Eventus doesn’t just “handle” ransomware, it helps you build cyber resilience around it through its advanced managed SOC services.
Table of Contents
This article walks through how a structured, multi-layered defense, anchored by a strong SOC as a service (SOCaaS), prevents attacks, protects and recovers data, detects threats in real time, coordinates response, and uses every incident to make your organization tougher over the long term.
This approach aligns with modern ransomware resilience frameworks, zero trust policies, and continuous monitoring, helping enterprises reduce cyber risk and maintain operational continuity.
What Is the Eventus Way to Cyber Resilience Against Ransomware?
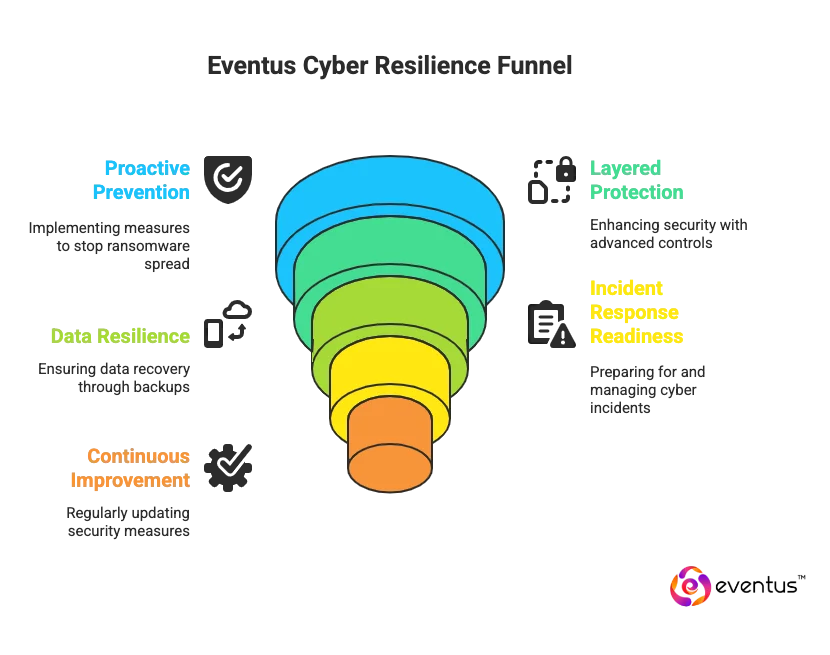
The Eventus Way to cyber resilience against ransomware is a multi-layered defense framework designed to protect organizations across prevention, detection, response, and recovery, integrating proven security practices, adaptive technologies, and the strength of SOC managed service providers to cut down vulnerabilities, stop exploitation, and ensure fast, precise recovery.
Eventus integrates advanced security controls, governance frameworks, and adaptive technologies to help organizations become ransomware resilient, making it a strong contender among the best SOC provider companies. The strategy involves minimizing vulnerabilities, mitigating exploitation, and ensuring rapid recovery through precision-driven processes.
Key elements of The Eventus Way include:
1. Proactive Prevention:
- Vulnerability management
- Continuous updates and patching
- MFA enforcement
- Firewall optimization
Eventus prioritizes vulnerability management, continuous security updates, and multi-factor authentication (MFA) to stop ransomware before it spreads. This is a core reason why a Managed SOC prevents ransomware effectively in hospitals and other high-risk sectors.
2. Layered Protection:
- Advanced endpoint protection
- Anti-malware controls
- Zero Trust architecture
Advanced endpoint protection, anti-malware, and zero trust architecture minimize the attack surface, ensuring critical assets remain secure even during a cyber incident. This approach showcases the benefits of AI-driven SOC as a service.
3. Data Resilience:
- Immutable backups
- Offsite storage
- Regular audits
The 3-2-1 backup strategy with immutable and offsite storage ensures that systems and data can recover quickly without paying the ransom. Regular audit and readiness assessments validate backup integrity and restoration capability.
4. Incident Response Readiness:
- Detailed IR checklists
- Simulation exercises
- SOC-driven ransomware playbooks
Eventus implements a detailed incident response checklist, supported by simulation exercises and playbooks that help organizations respond to and recover from ransomware attacks with minimal disruption, strengthened further by managed SOC services.
5. Continuous Improvement:
- Security audits
- Penetration testing
- Attack surface management
Through regular security audits, penetration testing, and attack surface management, Eventus uses its SOC service to help organizations spot weaknesses early, fix them quickly, and stay resilient against evolving cyber threats.
6. People and Processes:
- Employee awareness training
- Phishing prevention education
- Governance frameworks
Employees receive awareness training to recognize phishing attempts—the leading cause of ransomware infections—ensuring that human error does not compromise organizational security.
How Does Eventus Prevent Ransomware Attacks Before They Start?
Eventus prevents ransomware before it starts by enforcing a layered, standards-driven cyber security program strengthened by a managed SOC services that closes every path attackers can exploit.
Here’s how:
- Eliminate vulnerabilities: Continuous patching, configuration hardening, and cyber hygiene to reduce exposure across network and systems.
- Control identity and access: Least privilege, strong access controls, and segmentation across cloud service environments.
- Block initial infection: Advanced email filtering, phishing defenses, and EDR-based ransomware protection on every endpoint and device security baseline.
- Architect for containment: Zero-trust policies and micro-segmentation to limit blast radius for internal and external threats.
- Assure recoverability: Offline and isolated backups with routine drills so you can recover from an attack without paying ransom, restoring applications and data and recover systems fast.
- Prove readiness: Ransomware resilience assessment, mapped security practices to Cyber Essentials certification, and KPI-driven audits to protect your organization and reassure every stakeholder.
This prevention approach positions Eventus strongly in the domain of SOCaaS, managed SOC solutions, and top SOC as a Service providers.
How Does Eventus Ensure Data Protection and Recovery After an Attack?
Eventus ensures data protection and recovery after a ransomware attack through a structured, resilience-focused process designed to restore operations quickly without compromising integrity, and its best SOC as a service capability strengthens this effort by catching threats early and supporting clean, confident recovery.
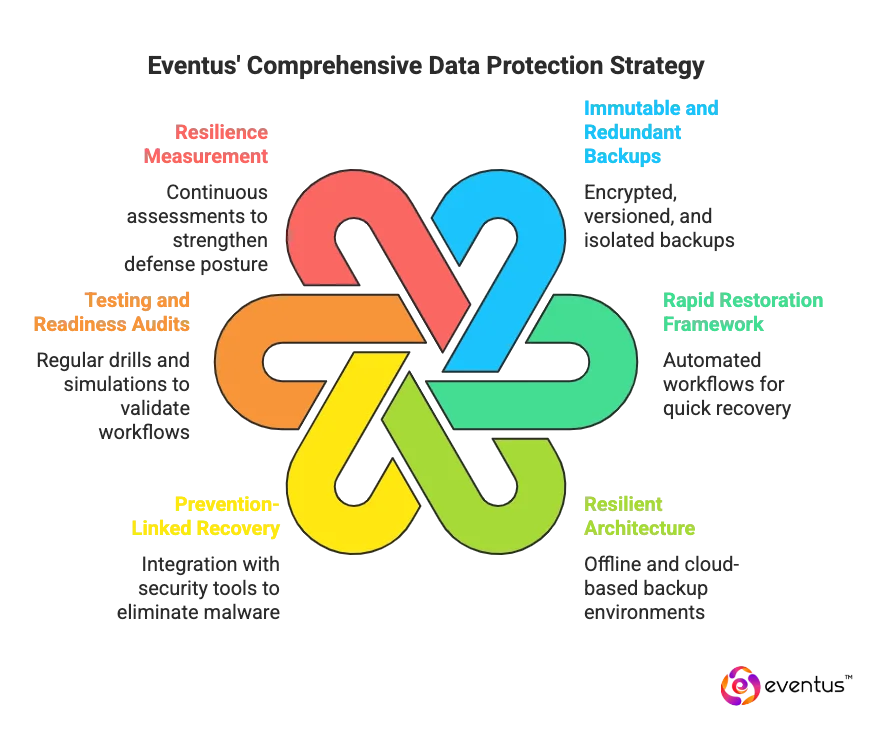
Key data protection and recovery measures include:
- Immutable and Redundant Backups: Eventus maintains encrypted, versioned, and isolated backups following industry ransomware defense standards to guarantee that data remains untouched even when ransomware attackers attempt to encrypt systems.
- Rapid Restoration Framework: Automated workflows ensure businesses can recover from a ransomware attack within defined recovery time objectives (RTOs), protecting applications and data vital to operations.
- Resilient Architecture: Offline and cloud-based backup environments provide data continuity during a security incident, ensuring minimal downtime for the organization against ransomware.
- Prevention-Linked Recovery: Integration with security tools and monitoring platforms allows Eventus to trace and eliminate malware sources before restoring data, reducing reinfection risk.
- Testing and Readiness Audits: Regular recovery drills, audits, and simulations validate recovery workflows and ensure every action to take is documented and tested under real-world ransomware scenarios like WannaCry.
- Resilience Measurement: Continuous ransomware resilience assessments and forensic reviews strengthen long-term defense posture, helping to improve resilience and maintain trust with every stakeholder.
How Does Eventus Detect and Respond to Ransomware Threats in Real Time?
Eventus detects and responds to ransomware threats in real time by integrating automated detection, behavioral analytics, and human-led response orchestration into one adaptive system—backed by AI driven cloud SOC, SOCaaS, and managed SOC services that ensure early identification, rapid containment, and complete recovery.
Core detection and response mechanisms include:
- Behavioral and Anomaly Detection: Eventus continuously monitors system and network behavior to identify suspicious patterns that indicate ransomware activity, such as mass file encryption or privilege escalation.
- Real-Time Threat Intelligence: Leveraging the latest security intelligence feeds, Eventus correlates alerts from multiple data sources to detect ransomware variants before they spread.
- Automated Incident Response: Once a ransomware is a type of encryption-based attack is detected, automated playbooks isolate infected systems, terminate malicious processes, and prevent lateral movement—helping protect against ransomware instantly.
- Containment and Recovery Actions: Eventus executes the essential steps to mitigate active threats, restore integrity, and ensure systems are not left vulnerable to ransomware reinfection.
- Continuous Learning and Resilience Building: Post-incident analysis and telemetry-driven improvements strengthen your ransomware defense framework and build a strong, adaptive response capability across the enterprise.
How Do People and Processes Strengthen Ransomware Resilience at Eventus?
People and processes are central to how Eventus builds true ransomware resilience, and its role as a managed security service provider helps teams operate with the knowledge, structured workflows, and compliance-driven processes needed to stay protected against ransomware and maintain continuity under pressure.
Key enablers include:
- Employee Awareness and Training: Regular sessions educate staff on phishing tactics, social engineering, and steps to prevent ransomware incidents, reducing the likelihood of users becoming vulnerable to ransomware.
- Defined Incident Response Roles: Clearly assigned responsibilities ensure every team member knows the essential steps to take during a ransomware event, minimizing confusion and response delays.
- Standardized Security Processes: Eventus follows globally recognized ransomware prevention and governance frameworks to ensure consistency, traceability, and accountability in every action.
- Continuous Improvement Culture: Lessons learned from real-world events are integrated back into policies, refining both human and procedural defenses to build a strong and adaptive security posture.
- Compliance and Risk Management: Regular audits and reviews align organization’s security with the latest security and regulatory requirements, maintaining resilience even as threats evolve.
How Does Eventus Help Organizations Recover and Build Long-Term Resilience?
Eventus helps organizations recover and build long-term resilience through structured restoration, data integrity, and adaptive defense mechanisms that evolve after every incident, strengthened by an AI driven SOC as a service model that aligns technology, governance, and continuous learning to sustain true ransomware resilience over time.
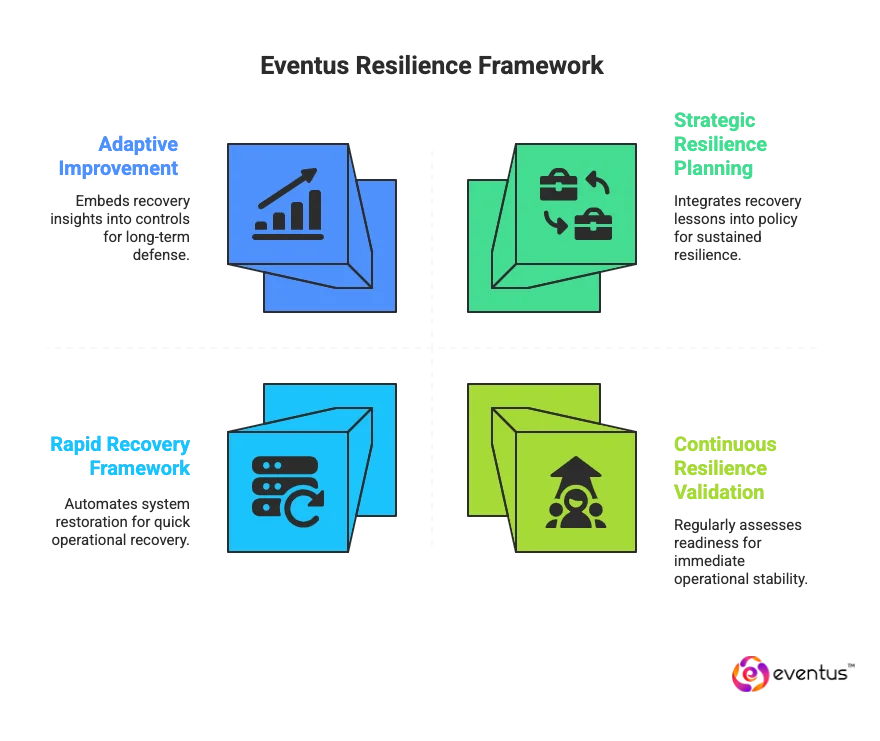
Key recovery and resilience enablers include:
- Rapid Recovery Framework: Automated restoration of systems and applications ensures quick return to normal operations after any ransomware is a type of encryption-based disruption.
- Post-Incident Forensics: Detailed analysis of infection vectors strengthens security posture and eliminates vulnerabilities that could lead to recurrence.
- Adaptive Improvement: Insights from every recovery are embedded into new controls and processes to strengthen your ransomware defense strategy.
- Continuous Resilience Validation: Regular resilience assessments and restoration drills confirm long-term readiness and operational stability.
- Strategic Resilience Planning: Eventus integrates recovery lessons into organizational policy and compliance workflows, ensuring sustained resilience and business continuity.
This combination makes Eventus highly competitive among the best SOC as a service provider companies.
FAQs
Q1. What types of organizations benefit most from the Eventus ransomware resilience approach?
Eventus is designed for mid-market and enterprise organizations that rely on always-on operations, regulated data, or complex hybrid environments. Sectors such as financial services, healthcare, manufacturing, and SaaS providers benefit most because they face higher ransomware risk and stricter uptime and compliance requirements.
Q2. How does Eventus work with our existing security tools and IT team?
Eventus integrates with your existing security stack (SIEM, EDR, firewalls, backup platforms) rather than replacing everything on day one. Your internal IT and security teams remain decision-makers, while Eventus SOC analysts provide 24/7 monitoring, playbooks, and incident handling to close coverage gaps and standardize response.
Q5. Can Eventus help if we have already experienced a ransomware incident?
Yes. Eventus can engage after an incident to contain residual threats, validate that the environment is clean, and coordinate safe recovery from known-good backups. The team then runs a post-incident review to identify root causes and implement controls that reduce the likelihood and impact of future ransomware events.
Q6. How does Eventus support cyber insurance and regulatory compliance during ransomware events?
Eventus maintains detailed incident timelines, evidence, and reports that align with typical cyber insurance and regulator expectations. This documentation helps you demonstrate due diligence, prove that controls and playbooks were followed, and speed up both insurance claims and mandatory breach notifications where required.
Q7. What KPIs does Eventus use to measure ransomware resilience over time?
Key ransomware resilience KPIs include mean time to detect (MTTD), mean time to respond (MTTR), percentage of critical assets covered, backup recovery time against RTOs, and the number of high-risk exposures closed per month. Tracking these metrics shows whether your organization is becoming harder to compromise and faster to recover.