SOC as a Service has evolved into a comprehensive, outcome-driven model in 2025 that goes far beyond monitoring. This article examines what businesses should expect from the best SOC providers companies today, covering capabilities such as advanced threat detection, AI-driven response, and automation. It also explores platform architecture, integrations, compliance, governance, measurable security outcomes, pricing, and preparation for future directions. By outlining these key themes, the article provides organizations with a clear roadmap for evaluating and adopting SOCaaS effectively.
Table of Contents
What is the scope and purpose of SOC as a service in 2025?
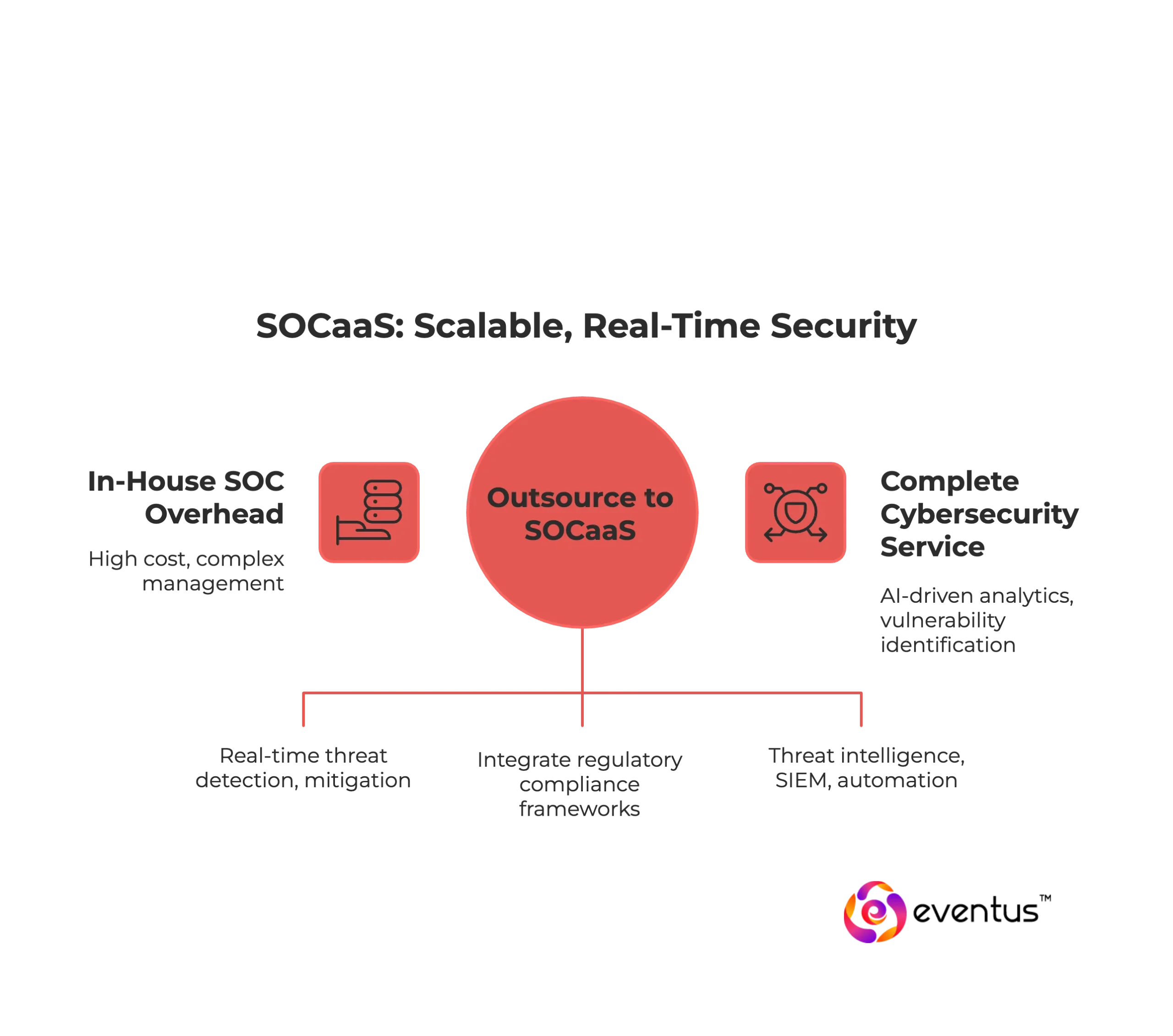
The scope and purpose of SOC as a Service (SOCaaS) in 2025 is to give businesses scalable, real-time, and proactive security operations without the overhead of running an in-house SOC. This model allows organizations to outsource cybersecurity monitoring, threat detection, and incident response to a specialized SOCaaS provider that leverages advanced analytics, machine learning, and automation.
The main purpose is threefold:
- Strengthen cyber defense: SOC security services offer continuous monitoring, real-time threat detection, and advanced threat hunting that help businesses proactively mitigate risks and remediate security incidents.
- Simplify compliance: Best SOC Providers integrate regulatory compliance frameworks (HIPAA, GDPR, PCI-DSS) into their services, enabling evidence-based reporting and governance.
- Address evolving security needs: By combining threat intelligence, SIEM, and cutting-edge technologies, SOCaaS providers evolve with the cyber threat landscape, ensuring organizations stay ahead of cyberattacks.
In 2025, the scope of managed soc as a service has expanded beyond traditional monitoring to include AI-driven analytics, vulnerability identification, and automation-led remediation, positioning SOCaaS as a complete cybersecurity service rather than a support function. The purpose is to help companies meet regulatory compliance, reduce exposure to cyber threats, and replace fragmented security solutions with a unified, managed service operated by experienced security analysts.
How Is SOC As A Service Defined And Positioned In The Market?
Best Managed Security Service Provider is a provider-run security operations center that delivers 24×7 monitoring, detection and response, threat hunting, and incident management across endpoints, cloud, network, and identities. Positioned as an outcome-focused alternative to in-house SOCs, it is evaluated on detection performance, integrations, reporting, and compliance support. Core capabilities include centralized log ingestion, detection engineering mapped to MITRE ATT&CK, real-time alerting, threat intelligence, incident response, automation via SOAR playbooks, compliance reporting, and integrations with key security tools.
Which advanced capabilities differentiate leading Best SOC providers?
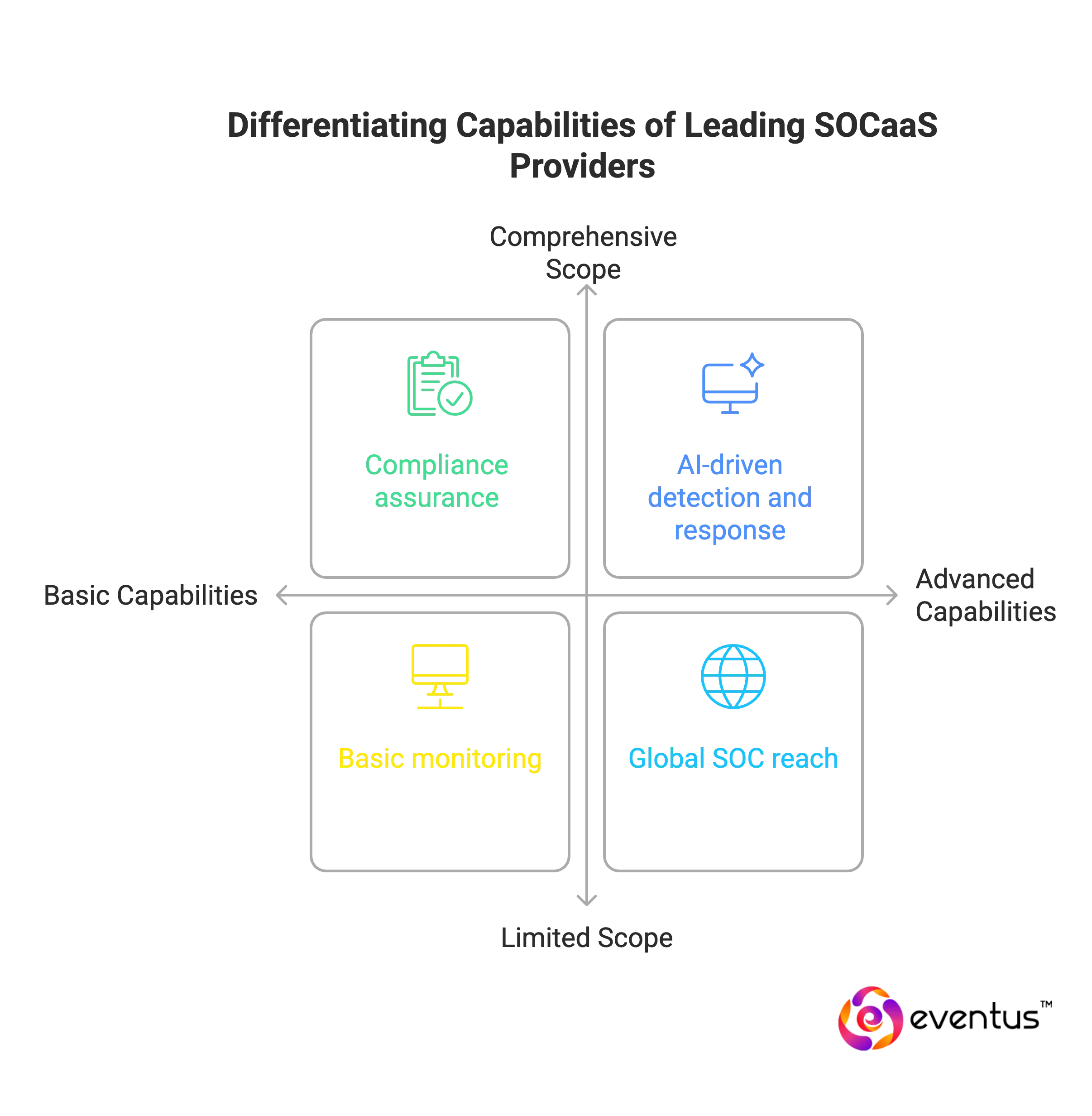
Leading SOC as a Service providers distinguish themselves by going beyond baseline monitoring and incident response. Their advanced capabilities are positioned as best practices in the cybersecurity field and reflect compliance with industry standards. The following differentiators define the soc as service provider in india companies:
- AI-driven detection and response: Leading SOCaaS providers use ai driven soc and advanced analytics and machine learning to detect sophisticated threats faster than traditional methods.
- Scalable architecture: Services are designed to scale with business growth, allowing organizations to avoid the limitations of managing an in-house SOC.
- Cloud-native coverage: Advanced Managed SOC operations integrate telemetry from SaaS, cloud, and hybrid environments, addressing modern attack surfaces.
- Automation and orchestration: Trusted Managed SOC providers implement SOAR playbooks that automate containment, enabling reliable SOC operations with reduced manual overhead.
- Global SOC reach: Leading SOCaaS companies operate global SOC centers with follow-the-sun coverage to respond to cybersecurity incidents in real time.
- Compliance assurance: Services include tailored compliance packages to align with HIPAA, GDPR, PCI-DSS, and other regulatory standards.
- Consulting services: SOC Providers complement managed cybersecurity services with advisory input, helping clients choose the right SOC model and implement best practices.
Additional services: Managed SOC services are designed to integrate vulnerability management, exposure monitoring, and attack surface reduction alongside core detection.
What platform architecture and integrations should you expect?
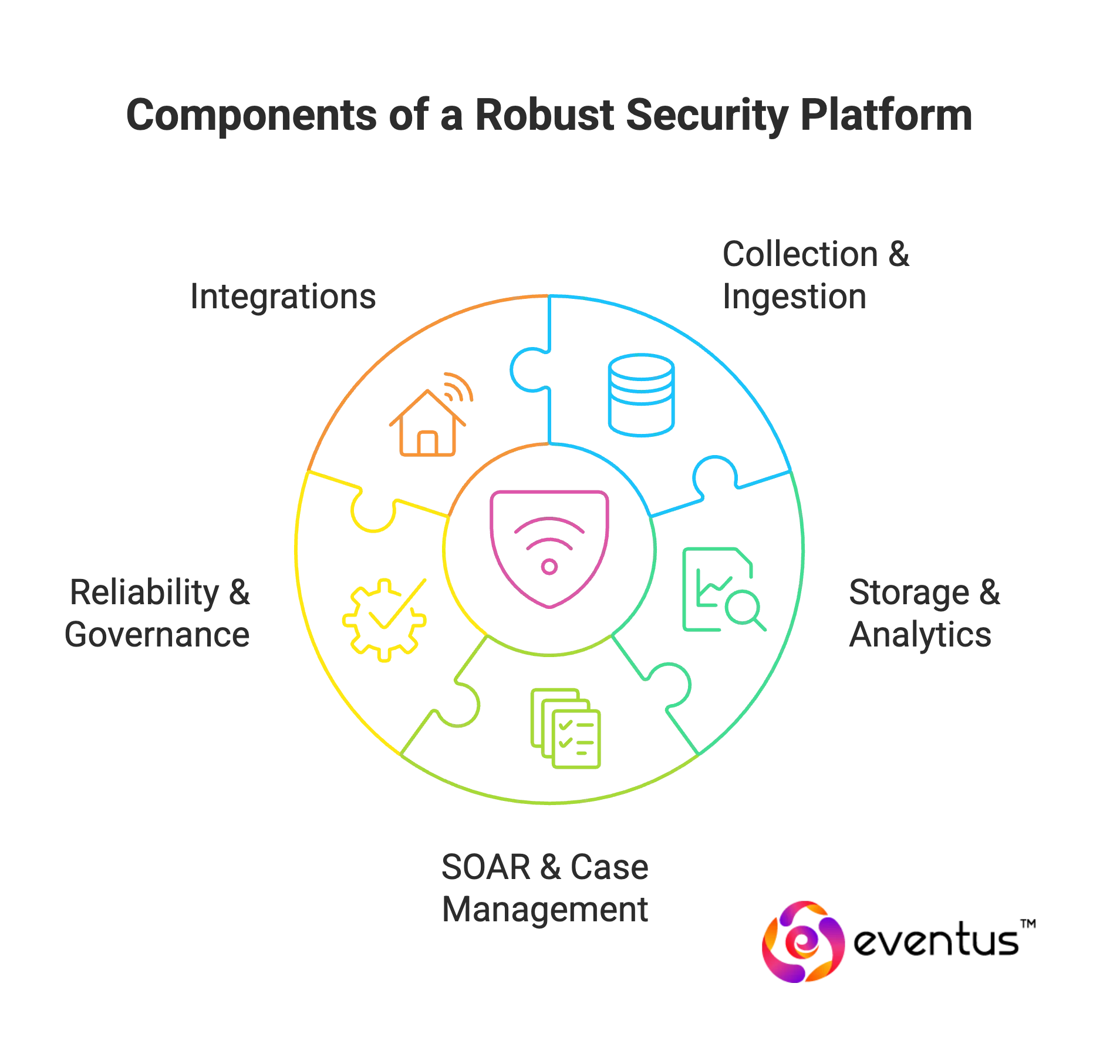
A robust managed security service provider solutions platform uses modular, multi-tenant architecture with secure pipelines and integrations. Core elements include:
- Collection & Ingestion – agents, APIs, syslog; normalized and enriched telemetry.
- Storage & Analytics – tiered retention, ATT&CK-mapped detections, UEBA, SIEM-grade correlation.
- SOAR & Case Management – automated playbooks, evidence handling, RBAC controls.
- Reliability & Governance – autoscaling, DR, tamper-proof logging, compliance reporting.
- Expected Integrations: EDR/XDR, IdPs, AWS/Azure/GCP, SaaS/email tools, firewalls/NDR, vulnerability scanners, ITSM systems, collaboration platforms, and threat intelligence feeds.
How do Best SOC providers approach detection engineering and content quality?
Best SOC Providers handle detection engineering and content quality through a disciplined lifecycle that produces reliable, low-noise detections and clear operational guidance.
- Maintain a versioned use-case library mapped to MITRE ATT&CK with test cases.
- Build rules with clear logic, prerequisites, severity, and suppression criteria.
- Validate via tests, attack replays, and red/purple team exercises.
- Continuously tune using triage feedback and false-positive reviews, targeting precision and faster detection.
- Provide runbooks with investigation steps, queries, and containment actions.
- Include data dictionaries, mappings, and release notes for each update.
- Enforce code reviews, approval gates, and rule health metrics.
- Localize content to customer environments.
How are response operations and service levels defined?
Response operations and service levels are defined through a clear operating model, measurable targets, and audited workflows that bind the provider and your team to specific outcomes.
- Severity Model – Clear P1–P4 definitions with impact criteria and required actions.
- SLAs/SLOs – Time-bound targets (e.g., P1 acknowledge ≤10 min, investigation ≤15 min, containment ≤60 min).
- Runbooks/Playbooks – Versioned procedures with decision trees, rollback, and human approvals.
- Escalation – Named on-call tiers, duty rotations, and executive escalation rules.
- Communication – Secure channels, ticket timestamps, exec summaries, and post-incident briefs.
- Containment/Remediation – Preapproved actions (isolate host, disable account, revoke token, block IOC).
- Evidence & Compliance – Forensic snapshots, immutable logs, mapped controls, retention policies.
- Automation Guardrails – SOAR playbooks with scope limits, approvals, and audit trails.
- Co-Managed RACI – Defined roles for provider analysts, internal teams, and app owners.
- Reporting & Improvement – Monthly SLA scorecards, KPIs, and corrective actions.
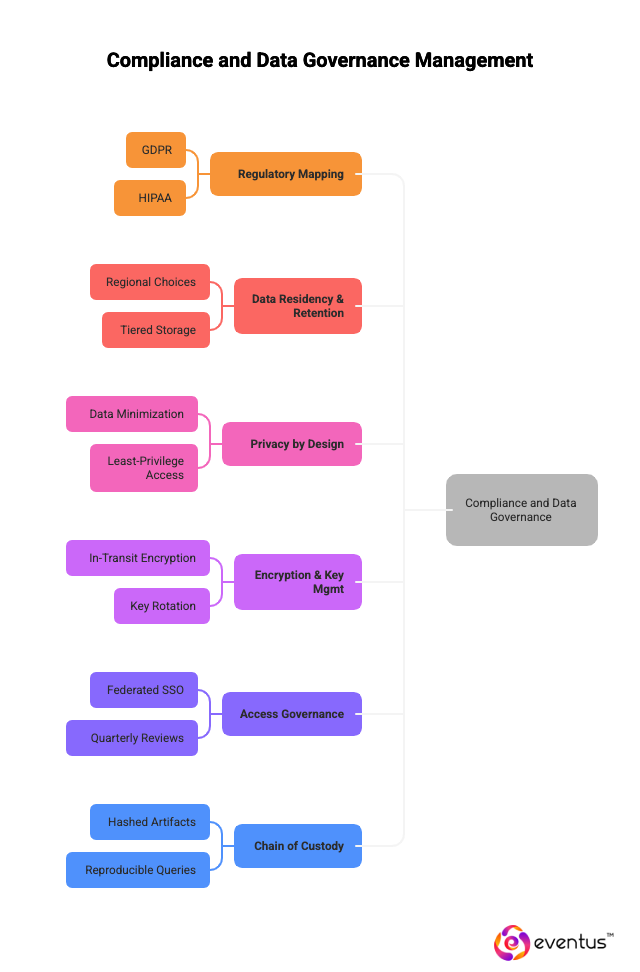
How are compliance and data governance managed?
- Regulatory Mapping – Controls aligned to GDPR, HIPAA, PCI DSS, ISO 27001, SOC 2; audit evidence provided.
- Data Residency & Retention – Regional choices, tiered storage, immutability/WORM for forensics.
- Privacy by Design – Data minimization, masking, tokenization, least-privilege access.
- Encryption & Key Mgmt – In-transit/at-rest encryption, BYOK, key rotation, tamper-evident logs.
- Access Governance – Federated SSO, MFA, just-in-time access, quarterly reviews.
- Chain of Custody – Hashed artifacts, timestamps, reproducible queries for investigations.
- Cross-Border Transfers – Safeguards (SCCs), vendor risk assessments, disclosure.
- Breach Notification – Jurisdiction-aware timelines, regulator/customer templates, dashboards.
- Policy & Change Mgmt – Versioned policies, SDLC controls, peer-reviewed updates.
- Ongoing Assurance – Independent audits, pen tests, continuous monitoring, corrective actions.
How are security outcomes measured and improved?
Measuring Security Outcomes
- MTTD/MTTR – detection, response, and containment times by severity.
- Alert Fidelity – precision, false-positive rate, analyst validation.
- Coverage – log source onboarding, ATT&CK coverage, control efficacy.
- Incident Quality – P1/P2 cases with full evidence and corrective actions.
- Risk Reduction – vuln backlog burn-down, exposure windows, repeat incidents.
- Service Adherence – SLA/SLO attainment, investigation and notification timeliness.
- Business Alignment – audit pass rates, RTO adherence, incidents per asset, cost per incident.
Improvement Methods
- Post-incident reviews with tracked remediation tasks.
- Rule health dashboards and peer-reviewed updates.
- Threat-led validation (purple team, attack replay).
- Hypothesis-driven hunts and curated threat intel.
- SOAR playbook tuning with guardrails and rollback.
- Quarterly reviews to expand telemetry and align to business risk.
How are pricing and packaging models structured?
| Dimension | Details |
| Pricing Drivers | Per asset (endpoints, servers, identities); data volume (GB/day, EPS); scope multipliers (cloud, sites, apps); response scope (IR hours, surge rates); retention & compliance (storage tiers, attestations); geography (regional hosting); implementation (onboarding fees). |
| Packaging Models | Monitoring & Triage – 24×7 alerting, case mgmt, starter containment.
MDR Bundle – Detection & response with EDR/XDR, SOAR basics, monthly reports. Full SOCaaS – SIEM, SOAR, hunting, threat intel, compliance, SLAs. Co-Managed – Shared console/ticketing; provider manages detections. Add-ons – DFIR, vuln mgmt, phishing sims, red/purple team, exec dashboards. |
| Contract Mechanics | 12–24 month terms; phased onboarding; true-ups; usage caps with transparent overages; SLA tiers by package; quarterly reviews for scope/integration changes. |
How should organizations prepare for future directions?
Organizations should prepare by building capabilities that track where soc security services is heading and by setting measurable targets.
- AI and analytics readiness: Establish a curated data lake for security with labeled incidents to train and validate ML detections. Target ≥90% timestamp integrity and ≤1% schema error rate across sources.
- Identity-first defense: Enforce strong identity telemetry (SSO, IdP, PAM). Require containment actions (disable account, revoke token) to be executable via playbooks within ≤15 minutes for P1 events.
- Cloud-native coverage: Onboard CSP logs, posture APIs, and runtime telemetry across AWS, Azure, and GCP. Aim for ≥95% onboarding of critical cloud accounts and Kubernetes clusters.
- Automation with guardrails: Convert top 10 incident types into SOAR playbooks with human approval for high-impact steps. Measure ≥30% reduction in handling time without increased error rate.
- Detection content as a product: Maintain a versioned use-case library mapped to ATT&CK with unit tests and release notes. Retire rules with precision <60% and document replacements.
- Continuous exposure management: Integrate vulnerability, attack-surface, and asset inventories with case management. Burn down exploitable criticals by ≥80% within 30 days.
- Threat-led validation: Run quarterly purple-team exercises and replay real attack traces. Track MTTD and MTTR improvements per exercise and update runbooks within five business days.
- Compliance by design: Lock data residency, retention tiers, and BYOK/CMK before go-live. Produce monthly evidence packs and complete quarterly access reviews with 100% closure.
- Incident readiness and forensics: Pre-approve isolation, credential resets, and token revocations. Ensure forensic collection can start ≤60 minutes from P1 declaration with chain-of-custody.
- Metrics and governance: Operate a detection health dashboard (precision, volume impact, rule age). Hold monthly KPI reviews and quarterly roadmap sessions tied to business risks.
- Talent and operating model: Define a co-managed RACI, enabling internal analysts to run vetted playbooks while the provider owns detection engineering and tuning.
- Vendor strategy and portability: Require rule export, data egress, and decommission plans to avoid lock-in. In most engagements the service is subscription based, so align term, usage caps, and exit criteria up front.
FAQs
Q1. What is SOC as a Service in 2025?
SOC as a Service delivers outsourced 24×7 monitoring, detection, and response with AI, automation, and compliance frameworks, reducing the need for in-house SOCs.
Q2. How does SOCaaS differ from MDR?
MDR focuses mainly on detection and response, while SOCaaS offers a broader service including SIEM, SOAR, vulnerability management, and compliance reporting.
Q3. What advanced features do Best SOC providers include?
Leading providers deliver AI-driven analytics, global SOC coverage, cloud-native telemetry, automated playbooks, and tailored compliance support.
Q4. How are SOCaaS services priced?
Pricing is usually subscription-based, structured around endpoints, data volume, scope, and compliance needs, with add-ons like DFIR or vulnerability management.
Q5. How should organizations prepare for SOCaaS adoption?
They should align data governance, identity monitoring, cloud coverage, automation playbooks, and exit strategies to ensure scalability and compliance readiness.