This article explores the fundamentals and practical value of a threat intelligence platform (TIP) for modern cybersecurity. It answers key questions including what a TIP is, how it differs from threat data repositories, and how it works. The discussion covers the stages of the threat intelligence lifecycle, the key features of a platform, and its support for TIP-to-TIP and TAXII standards. It also highlights the benefits, types, and sources of threat intelligence, explains who uses TIPs, how they are implemented, the metrics that define success, and how they help prevent cyber attacks.
Table of Contents
What is a threat intelligence platform?
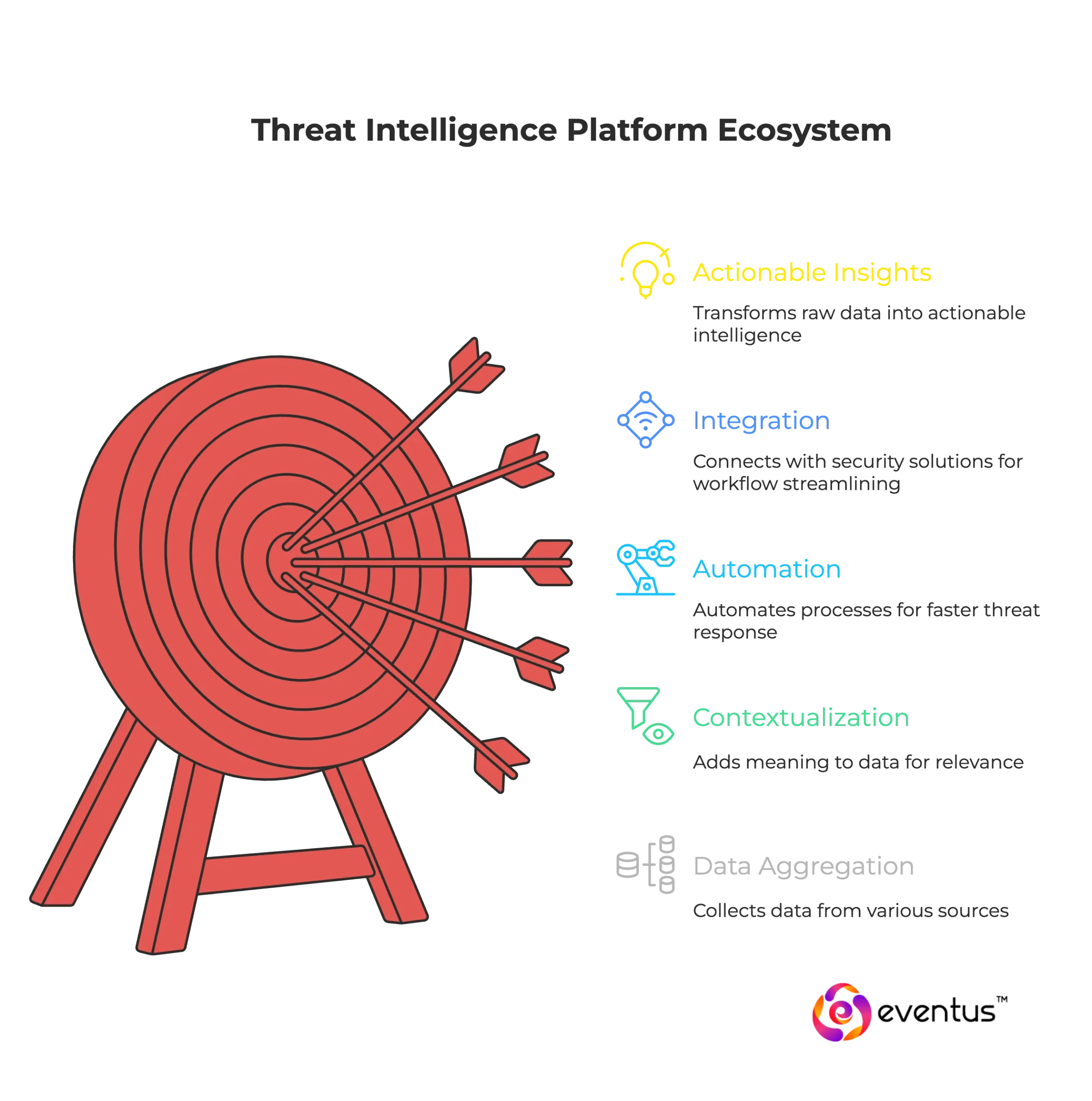
A threat intelligence platform (TIP) is a dedicated cybersecurity solution designed to collect, aggregate, and analyze threat information from various sources to help organizations detect and respond to potential threats more effectively. It transforms raw cyber threat intelligence into actionable insights that a security team can use to strengthen defenses and support decision-making across the security operations center.
How does a threat intelligence platform differ from threat data repositories?
| Aspect | Threat Intelligence Platform (TIP) | Threat Data Repository (TDR) |
| Nature of information | Aggregates data from various sources and enriches it into contextual, actionable cyber threat intelligence. | Stores raw threat information such as IPs, domains, hashes, and indicators of compromise (IOCs). |
| Context | Correlates intelligence with SIEM, endpoint, and security operations data to highlight relevant security threats. | Provides unprocessed data without deeper meaning or prioritization. |
| Actionability | Transforms intel into actionable insights that support real-time threat detection and response. | Functions as a static reference library for threat information. |
| Automation | Can automate enrichment, scoring, and alerting to help the security team respond faster to potential threats.
|
No automation; requires manual effort to use. |
| Integration | Integrates with SIEM, SOAR, and other security solutions to streamline workflows in the security operations center. | Typically standalone with limited connectivity. |
| Support for SOC | Directly supports security operations center analysts with alerts, dashboards, and advanced threat detection. | Useful for retrospective checks but not directly tied to workflows. |
| Use cases | Real-time threat actor tracking, malware campaign detection, TTP correlation, and prioritization of potential threats. | Historical lookups, verification of IOCs, reference storage. |
How does a TIP work?
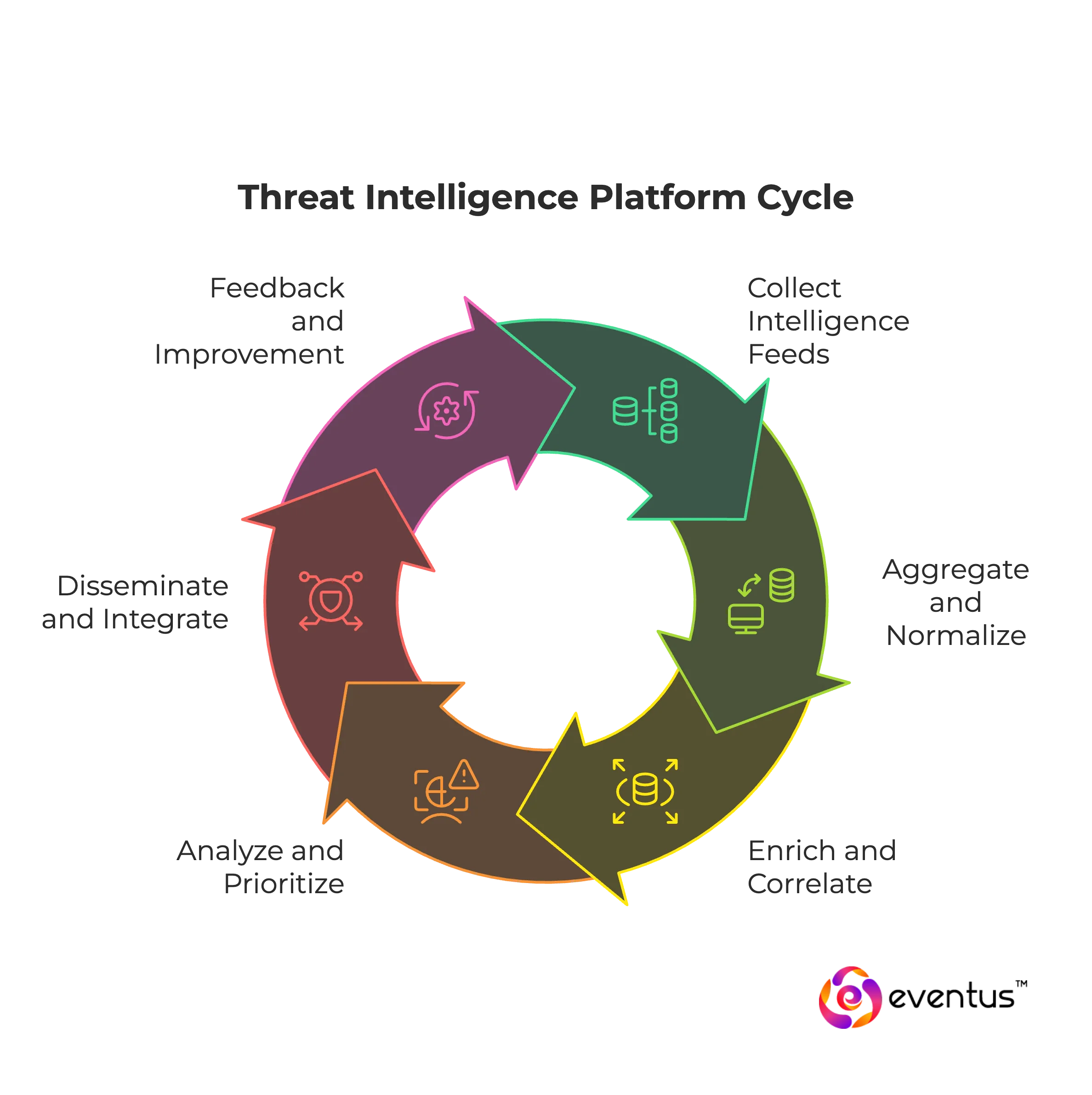
A threat intelligence platform (TIP) works by transforming raw threat information into structured, actionable insights that security teams can use to defend against an evolving threat landscape. The process involves multiple coordinated stages:
- Collection of intelligence feeds: The platform gathers data from open source intelligence, commercial providers, and internal telemetry. These feeds may include IP addresses, domains, file hashes, and TTPs (tactics, techniques, and procedures) used by attackers.
- Aggregation and normalization: Data from various sources is aggregated and standardized into a consistent format. This ensures that disparate feeds can be compared, correlated, and analyzed effectively.
- Enrichment and correlation: The TIP enriches raw data with context, such as historical activity, links to known threat actors, and relevance to a specific environment. Correlation across feeds and incidents helps identify patterns within the broader threat landscape.
- Analysis and prioritization
Using automation and contextual scoring, the platform filters out noise, highlights relevant intelligence, and prioritizes potential threats. This helps security teams focus on the most critical issues. - Dissemination and integration
The processed intelligence is distributed to security operations, integrated with SIEMs and other tools, and used to update detection rules or create proactive defenses. - Feedback and continuous improvement
Analysts provide feedback on intelligence accuracy, which the platform uses to refine processing, ensuring that future intelligence is more reliable and precise.
What are the stages of the threat intelligence lifecycle a platform supports?
A threat intelligence platform (TIP) supports the threat intelligence lifecycle by turning raw data into actionable insights for security operations teams. The stages are:
- Planning – Define intelligence needs and align with incident response priorities.
- Collection – Gather threat intelligence data from open-source intelligence, dark web monitoring, and commercial intelligence feeds.
- Processing – Aggregate and normalize indicators like IPs, domains, and malware hashes into usable formats.
- Analysis – Correlate data with MITRE ATT&CK, detect threat actors, and produce advanced threat intelligence.
- Dissemination – Share intelligence with SIEMs, SOC dashboards, and existing security tools for threat management.
- Feedback – Security teams refine intelligence, ensuring it stays relevant to evolving cyber risks.
What are the key features?
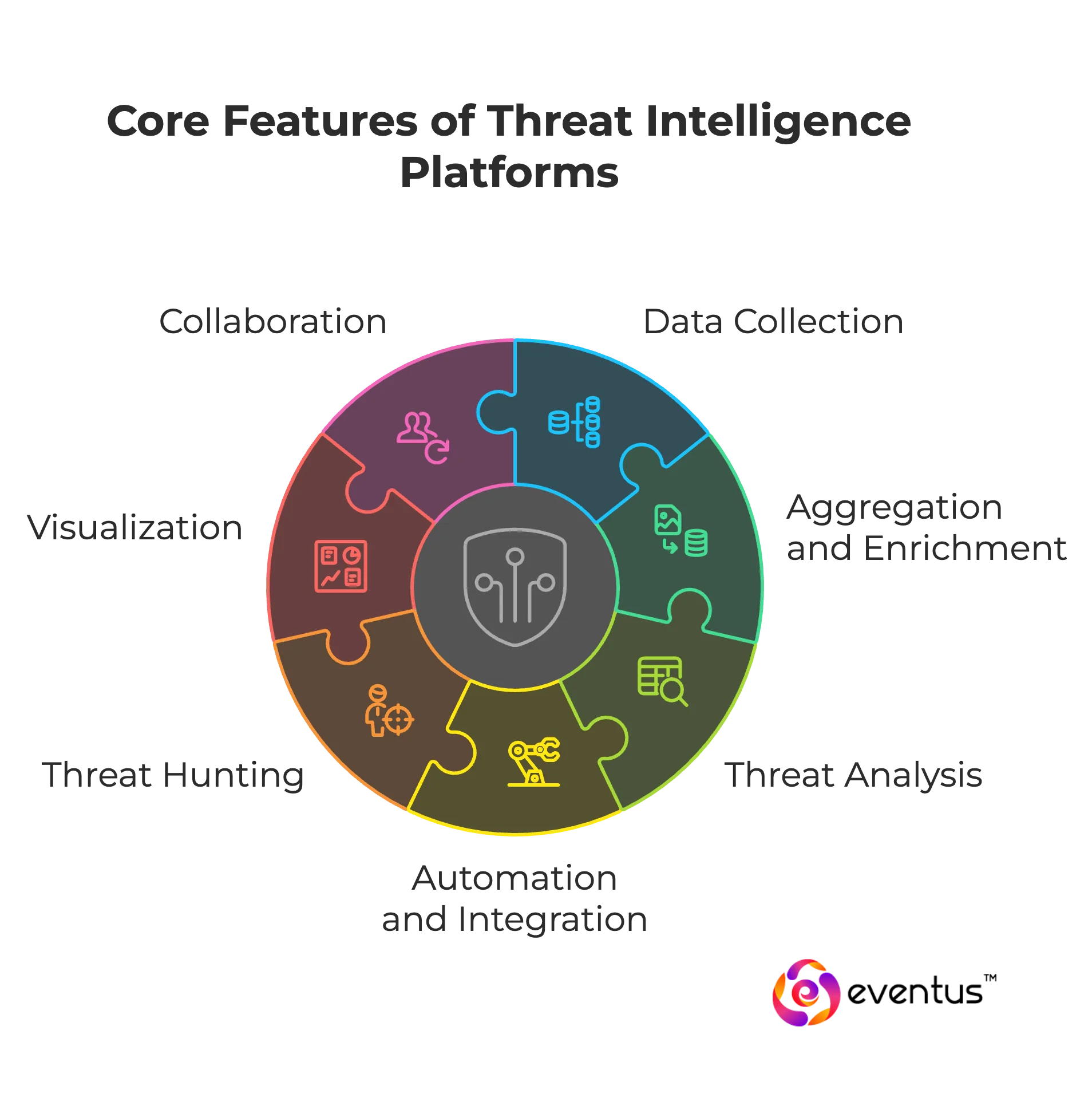
A threat intelligence platform (TIP) provides core features that make threat intel actionable for cyber defense. Key features include:
- Data collection – A threat intelligence platform collects threat indicator data from open-source intelligence, commercial threat intelligence products, and finished intelligence from vendors like Palo Alto Networks and Microsoft Defender.
- Aggregation and enrichment – Platforms aggregate threat intelligence feeds, normalize formats, and enrich threat intelligence data with context to understand their threat landscape.
- Threat analysis – TIP provides advanced threat intelligence capabilities, correlating threat indicators and highlighting top threat activity.
- Automation and integration – A threat intelligence platform automates threat intelligence management, integrates with SIEM and security tools, and delivers real-time threat alerts.
- Threat hunting – Intelligence provides support for threat hunting, enabling security operations teams to use threat intelligence against external threat actors and new threat campaigns.
- Visualization – Platforms enhance visibility with dashboards that present a comprehensive intelligence view of the threat landscape.
- Collaboration – Threat intelligence platforms offer sharing functions so security teams can make threat intelligence part of broader cyber defense practices.
How does the platform support TIP-to-TIP and TAXII standards?
A threat intelligence platform (TIP) supports TIP-to-TIP and TAXII standards to enable seamless sharing of threat intelligence across tools and teams.
- TIP-to-TIP – TIP vendors allow platforms to exchange common threat intelligence, making it easier for threat intelligence teams to aggregate intelligence sources, share types of threat data, and enhance the threat intelligence experience.
- TAXII – A TIP uses TAXII to automate structured sharing of threat intelligence feeds with partners, ISACs, and security information and event management (SIEM) systems. Best practices include configuring TAXII collections to manage threat information effectively.
- Integration – By following these standards, a threat intelligence solution provides consistent security information across existing security platforms, ensuring intelligence also supports automated detection and incident response.
What are the benefits?
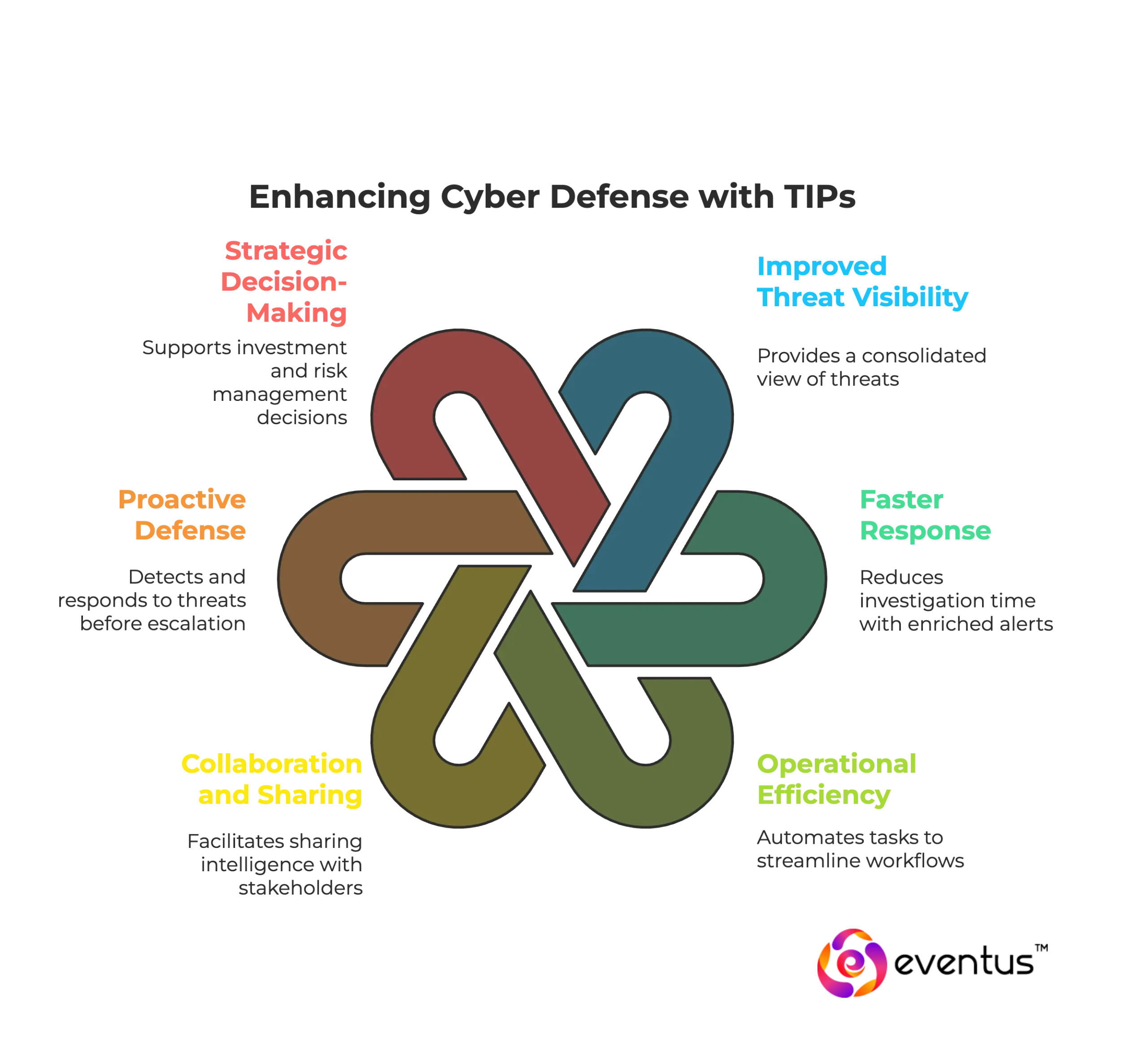
A threat intelligence platform (TIP) delivers measurable benefits by transforming raw data into actionable insights that strengthen an organization’s cyber defense.
- Improved threat visibility – The right platform provides a consolidated view of threats across multiple sources, helping organizations understand the threat landscape more clearly.
- Faster response – Intelligence helps reduce investigation time by enriching alerts with context, allowing security teams to mitigate cyber risks quickly.
- Operational efficiency – A platform provides automation to cut down manual workloads, streamline workflows, and improve the effectiveness of SOC analysts.
- Collaboration and sharing – TIPs make it easier to share threat intelligence with partners, industry groups, and stakeholders, strengthening collective defense.
- Proactive defense – By correlating indicators and mapping activity against frameworks like MITRE ATT&CK, intelligence helps detect and respond to threats before they escalate.
- Strategic decision-making – The right platform provides executives and security leaders with intelligence that supports investment decisions, risk management, and long-term resilience.
What are the types of threat intelligence?
There are four main types of threat intelligence, each serving a different purpose within an organization’s security strategy. Together, they create a layered approach that delivers actionable intelligence for both strategic and operational decisions.
- Strategic Threat Intelligence: High-level insights into global threat trends, adversary motives, and long-term risks. Helps executives and decision-makers align security investments with business objectives.
- Tactical Threat Intelligence: Details about adversary tactics, techniques, and procedures (TTPs). Provides actionable intelligence to SOC teams and analysts for improving detection rules and defense mechanisms.
- Operational Threat Intelligence: Focuses on specific campaigns, attack vectors, and threat actor activities. Enables security operations teams to anticipate and respond to active or emerging threats.
- Technical Threat Intelligence: Data on indicators of compromise (IOCs) such as malicious IPs, domains, file hashes, and malware signatures. Supports day-to-day threat detection, incident response, and immediate security operations.
What are the sources of threat intelligence data?
Sources of threat intelligence data fall into several main categories that together create actionable intelligence:
- Open-source intelligence (OSINT) – Public data from blogs, forums, research, and social media.
- Commercial feeds – Paid threat intelligence products offering curated, high-confidence data.
- Internal telemetry – Logs and alerts from SIEM, firewalls, and endpoint tools.
- Industry groups – ISACs and sector-sharing communities for common threat intelligence.
- Dark web monitoring – Intelligence from underground forums and marketplaces.
- Government advisories – Alerts from agencies like CISA or NCSC.
- Security vendors – Data from platforms and providers such as Microsoft Defender or Palo Alto Networks.
Who uses a threat intelligence platform?
A threat intelligence platform (TIP) is used by different teams depending on their role in cybersecurity:
- SOC teams – Correlate intelligence with SIEM alerts, prioritize threat alerts, and cut false positives.
- Threat intelligence teams – Collect, analyze, and enrich threat intelligence feeds to create actionable insights.
- Incident response teams – Use intelligence to investigate and contain attacks faster.
- Threat hunters – Apply intelligence to proactively detect threat activity and advanced attacks.
- Vulnerability management teams – Prioritize patches by linking exploits with real-world threat indicators.
- Executives and risk leaders – Rely on strategic intelligence to understand risks and guide cyber defense investments.
How do you implement a threat intelligence platform?
Implementing a threat intelligence platform (TIP) involves a clear, phased approach:
- Define needs – Identify intelligence priorities relevant to SOC, IR, and risk teams.
- Assess stack – Map SIEM, SOAR, EDR, and intelligence feeds the platform must connect with.
- Select platform – Choose the right platform based on scale, integration, and threat intelligence capabilities.
- Pilot – Test with a proof of concept to measure reduction in false positives and response time.
- Integrate – Connect with security tools, automate enrichment, and enable threat detection workflows.
- Operationalize – Deliver dashboards, threat alerts, and reporting to security operations teams.
- Refine – Gather feedback, adjust intelligence sources, and tune automation for evolving cyber risks.
What metrics matter for threat intelligence success?
The metrics that define threat intelligence success focus on detection, response, and actionable value:
- Detection effectiveness – Incidents detected with threat intelligence, reduction in false positives, percentage of advanced threats identified.
- Response efficiency – Mean time to detect (MTTD) and mean time to respond (MTTR), reduced investigation and remediation time.
- Intelligence quality – Accuracy, relevance, and percentage of intelligence judged actionable by analysts.
- Coverage – Number of intelligence sources integrated and visibility across types of threat activity.
- Operational impact – Automations triggered, intelligence used in threat hunting, incident response, and vulnerability management.
- Strategic value – Use of intelligence in executive reporting, risk decisions, and demonstrated ROI through reduced breaches or cost savings.
How does a TIP help prevent cyber-attacks?
A threat intelligence platform (TIP) helps prevent cyber attacks by delivering early, actionable intelligence that strengthens defenses:
- Early detection – Monitors intelligence feeds and IOCs to spot potential threats before attacks begin.
- Contextual analysis – Correlates threat activity and TTPs to anticipate attacker behavior.
- Integration – Feeds intelligence into SIEM, SOAR, and endpoint tools to automate blocking of malicious indicators.
- Threat hunting – Supports proactive searches for hidden or ongoing attacks.
- Faster response – Automates enrichment and prioritization of alerts, helping security teams mitigate cyber risks quickly.
In short, a TIP prevents attacks by combining early warning, actionable intelligence, and automated defenses to reduce exposure and attacker dwell time.
FAQ
Q: Is SIEM a threat intelligence platform?
Ans: No. SIEM collects and correlates security logs; it consumes threat intel but is not a Threat Intelligence Platform (TIP). It typically ingests feeds from a TIP to enhance correlation and alerting.
Q: What is a threat intelligence tool?
Ans: A threat intelligence tool aggregates, normalizes, and enriches threat data (IOCs, TTPs, actors) to deliver actionable insights and automate defenses. It helps analysts prioritize risks and push automated blocks to security controls.
Q: What are CTI platforms?
Ans: CTI (Cyber Threat Intelligence) platforms centralize, enrich, and share threat intel (often via STIX/TAXII) and integrate with SIEM/SOAR/EDR to improve detection and response. They support workflows such as triage, scoring, case management, and team-wide intel sharing.