This article explains how end-to-end managed SOC solutions work. It outlines core components, the services included (monitoring, SIEM/MDR, incident response, vulnerability management), and the measurable benefits for cost, coverage, and security posture.
Table of Contents
You’ll see how SOCaaS compares with an in-house SOC, how to evaluate and choose a provider, and how a managed soc solution model supports compliance and governance.
We also cover how SOC as a service providers strengthens enterprise cybersecurity across cloud and endpoint environments and conclude with what’s next for managed SOC and 24/7 managed SOC evolution.
Who are SOC as a Service Providers?
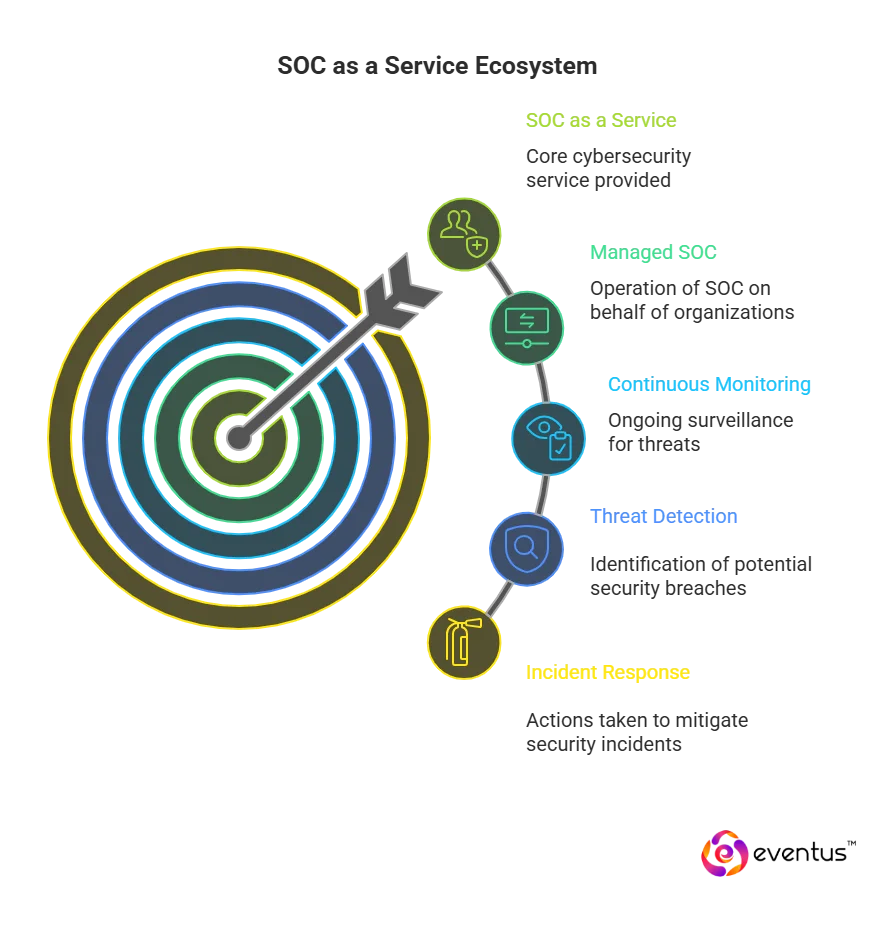
SOC as a Service providers are specialized cybersecurity companies that deliver end-to-end managed SOC services through cloud-based, subscription-driven models.
They operate a Security Operations Center (SOC) on behalf of organizations, offering continuous monitoring, threat detection, and incident response services without requiring an in-house SOC.
| Aspect | In-House SOC | SOC as a Service (SOCaaS) |
| Setup Time | 6–12 months | Immediate onboarding |
| Cost | High CapEx + Opex | Predictable monthly subscription |
| Staffing | Requires full internal team | Managed by provider experts |
| Coverage | Business hours | 24/7/365 |
| Scalability | Limited | Fully scalable |
| Technology | Often outdated | Regularly updated & integrated |
What Are the Core Components of an End-to-End Managed Security Operations Centre?
An end-to-end Managed Security Operations Centre (SOC) integrates advanced technology, expert security analysts, and automated processes to deliver comprehensive security across networks, endpoints, and cloud systems. Each component plays a defined role in ensuring real-time protection, incident management, and threat intelligence integration.
Key components include:
- Continuous Security Monitoring: The foundation of any managed soc as a service providers, it provides 24/7 visibility across systems, networks, and users. This ensures immediate detection of suspicious security events and potential breaches.
- Threat Detection and Response (MDR Services): Using 24/7 managed soc solutions detection and response capabilities, SOC teams identify cyber threats early and contain them through automated playbooks and expert analysis.
- Security Information and Event Management (SIEM): Centralized logging and correlation of security incidents help SOC analysts interpret threat data, streamline investigations, and maintain compliance with regulatory standards.
- Incident Response and Recovery: A core security service where SOC as a service providers manage detection, containment, and mitigation to reduce business disruption and strengthen the organization’s security posture.
- Vulnerability and Endpoint Security Management: Regular scanning and patching of vulnerabilities across devices maintains robust security and reduce exposure to potential security threats.
- Threat Intelligence Integration: SOC teams use curated intelligence feeds to anticipate evolving cybersecurity risks and align proactive defense strategies with emerging threats.
- Cloud and Network Security: Through cloud service integration and network security controls, 24/7 managed SOC services providers ensure seamless protection across hybrid and multi-cloud infrastructures.
- Security Analytics and Automation: AI-driven analytics, automation, and correlation tools improve accuracy in threat detection and response, minimizing manual intervention and improving service levels.
- Compliance and Reporting: Continuous audit logging and evidence collection simplify compliance management while maintaining transparency with regulatory requirements.
- Dedicated SOC Team and Expertise: 24/7 managed SOC solutions deploys a team of security experts, SOC analysts, and engineers who continuously refine detection rules, respond to incidents, and ensure operational excellence.
What Services Are Included in Eventus SOC as a Service?
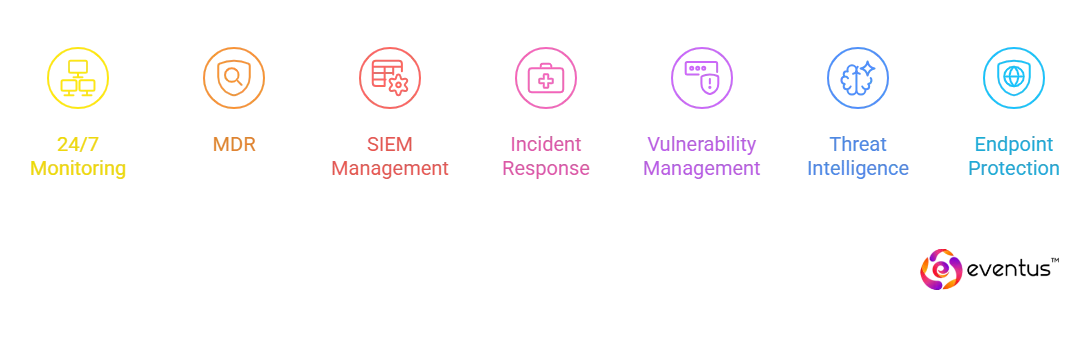
Given below are the services of best soc as a service:
- 24/7 SOC monitoring and alerting: Continuous soc monitoring across endpoints, networks, and cloud to respond to security events.
- Managed detection and response (MDR): Analytics, threat hunting, and rapid containment as 24/7 managed soc solutions for end-to-end security.
- SIEM management and correlation: Operate and tune soc and siem for log aggregation, normalization, and incident correlation.
- Incident response and recovery: Playbooks, triage, forensics, and coordinated remediation with post-incident reporting.
- Vulnerability and exposure management: Scanning, prioritization, and patch guidance to meet security requirements.
- Threat intelligence and hunts: Curated intel, IOC/IOA matching, and proactive hunts for emerging cyber security risks.
- Endpoint, identity, and cloud protection: EDR/XDR tuning, IAM hardening, and cloud configuration monitoring via managed soc solutions.
- Compliance reporting and audits: Evidence collection and mapped controls—services designed to help regulated teams.
- Security architecture & consulting services: Gap assessments and use-case design to optimize existing security.
- SOAR playbook automation: Automated enrichment and response to improve consistency and service level outcomes.
- Tooling integration: Harmonize with current cybersecurity solutions to avoid rip-and-replace.
- Program governance: KPIs, executive reporting, and continuous improvement with 24/7 managed soc services provider.
What Are the Benefits of Using SOC as a Service (SOCaaS)?
Partnering with Eventus gives your organization measurable improvements in both security and operational efficiency. Given below are the benefits:
| Benefit | Description |
| Lower Cost, Higher Agility | Eliminate CapEx and scale as your business grows. |
| Expert Coverage | Access top-tier analysts without hiring overhead. |
| Faster Detection & Response | Reduce threat dwell time through AI and automation. |
| End-to-End Protection | Comprehensive coverage across endpoints, cloud, and networks. |
| Improved Compliance | Maintain audit-ready data aligned with GDPR, HIPAA, ISO 27001. |
| Business Focus | Let your team focus on core business priorities. |
For a detailed Benefits visit our article – Benefits of AI Driven SOC as a Service
What Makes Eventus a Leading SOC as a Service Provider?
The following are the points that make a top SOC as a service provider:
- Proven expertise and reliability: Top SOC providers deliver trusted ai and automation SOC operations with skilled analysts, advanced tooling, and mature processes that ensure continuous protection.
- Comprehensive service coverage: The best SOC provider companies offers end-to-end soc solutions, including monitoring, threat detection, and response, aligned with evolving managed soc solutions security services standards.
- Automation and innovation: Leading SOCaaS providers leverage orchestration, AI analytics, and automation—services designed to improve accuracy and speed of response.
- Scalable and flexible delivery: Top SOC as a Service (SOCaaS) models adapt to different business sizes and risk profiles, providing modular services to meet unique security needs.
- Strong governance and transparency: Clear service levels, performance metrics, and audit reporting define how the service works and maintains accountability.
- Integration with existing environments: A capable provider seamlessly connects to in-house security tools and infrastructure for unified soc operations.
- Customized approach: Soc as a service Providers offer tailored security solutions, additional services, and architecture consulting for organizations that need a security operations center as a service or are implementing a SOC.
- Trusted partnerships: A service solution provider that builds long-term relationships, enabling a successful SOC through collaboration and continuous improvement.
How Does It Help Maintain Compliance and Governance?
A Security Operations Center (SOC) helps organizations maintain compliance and governance by aligning security monitoring and reporting with regulatory and policy frameworks. Through automation, standardization, and continuous oversight, SOC ensures adherence to data protection and governance standards. Here’s how:
- Centralized visibility: The latest SOC architecture consolidates logs, alerts, and incidents to maintain audit-ready evidence and reduce compliance gaps.
- Regulatory alignment: Services designed to help map controls and reporting mechanisms to industry mandates such as GDPR, HIPAA, or ISO 27001.
- Automated audit trails: SOC uses automation to generate verifiable records, reducing manual errors while improving accuracy and traceability.
- Policy enforcement: Defined processes ensure consistent implementation of governance policies that every SOC requires to maintain accountability.
- Support for hybrid models: Whether outsourcing or maintaining an in-house SOC, compliance functions are standardized for operational integrity.
- Continuous assessment: Services are designed to provide proactive compliance checks and gap analysis for ongoing governance improvements.
- Business assurance: A compliant SOC framework service gives confidence to stakeholders by demonstrating that data and operations are governed responsibly.
What Is the Future of Managed SOC and Cybersecurity Evolution?
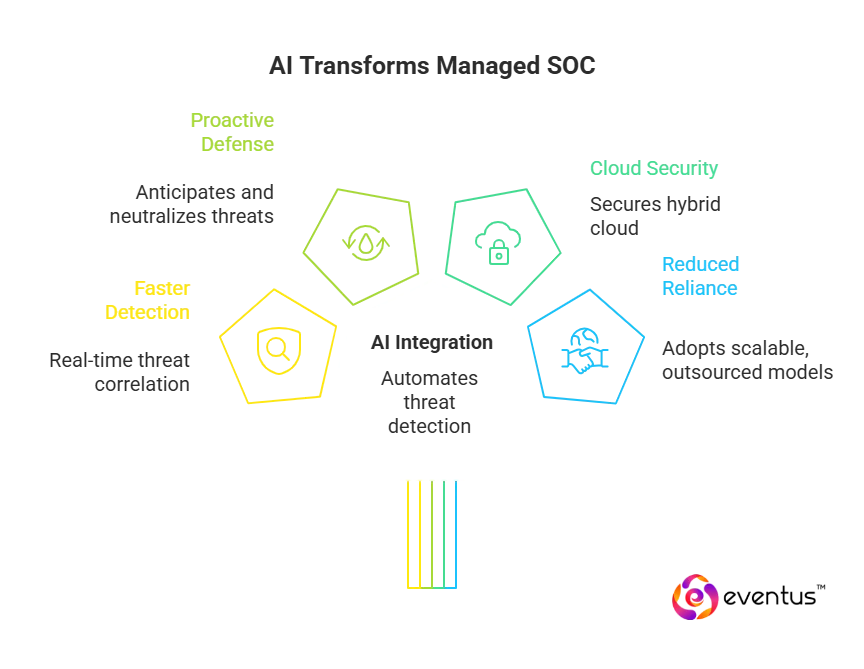
The future of managed SOC is defined by automation, intelligence, and adaptive defense strategies that address complex, evolving threats. As organizations face increased cyber risk, the benefits of a SOC will extend beyond detection and response to predictive and autonomous security management.
Given below are some points:
- AI-driven operations: Advanced ai driven soc as a service and machine learning will enable faster threat detection, real-time correlation, and automated mitigation.
- Integrated cybersecurity ecosystems: Service companies will consolidate services offered under unified platforms combining SOC, SOAR, and XDR for end-to-end visibility.
- Shift from reactive to proactive defense: Predictive analytics and behavioral modeling will allow 24/7 managed SOCs to anticipate and neutralize threats before exploitation.
- Cloud-first security: With more workloads moving to the cloud security, SOCs will evolve to secure hybrid and multi-cloud infrastructures effectively.
- Reduced reliance on in-house SOCs: Businesses will transition from managing an in-house SOC to adopting scalable, outsourced managed models that provide continuous improvement and adaptability.
Secure Your Business with Eventus SOC as a Service (SOCaaS)
Cybersecurity is no longer optional — it’s a business imperative. Eventus SOC as a Service provides the visibility, intelligence, and protection your organization needs to defend against ever-evolving cyber threats.
By combining AI-driven automation, 24/7 monitoring, and expert response teams, Eventus empowers businesses to stay one step ahead of attackers while maintaining compliance and operational resilience.
Eventus SOC-as-a-Service — a trusted partner for end-to-end managed SOC solutions, delivering reliability, speed, and peace of mind.
FAQs
Q1. What Is SOC as a Service (SOCaaS)?
Ans: SOCaaS is a cloud-based service where a provider manages your Security Operations Center, offering 24/7 monitoring, threat detection, and incident response without building an in-house SOC.
Q2. How Does a Managed SOC Solution Work?
Ans: It combines advanced tools, automation, and expert analysts to detect, respond to, and prevent threats across networks, endpoints, and cloud environments.
Q3. What Are the Benefits of Using SOC as a Service?
Ans: Lower cost, 24/7 expert coverage, faster threat response, improved compliance, and scalable security operations.
Q4. How Does SOC as a Service Support Compliance and Governance?
Ans: SOCaaS ensures audit-ready reporting, automates compliance processes, and aligns security controls with standards like GDPR, HIPAA, and ISO 27001.
Q5. How Is SOC as a Service Evolving in the Future?
Ans: SOCaaS is moving toward AI-driven automation, integrated XDR/SOAR platforms, and proactive threat defense for smarter, predictive security.