Eventus Security’s SOC as a Service (SOCaaS) delivers real-time visibility across your environment, turning raw alerts into investigated, contained, and remediated incidents. The platform is built to detect, prioritize, and contain threats quickly, manage remediation and recovery, and continuously refine detections and playbooks for better outcomes over time. Positioned alongside leading SOC as a service providers, Eventus SOCaaS helps enterprises achieve measurable resilience and a proactive security posture without building or staffing an in-house SOC.
Table of Contents
What Is Real-Time Threat Visibility in Eventus SOCaaS?
Real-time threat visibility in Eventus SOCaaS represents the continuous capability of the Security Operations Center (SOC) to detect, analyze, and respond to potential cyber threats the moment they emerge. Through an AI-powered framework that combines machine learning, advanced analytics, and security information and event management (SIEM).
Eventus Security provides instant awareness across endpoints, networks, and cloud environments. This integration allows them best SOC provider companies to correlate high-volume security events, transform them into actionable insights, and enable security analysts to identify anomalies faster.
By leveraging threat intelligence and automated data enrichment—while maintaining alignment with each organization’s privacy policy—Eventus ensures that businesses maintain complete situational awareness and reduce their mean time to detect (MTTD) significantly.
How Does Eventus SOCaaS Detect Threats in Real Time?
Here’s how:
- Continuous Monitoring: Eventus SOCaaS constantly monitors endpoints, networks, and cloud environments to detect anomalies and suspicious behaviors as they occur, reinforcing its role as a trusted managed soc services provider committed to proactive threat detection and response.
- AI-Powered Threat Detection: Advanced AI and machine learning models identify patterns, deviations, and unusual activities that traditional tools may miss, improving real-time accuracy.
- Contextual Correlation: The SOC correlates data from multiple sources using security information and event management (SIEM) and threat intel to expose complex attack chains and insider risks.
- Alert Prioritization: Intelligent filtering and scoring reduce false positives by ranking alerts based on contextual risk, allowing security analysts to focus on genuine, high-impact threats.
- Automated Playbooks: Predefined playbooks automate response workflows such as isolating endpoints, revoking credentials, or blocking malicious IPs, enabling faster containment.
- Proactive Threat Detection: Eventus’s managed security service detects emerging threats and potential attack vectors early, strengthening enterprise-grade security without the need for an in-house SOC through its AI-driven SOC as a Service model.
- Integrated Analytics and Reporting: Built-in analytics provide actionable insights into cybersecurity operations, improving visibility, compliance, and overall security posture.
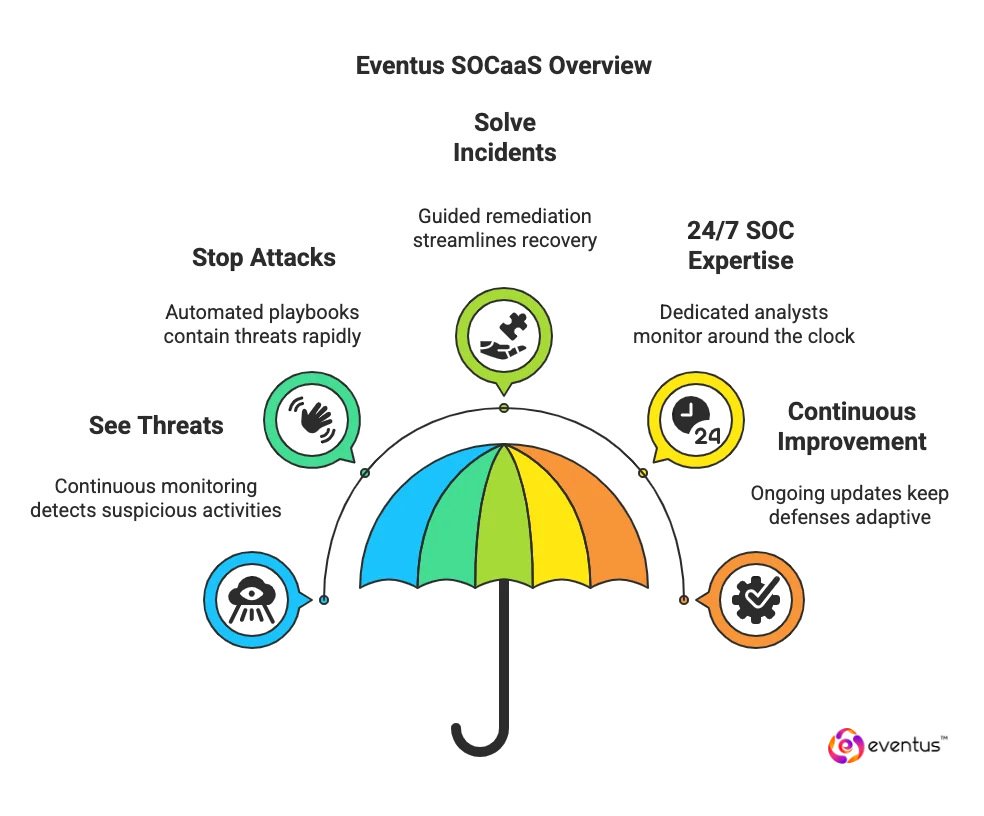
Eventus SOCaaS: See, Stop, and Solve Threats in Real Time
Eventus SOCaaS empowers you to manage cybersecurity threats efficiently and effectively:
| Capability | What It Does | Real-Time Benefit |
| See Threats | Continuous monitoring powered by AI and analytics across all IT environments. | Instantly detects suspicious activities and early threats. |
| Stop Attacks | Automated playbooks and expert analysis contain threats rapidly. | Prevents lateral movement and reduces breach impact. |
| Solve Incidents | Guided remediation, forensic analysis, and compliance reporting streamline recovery. | Speeds incident resolution and strengthens security posture. |
| 24/7 SOC Expertise | Dedicated security analysts monitor and investigate around the clock. | Ensures threats are addressed promptly, day or night. |
| Continuous Improvement | Ongoing updates to detection rules, playbooks, and threat intelligence. | Keeps defenses adaptive against emerging threats. |
How Does Eventus SOCaaS Prioritize and Investigate Threats?
Eventus SOCaaS prioritizes and investigates threats through an intelligent, multi-layered process that combines AI-driven analytics, expert review, and automated security tools. Each alert is evaluated based on its severity, impact, and alignment with the organization’s risk profile to ensure genuine threats are addressed first. By integrating real-time correlation, contextual data, and cybersecurity solutions, the SOC as a Service (SOCaaS) model minimizes noise and focuses efforts on incidents that pose the highest risk to the enterprise.
Here’s how:
- Automated Alert Prioritization: Eventus uses AI models to rank and filter alerts by risk level, enabling security experts to act quickly on verified advanced threats.
- Context-Aware Investigation: Each threat is analyzed using security measures that factor in user behavior, endpoint activity, and potential data exposure.
- Threat Correlation and Enrichment: The system correlates alerts with threat monitoring data and known threats targeting the organization to validate authenticity.
- Analyst-Led Validation: Skilled cybersecurity talent in the SOC conducts in-depth analysis of high-priority cases, confirming impact and attack scope before escalation.
- Data-Driven Escalation: Confirmed incidents trigger real-time detection and response workflows designed to contain and mitigate risk across the infrastructure.
- Compliance and Audit Alignment: Every investigation supports data security and compliance requirements, ensuring that organization’s security posture remains resilient and audit-ready.
How Does Eventus Respond to and Contain Detected Threats?
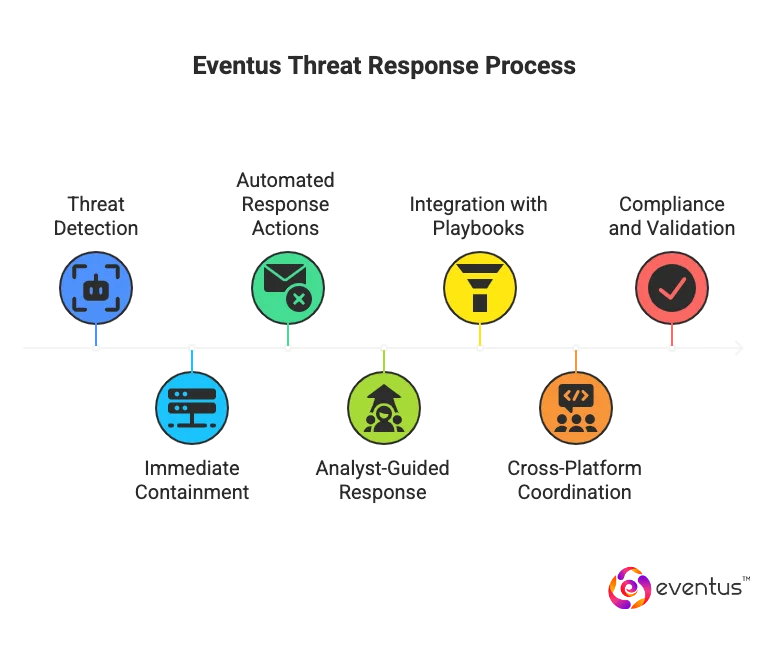
Eventus SOCaaS responds to and contains detected threats through a structured, automation-driven process designed to reduce damage and restore organizational security quickly. As a SOCaaS provider, Eventus Security integrates AI-driven threat detection and response with expert-led decision-making as part of its managed SOC services to neutralize complex cyber threats efficiently and in compliance with enterprise security requirements.
Here’s how:
- Immediate Containment: Upon detection, predefined response workflows isolate affected systems, endpoints, or user accounts to prevent lateral movement and stop the spread of malicious activity.
- Automated Response Actions: Automated processes execute key mitigation steps such as disabling compromised credentials, blocking malicious IPs, and enforcing updated security configurations.
- Analyst-Guided Response: Experienced cybersecurity analysts assess the scope of the incident and determine corrective measures tailored to the organization’s existing security setup.
- Integration with Playbooks: Structured response security solutions guide containment and remediation procedures, ensuring alignment with internal security policies.
- Cross-Platform Coordination: The SOC coordinates with client systems and tools to address threats like malware outbreaks, insider misuse, or unauthorized access in real time.
- Compliance and Validation: Each containment action adheres to data protection and compliance standards, supporting robust security and long-term resilience.
How Does Eventus Manage Remediation and Recovery After an Incident?
Eventus SOCaaS manages remediation and recovery through a structured, intelligence-driven process that ensures rapid restoration and long-term resilience. The Eventus platform integrates cyber security expertise, automation, and continuous validation to eliminate residual risks while restoring normal operations.
Here’s how:
- Root Cause Identification: The SOC team investigates each incident’s origin to identify exploited vulnerabilities, compromised accounts, or misconfigurations within the organization’s security environment.
- Vulnerability Patching: Detected weaknesses are fixed promptly through coordinated remediation steps that align with enterprise security needs and system dependencies.
- System Restoration: Affected systems are rebuilt or restored from trusted backups, ensuring modern cybersecurity integrity and minimizing operational downtime.
- Validation and Testing: Restored assets undergo security validation to confirm the absence of persistence mechanisms or hidden backdoors before reintroduction to the network.
- Compliance Alignment: Every remediation step supports data protection and security requirements, maintaining adherence to organizational and regulatory standards.
- Post-Recovery Hardening: Eventus applies additional security measures and configuration updates to reinforce long-term defenses and prevent recurrence.
How Does Eventus Ensure Continuous Improvement Post-Remediation?
Eventus ensures continuous improvement post-remediation by implementing a feedback-driven approach that strengthens security operations and prepares organizations for future challenges. Through its managed service model, Eventus Security performs ongoing evaluation and refinement of tools, processes, and detection mechanisms to maintain peak efficiency and accuracy.
Here’s how:
- Post-Incident Review: Every resolved incident undergoes an in-depth analysis to identify gaps in response, containment, or application security controls.
- Rule and Playbook Optimization: Detection rules, correlation logic, and automated playbooks are updated to adapt to new insider threats and evolving attack methods.
- Performance Assessment: The SOC continuously measures incident handling metrics and compares them with current security benchmarks to enhance operational outcomes.
- Knowledge Integration: Lessons learned from investigations are added to Eventus’s central intelligence base, improving predictive threat detection and response capabilities.
- Client Collaboration: Eventus shares insights and recommendations to align the organization’s evolving needs with the best practices of modern cybersecurity.
Why Choose Eventus SOCaaS for Your Security Operations?
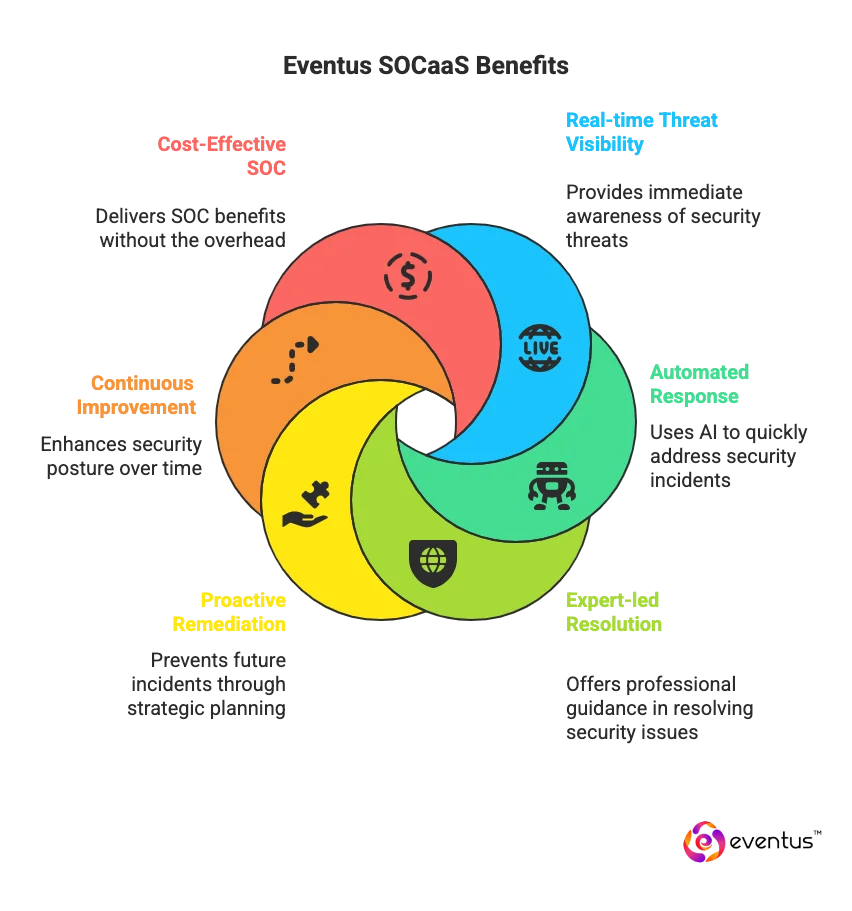
Eventus SOCaaS empowers organizations to stay ahead of attackers with continuous monitoring, rapid response, and expert-led incident resolution. By combining advanced AI, LLM-powered analytics, and dedicated SOC professionals, Eventus delivers the real-time visibility and protection modern businesses need.
By partnering with Eventus, your organization gains:
- Real-time, AI-powered threat visibility and detection
- Automated and expert-led response and containment
- Proactive remediation and incident recovery
- Continuous improvement of your cybersecurity posture
- The benefits of a fully staffed SOC without the overhead
If you’re ready to strengthen your cybersecurity posture and eliminate blind spots, Eventus SOCaaS provides an end-to-end solution built for today’s threat landscape. Contact Eventus Experts Today: - https://eventussecurity.com/contact-us/
FAQ’s.
Q1. Is container orchestration necessary if I only run a few containers?
If you run fewer than 5–10 containers on a single host, basic Docker commands or simple scripts are usually enough. Orchestration becomes useful when you add multiple nodes, need high availability, or roll out updates frequently.
Q2. Can I use containers in production without Kubernetes?
Yes. You can run production workloads with Docker on a single server or lighter tools like Docker Swarm, but once you need cluster-level scaling, self-healing, and consistent rollouts, most teams adopt Kubernetes or another orchestration platform.
Q3. Does container orchestration only work in the cloud?
No. Container orchestration runs on on-premises, private cloud, and public cloud. Many organizations use a hybrid model with the same orchestrator (such as Kubernetes) across physical hardware and cloud providers.
Q4. Can stateful applications run under container orchestration?
Yes. Stateful apps run under orchestration using persistent volumes, storage classes, and patterns like StatefulSets. The main requirement is explicit design for data durability, backups, and failover.
Q5. How does container orchestration affect cloud costs?
Orchestration can reduce costs by bin packing workloads and scaling replicas down when demand drops. Misconfigured autoscaling, oversized requests, or idle clusters, however, can increase spend, so cost management remains essential.
Q6. What skills do teams need to operate container orchestration safely?
Teams need strong Linux, networking, and containerization fundamentals. For Kubernetes, they also need familiarity with YAML, RBAC, namespaces, and monitoring and troubleshooting clusters and workloads.
Q7. Is container orchestration suitable for regulated or security-sensitive environments?
Yes, if implemented with strict security controls such as hardened base images, tight RBAC, network policies, audit logging, and integration with enterprise IAM and secrets management to meet compliance requirements.