This article explains what a Managed Security Service Provider is and how it works, then outlines core managed security services and where they apply. You’ll see the benefits organizations can expect, how to choose the right provider, and how MSSPs differ from MSPs. We also cover support for cloud and hybrid environments, the industries that benefit most, and practical outcomes such as improved detection and faster response. Finally, we examine the future of MSSPs, including AI-driven operations, unified platforms, and outcome-based SLAs.
Table of Contents
What is a MSSP and How Does it Work?
MSSP means Managed Security Service Provider. MSSP is a specialized company that delivers outsourced managed security services to protect an organization’s digital infrastructure. Instead of relying solely on an internal security team, businesses use managed soc service provider to monitor, detect, and respond to security incidents around the clock.
An MSSP operates through a combination of security operation centers (SOCs), advanced analytics, and experienced security experts to safeguard networks, systems, and applications.
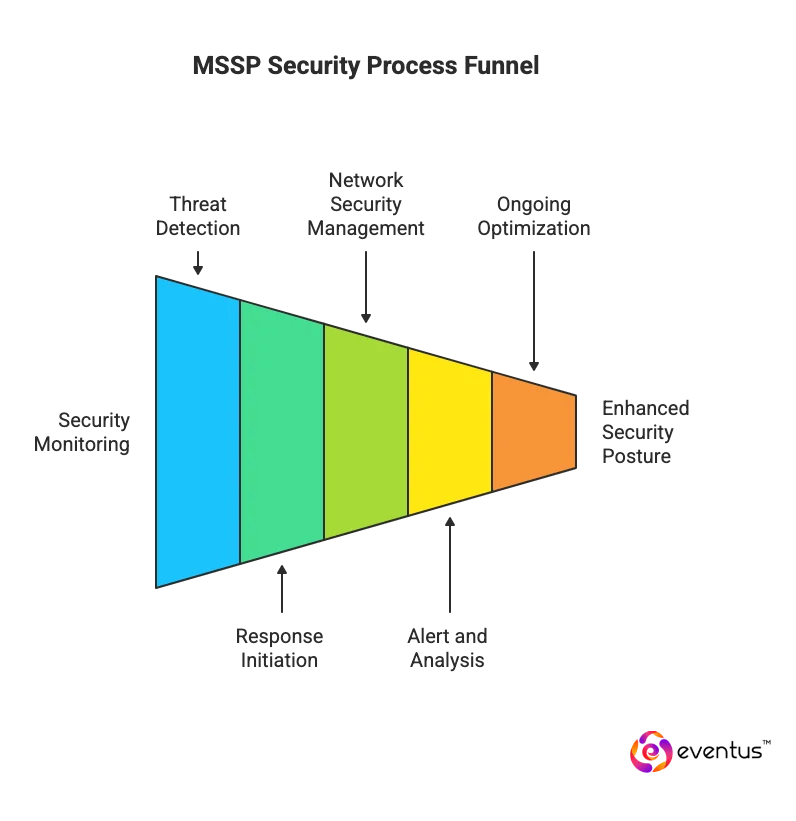
How MSSP Works
- Continuous Security Monitoring – MSSPs use security operations centers to provide 24/7 monitoring and management of networks, systems, and endpoints.
- Threat Detection and Response – Through managed detection and response (MDR) tools, MSSPs identify potential threats, investigate anomalies, and initiate mitigation before a security incident escalates.
- Network Security Management – They handle intrusion detection, managed firewalls, and access control to ensure consistent enforcement of security policies.
- Alert and Analysis – When anomalies occur, real-time alerts are generated, allowing rapid triage and containment by security experts.
- Ongoing Optimization – MSSPs continually assess the organization’s security posture and adapt controls to evolving threats.
- Outsourced Security Operations – By choosing to outsource to a managed service provider, organizations gain access to skilled professionals, cost efficiency, and advanced tools they may not afford internally.
In essence, an MSSP—one of the soc managed service providers—serves as an external security partner that helps organizations manage security more effectively, ensuring consistent protection, faster detection, and reduced exposure to emerging cyber threats.
What Services Do MSSPs Offer?
A Managed Security Service Provider (MSSP) delivers a wide range of security monitoring and management services designed to safeguard an organization’s security needs and reduce exposure to cyber risks. By partnering with an managed soc providers, organizations gain access to expert-driven security solutions that address every layer of defense — from network security services to cloud security and compliance.
Core MSSP Services Include:
- 24x7 Security Monitoring and Incident Response – Continuous tracking of network, endpoint, and system activities to identify and respond to security events in real time.
- Network Security Monitoring and Management – Oversight of security devices and systems such as firewalls, routers, and intrusion detection systems to prevent security breaches.
- Managed Detection and Response (MDR) – Combining advanced analytics, automation, and security professionals to detect and contain threats quickly.
- Vulnerability and Security Assessments – Ongoing evaluation of security parameters and security configuration management to identify security vulnerabilities and misconfigurations.
- Cloud Security and Data Protection – Implementation of security best practices for cloud workloads, ensuring information security and compliance with frameworks such as the Payment Card Industry Data Security Standard (PCI DSS).
- Threat Intelligence and Security Alerts – Delivery of real-time security data and alerts that enable proactive decision-making.
- Managed Firewall and Endpoint Protection – Configuration and management of security tools and security systems that enforce perimeter defenses and endpoint integrity.
- Incident Analysis and Remediation – Root cause investigation of critical security incidents, followed by containment and recovery.
- Compliance Management – Support for audits and adherence to data security standards through continuous monitoring and reporting.
- Security Consulting and Expertise – Access to trained security personnel who advise on implementation of security frameworks, security measures, and risk reduction.
- Security Operations Center (SOC) Management – Operation of dedicated or high-availability security operation centers that centralize threat detection and monitoring and management of security operations.
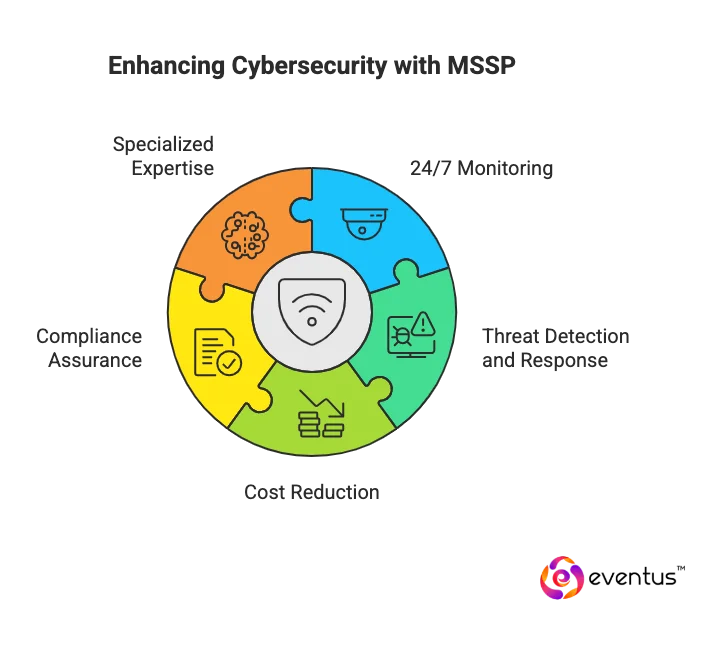
What Are the Benefits?
A Managed Security Service Provider (MSSP) offers measurable advantages to organizations seeking to strengthen their security across infrastructure, cloud, and applications. Unlike an MSP vs MSSP comparison where MSPs focus on IT maintenance, MSSPs specialize in providing security through 24x7 monitoring, proactive threat detection, and expert-led response.
Key Benefits of a Managed Security Service Provider:
- Access to Specialized Security Expertise – An MSSP gives organizations access to experienced analysts and threat hunters who understand evolving attack vectors, compliance demands, and advanced defense technologies.
- Continuous Monitoring and Rapid Response – With dedicated security operations centers, MSSPs detect, analyze, and respond to incidents around the clock, reducing downtime and exposure.
- Comprehensive Security Coverage – An MSSP offering integrates network, endpoint, and cloud protection for unified visibility and control over all attack surfaces.
- Reduced Security Risks – Partnering with an MSSP gives enterprises consistent vulnerability management and rapid containment capabilities, minimizing breach probability.
- Cost Efficiency Through Outsourced Security Services – Instead of building costly internal infrastructure, organizations outsource to the right MSSP, reducing operational overhead while maintaining enterprise-grade defense.
- Enhanced Scalability and Flexibility – An MSSP can help organizations scale protection with business growth and integrate software as a service tools that adapt to changing risk environments.
- Leverage of Advanced Technology – Enables an MSSP to use automation, analytics, and AI for predictive threat modeling and improved detection accuracy.
- Improved Compliance and Governance – MSSPs assist in meeting regulatory requirements and aligning with security frameworks through continuous audits and documentation.
- Strengthened Existing Security Infrastructure – An MSSP can also enhance existing security controls, ensuring cohesive defense without duplicating systems.
Ultimately, choosing a managed security service allows organizations to achieve comprehensive security with operational efficiency, enabling faster response, lower cost, and stronger cyber resilience.
How to Choose the Right MSSP?
Selecting the right Managed Security Service Provider (MSSP) is critical for organizations that depend on continuous protection, rapid response, and compliance assurance. The process involves evaluating security expertise, technological capabilities, and alignment with your operational and regulatory goals.
How to Choose the Right Managed Security Service Provider:
- Assess Security Expertise and Experience – Evaluate the MSSP’s credentials, certifications, and track record in handling complex security risks across industries. A capable MSSP can help implement tailored defense strategies aligned with your environment.
- Compare MSP vs MSSP Capabilities – While an MSP focuses on IT support, an MSSP gives comprehensive security coverage, including outsourced security services such as threat detection, incident response, and continuous monitoring.
- Review Service Offerings and Flexibility – The right MSSP should provide scalable, modular MSSP offerings that align with your business needs, from software as a service integrations to hybrid deployment models.
- Evaluate Technology and Infrastructure – Ensure the provider operates dedicated security operations centers with real-time monitoring and uses automation that enables an MSSP to use analytics for faster detection and response.
- Check Integration with Existing Security Systems – The chosen MSSP must seamlessly enhance your existing security stack without redundancy or disruption.
- Understand Response and Escalation Protocols – The MSSP should define clear procedures for incident handling, escalation, and coordination with internal teams.
- Verify Compliance and Reporting Capabilities – Look for an MSSP that supports regulatory obligations, audit readiness, and transparent reporting to maintain trust and accountability.
- Evaluate Cost and ROI – Partnering with an MSSP gives cost efficiency compared to building in-house capabilities while maintaining enterprise-grade defense.
- Ensure Ongoing Support and Collaboration – The right security partner prioritizes communication, adapts to evolving threats, and proactively strengthens defenses.
Ultimately, choosing a managed security service requires a balance of technology, expertise, and reliability. A qualified MSSP gives organizations the resilience and assurance needed to safeguard operations effectively.
What are the uses of MSSP?
The use of a Managed Security Service Provider (MSSP) is to help organizations strengthen their cybersecurity posture by outsourcing critical security operations to experts.
An MSSP is used to:
- Monitor and protect IT infrastructure 24/7, including networks, servers, endpoints, and cloud environments.
- Detect and respond to cyber threats using advanced tools like SIEM, EDR, and SOAR.
- Reduce operational costs by replacing in-house security infrastructure with managed services.
- Ensure compliance with regulatory standards such as GDPR, HIPAA, and PCI DSS.
- Provide access to specialized expertise in threat hunting, incident response, and vulnerability management.
In essence, the use of an MSSP is to deliver continuous, expert-driven protection that enhances an organization’s resilience against evolving cyber threats.
MSSP vs MSPs: What's the Difference?
Here is the difference between Managed Service Provider and Managed Security Service Provider:
| Aspect | Managed Security Service Provider | Managed Service Provider |
| Core focus | Providing security and risk reduction | IT operations |
| Objective | Threat prevention, detection and response | Uptime, performance |
| Scope | Security across endpoints, networks, cloud, identities | End-user, servers, networks |
| Operations center | 24x7 SOC (MSSP may run dedicated, high-availability SOCs) | NOC (often business-hours) |
| Services | SIEM/SOAR, managed detection and response, incident handling | Patching, backups, helpdesk |
| Tech stack | EDR/XDR, IDS/IPS, UEBA; MSSP can also manage managed firewall | RMM, backup tools |
| Responsibility | Proactive monitoring, triage, containment, recovery | IT upkeep and escalation |
| KPIs | MTTD/MTTR, incident rate, dwell time | Ticket SLAs, uptime |
| Partners | Security vendors, threat-intel and IR partners | OEMs, internet service providers |
| Best fit | Continuous security monitoring and defense | General IT management |
How Do MSSPs Support Cloud and Hybrid Environments?
A Managed Security Service Provider (MSSP) supports both cloud and hybrid environments by providing unified visibility, proactive threat defense, and compliance management across distributed infrastructures. Many providers now deliver security operations center as a service to centralize monitoring and response across multi-cloud and on-prem estates.
How MSSPs Support Cloud and Hybrid Environments:
- Unified visibility and control across on-prem and cloud from a single managed security service provider console.
- Native cloud integration (AWS, Azure, GCP) for config drift, IAM, and network exposure monitoring.
- Cross-platform detection and response for malware, data exfiltration, and unauthorized access.
- Compliance and data protection via continuous controls monitoring and audit-ready reporting.
- Identity and access management hardening (MFA, least privilege, key rotation).
- Centralized log and telemetry aggregation for full-stack investigation and threat hunting.
- Continuous optimization as architectures change, using managed security service provider solutions.
What is the Future of Managed Security Service Providers?
The future of Managed Security Service Providers & soc services in India is defined by consolidation, automation, and outcome-based delivery:
- AI driven soc as a service for correlation, summarization, guided response
- Unified managed SecOps platforms (SIEM/SOAR/XDR/ASM/CTI)
- Outcome-based SLAs tied to MTTD/MTTR and containment time
- CTEM at scale (attack-surface discovery, risk scoring, remediation tracking)
- Identity-first, Zero Trust delivered as a managed program
- Cloud-native analytics + detection-as-code with versioning and CI/CD
- Autonomous containment (isolation, credential revocation, micro-segmentation)
- Co-managed models and vertical packs, plus supply-chain/SaaS posture management
- Privacy/sovereignty controls and transparent per-asset/event pricing