SOC as a Service (SOCaaS) is an outsourced security operations model where a provider runs 24x7 monitoring, detection, and response across endpoints, networks, cloud, and identity. The article defines SOCaaS, explains how it works, outlines core components and managed SOC features, and highlights measurable benefits and ROI. It also covers SOC services, pricing models and cost drivers, common challenges and risks, compares SOCaaS with MDR and other models, and maps which organizations benefit most.
Table of Contents
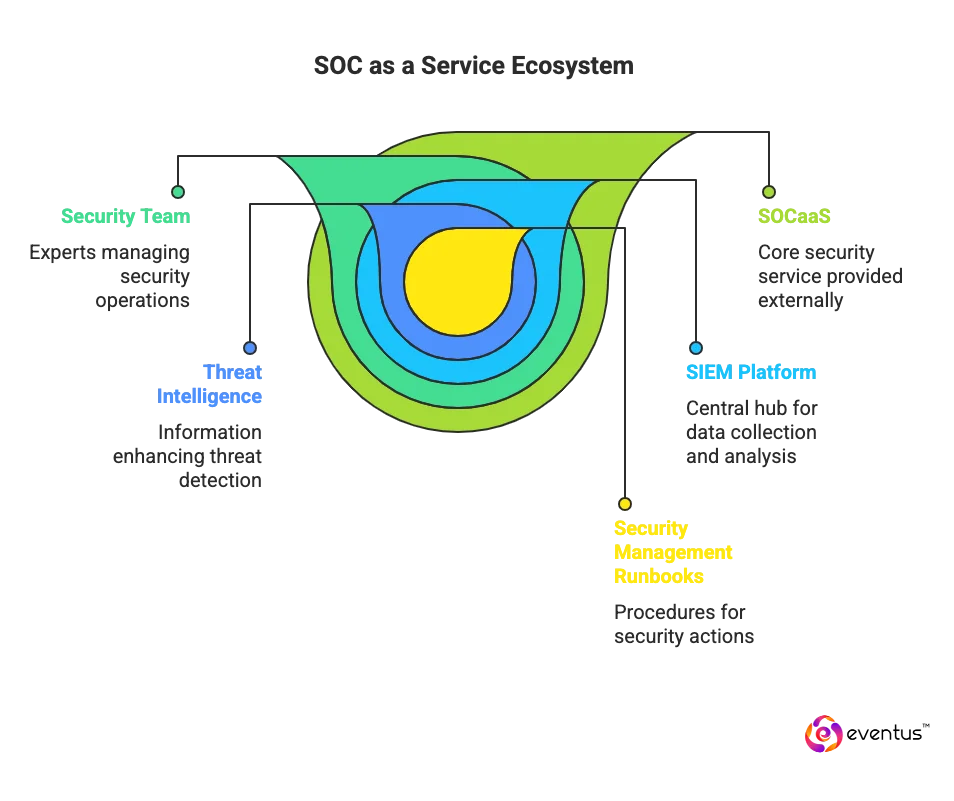
What is SOC as a Service?
SOC as a Service (SOCaaS), which means Managed Soc Service, is a subscription security solutions where a specialized service provider runs a 24/7 security operations center for you. The SOCaaS provider’s security team and security analysts handle threat detection and response across your endpoints, networks, cloud, and SaaS by collecting and correlating telemetry in a security information and event management platform, enriching it with threat intelligence, and executing security management runbooks. The difference between SOC as a Service and SOC is that SOCaaS is an outsourced, cloud-based model managed by external experts, while a traditional SOC is built and operated in-house with dedicated staff and infrastructure
How does SOC as a Service works?
A SOCaaS provider delivers a managed service in which its SOC team operates your detection and response program end to end with data sources. The workflow is standardized:
- Onboarding and integration: Connect log sources, endpoints, cloud, and SaaS; establish access, playbooks, and SLAs with the ai driven soc as a service team.
- Data collection and enrichment: Centralize telemetry, normalize it, and enrich with asset context and threat intel.
- Detection engineering: Deploy and tune rules, behavior analytics, and correlation for high-fidelity alerts.
- Triage and investigation: Analysts validate alerts, determine scope, and assess impact with clear escalation paths.
- Incident response: Contain, eradicate, and recover using predefined runbooks; coordinate actions with your IT and security owners.
- Continuous improvement: post-incident reviews, rule tuning, and hygiene fixes; periodic reporting and control reviews.
In practice, a managed soc service provider, runs the people, processes, and tooling while you retain governance and approve actions, achieving 24x7 coverage without building and staffing an internal managed service.
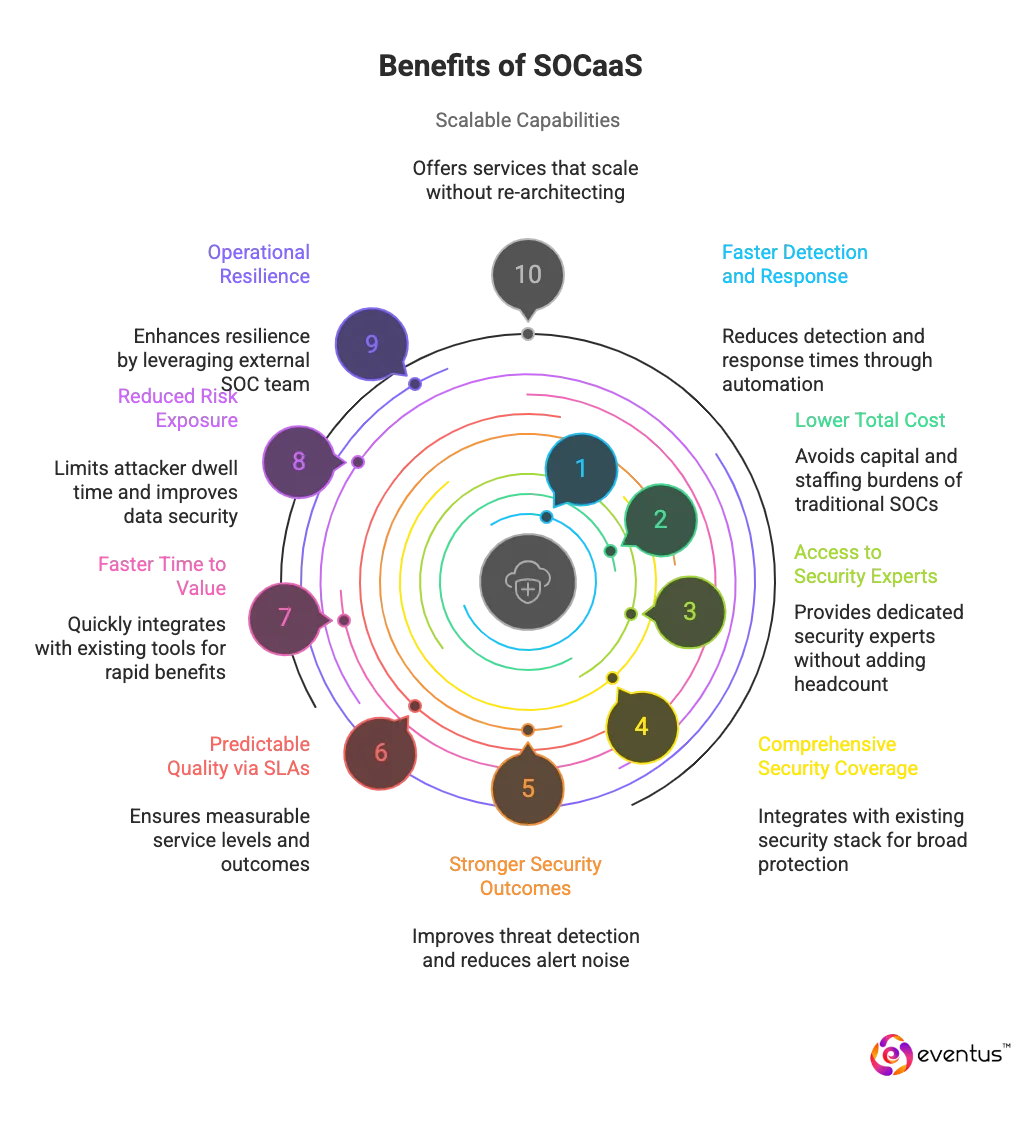
What are the top 10 benefits of SOCaaS?
Here are some benefits:
- Faster detection and response: A fully managed security operations center as a service delivers 24/7 monitoring and managed detection and response, reducing mean time to detect and respond by centralizing security events and automating triage (SOC automation).
- Lower total cost than a traditional SOC: Outsourcing security operations avoids the capital and staffing burden of an on-premises SOC or in-house security operations center while providing a comparable or higher level of security and service.
- Access to a team of security experts: SOC as a Service providers supply a dedicated SOC with security experts who monitor, investigate, and remediate—augmenting existing security teams without adding headcount.
- Comprehensive security coverage: SOCaaS includes threat detection and response across users, endpoints, network, cloud-based security, and SaaS, integrating with your current security stack and security infrastructure.
- Stronger security outcomes: SOC service runbooks, threat intelligence, and correlation improve organization’s security by increasing true-positive threat detection and decreasing alert noise.
- Predictable quality via SLAs: Clear service level agreements define investigation start times, escalation paths, and reporting cadence, giving measurable assurance of service level and outcomes.
- Faster time to value: Managed SOC as a Service onboards quickly by integrating existing security tools, so benefits materialize without lengthy buildouts.
- Reduced risk exposure: Continuous visibility plus managed threat detection and response limits attacker dwell time and lateral movement, improving data security and compliance readiness.
- Operational resilience: Unlike a traditional managed security service provider (MSSP) operating internally, where staffing limitations and burnout can create security blind spots, leveraging an external SOC team enhances operational resilience.
- Scalable capabilities: As security requirements grow, SOCaaS providers in India offer a range of services (from basic monitoring to advanced investigations) so SOCaaS operates and scales without re-architecting.
What are the key components of SOCaas?
The key components of SOCaaS—the security service that provides end-to-end monitoring, detection, and response—are:
- SOC team and governance: A 24x7 analyst and engineering roster with defined roles, escalation paths, and SLAs owned by the SOCaaS vendor.
- Telemetry ingestion layer: Connectors for endpoints, network, cloud, identity, and SaaS that normalize and enrich data for high-fidelity detection of security issues.
- Analytics and correlation engine: SIEM/XDR rules, behavioral analytics, and threat intelligence correlation to surface prioritized alerts.
- Automation and orchestration: SOAR playbooks to standardize triage, containment, and recovery; SOCaaS eliminates manual bottlenecks and speeds execution.
- Incident response runbooks: Preapproved actions, communications, and evidence handling to contain threats and document root cause.
- Use-case library and detection engineering: Continuously tuned rules and hunts; SOCaaS also adds new use cases as the environment and threats evolve.
- Reporting and metrics: Executive and technical reports covering MTTR/MTTD, incident trends, and control gaps and log management.
- Compliance and data management: Evidence retention, access controls, and audit artifacts aligned to regulatory requirements.
- Onboarding and integration operations: Asset discovery, tool integrations, role mapping, and go-live validation.
Many managed SOC service offerings bundle these components—people, processes, and platforms—into a unified solution delivered as a single service.
What are the Core Features of Managed SOC?
A Managed Security Operations Center (Managed SOC, which is also known as a service), combines technology, process, and expertise to deliver proactive threat detection, continuous monitoring, and rapid response. The core features include:
- 24/7 monitoring and high-fidelity detection across endpoint, network, cloud, identity
- Incident triage, investigation, and response via preapproved runbooks
- Threat-intel enrichment and correlation to raise true-positive rates
- Automation/orchestration (SOAR) to cut MTTR and remove toil
- Behavioral analytics/UEBA and proactive threat hunting
- Compliance-ready reporting (MTTD/MTTR, trends) and audit artifacts
- Scalable integrations with SIEM, EDR, and cloud-native logs
- Vulnerability management and prioritized remediation support
What are the Soc Services List?
A modern SOC (or Managed SOC / SOC as a Service) typically delivers a bundle of monitoring, detection, and response services.
The following points are related to common SOC services for businesses.
- Continuous log collection and security monitoring
- SIEM/XDR management and alert triage
- Threat detection, correlation, and use-case development
- Incident investigation and containment support
- Threat hunting and compromise assessment
- Vulnerability monitoring and exposure management inputs
- Endpoint, network, and cloud security monitoring
- Playbook-based incident response and runbooks
- Security reporting, dashboards, and executive summaries
- Compliance-focused logging and audit-ready evidence (e.g., ISO 27001, SOC 2, PCI-DSS)
How to choose the right SOCaaS provider?
Choosing a SOCaaS provider is a strategic decision. You need a partner that fits your risk profile, technology stack, and security maturity while improving key metrics like MTTD and MTTR.
The following points are related to evaluating and choosing the right SOC as a Service provider.
- Threat coverage and use cases
Check which threats and attack paths they cover (ransomware, account takeover, lateral movement, insider threats, cloud misconfigurations) and whether detections align with your critical assets and workflows. - Technology integrations and data sources
Verify native integrations with your SIEM, EDR/XDR, firewalls, cloud platforms, identity providers, and key SaaS apps so you minimize blind spots and custom engineering. - SLAs, response model, and playbooks
Review written SLAs for triage, investigation, and response times, and request sample playbooks to see exactly what actions they take and when they escalate to your team. - Visibility, reporting, and communication
Assess the quality of dashboards, incident timelines, and executive reports, plus escalation paths and cadence for regular service reviews. - Compliance, certifications, and data residency
Confirm certifications and controls (for example ISO 27001, SOC 2, HIPAA, PCI-DSS) and ensure their data storage and processing locations match your regulatory and internal policies. - Pricing transparency and scalability
Insist on clear pricing (per user, endpoint, or log volume) with defined assumptions for growth, and validate how the service scales without losing detection depth or performance.
Eventus’s SOCaaS is the right fit for your organization
How much does SOCaaS cost and how is pricing calculated?
This is how SOCaaS cost and is pricing calculated:
- How it’s priced: By GB/day ingested, # of assets, service tier/SLAs, and data retention. Subscription Model + one-time onboarding.
- Typical monthly ranges
| Business Tier | Pricing (INR) | Pricing (USD) |
| SMB | ₹2,66,250 – ₹8,87,500 | $3,000 – $10,000 |
| Mid-Market | ₹7,10,000 – ₹35,50,000 | $8,000 – $40,000 |
| Enterprise | ₹26,62,500 – ₹2,21,87,500+ | $30,000 – $250,000+ |
| Onboarding (One-Time) | ₹4,43,750 – ₹44,37,500 | $5,000 – $50,000 |
- Main cost drivers: Telemetry volume, scope (monitoring vs MDR/hunting/forensics), SLA speed/coverage, retention window, integration complexity, compliance, data residency.
- What’s included: 24×7 monitoring, alert triage, detection and response runbooks, reports, baseline tuning, platform tooling.
- Common extras: IR beyond included hours, custom content, advanced hunting/forensics, extended retention, premium support.
- Per-asset & storage references
| Metric | Pricing (INR) | Pricing (USD) |
| Endpoints | ₹266 – ₹1,331 per endpoint/month | $3 – $15 |
| Users | ₹178 – ₹710 per user/month | $2 – $8 |
| Retention Storage | ₹4.44 – ₹22.19 per GB-month | $0.05 – $0.25 |
To get a tailored SOCaaS pricing and coverage plan for your Environment
What are common challenges or risks?
Here are some common challenges or risks:
- Vendor lock in and poor portability of detections, playbooks, and schemas.
- Reduced visibility into tooling changes, rule logic, and incident handling.
- Data privacy, residency, and cross border transfer risk in multitenant platforms.
- Integration complexity across SIEM, EDR, identity, cloud, OT, and custom apps causing blind spots.
- False positives and alert fatigue from weak tuning and context.
- SLA gaps for detection start, investigation start, and containment authority off hours.
- Limited customization of use cases and runbooks versus an internal build.
- Business context gaps—missed crown jewels, critical processes, or change windows.
- Cost volatility from ingest based pricing, bursty telemetry, and long retention.
- Provider dependency risks from outages, analyst turnover, or shift quality variance.
- Chain of custody and evidence handling issues that hinder forensics and legal needs.
- Compliance mapping mismatches and incomplete audit artifacts for specific frameworks.
- Communication and escalation failures across time zones or with third party IT partners.
- Security of the provider itself, including insider risk and supply chain exposure.
- Coverage gaps for shadow IT, unmanaged endpoints, or newly onboarded subsidiaries.
- Limited transparency into detection efficacy (true positive rate, dwell time).
- Long onboarding timelines delaying time to value in complex environments.
What is the difference between SOCaaS and MDR?
Here is the difference between SOCaaS and MDR:
| Criterion | SOCaaS (SOC as a Service) | MDR (Managed Detection and Response) |
| Scope | Service that provides organizations an entire security operations center across endpoints, network, cloud, identity, and SaaS. | Focused on threat detection and remote response, primarily endpoint-centric with limited network/cloud add-ons. |
| Primary functions | 24x7 monitoring, triage, investigation, governance, threat hunting, reporting—broader security functions. | Containment and remediation on managed hosts; targeted investigations. |
| Tooling and data | Ingests diverse sources (SIEM, cloud logs, identity, NDR) for comprehensive visibility. | Provider-controlled EDR stack and its telemetry. |
| Operations model | Operates as an external SOC vendor running people, process, and platform end-to-end. | Acts as incident responders for enrolled assets. |
| Outcomes | Cross-environment detection, root-cause analysis, continuous improvement; benefits of SOCaaS for program maturity. | Rapid host-level containment of security threats. |
| Ownership | Eliminates need to build an in-house SOC by delivering a managed security service. | Augments internal team for targeted response. |
| When to choose | Best when comprehensive security management and 24x7 operations are required. | Best when the main gap is endpoint-focused detection and response. |
What is the Difference Between Managed SOC and Other Models?
| Model | Key difference from Managed SOC | Best fit |
| Managed SOC | Full outsourced SOC: people + process + platform, 24/7 ops | Teams wanting end-to-end SOC without building in-house |
| MDR | Endpoint-centric detection/response; narrower scope | Need rapid endpoint containment, not full SOC |
| Managed SIEM | Tool + rules managed; you still investigate/respond | Org with analysts who want SIEM integration offloaded |
| XDR | Unified detections within one vendor stack; not full SOC ops | Standardized on a single ecosystem, want tighter integration |
| Co-managed SOC | Shared duties/runbooks with provider | Keep oversight while adding external coverage |
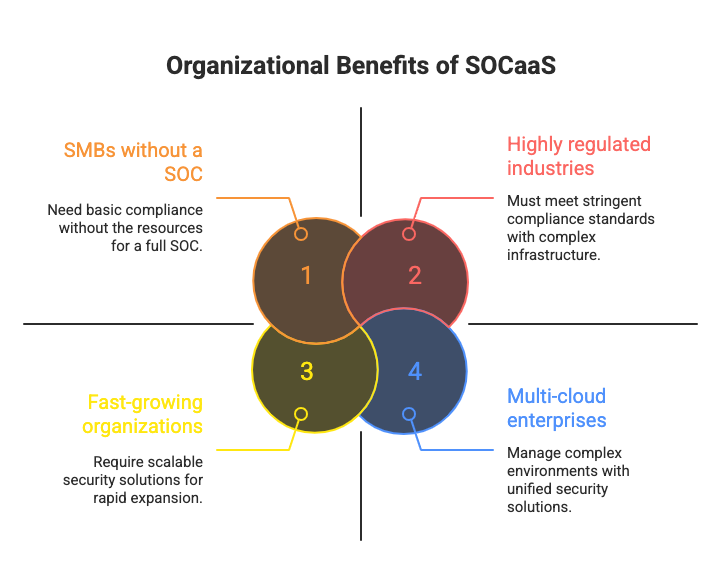
What types of organizations benefit?
Here are types of organizations that benefit from SOCaaS for scalability:
- SMBs and mid-market without a SOC — need 24×7 monitoring and response without hiring a full team.
- Fast-growing organizations — rapid asset growth demands scalable coverage and quick onboarding.
- Highly regulated (finance, healthcare, government, critical infrastructure) — must evidence controls, retention, and audit trails.
- Multi-cloud or hybrid enterprises — unified detection and response across AWS, Azure, GCP, and on-prem.
- Distributed or 24×7 operations (retail, logistics, manufacturing) — continuous coverage across time zones and sites.
- Companies with high-value data or elevated risk (SaaS, fintech, biotech) — tighter MTTD/MTTR and proactive threat hunting.
- OT/ICS environments (energy, utilities, factories) — specialized monitoring for industrial protocols and safety constraints.
How does a soc as a service solution work in real environments?
In real environments, SOC as a service solutions run as an always-on operational layer that ingests security signals, turns them into prioritized incidents, and drives response actions across your existing stack. A typical enterprise setup connects cloud logs, endpoints, identity, network telemetry, and SaaS audit trails into a single detection pipeline. The provider then standardizes the data, correlates events into attack stories, and applies escalation rules so your team only sees incidents that need a business decision.
The practical difference is workflow. Instead of “alerts,” you get tickets with evidence, timelines, and recommended containment steps. For example, when an attacker uses a stolen identity token to access Microsoft 365 and then pivots to a cloud workload, the SOC maps the chain of activity, isolates the impacted endpoint, blocks the session, and preserves artifacts for forensics. The service also runs recurring tuning cycles so detections match your environment and reduce false positives
Explore our overview of top soc service providers in USA to see how leading vendors stack up on coverage, response times, and compliance expertise. Use it as a benchmark to choose the SOC partner that best matches your organisation’s risk profile and growth plans.
FAQs
Q1. What are the 3 tiers of SOC?
Tier 1 – Monitor alerts and escalate
Tier 2 – Investigate and respond
Tier 3 – Hunt threats and improve tooling
Q2. What is SOC used for?
A SOC is used to continuously monitor, detect, investigate, and respond to cyber threats across an organization’s IT environment.
Q3. Which is better, NOC or SOC?
Neither is “better” overall: a NOC focuses on uptime and performance, while a SOC focuses on security, and mature organizations typically need both.