This article explains what breach and attack simulation (BAS) is and why it matters. You’ll learn how BAS works; the benefits; how it compares to penetration testing and red teaming; which security controls and attack vectors it exercises; how to map results to MITRE ATT&CK and other frameworks; best practices to implement BAS; how to measure effectiveness with KPIs such as block and detection rates, MTTD and MTTR; safety considerations; typical pricing; integrations with your stack; who should use BAS; and key FAQs
Table of Contents
What is breach and attack simulation (BAS)?
Breach and attack simulation (BAS) is a cybersecurity methodology that enables organizations to emulate real-world attack scenarios in a controlled environment to assess and improve their defenses. Unlike a one-time penetration test or red team engagement, BAS platforms run continuous and automated simulations, providing ongoing visibility into the effectiveness of security controls and enabling rapid remediation of weaknesses.
A BAS solution uses attack simulation tools to replicate the tactics, techniques, and procedures (TTPs) of real attackers across multiple attack vectors—including phishing, malware delivery, lateral movement, privilege escalation, and data exfiltration. These simulations validate how well an organization’s security posture can detect, respond to, and block adversarial activity.
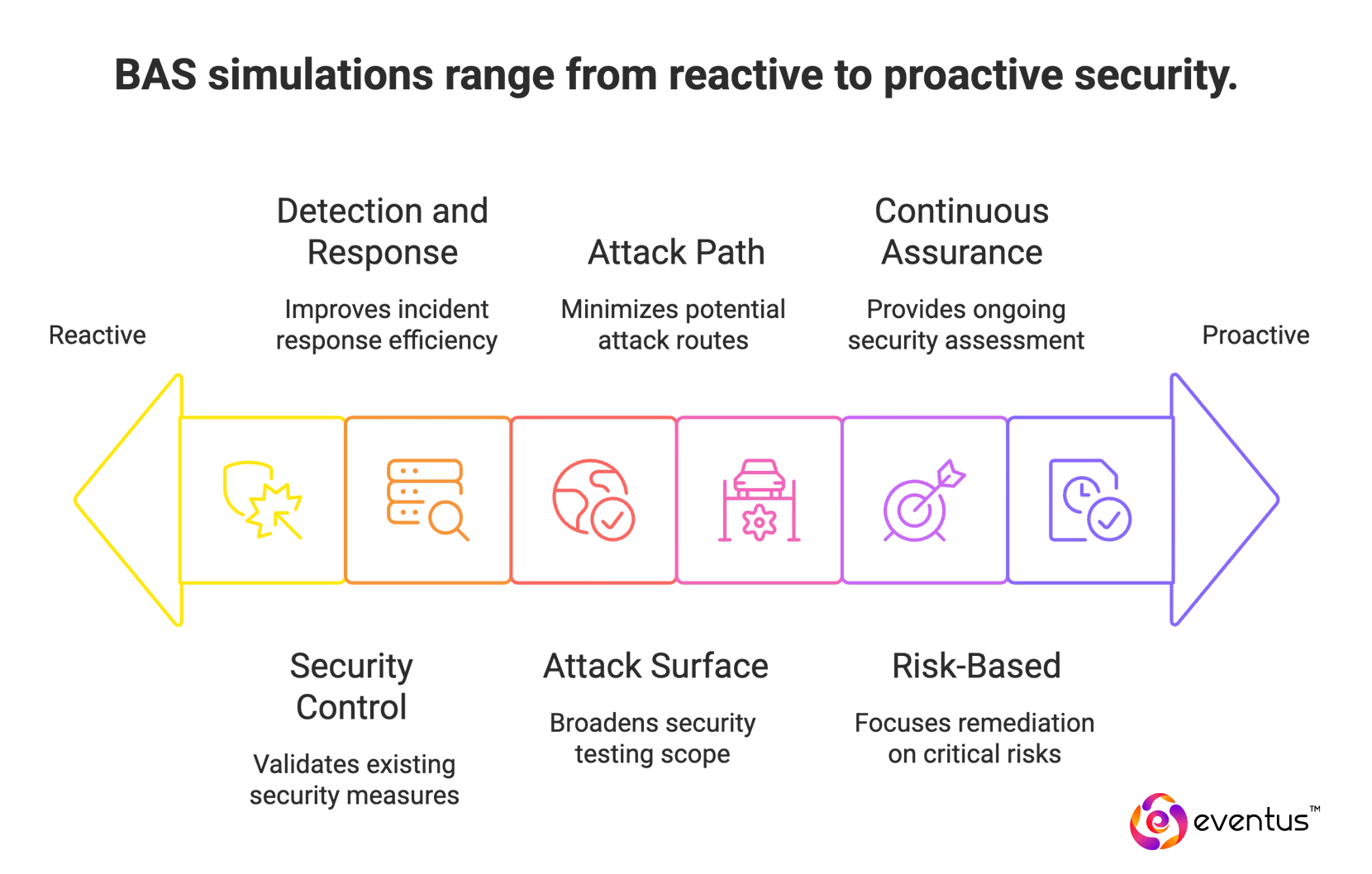
What is the objective of BAS simulations?
Simulate real-world attack vectors across your attack surfaces to validate security controls, quantify detection and response, and help the security team prioritize remediation by cyber risk. BAS tools deliver continuous and automated security testing integrated with security operations.
- Security control validation — block rate (%), detection rate (%), false-negative rate (%), misconfigurations fixed (count)
- Detection and response — MTTD, MTTR, alert precision (%), escalation success (%)
- Attack surface coverage — critical assets covered (%), segments tested (count)
- Attack path reduction — viable attack paths closed (count), lateral hops (count), privilege-escalations removed (count)
- Risk-based prioritization — high-risk vulnerability backlog reduction (%), time to mitigate (days)
- Continuous assurance and reporting — simulations per week (count), coverage trend (%), drift events detected/remediated (count), pass/fail by control, framework mapping (count)
How does breach and attack simulation work?
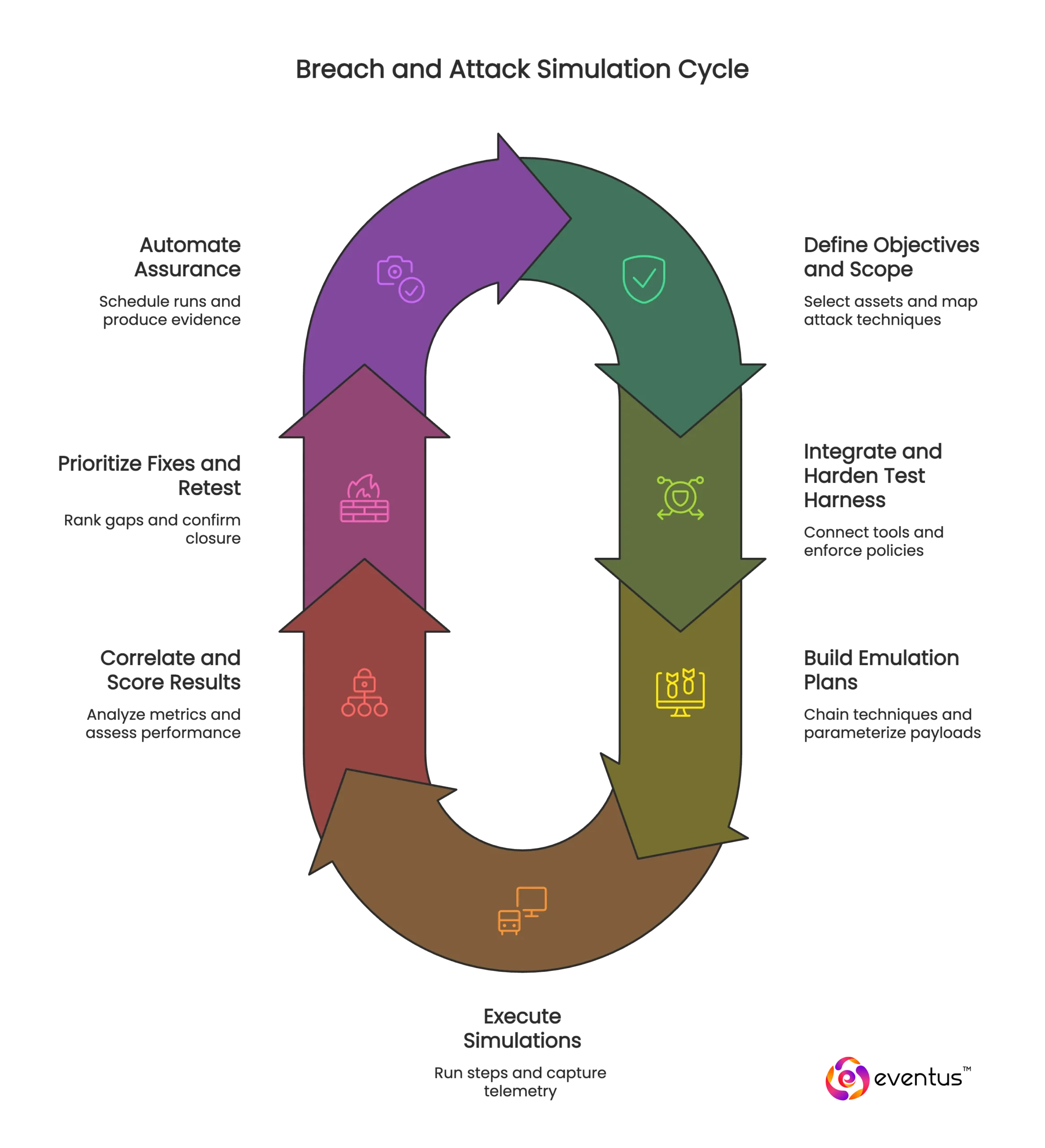
Breach and attack simulation tools orchestrate controlled emulations of adversary attack techniques and measure security validation outcomes across each integrated security tool. The workflow is deterministic:
1. Define objectives and scop
- Select target assets and controls
- Map required attack techniques (e.g., MITRE ATT&CK) to scenarios
2. Integrate and harden the test harnes
- Connect breach and attack simulation tools to each security tool (SIEM, EDR, NDR, email, firewall)
- Enforce safe-run policies and rollbacks
3. Build emulation plan
- Chain attack techniques into end-to-end sequences (initial access → execution → lateral movement → exfiltration)
- Parameterize payloads, users, and timing
4. Execute simulation
- Run deterministic steps, capture telemetry, and avoid destructive actions by design
- Trigger detections and controls exactly where planned
5. Correlate and score result
- Security validation metrics: block rate (%), detection rate (%), false negatives (%), alert fidelity (%)
- Time-based metrics: mean time to detect (minutes), mean time to respond (minutes)
6. Prioritize fixes and retes
- Rank gaps by business impact and control criticality
- Auto-retest after each change to confirm closure
7. Automate assuranc
- Schedule recurring runs and drift checks
- Produce audit-ready evidence of validate security controls across tools and time
What Are The Benefits Of Breach And Attack Simulation?
Breach and Attack Simulation (BAS) offers several key benefits for organizations looking to strengthen their cybersecurity posture:
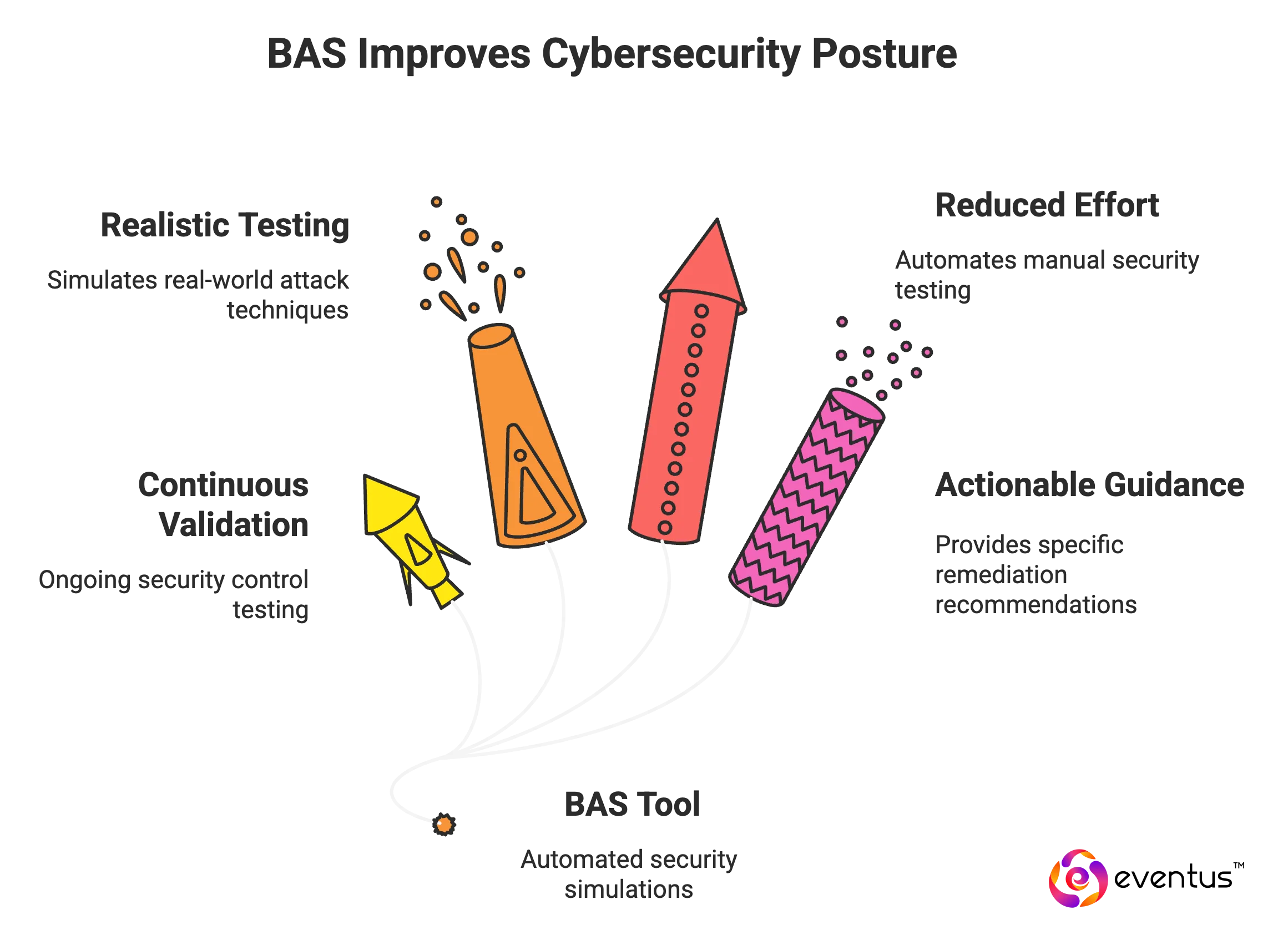
- Continuous Security Validation BAS tools run automated simulations that continuously test your security controls, providing ongoing validation rather than point-in-time assessments. This helps identify gaps that emerge as your environment evolves.
- Realistic Threat Testing These platforms simulate actual attack techniques used by real adversaries, including those documented in frameworks like MITRE ATT&CK. This gives you a more accurate picture of how your defenses would perform against genuine threats.
- Reduced Manual Effort Instead of requiring security teams to manually conduct penetration tests or red team exercises, BAS automates much of this testing, freeing up skilled personnel for other critical tasks.
- Actionable Remediation Guidance Most BAS solutions don't just identify vulnerabilities – they provide specific, prioritized recommendations for fixing issues, often including step-by-step remediation instructions.
- Improved Security ROI Measurement By quantifying security control effectiveness and demonstrating improvements over time, BAS helps justify security investments and shows measurable progress to leadership.
- Enhanced Incident Response Preparedness Regular simulation of attack scenarios helps security teams practice their response procedures and identify weaknesses in their incident response processes before a real attack occurs.
- Compliance and Audit Support BAS provides documented evidence of security testing and control effectiveness, which can be valuable for regulatory compliance and audit requirements.
- Risk Quantification These tools help translate technical vulnerabilities into business risk metrics, making it easier to communicate security posture to executives and prioritize remediation efforts based on actual business impact.
The automation and continuous nature of BAS makes it particularly valuable for organizations that need to maintain strong security postures but have limited resources for manual testing.
Which breach and attack simulation tools are most widely used?
Each platform simulates current attack techniques and validates defenses along the entire attack path:
- AttackIQ — independent breach simulation and validation platform with ready-to-run scenarios that exercise multiple types of attack and measure attack success versus each integrated security tool
- Cymulate — breach and attack simulation platform with ready-to-run attack templates and custom campaigns that reflect current attack techniques used by advanced actors; broadly reviewed on G2
- Mandiant Security Validation — threat-intel-driven simulation and attack assessments that test controls end-to-end against advanced attack patterns
- Pentera — automated security validation that operationalizes bas technology to uncover potential attack paths and prioritize fixes
- Picus Security — Picus Breach and Attack Simulation validates detections with an extensive attack database, enabling teams to simulate real attack sequences and prioritize remediation
- SafeBreach — continuous automated breach testing using a large playbook to emulate attack techniques used by advanced adversaries and measure control efficacy
- SCYTHE — adversary emulation platform for custom attack simulations and campaign-level testing across the entire attack chain
- XM Cyber — BAS plus exposure analytics focused on mapping potential attack paths and validating defenses from initial access to impact
These products consistently appear in category pages and comparative lists tracking bas tools excel at security validation, validate security controls, and demonstrate how bas tools work against evolving threats.
How does breach and attack simulation compare to penetration testing?
Breach and attack simulation solutions (BAS) deliver continuous, automated control validation; penetration tests are human-led point-in-time assessments focused on exploit discovery and proof-of-compromise.
| Criterion | Breach and attack simulation (BAS) | Penetration testing |
| Primary purpose | Continuous security validation of security controls against mapped attack techniques | Human-led exploitation to prove real-world impact on specific targets |
| Cadence | Scheduled, continuous and automated (e.g., daily or weekly) | Periodic (e.g., quarterly, annually, or before releases) |
| Method | Emulates curated attack techniques and attack paths with safety guardrails; pulls from an attack database to quickly assemble scenarios | Creative adversarial testing by experts who chain novel weaknesses to achieve objectives |
| Kill-chain coverage | End-to-end sequences along the entire attack path with ready-to-run templates and custom scenarios | Depth on selected paths; breadth depends on scope, time, and tester skill |
| Evidence | Control-by-control outcomes and trendable simulation results | Exploit narratives, screenshots, and proofs of compromise |
| Typical metrics | Block rate (%), detection rate (%), false negatives (%), MTTD/MTTR (minutes), scenarios passed/failed (count) | Vulnerabilities confirmed (count), exploitable paths (count), time-to-compromise (minutes/hours) |
| Integration | Native integrations with SIEM/EDR/NDR, ticketing, and CI/CD to validate security controls and auto-retest fixes | Report-driven; integrations depend on tester workflow and client processes |
| Safety | Designed to avoid destructive actions; production-safe profiles | Bound by rules of engagement; impact minimized but depends on test actions |
| Change management | Fast re-tests after config changes; detects drift quickly | Re-testing requires a new engagement or defined remediation window |
| Best fit | Ongoing control assurance, SOC tuning, readiness against current attack techniques used by advanced actors | Assurance of business-risk exposure via creative, human adversary tradecraft |
Analyst note: Industry analysts (e.g., Gartner) position BAS as a control-validation and exposure-reduction capability; selecting the best BAS solution depends on required integrations, scenario coverage, reporting needs, and operational cadence.
How does breach and attack simulation compare to red teaming?
Breach and attack simulation (BAS) delivers continuous, automated control validation. Red teaming is a human-led adversarial exercise that proves real business impact.
| Criterion | Breach and attack simulation (BAS) | Red teaming |
| Primary purpose | Validate security controls at scale and on schedule. | Demonstrate how a successful attack may achieve objectives against the organization. |
| Cadence | Continuous and automated (daily or weekly). | Point-in-time (multi-week campaigns). |
| Method | Emulates mapped attack techniques and attack paths; uses an attack database to quickly assemble safe, repeatable scenarios. | Creative adversary tradecraft, social engineering, custom payloads, live pivoting. |
| Scope | Broad coverage across endpoints, network, identity, email, web, and cloud. | Depth on selected targets and crown jewels. |
| Evidence | Control efficacy and trendable simulation results. | Proof of compromise, time-to-compromise, business impact narrative. |
| Typical metrics | Block rate (%), detection rate (%), false-negative rate (%), MTTD (minutes), MTTR (minutes), scenarios passed/failed (count). | Time-to-initial-access (minutes/hours), dwell time (hours/days), controls bypassed (count), data access achieved (GB or records), privilege escalations (count). |
| Safety profile | Production-safe by design with non-destructive actions. | Governed by rules of engagement; risk managed but real operations executed. |
| Change validation | Fast re-tests after configuration changes; detects drift quickly. | Re-testing requires a new or follow-on engagement. |
| Best fit | Ongoing security validation, SOC tuning, readiness against current techniques. | Executive-level assurance of real-world impact and response readiness. |
Which security controls are tested with breach and attack simulation?
BAS validates controls across layers. Most platforms use an attack database to quickly assemble safe, repeatable scenarios aligned to specific techniques.
Endpoint Security Controls
- Endpoint protection and EDR: Tests malware execution, fileless attacks, credential theft, and lateral movement. Measures block rates, detection accuracy, false negatives, and response times.
- Endpoint hardening: Evaluates script controls, DLL protections, driver restrictions, and macro policies. Tracks enforcement rates and bypass detection.
Network Security Controls
- Firewalls, IDS/IPS, and NDR: Simulates command-and-control traffic, port scanning, exploit delivery, and data exfiltration. Measures prevention rates, alert accuracy, coverage, and containment speed.
- Web gateways and DNS security: Tests URL filtering, domain blocking, DNS tunneling, and TLS inspection. Tracks policy enforcement and harmful content blocking.
Email and Communication Security
- Email security and sandboxing: Runs phishing simulations, payload testing, and business email compromise scenarios. Measures block rates, user susceptibility, and sandbox effectiveness.
Identity and Access Controls
- Identity and access management: Tests authentication bypasses, brute force attacks, and conditional access policies. Tracks detection rates and unauthorized access prevention.
- Privileged access management: Simulates credential misuse, Kerberoasting, and directory attacks. Measures privileged session monitoring and high-risk activity blocking.
Cloud Security Controls
- Cloud security platforms: Tests permission misuse, metadata abuse, storage exposures, and cross-account attacks. Tracks misconfiguration detection and remediation speed.
- Container and Kubernetes security: Evaluates admission policies, privilege escalation, and runtime protections. Measures policy violations and containment effectiveness.
Application Security Controls
- Web application firewalls and API gateways: Tests injection attacks, authentication bypasses, and API abuse. Measures attack coverage and blocking accuracy.
Data Protection Controls
- Data loss prevention: Simulates data exfiltration through various channels including encrypted methods. Tracks blocked attempts and detection precision.
- Ransomware protection and backups: Tests early-stage ransomware behaviors and recovery capabilities. Measures detection speed and restore success rates.
Detection and Response Systems
- SIEM and analytics: Evaluates rule effectiveness, correlation accuracy, and data quality. Tracks detection rates and false negatives.
- SOAR and incident response: Tests automated workflows, containment procedures, and notification systems. Measures playbook success and response times.
What Are Best Practices For Implementing Breach And Attack Simulation?
Each control category provides specific metrics to quantify security effectiveness and identify areas needing improvement.
- Define Clear Objectives Establish specific goals (control validation, compliance, maturity assessment) and scope boundaries. Start small and expand gradually as the program matures.
- Align with Business Risk Prioritize simulations based on your actual threat landscape and business-critical assets. Use threat intelligence to focus on relevant attack techniques for your industry.
- Integrate with Security Operations Coordinate with SOC, incident response, and security teams. Schedule testing to avoid conflicts with business operations and establish clear communication protocols.
- Establish Baselines and Metrics Document current security posture before testing begins. Track key metrics like detection rates, response times, and prevention effectiveness to measure improvement.
- Implement Gradual Rollout Begin with non-production environments and well-understood attack vectors. Progressively expand to more comprehensive testing as team confidence builds.
- Focus on Remediation Create processes for prioritizing and addressing identified gaps. Assign clear ownership for fixes and integrate findings into vulnerability management workflows.
- Maintain Realistic Scenarios Keep simulations based on actual adversary behavior, not theoretical attacks. Regular updates based on current threat intelligence ensure relevance.
- Build Cross-Team Collaboration Secure buy-in from IT operations, network teams, and business stakeholders. Establish clear roles and communicate how BAS supports broader security objectives.
- Monitor and Tune Continuously Review results for patterns and adjust testing frequency based on control maturity. Update scenarios as infrastructure and threats evolve.
- Report Effectively Tailor reporting for different audiences - technical details for security teams, risk metrics for management, and trend analysis for strategic planning. The key is treating BAS as an ongoing security program rather than a point-in-time tool, with continuous refinement based on results and changing organizational needs.
What is the average price of a breach and attack simulation tool?
Breach and attack simulation tools typically cost $50,000 to $250,000+ annually (₹50,000 to ₹250,000 Indian rupees) for mid-to-large enterprises, with pricing varying significantly based on organization size, features, and deployment model. Specific examples include AttackIQ's Starter Pack at $250,250 per year and Cymulate's 7 attack vector bundle at approximately $91,000 annually for up to 1,000 endpoints. However, most major vendors like Pentera, Picus Security, and SafeBreach don't publish standard pricing and require custom quotes, which "is a factor that is going to deter small businesses from enquiring about the product." Organizations should expect enterprise-level pricing for comprehensive BAS solutions, though many vendors offer free trials for evaluation.