This article defines cyber law, its scope, and its role in the digital age. It covers the main categories of cyber law and the types of cybercrime they address; the objectives and importance of cyber law; core statutes in India and the United States; leading international instruments; and governance and compliance essentials for organizations and individuals. It concludes with practical guidance on learning paths and career options in cyber law.
Table of Contents
What is Cyber Law?
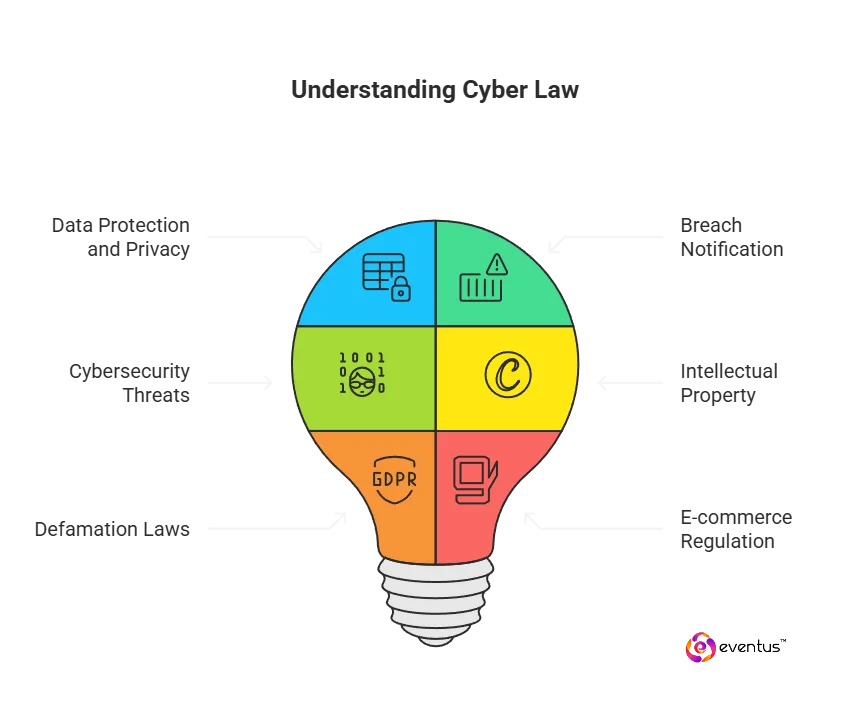
Cyber law, also called digital law, is the body of laws and regulations that forms the legal framework for online activities across computer systems and networks. It defines rights and duties for individuals and organizations and resolves legal issues arising from cybersecurity and cyber threats. Its scope includes data protection and privacy for personal data and sensitive information, breach notification after a data breach, and safeguards against unauthorized access, hacking, phishing, identity theft, and other cybercrimes by cybercriminals. It also governs intellectual property and copyright infringement online, applies defamation laws to digital publications, and regulates e-commerce by recognizing electronic agreement formation and consumer protections. In short, cyber law integrates enforceable rules with practical security standards to deter malicious conduct and provide remedies.
What are the types of cyber law?
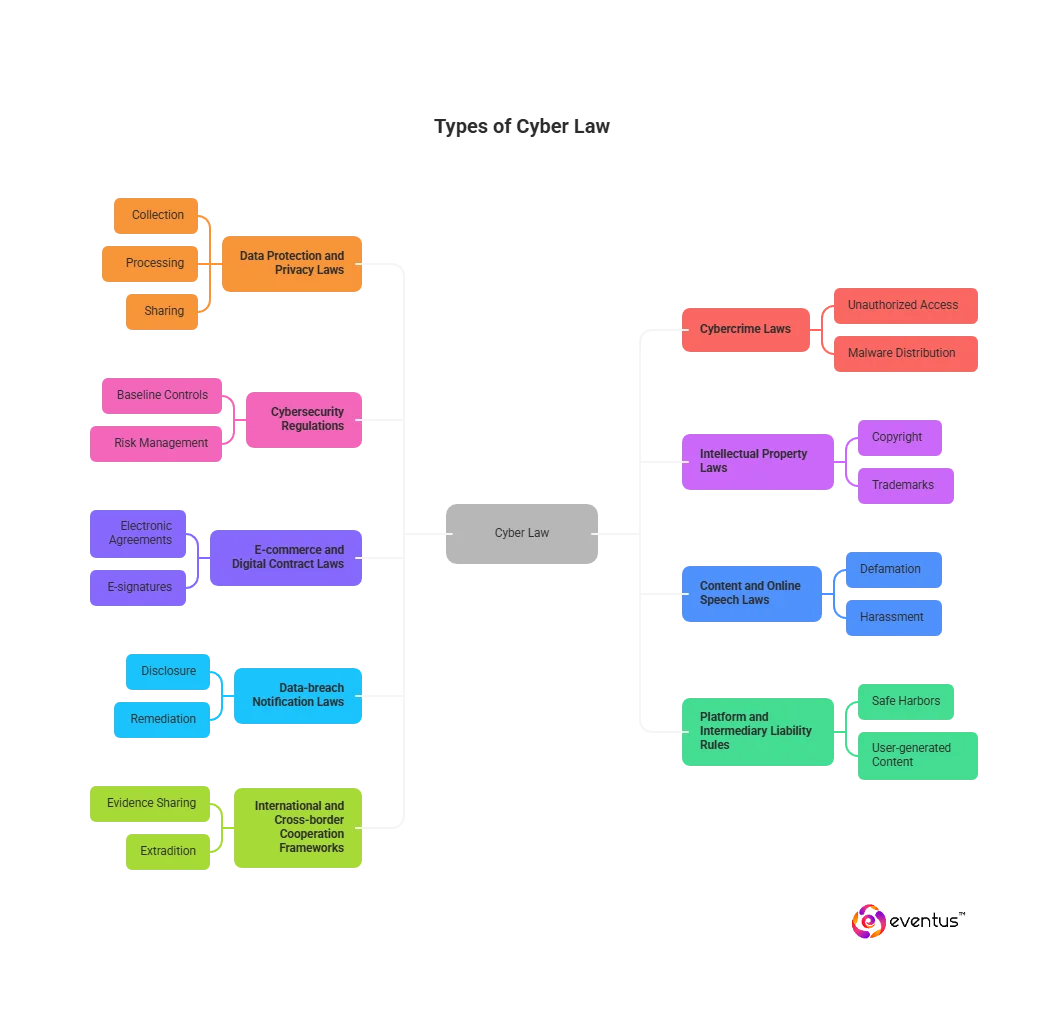
The main types of cyber law commonly applied across jurisdictions are:
- Data protection and privacy laws — govern the collection, processing, sharing, and retention of personal information; mandate safeguards and user rights (access, correction, deletion).
- Cybercrime laws — criminalize offenses such as unauthorized access, system interference, malware distribution, identity theft, phishing, and online fraud; define investigation and penalties for cybercrime.
- Cybersecurity regulations — set baseline controls, risk management, and incident-reporting duties to protect networks and systems; align legal compliance with cyber security practices.
- Intellectual property laws (digital context) — address copyright, trademarks, patents, and trade secrets online, including takedowns and anti-circumvention measures.
- E-commerce and digital contract laws — validate electronic agreements, e-signatures, records retention, and consumer protection in online transactions.
- Content and online speech laws — apply defamation, harassment, and related torts to digital publications and platform activity.
- Data-breach notification laws — require disclosure to users and regulators when protected personal information is exposed, with timelines and remediation steps.
- Platform and intermediary liability rules — define duties and safe harbors for hosts, ISPs, and marketplaces regarding user-generated content and unlawful activity.
- International and cross-border cooperation frameworks — enable evidence sharing, extradition, and harmonized enforcement for crimes and incidents spanning multiple countries
These categories show the importance of cyber law in organizing how states protect people and businesses, deter attacks, and enforce accountability online.
What types of cybercrime are covered by cyber law?
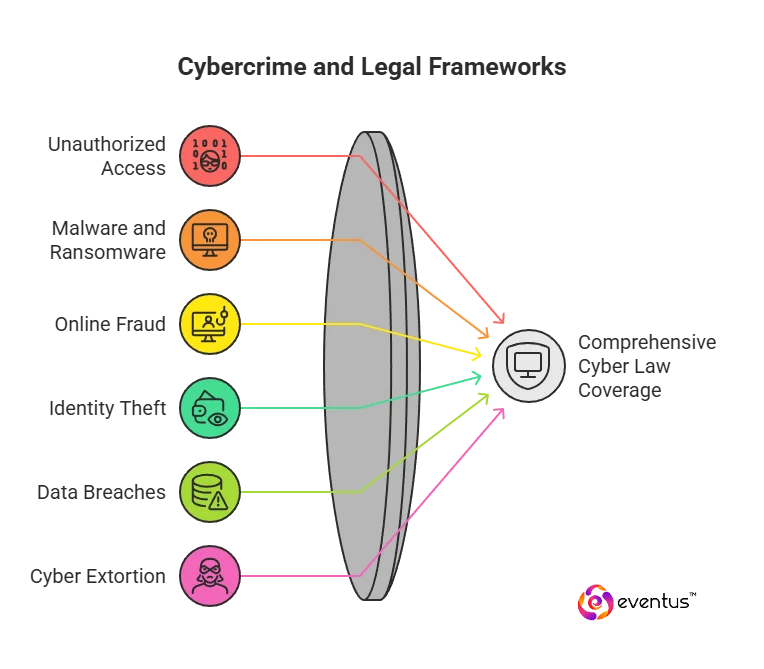
These are the primary types of cybercrime that cyber law targets in the digital world, reflecting the importance of cyber law in aligning law and cybersecurity across the digital age.
- Unauthorized access and hacking — breaking into computer systems or networks, escalating privileges, or maintaining backdoors. Covered by information technology law and cybersecurity laws.
- Malware, ransomware, and botnets — creating, distributing, or using malicious code to disrupt operations, encrypt data, or exfiltrate sensitive information.
- Fraud and deception online — phishing, business-email compromise, payment-card and auction fraud, and other e-frauds governed by e-commerce regulations and internet law.
- Identity theft and account takeover — using another person’s credentials to obtain access to sensitive information or commit further offenses.
- Data breaches and unlawful processing — unauthorized acquisition, disclosure, or sale of personal information; duties triggered under data breach notification laws and privacy regulations to protect privacy and security.
- Cyber extortion — threats to leak data or disrupt services unless a ransom is paid.
- Online defamation and harassment — defamatory posts, impersonation, and targeted abuse on social media platforms; cyber defamation laws address unlawful speech while balancing freedom of expression under social media laws.
- Intellectual property offenses — copyright infringement, digital piracy, and trade-secret theft.
- Illegal content and child protection offenses — creation, possession, or distribution of prohibited material.
- Interference and denial-of-service attacks — degrading or blocking services, impairing availability and information security.
- Unlawful surveillance and stalking — spyware use, doxxing, or tracking without consent.
- Contract and signature manipulation — forging or misusing digital signatures and falsifying electronic contracts, covered by cyber contracts and e-signature laws.
- Critical infrastructure attacks and cyber terrorism — targeting healthcare, energy, transport, or government systems.
- Cross-border conspiracies — crimes spanning multiple jurisdictions; international cyber laws address cooperation among law enforcement agencies.
Why it is important?
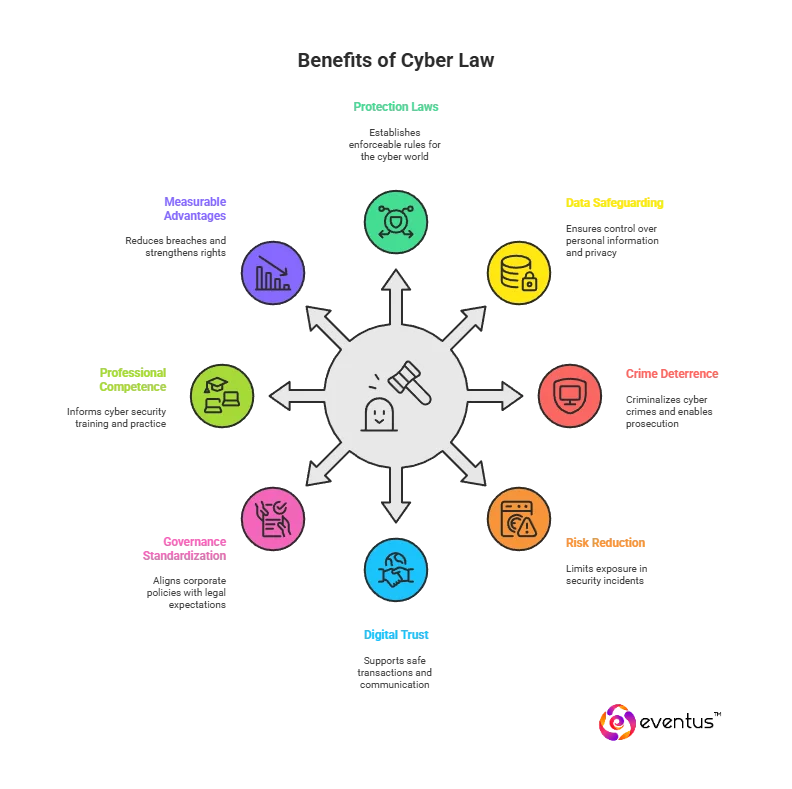
- It establishes protection laws. Cyber law is the area of law (and field of law) that creates enforceable rules for the cyber world, defining duties, rights, and remedies for individuals and organizations after security incidents and cyber crimes.
- It safeguards people and data. Cyber law ensures that individuals can control personal information, seek redress for misuse, and enforce privacy—one of the core aspects of cyber law and a key advantage of cyber law.
- It deters and prosecutes offenses. By criminalizing hacking, fraud, and other cyber crimes, it gives investigators clear grounds to act and courts clear bases to punish wrongdoing.
- It reduces risk and liability. Clear duties for prevention, detection, and reporting help organizations limit exposure when managing security incidents involving personal or business data.
- It enables digital trust. Predictable rules for identity, consent, and accountability support safe transactions and communication in the digital age.
- It standardizes governance. Common definitions and procedures align corporate policies with legal expectations across the world of cyber law.
- It builds professional competence. A legal baseline informs cyber security training, every cyber security professional’s practice, and the curriculum of a cyber law course covering the essentials of cyber compliance.
- It delivers measurable advantages. The advantages of cyber regulation—fewer breaches, faster response, stronger rights—flow from consistent statutes, enforcement, and education.
What are the key cyber laws in India?
These instruments form the operative legal framework for cyber offences, platform duties, incident handling, and data protection in India.
- Information Technology Act, 2000 (as amended in 2008) — India’s core cyber statute for e-records, e-signatures, offences and enforcement: offences (Secs. 65–74), intermediary safe-harbour (Sec. 79), interception/decryption (Sec. 69), blocking of content (Sec. 69A), protected systems and critical infrastructure (Secs. 70, 70A), and CERT-In (Sec. 70B).
- IT procedural rules under the Act
-
- Blocking Rules 2009 — procedure and safeguards for blocking public access to online information under Sec. 69A.
- Interception, Monitoring and Decryption Rules 2009 — process for lawful access under Sec. 69.
- Traffic Data/Information Monitoring Rules 2009 — monitoring and collection of traffic data for cyber security and offences.
- Information Security Practices for “Protected System” Rules 2018 — baseline controls for notified critical information infrastructure.
-
- Intermediary Guidelines and Digital Media Ethics Code Rules, 2021 (amended 2022 & 2023) — due-diligence, grievance redressal and takedown workflow for intermediaries; adds a Grievance Appellate Committee and an online-gaming compliance layer.
- CERT-In Directions, 2022 (under Sec. 70B IT Act) — 6-hour incident reporting, expanded reportable categories, 180-day log retention, and KYC obligations for certain service providers.
- Digital Personal Data Protection Act, 2023 — consent-based data protection regime with a Data Protection Board and significant penalties; enacted on 11 Aug 2023. As of mid-2025, most substantive provisions await notification for enforcement.
- Bharatiya Sakshya Adhiniyam, 2023 (Evidence law) — modernises electronic evidence; electronic/digital records are admissible subject to Section 63 conditions.
- Bharatiya Nyaya Sanhita, 2023 (Criminal code) — replaces the IPC and is applied alongside the IT Act for cyber offences such as cheating, forgery, extortion and organised cyber-crime conduct.
What are the key U.S. cyber law statutes?
Here are the core U.S. statutes most often cited in cyber matters:
- Computer Fraud and Abuse Act (CFAA), 18 U.S.C. §1030 — anti-hacking, fraud, and unauthorized access to “protected computers.”
- Electronic Communications Privacy Act (ECPA), 1986 — Wiretap Act (real-time interception), Stored Communications Act (stored content), and Pen Register/Trap-and-Trace rules.
- Digital Millennium Copyright Act (DMCA), 1998 — notice-and-takedown (17 U.S.C. §512) and anti-circumvention (17 U.S.C. §1201).
- Children’s Online Privacy Protection Act (COPPA), 15 U.S.C. §6501 et seq. — restrictions on collecting personal data from children under 13 (implemented at 16 C.F.R. Part 312).
- Communications Decency Act §230, 47 U.S.C. §230 — platform/intermediary liability shield for user-generated content (with exceptions).
- CAN-SPAM Act, 15 U.S.C. §7701 et seq. — requirements for commercial email (headers, subjects, opt-outs, enforcement).
- Gramm-Leach-Bliley Act (GLBA), 15 U.S.C. §§6801–6809 — financial-sector privacy; FTC Safeguards Rule for information security programs.
- HIPAA Security Rule, 45 C.F.R. Part 164 Subpart C — administrative/technical/physical safeguards for electronic protected health information.
- Federal Information Security Modernization Act (FISMA), 44 U.S.C. §3551 et seq. (2002, updated 2014) — federal-agency information security framework and oversight.
- Cybersecurity Information Sharing Act (CISA) of 2015 — liability-protected private-public cyber-threat information sharing (reauthorization pending; current sunset Sept. 30, 2025).
- Cyber Incident Reporting for Critical Infrastructure Act (CIRCIA) of 2022 — requires critical-infrastructure entities to report substantial cyber incidents (72 hours) and ransom payments (24 hours); final rulemaking is in progress.
- Electronic Signatures in Global and National Commerce (E-SIGN) Act, 15 U.S.C. §7001 et seq. — gives legal effect to electronic records and signatures in commerce.
These statutes collectively define offenses, privacy/security duties, platform responsibilities, government-sector controls, incident reporting, and the legal validity of electronic transactions.
How to learn cyber law and build a career
Choose a track, build legal and technical fundamentals, and prove capability with real deliverables and verified credentials.
- Choose a track and role: legal first (counsel), tech or GRC first (privacy or compliance manager), or policy first (regulator or analyst).
- Build foundations: core law (contracts, criminal, evidence, intellectual property, administrative, constitutional) and core tech (networks, identity and access management, logging, encryption, cloud).
- Master pillars: data protection and privacy, cybercrime, platform and speech, e-commerce and e-signatures, intellectual property online, public sector and critical infrastructure obligations.
- Practice deliverables: privacy notice, data processing agreement, terms of service, incident response plan; two tabletop exercises (ransomware and data breach); map ISO 27001 or NIST CSF to one statute; assemble a breach file.
- Credentials: LLB or JD or diploma or LLM; IAPP CIPP US or CIPP E and CIPM; ISO 27001 Lead Implementer or Auditor; forensics or eDiscovery if you support investigations.
- Portfolio: three case notes on recent decisions, two practitioner articles, anonymized policies and assessments.
- Experience: clinic or internship with law firms, in-house GRC, regulators, or incident-response vendors; assist on real incidents under supervision.
- Progression: entry (privacy analyst, junior associate, compliance analyst) to mid (privacy or product counsel, compliance manager, incident-response counsel) to senior (data protection officer, head of cyber legal, policy lead).
- Twelve-month cadence: months 0 to 3 foundations plus one certification plus privacy notice and DPA; months 4 to 6 two tabletops plus one case note plus breach assistance; months 7 to 9 map ISO or NIST to a statute plus evidence pack plus second article; months 10 to 12 apply with verified portfolio and references.
FAQ:
What is RA 10175 cybercrime law?
RA 10175 is the Philippines’ Cybercrime Prevention Act of 2012. It criminalizes offenses done through computers or the internet—such as illegal access, data interference, online fraud, child sexual abuse material, identity theft, and online libel—and sets investigation powers and penalties.
What is the cyber law Act in India?
India’s main cyber law is the Information Technology Act, 2000, as amended in 2008. It gives legal status to electronic records and digital signatures, defines cybercrimes, and prescribes penalties and procedures. Related rules and updates (for example, the 2021 IT Rules and the 2023 data protection law) complement it.
What is cyber law class 7th?
Cyber law is the set of rules that govern how we use computers and the internet. It protects people’s data and identity and punishes online crimes like hacking, cheating, cyberbullying, and sharing harmful content. For Class 7 students, it means follow safe habits online, respect others’ privacy, and report anything unsafe to a trusted adult.