This article explains what SIEM is and why it matters, then walks through how SIEM works end to end. It covers benefits, primary use cases, and key components and features. You’ll see how SIEM compares with adjacent tools, what cloud SIEM changes, and how AI and machine learning enhance outcomes. We outline integrations across the stack, implementation best practices, and common challenges and limitations. Finally, we address how to choose a SIEM, the evolution and future of SIEM, compliance and governance, practical rule examples, and concise FAQs. A SOC is the 24/7 team and process, and SIEM is the analytics backbone; together they ingest, correlate, and act on security data to cut MTTD/MTTR and improve compliance.
Table of Contents
What is SIEM?
Security Information and Event Management (SIEM) is a security analytics and monitoring system that ingests logs and events from across your environment, normalizes them, correlates related activity, and surfaces high-fidelity detections for investigation and response. The SIEM full form is Security Information and Event Management. In practice, a SIEM platform centralizes telemetry from endpoints, servers, identity providers, cloud services, firewalls, and applications to give security teams a single, queryable view of risk. This is the accepted SIEM definition in cybersecurity.
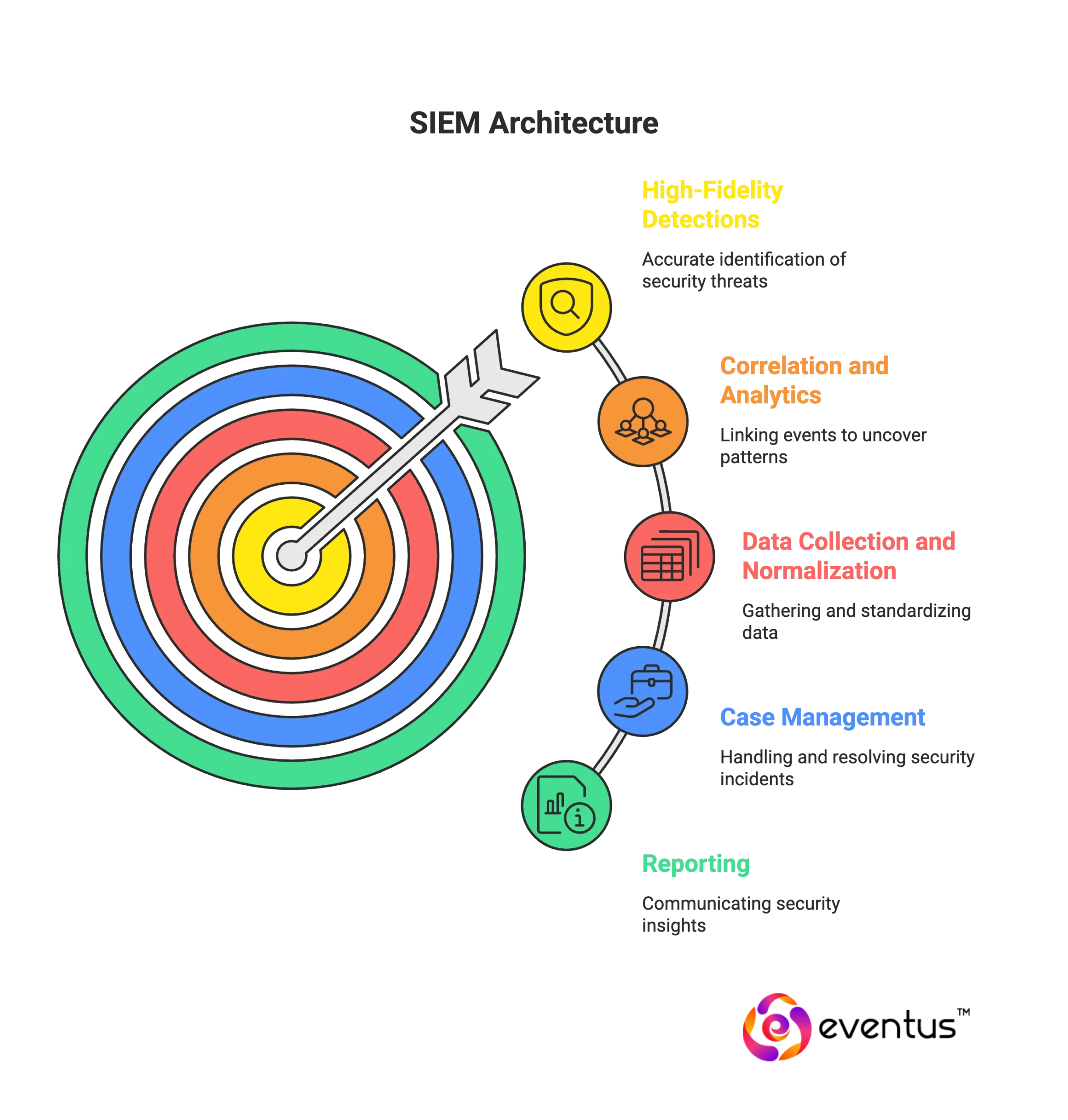
A modern SIEM architecture includes data collection and normalization, correlation and analytics, detection content, case management, and reporting. SIEM monitoring applies rules, behavioral analytics, and threat-intel enrichment to identify suspicious patterns in near real time. Many organizations consume SIEM as a service to offload infrastructure while retaining control over detections, or adopt SIEM services from an MSSP for 24/7 coverage. This is what a SIEM system is—and what SIEM stands for—in cyber security terms..
Why does it matter?
Why it matters:
- It delivers centralized visibility across hybrid networks and cloud, enabling faster triage and incident response.
- It improves threat detection with correlation that a single tool cannot achieve, reducing blind spots in SIEM security operations.
- It supports SIEM compliance by producing auditable reports and retention aligned to regulations.
- It enhances risk reduction by prioritizing alerts with context (user, asset, identity, geolocation) so analysts focus on what matters.
- It scales with your business via flexible ingestion, storage, and analytics—core SIEM benefits for modern environments.
How does SIEM work end to end?
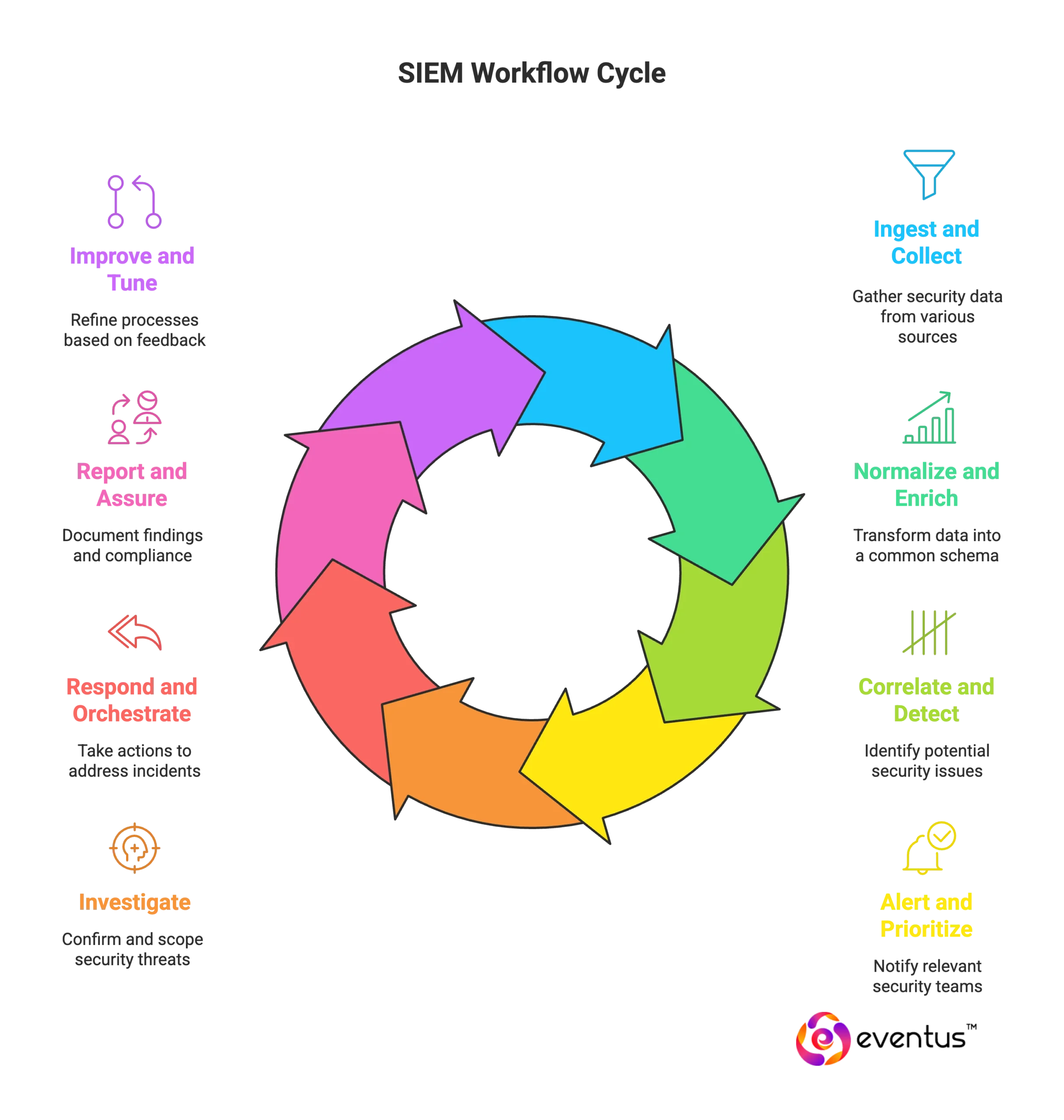
End-to-end workflow of a SIEM system (Security Information and Event Management):
- Ingest and collect
- Agents, APIs, and connectors pull security data and event data from endpoints, servers, identity providers, cloud, network, and security systems.
- Log management handles parsing, timestamps, and source integrity for a modern SIEM or managed SIEM solution.
- Normalize and enrich
- Records are transformed to a common schema (security information management).
- Enrichment adds user and asset context, geo, threat intelligence, and vulnerability data so security analysts can analyze security with fewer gaps.
- Correlate and detect
- Rules, statistical baselines, and machine learning correlate security events across sources (security event management).
- The SIEM tool scores risk and flags a potential security issue or security incident tied to users and hosts.
- Alert and prioritize
- The SIEM platform de-duplicates, suppresses noise, and applies risk and confidence scoring.
- Playbooks and use-case logic ensure the right security team in the security operations center is notified.
- Investigate
- Analysts pivot across timelines, entities, and lateral movement paths to confirm the security threats and scope.
- The SIEM provides graph views, evidence collections, and case records that help security teams maintain chain of custody.
- Respond and orchestrate
- Integrated SOAR and security orchestration trigger actions such as account disable, host isolation, or block rules.
- Tickets are created in ITSM tools; containment and eradication steps respond to security incidents consistently.
- Report and assure
- Dashboards and compliance reports document detections, response times, and control effectiveness to improve security posture.
- Metrics feed weekly and monthly reviews for security operations and executive security management.
- Improve and tune
- Feedback from incidents refines correlation, data onboarding, and SIEM use cases.
- New integrations and detections are added as the environment evolves; SIEM solutions can help extend coverage through built-in content and third-party integration.
What are the benefits?
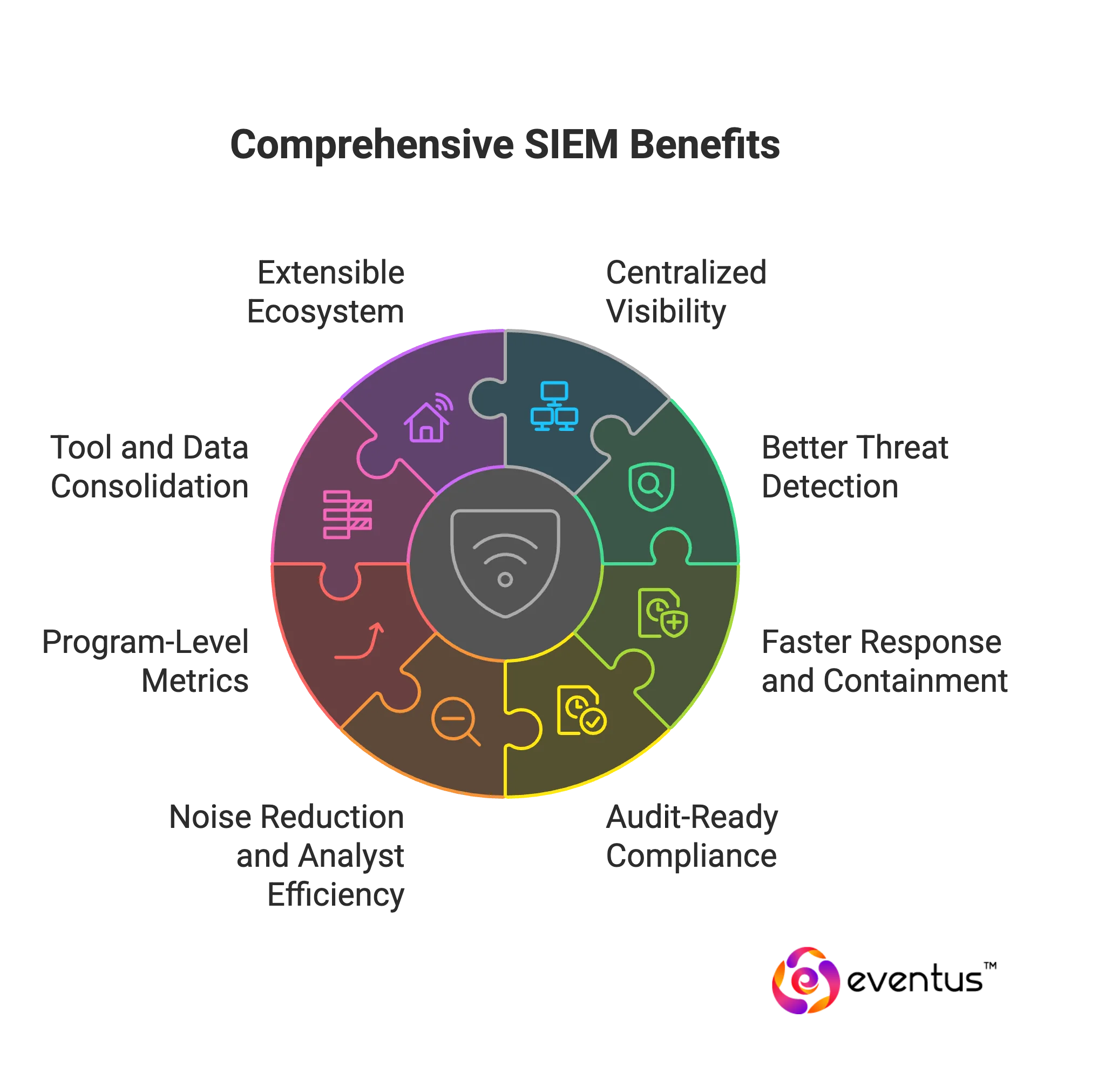
Here are the benefits of SIEM:
- Centralized visibility
Consolidates logs and events across endpoints, network, cloud, and identity into one security monitoring plane for faster, complete investigations (comprehensive security) - Better threat detection
Correlates multi-source signals using SIEM technologies (rules, UEBA, threat intel) to surface high-fidelity alerts a single security tool would miss - Faster response and containment
Streamlines triage, case management, and automated actions (disable accounts, isolate hosts), cutting mean time to detect and respond - Audit-ready compliance
Produces immutable records, retention, and mapped reports (PCI DSS, ISO 27001, HIPAA), reducing audit effort and risk - Noise reduction and analyst efficiency
Deduplicates alerts, applies risk scoring and context so analysts focus on the highest-impact incidents - Program-level metrics
Tracks control effectiveness, attacker dwell time, and coverage gaps to guide security investment and improve resilience - Tool and data consolidation
Replaces fragmented point products, standardizes schemas, and lowers total cost of ownership through shared analytics and storage - Extensible ecosystem
Integrates with EDR, IAM, cloud, and ticketing to operate as the backbone security solution and cybersecurity solution for the SOC.
What are the primary SIEM use cases?
Here are the primary SIEM use cases:
- Comprehensive security monitoring: A SIEM collects security data from endpoints, network, identity, cloud, and apps, aggregates and analyzes security data in one place, and delivers a centralized view of security events for a precise view of an organization’s security.
- Real-time threat detection and alerting: Correlates signals to surface security alerts and security threats in real time so security teams identify and respond to security threats faster; SIEM solutions enhance threat detection beyond single tools.
- Incident investigation and response: Preserves timelines and evidence, supports root-cause analysis, and triggers security orchestration and automation response actions (isolate host, disable account) to speed responding to security incidents.
- Compliance and audit readiness: Produces retention, reports, and controls mapping; this SIEM simplifies evidence collection for PCI DSS, ISO 27001, HIPAA—strengthening overall security posture.
- Insider threat and UEBA: Analyzes security data for anomalous user or entity behavior (privilege misuse, impossible travel) to reduce security breaches originating inside the organization.
- Lateral movement and advanced attack detection: Correlates east-west activity and authentication patterns so SIEM solutions can help security teams spot stealthy paths used by attackers.
- Cloud and SaaS monitoring: Modern SIEM platforms ingest telemetry from IaaS, PaaS, and SaaS to unify security events across the network and cloud for comprehensive security monitoring.
- Endpoint, identity, and application monitoring: Ties EDR, IAM, and app logs together so siem collects and analyzes security data from various sources to catch credential abuse, risky processes, and suspicious API calls.
- Third-party and supply-chain risk monitoring: Uses integration with vendor systems and CASB to monitor partners and help security analysts identify external compromise signals early.
- Vulnerability exposure and risk-based prioritization: Correlates scanner findings with detections so siem solutions also focus response on exploitable assets that impact overall security posture.
- Fraud and payment abuse detection: Models high-risk transactional patterns (ecommerce, fintech) using correlation and behavior analytics to cut losses.
- Operational technology and IoT visibility: Normalizes logs from OT gateways and IoT fleets so a SIEM solution extends coverage beyond IT to critical environments.
- MSSP and managed security service delivery: Multi-tenant use where a provider uses siem software to deliver 24x7 monitoring and security services for multiple clients efficiently.
- Correlation hub with XDR: Acts as the analytics backbone in SIEM and XDR deployments, enriching detections and giving a unified view of an organization's security across controls.
What are the key components and features?
- Data collection and ingestion: Key components of a SIEM start with connectors, agents, and APIs. SIEM systems collect logs, metrics, and telemetry from endpoints, network, identity, cloud, and apps, then collects and analyzes security events at scale.
- Parsing, normalization, and schema: Components of a SIEM solution include pipelines that standardize fields and timestamps so modern SIEM solutions can correlate diverse sources reliably through combined security information management.
- Context enrichment: Joins asset inventory, identity data, vulnerabilities, and geolocation so analysis of security signals is risk aware and investigation ready.
- Correlation and detection engine: Rules, statistical baselines, and behavior analytics generate high-fidelity alerts. This is where core SIEM capabilities transform raw events into actionable detections.
- Threat intelligence integration: Ingests feeds and indicators, matches against events, and automates scoring to improve precision.
- User and entity behavior analytics: Learns typical activity and flags anomalies like impossible travel or privilege misuse.
- Search and investigations: Fast queries, timelines, and graph pivots help analysts reconstruct attack paths and validate scope.
- Case management and workflow: Evidence capture, tasking, and ticketing integrations coordinate the approach to security across teams.
- Reporting and compliance: Prebuilt mappings, dashboards, and attestations satisfy audit requirements and prove control effectiveness.
- Dashboards and visualization: Real-time posture views and KPI tracking surface coverage gaps and operational trends.
- Automation and integrations: Playbooks and API hooks enrich alerts and trigger downstream actions in EDR, IAM, and ITSM. SIEM solutions include expansive ecosystem connectors that siem can help extend.
- Scalability and retention: Hot, warm, and cold storage tiers balance performance and cost; multi-tenant controls support service providers and large enterprises.
- Security and reliability of the platform: Role-based access, encryption, health monitoring, and high availability protect the SIEM itself.
- Content management: Versioned detection packs, testing harnesses, and drift control keep detections current as threats evolve.
- Positioning with adjacent tools: Understand differences between SIEM and XDR to design complementary coverage rather than duplication.
- Fit to mission: SIEM solutions help only when aligned to use cases; organizations should consider their specific security needs and data flows during SIEM implementation and when they choose a SIEM in a dynamic SIEM market.
How do SIEM and other security solutions compare?
| Comparison | Primary purpose | Scope / telemetry | Strengths | Limitations | How they work together |
| SIEM vs Log management | SIEM correlates, detects, investigates; log management stores and searches | SIEM: multi-domain (endpoint, identity, network, cloud). Log mgmt: raw logs | Cross-source analytics, detections, case management | Log tools lack correlation and response workflows | Use log store for retention; SIEM pulls/queries it for detections and investigations |
| SIEM vs SOAR | SIEM finds and prioritizes threats; SOAR orchestrates and automates response | SIEM: analytics on events; SOAR: playbooks across tools | Reduced MTTR via automation and tickets | SOAR depends on quality detections | SIEM supplies context; SOAR executes containment and remediation |
| SIEM vs XDR | SIEM is telemetry-agnostic; XDR is control-stack-centric detection/response | SIEM: any source; XDR: vendor ecosystem (EDR, email, network) | Breadth and compliance (SIEM); curated depth and speed (XDR) | XDR can be vendor-locked; SIEM can be cost/complexity heavy | Feed XDR alerts into SIEM to enrich enterprise-wide investigations |
| SIEM vs EDR | SIEM: enterprise correlation; EDR: endpoint detection and containment | EDR: process, file, memory on hosts | Host-level visibility and kill-chain stops | EDR lacks cross-domain context | Ingest EDR alerts/telemetry into SIEM for lateral movement and identity context |
| SIEM vs NDR | SIEM: fusion analytics; NDR: deep network behavior analytics | NDR: packets/flows, east-west traffic | High-fidelity network detections | Limited identity/endpoint linkage | Combine NDR signals with identity and EDR in SIEM for full path analysis |
| SIEM vs UEBA | SIEM: platform; UEBA: behavior modeling capability | UEBA: user/entity baselines and anomalies | Insider and misuse detection | UEBA alone lacks case workflow | Embed UEBA in SIEM to score risk and prioritize investigations |
| SIEM vs Data lake / observability | SIEM: security analytics and compliance; lake: cheap storage and generic query | Lake: scalable storage; SIEM: detection content, cases, reports | Cost-effective retention (lake); security outcomes (SIEM) | Lake lacks security semantics | Offload cold data to lake; keep real-time detections and cases in SIEM |
| SIEM vs Managed SOC | SIEM: technology; managed SOC: 24×7 service operating the stack | SOC uses SIEM, EDR, SOAR, ND |
What is cloud SIEM and how is it different?
Cloud SIEM is a SIEM platform delivered as a cloud-native service. In practice, cloud SIEM performs the same core functions as any SIEM system—centralized SIEM monitoring, correlation of SIEM events, investigation, reporting, and SIEM compliance—but the control plane, data lake, and analytics run in the provider’s cloud. This answers what is SIEM in cyber security when deployed as a managed, elastic service rather than self-hosted software.
How is it different from on-prem SIEM?
- Deployment and operations
Cloud SIEM is provisioned by the vendor; upgrades, scaling, and SIEM management are handled as SIEM as a service, reducing admin overhead compared with self-managed SIEM technology. - Scalability and performance
Elastic ingestion and compute handle bursty telemetry without capacity planning, unlike fixed on-prem SIEM architecture. - Cost model
Consumption pricing (ingest, storage, analytics) replaces hardware and perpetual licenses, changing total cost dynamics for cybersecurity SIEM. - Data onboarding
Native connectors for cloud logs, SaaS apps, and modern pipelines simplify how a SIEM platform collects and analyzes security events across hybrid estates. - Analytics and content
Cloud SIEM typically delivers continuous detection content updates, UEBA, and threat-intel enrichment as part of the service, accelerating SIEM security outcomes. - Resilience and availability
Built-in redundancy and managed SLAs reduce outage risk compared with single-site deployments. - Compliance and data residency
Region selection, retention tiers, and access controls address SIEM compliance and sovereignty; on-prem may offer tighter physical control but requires more effort. - Security model
Provider-managed hardening and isolation protect the service; customers still own use-case tuning, access governance, and response workflows in SIEM cyber security.
How do AI and machine learning enhance SIEM?
AI and machine learning elevate SIEM by learning normal behavior and flagging anomalies, producing high-precision detections with fewer false positives. They enrich events with threat intelligence, adapt correlation thresholds from outcomes, and route alerts by technique and business impact. Automated investigations assemble timelines and entity graphs; natural-language queries speed analysis. Models optimize SOAR actions, uncover new campaigns, and score identity and asset risk. They also monitor data quality, govern model drift, and apply cost-aware analytics that preserve detection fidelity in cloud SIEM.
How do you implement SIEM successfully?
- Define objectives and success metrics
- Map primary use cases (threat detection, compliance, insider risk) to measurable KPIs (MTTD, MTTR, alert precision, false-positive rate, data coverage).
- Set targets, e.g., MTTD ≤ 15 minutes for high severity, MTTR ≤ 60 minutes, alert precision ≥ 70 percent, false positives ≤ 20 percent, data coverage ≥ 90 percent of critical assets.
- Scope and data inventory
- Produce a system-of-record for all log sources (EDR, IAM, DNS, proxy, email, SaaS, cloud control plane, firewalls, servers, AD, vulnerability scans).
- Prioritize onboarding by risk and business criticality.
- Select architecture and deployment model
- Choose cloud SIEM or self-managed based on scale, skills, data residency, and cost ceilings.
- Define ingestion patterns (agents, syslog, APIs), retention tiers (hot/warm/cold), and high availability.
- Plan governance and roles
- Establish RACI across security operations, platform engineering, IT, and compliance.
- Enforce access controls, least privilege, key management, and change management for detection content.
- Onboard and normalize data
- Standardize to a common schema; validate timestamps, hostnames, user IDs, and network context.
- Automate data quality checks (schema drift, source health, event lag thresholds).
- Build detection content deliberately
- Start with high-value detections tied to MITRE ATT&CK techniques observed in your environment.
- Include baseline correlation rules, UEBA models, and threat-intel matches with clear severities and runbooks.
- Integrate SOAR and ITSM
- Connect containment actions (host isolation, token revocation, rule pushes) and ticketing workflows.
- Gate automation with safeguards (approval steps, blast-radius limits).
- Design investigations and case management
- Standardize timelines, evidence capture, and chain of custody.
- Provide entity graphs, pivot queries, and playbook links inside cases.
- Compliance and reporting
- Map controls to frameworks (PCI DSS, ISO 27001, HIPAA) and prebuild audit reports.
- Align retention and immutability with legal and regulatory requirements.
- Performance, scale, and cost management
- Right-size ingestion (filters, field selection, sampling) without losing detection fidelity.
- Track cost per GB and cost per qualified alert; tune noisy sources first.
- Tuning and continuous improvement
- Run weekly rule reviews and monthly use-case retros.
- Suppress benign patterns, adjust thresholds, and retire low-value alerts using closed-case feedback.
- Training and readiness
- Train analysts on query languages, triage procedures, and playbooks.
- Conduct quarterly tabletop exercises and semiannual red-team or purple-team validations.
- Telemetry coverage management
- Monitor coverage drift; require new systems and apps to pass a “logging readiness” checklist before go-live.
- Enforce minimum fields for every source (user, asset, action, result, time, origin, destination).
- KPIs and executive reporting
- Report MTTD, MTTR, alert volume, precision, automation rate, and coverage trends to leadership.
- Tie improvements to risk reduction and incident cost avoidance.
- Security of the SIEM itself
- Segment the platform, enable MFA, encrypt at rest and in transit, and audit admin activity.
- Implement backup, disaster recovery objectives (RPO/RTO), and failover tests.
- Cutover and stabilization
- Phase rollout by business unit; run parallel operations until KPI thresholds are met.
- Document handoffs, escalation paths, and 24/7 on-call expectations.
What challenges and limitations should you expect with SIEM?
- Data volume and cost escalation
- Ingestion-based pricing grows with log expansion; GB/day can become TB/day as sources and fields increase.
- Duplicate, verbose, or low-value logs inflate storage and query costs without improving detections.
- Signal quality and false positives
- Noisy correlation rules and poorly scoped use cases produce alert fatigue and lower analyst precision.
- Missing context (asset criticality, identity ties, geo) degrades triage accuracy.
- Integration complexity and coverage gaps
- Heterogeneous sources (cloud, SaaS, OT, custom apps) require parsers and normalization; gaps create blind spots.
- API limits, throttling, and timestamp drift break end-to-end timelines.
- Performance and scalability constraints
- High-cardinality fields and long look-back windows increase query latency.
- Hot/warm/cold tier transitions can slow investigations if data is archived too aggressively.
- Detection content drift
- Static rules decay as attacker TTPs change; unmaintained UEBA baselines misclassify new business patterns.
- Threat-intel mismatches (stale indicators, poor confidence) cause both misses and noise.
- Operational skill and staffing gaps
- Effective SIEM operation needs engineering (parsers, pipelines), content authors (detections), and responders; shortages extend MTTD/MTTR.
- Query language proficiency is a constraint for complex investigations.
- Automation risk and SOAR dependencies
- Over-aggressive playbooks can cause self-inflicted outages; under-automated flows stall at human bottlenecks.
- Response actions depend on downstream tool reliability and permissions.
- Compliance, privacy, and data residency
- Regional storage and retention mandates conflict with centralized analytics.
- Sensitive data in logs (PII, secrets) requires masking, tokenization, or field-level controls.
- Platform security and reliability
- The SIEM itself is a target; weak RBAC, audit gaps, or unencrypted channels expose investigations and data.
- Single-region or single-AZ deployments increase outage risk.
- Vendor lock-in and portability
- Proprietary schemas, rule languages, and dashboards hinder migration.
- Egress fees and closed ecosystems limit cost control and tool choice.
- Measurement and ROI attribution
- Without baselines (coverage, precision, MTTD/MTTR), improvements are hard to prove; SIEM can become a cost center rather than a control plane.
- Onboarding friction and change management
- New apps and services often go live without “logging readiness,” causing chronic gaps.
- Schema changes upstream (version bumps) silently break parsers and detections.
- Edge and OT limitations
- Legacy protocols and intermittent connectivity restrict telemetry depth outside IT networks.
How has SIEM evolved and where is it heading?
SIEM evolved from separate SIM and SEM tools in the early 2000s into a unified platform for collection, correlation, and reporting; from 2010 to 2016 it matured with content-driven correlation, threat intel matching, dashboards, distributed search, and longer retention; from 2016 to 2019 it embedded UEBA, aligned detections to MITRE ATT&CK, and standardized identity and asset context; from 2019 to 2022 cloud-native SIEM delivered elastic scale, normalized SaaS and cloud control-plane logs, tighter EDR NDR IAM ITSM integrations, and detections as code; from 2022 to 2024 it converged with SOAR for playbooks, approvals, evidence handling, and used data-lake offload; by 2023 to 2025 AI copilots and anomaly models summarized alerts, built timelines, and prioritized risk.
Ahead, SIEM is converging with SOAR and XDR on a shared plane, adopting content as code with CI and canary releases, using cost-aware ingestion and lakehouse patterns, shifting to identity-first analytics, applying governed AI, embracing open schemas for portability, reporting outcomes like MTTD, MTTR, containment and dwell time, linking exposure to active exploit paths, extending coverage to edge, OT and IoT, and building privacy and sovereignty controls into the design.
FAQs
1. Can SIEM prevent cyberattacks or only detect them?
Ans. : SIEM primarily detects and investigates threats by correlating events; it does not, by itself, block attacks.
When integrated with preventive controls or SOAR, SIEM can trigger containment (isolate hosts, revoke tokens, block IOCs), reducing dwell time and blast radius.
2. Which industries benefit most from SIEM?
Ans: Heavily regulated and high-risk sectors benefit most: financial services, healthcare, government, energy and utilities, telecom, and payments/ecommerce where compliance and breach impact are high. Technology and SaaS, manufacturing, and large retailers also gain from centralized monitoring and rapid incident response across complex, distributed environments.
3. How is SIEM evolving with cloud security?
Ans: SIEM is shifting to cloud-native delivery with elastic ingestion, lake/lakehouse storage, native SaaS/cloud connectors, and continuously updated detections—improving scale, coverage, and time-to-value.
4. What is the typical cost of implementing SIEM?
Ans: Cloud SIEM is typically consumption-priced—about $2–$6 per GB ingested plus $0.02–$0.15 per GB-month for storage; self-managed adds hardware, licensing, and admin overhead.
5. How does SIEM assist with compliance in practice?
Ans: SIEM maps events to control frameworks (e.g., PCI DSS, ISO 27001, HIPAA), enforces retention and immutability, and generates audit-ready reports and evidence trails with timestamps, users, and actions.