine messages, reset tokens, and block sender infrastructure to reduce click-to-contain time.
- Insider misuse and data exfiltration: Baseline access patterns; flag unusual downloads, archive creation, or cloud-share spikes; throttle access and trigger DLP controls to protect sensitive data.
- Supply-chain and third-party compromise: Monitor vendor integrations, API keys, and OAuth grants; detect abnormal partner activity and rotate secrets to contain blast radius.
- Cloud misconfigurations and privilege abuse: Surface risky IAM changes, public buckets, and anomalous API calls; auto-remediate policies and enforce least privilege across multi-cloud estates.
- Endpoint malware and hands-on-keyboard intrusion: Correlate EDR detections with process trees and network beacons; isolate hosts, kill processes, and purge persistence to stop propagation.
- Lateral movement and Kerberoasting/NTLM relay: Detect abnormal admin paths, ticket abuse, and DC targeting; disable compromised accounts and enforce tiered admin boundaries.
- Web account takeover and credential stuffing: Fuse WAF, IDP, and app logs to detect high-velocity failures and new device patterns; apply adaptive challenges and block malicious networks.
- Data integrity attacks and backup tampering: Flag destructive commands, backup deletions, and mass policy changes; lock backup vaults and invoke recovery runbooks.
- OT/ICS anomaly detection (where applicable): Spot protocol deviations and unauthorized engineering-workstation actions; segment affected cells and coordinate safe shutdown.
- Compliance-critical event handling: Ensure evidence-ready case records, chain of custody, and control mapping during incidents to meet audit requirements while containing risk.
How should buyers evaluate and compare managed SOC providers?
- Detection & Coverage: Verify mapped use cases (BEC, ransomware, lateral movement, exfiltration) and data sources; aim for ≥90% coverage of critical systems.
- Alert Quality & Outcomes: Request precision/recall, false-positive rates, and percentile metrics for MTTD/MTTR (P1 containment ≤60 min).
- Threat Intel & Hunting: Check intel integration, hunt frequency, and hunt-to-detect conversion reporting.
- Automation & Orchestration: Review playbooks, automation success rate, and scope of containment (host, account, token).
- Investigation Tooling: Assess case management, evidence handling, and audit readiness.
- Cloud & Hybrid Skills: Confirm depth in AWS/Azure/GCP, Kubernetes, SaaS, and multi-cloud response.
- Staffing & Expertise: Validate analyst ratios, certifications, 24×7 coverage, and incident commander availability.
- SLAs & Model: Inspect definitions for P1–P3 handling, acknowledgement, and RACI clarity.
- Data Handling: Check retention, residency, privacy controls, and log export capability.
- Integration Breadth: Ensure native support for EDR, IDP, email, firewalls, ITSM, and collaboration tools.
- Detection Engineering: Look for rule tuning, missed-detection reviews, and purple-team validation.
- Reporting & Governance: Require KPI dashboards, executive summaries, and compliance mapping.
- Cost Transparency: Understand pricing drivers, burst costs, and overage rules.
- Surge Capacity: Verify crisis staffing, on-call escalation, and redundancy.
- Exit & Portability: Ensure data/IP portability, deprovisioning, and runbook escrow
- Customer Proof: Request recent case studies, references, and third-party audits.
FAQs
1. What is a Managed SOC and how does it improve threat detection?
A Managed SOC is a 24/7 outsourced security operations center that uses advanced tools like SIEM, threat intelligence, and automation to detect and respond to cyber threats in real time. It helps organizations identify and stop attacks before they cause damage
2. How do Managed SOC providers detect advanced threats?
They combine behavioral analytics, threat intelligence, and anomaly detection to uncover attacks that bypass traditional tools. Techniques include proactive threat hunting, telemetry correlation, and automated response to contain incidents quickly
3. How is threat intelligence used in a Managed SOC?
Threat intelligence feeds are integrated into SIEM systems to identify malicious IPs, domains, and file hashes in real time. This enriches data, provides context for analysts, and supports faster, more accurate responses to cyber threats
4. What makes Managed SOC services cost-effective?
They offer access to skilled security analysts, AI-driven automation, and advanced detection technologies without the expense of maintaining an in-house SOC, making enterprise-grade cybersecurity affordable for all organization sizes
5. How is performance measured in Managed SOC programs?
Performance is tracked using metrics such as Mean Time to Detect (MTTD), Mean Time to Respond (MTTR), alert accuracy, coverage percentage, and SLA adherence. These indicators help maintain continuous improvement in detection and response quality