Ransomware-as-a-Service (RaaS) has reshaped the cybercrime landscape, making it easier than ever for attackers to launch damaging ransomware campaigns. This article breaks down what RaaS is, how it differs from traditional ransomware, and how it works. It also explores who uses RaaS, how they join affiliate programs, and some of the most notorious examples in circulation. We cover the dangers, legal implications, compliance concerns, and offer actionable steps to protect against these threats. Finally, we look ahead at what the future holds for this fast-evolving cybercrime business model.
Table of Contents
What is ransomware?
Ransomware is a type of malicious software—malware—that encrypts a victim’s files or systems and demands a ransom payment in exchange for decryption. It’s one of the most disruptive and profitable forms of cyber threat used by threat actors worldwide.
Here’s how it works:
- Once installed, the ransomware encrypts critical files, rendering them inaccessible.
- Victims are shown a ransom note with instructions on how to pay—typically in cryptocurrency—to receive the decryption key.
- If the ransom isn’t paid, files may be permanently locked, deleted, or even leaked online, depending on the ransomware variant.
What is Ransomware-as-a-Service (RaaS)?
Ransomware-as-a-Service (RaaS) is a business model in which ransomware developers sell or lease ready-made ransomware tools to other cyber criminals, known as affiliates. These affiliates then launch ransomware attacks against victims, while the RaaS operator or RaaS provider handles development, infrastructure, and sometimes even customer support for payment negotiations.
Modeled after legitimate Software-as-a-Service (SaaS) platforms, RaaS platforms offer user-friendly dashboards, detailed documentation, and even raas kits to help affiliates deploy attacks with minimal technical knowledge. This affiliate model has made sophisticated cyber threats more accessible than ever.
What is the difference between RaaS and traditional ransomware?
The key difference between Ransomware-as-a-Service (RaaS) and traditional ransomware lies in how the attacks are developed, distributed, and executed.
| Aspect | Traditional Ransomware | Ransomware-as-a-Service (RaaS) |
| Development | Created and deployed by the same attacker | Developed by a RaaS provider, used by RaaS affiliates |
| Execution | One group manages the entire attack lifecycle | Multiple affiliates can launch RaaS attacks using a shared platform |
| Access | Restricted to technically skilled actors | Accessible via dark web marketplaces with minimal technical knowledge |
| Model | Direct attack model | RaaS model based on Software-as-a-Service (SaaS) principles |
| Scalability | Limited to the capacity of one operator | Highly scalable with multiple simultaneous campaigns by different affiliates |
| Revenue Sharing | Attacker keeps all ransom payments | Affiliates split ransom with RaaS operators |
| Complexity | High—requires custom tools, infrastructure, and negotiation | Lower—affiliates rely on pre-built ransomware tools and infrastructure |
| Barrier to Entry | High | Low—any threat actor can use RaaS with little technical skill |
| Distribution | Limited and manual | Automated or semi-automated via RaaS operations |
| Threat Surface | Narrower | Broader, due to the number of actors and parallel ransomware campaigns |
| Mitigation Focus | Targeted defenses and recovery | Emphasis on ransomware protection, endpoint protection, and proactive backup |
How does Ransomware-as-a-Service work?
Ransomware-as-a-Service (RaaS) operates like a criminal version of Software-as-a-Service (SaaS). Instead of selling legitimate tools, ransomware operators create and lease out malware to other cybercriminals, who use it to execute attacks.
Here’s how the process typically works:
- Development: A core team—known as the ransomware operators—builds the malware, attack infrastructure, and payment systems. This includes command-and-control servers, encryption modules, and victim communication portals.
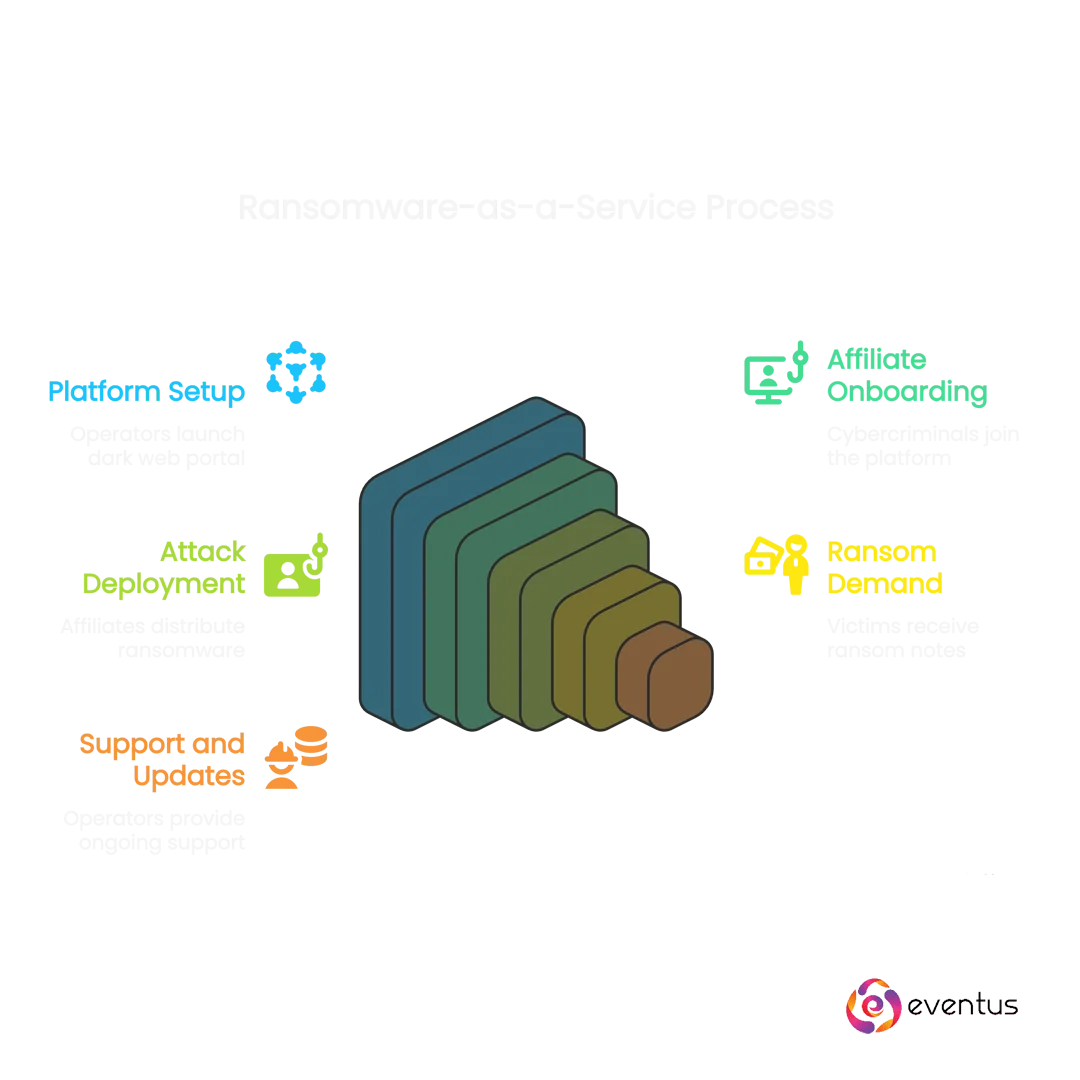
- Platform Setup: The operators launch a portal, usually on the dark web, that functions similarly to a SaaS dashboard. It includes documentation, automation tools, and status tracking for active ransomware infections.
- Affiliate Onboarding: Other cybercriminals (affiliates) sign up to the platform. They often pay an upfront fee or share a percentage of each ransomware threat payout.
- Attack Deployment: Affiliates distribute the ransomware via phishing emails, malicious links, exploit kits, or vulnerable remote access points. Once the malware infects the target, it encrypts files and locks systems.
- Ransom Demand and Payment: The victim is shown a ransom note demanding payment, usually in cryptocurrency. The affiliate and operator split the ransom once it’s paid.
- Support and Updates: Just like in SaaS, operators offer bug fixes, feature upgrades, and customer (attacker) support to improve success rates and attract more affiliates.
Because RaaS lowers the barrier to entry, it has dramatically increased the frequency and scale of ransomware infections. Organizations must prioritize layered defenses to prevent ransomware—this includes email filtering, patch management, employee training, regular backups, and endpoint security.
Who uses Ransomware-as-a-Service?
Ransomware-as-a-Service (RaaS) is primarily used by cybercriminals who want to profit from ransomware attacks without building the tools themselves. These actors are often not highly technical—they rely on RaaS platforms to provide everything they need to carry out attacks at scale.
The typical users of RaaS include:
- Low-skill threat actors: Individuals with limited coding or malware expertise who exploit RaaS platforms to deploy ransomware using pre-built dashboards and scripts.
- Organized cybercrime groups: Sophisticated criminal syndicates that use Ransomware-as-a-Service as a scalable extension of their operations, similar to how legitimate businesses adopt Software-as-a-Service for efficiency.
- Insiders and opportunists: Disgruntled employees or insiders who use RaaS tools to exploit their access to internal systems and maximize damage or extort employers.
- Affiliate networks: Groups or individuals who act as middlemen—distributing ransomware payloads for a cut of the ransom collected, often using phishing campaigns or supply chain attacks.
The accessibility and profitability of RaaS have led to its rapid adoption across the cybercriminal ecosystem. This widespread use increases the frequency, variety, and impact of ransomware incidents.
How do cybercriminals join RaaS programs?
Cybercriminals join Ransomware-as-a-Service (RaaS) programs through invitation-only forums, dark web marketplaces, or encrypted communication platforms where RaaS services are advertised. These platforms operate like commercial SaaS platforms—but instead of selling productivity tools, they rent ransomware tools designed for conducting ransomware attacks.
Here’s how the process typically unfolds:
- Accessing underground forums: Cybercriminals discover RaaS providers on private forums or darknet marketplaces. Advanced RaaS operators often vet applicants to avoid law enforcement infiltration.
- Registering as a RaaS affiliate: Once approved, the attacker signs up as a RaaS customer or ransomware affiliate. Depending on the RaaS services offered, they may pay upfront or agree to share a percentage of future ransomware payments.
- Using predeveloped ransomware tools: RaaS developers create a complete platform with dashboards, deployment scripts, and support for ransomware code. These predeveloped ransomware tools allow affiliates to execute ransomware attacks without writing their own code.
- Customizing the attack: Affiliates often switch to another ransomware kit or tweak existing settings based on information about their targets. Many RaaS services use modular designs to allow this flexibility.
- Launching campaigns: With access to the actual ransomware, affiliates spread it via phishing emails, malicious links, or exploit kits. Popular examples of RaaS kits include Dharma, LockBit, and BlackCat.
- Extorting victims and sharing revenue: When a ransomware victim pays up, the affiliate keeps a cut while the rest goes to the operator. Some sophisticated RaaS operators offer dashboards that track infections, status of ransomware payments, and success rates.
- Ongoing support: Like any service model, RaaS providers may offer updates, tech support, and even data leak sites to pressure victims.
What are some examples of Ransomware-as-a-Service?
Several notorious RaaS platforms have shaped the global ransomware landscape, offering plug-and-play capabilities for ransomware attackers through a scalable cybercrime business model where ransomware is commoditized. These RaaS kits provide access to the ransomware, dashboards, encryption modules, and extortion infrastructure—everything needed to run a full-scale ransomware campaign.
Here are some of the most well-known examples of Ransomware-as-a-Service:
- Dharma: Active since 2016, Dharma is one of the most common ransomware families sold as a service. It’s known for its consistent payload delivery and widespread use among many RaaS affiliates.
- LockBit: A highly adaptive RaaS platform known for rapid updates, high infection rates, and aggressive extortion ransomware tactics, including data leaks and DDoS threats.
- BlackCat (ALPHV): A modern RaaS platform coded in Rust, offering better evasion and performance. It supports both Windows and Linux targets and includes advanced support services for affiliates.
- REvil (Sodinokibi): One of the most infamous RaaS platforms, responsible for large-scale attacks against enterprises. REvil gained global attention for its role in high-profile incidents and ransom demands exceeding $50 million.
- Conti: A once-prolific RaaS that ran like a corporate entity with HR, payroll, and performance reviews. It became a benchmark for how professionalized RaaS operations can be.
- Hive: A multi-layered RaaS model known for targeting healthcare and infrastructure sectors. Hive was also notorious for rapid victim turnaround and leveraging email security weaknesses.
These examples of ransomware-as-a-service illustrate how RaaS works—democratizing the deployment of powerful ransomware strains through commercial-grade platforms. Each variant represents a type of malware engineered for scale, with varying features and support levels.
How dangerous is Ransomware-as-a-Service?
Ransomware-as-a-Service (RaaS) is one of the most disruptive forces in the cyber threat landscape—and it's not just because of the malware itself. What makes RaaS so dangerous is the ease with which attackers can now launch sophisticated ransomware operations without writing a single line of code.
Here’s why RaaS represents an escalating threat:
- It lowers the barrier to entry for cybercrime: Anyone can become a threat actor. If you can sign up for a streaming service, you can use the RaaS—no technical expertise required.
- It enables mass distribution of ransomware: Many ransomware variants are now circulating simultaneously, powered by well-known examples of RaaS kits like Dharma, LockBit, and BlackCat.
- It’s scalable and fast-moving: Ransomware attackers use these services to hit multiple targets across industries—often simultaneously.
- It introduces a professionalized criminal economy: Advanced RaaS operators often sell RaaS subscriptions, offer performance-based commissions, and run operations like a SaaS company.
- It evolves faster than traditional cybersecurity defenses: New ransomware variants emerge constantly. Since ransomware is malware that locks systems and data.
- The impact goes beyond financial loss: In high-profile cases like Colonial Pipeline, RaaS-linked attacks disrupted national infrastructure.
Is Ransomware-as-a-Service legal?
No, Ransomware-as-a-Service (RaaS) is not legal. While it mimics the structure of legitimate SaaS (Software-as-a-Service) platforms, the intent and outcome are criminal. RaaS is designed to enable cyberattacks that extort money from victims, often by encrypting their data and demanding ransom for its release.
Here’s what makes it illegal:
- Criminal purpose: Even though some actors claim they only “sell the software,” the sole function of RaaS platforms is to deploy malicious code that locks systems, steals data, and disrupts operations. That makes the use of the RaaS a prosecutable offense.
- Conspiracy and facilitation: Developers and affiliates aren’t just bystanders. If you develop ransomware or promote a platform that others can use to launch attacks, you're complicit in the crime—even if you don’t execute the attack yourself.
- Global law enforcement action: Agencies worldwide—like the FBI, Interpol, and Europol—are actively tracking, arresting, and charging individuals involved in RaaS networks. High-profile takedowns of platforms like REvil and DarkSide prove that ransomware operators are on law enforcement’s radar.
- Intent matters more than the tool: Whether you’re writing malware, distributing payloads, or managing payments, it doesn't matter how the ransomware operates—if your goal is to profit from extortion, it’s illegal.
What compliance issues does RaaS raise?
Ransomware-as-a-Service (RaaS) introduces serious compliance challenges for organizations across industries. Because ransomware operates by compromising systems and demanding payment for data release, it directly impacts legal, regulatory, and operational frameworks designed to protect information and ensure business continuity.
Key compliance issues include:
- Data protection violations: RaaS attacks often lead to unauthorized access or exfiltration of personal or sensitive data. This violates laws like GDPR, HIPAA, and India's DPDP Act, which require organizations to secure user data and report breaches.
- Failure to maintain cybersecurity standards: If a company falls victim to a RaaS attack and it’s found that they lacked adequate security controls, they can face regulatory penalties. This includes failure to update systems, weak authentication practices, or not deploying endpoint protection.
- Delayed breach reporting: Many regulations mandate that companies report breaches within a defined timeframe. The use of the RaaS by attackers complicates incident tracking, but delay or non-disclosure can trigger legal consequences.
- Risk of illegal ransom payments: In some countries, paying ransom may violate anti-money laundering (AML) or anti-terrorism financing laws—especially if the payment benefits sanctioned groups. Even when it's legal, companies paying ransoms must often disclose the event to regulators.
- Third-party and supply chain compliance: If ransomware developed by a RaaS group spreads through vendor software or managed services, it opens liability for third-party risk exposure. Companies are expected to assess and manage their vendor ecosystems for such vulnerabilities.
- Recordkeeping and audit failures: After an attack, companies must provide forensic records showing how the ransomware makes its way into their systems and what was done in response. Weak documentation or missing logs complicate regulatory investigations and insurance claims.
How can you protect against Ransomware-as-a-Service?
Protecting against Ransomware-as-a-Service (RaaS) isn’t just about installing antivirus software. It requires a multi-layered security approach, real-time monitoring, and quick incident response.
Here’s how organizations can stay ahead of these evolving threats:
- Establish a Security Operations Center (SOC)
A SOC is the nerve center for detecting, analyzing, and responding to cybersecurity incidents. Whether in-house or outsourced, a SOC enables around-the-clock visibility into potential RaaS threats. - Deploy a SIEM system
What is SIEM? Security Information and Event Management tools collect and correlate log data from across your environment to flag suspicious activity—like unusual file encryption or privilege escalation that may signal a ransomware infection. - Partner with a Managed Security Service Provider (MSSP)
If building an internal team isn’t feasible, an MSSP offers expert monitoring and incident response capabilities. These providers can act as your outsourced SOC, equipped to detect and respond to RaaS campaigns in real time. - Segment your network
Limit how far ransomware can spread by isolating critical systems from less-secure areas. Network segmentation can contain an attack before it becomes a full-scale breach. - Regularly back up your data
Offline and immutable backups can save you from paying a ransom. Test your backups often and store them in locations not accessible from your primary network. - Patch vulnerabilities promptly
Many RaaS infections exploit known flaws in software. Maintain a consistent patch management schedule across operating systems, apps, and firmware. - Train your team
RaaS often enters via phishing. Teach employees how to spot suspicious emails, links, and attachments. One click can open the door to a major breach. - Enable endpoint protection
Modern endpoint detection and response (EDR) tools can spot and shut down malicious behavior before it spreads—especially useful against newer RaaS variants. - Use strong access controls
Enforce least privilege. Limit admin access, use multi-factor authentication (MFA), and monitor account activity closely to prevent lateral movement by attackers.
What is the future of Ransomware-as-a-Service?
Ransomware-as-a-Service (RaaS) isn’t slowing down—it’s evolving. What started as a niche in cybercrime has become a dominant business model, making it easier for low-skill threat actors to launch high-impact attacks. Here's what the future looks like:
- More automation, less technical skill required: RaaS platforms are becoming more polished and user-friendly, similar to mainstream Software-as-a-Service (SaaS).
- Rise of customization and modularity: Future RaaS kits will likely offer modular ransomware code—letting affiliates tailor payloads based on the target’s OS, region, or backup defenses.
- Integration with AI and machine learning: As security tools grow smarter, so will ransomware. Expect more adaptive ransomware strains that can bypass traditional endpoint protection, identify high-value data, and evade detection longer.
- Expansion into double and triple extortion: Encrypting files is just the start. Attackers increasingly combine encryption with data theft (double extortion) and pressure campaigns—like contacting customers or leaking data to regulators (triple extortion). RaaS will refine these tactics as part of its standard offering.
- More RaaS operators on the dark web: As profits grow, more cybercriminal developers will launch their own RaaS operations, competing by offering better tools, lower cuts, or niche ransomware variants. This will further saturate the RaaS market and drive innovation.
- Tighter law enforcement pressure, but limited disruption: While international task forces are cracking down on major ransomware groups, the decentralized nature of RaaS makes it harder to fully dismantle. For every RaaS provider shut down, another often pops up under a new name.
- Security budgets will shift: Businesses will prioritize real-time threat intelligence, SOC capabilities, and ransomware protection. Preventing ransomware won’t just be about firewalls—it’ll involve rapid detection, response, and recovery.
What industries are common targets for ransomware attacks?
Ransomware attackers don’t strike randomly—they go after sectors where downtime is costly, data is critical, and security gaps are common. These are some of the industries that routinely find themselves in the crosshairs:
- Healthcare
- Education
- Financial Services
- Government Agencies
- Manufacturing and Industrial Control Systems (ICS)
- Legal Services
- Retail and E-commerce
- Energy and Utilities
- Technology and SaaS providers