Ransomware as a Service is no longer just malware, it’s a full-fledged subscription business. From this guide, you will learn what Ransomware as a Service (RaaS) is, why it matters for modern organizations, and how the RaaS ecosystem of operators and affiliates actually works. You’ll see the business, technical, and resilience risks it creates, then move into practical protection strategies. Finally, we break down how Eventus Security’s SOC, AI-driven analytics, RaaS-focused playbooks, and continuous services help detect, disrupt, and recover from Ransomware as a Service (RaaS) attacks across the kill chain.
Table of Contents
Many organizations assume they are ready—until they ask themselves:
Would Your Team Know What to Do If Ransomware Hit Tomorrow?
What is Ransomware as a Service RaaS and why does it matter for modern organizations?
Ransomware as a Service (RaaS) is a commercialized cybercrime model where ransomware operators develop and maintain ransomware platforms, then lease them to affiliates who carry out attacks in exchange for a share of the ransom. It works very much like a legitimate Software as a Service subscription, but for criminal purposes, which is why many organizations now look to the best managed security service provider they can find to continuously detect and disrupt these attacks.
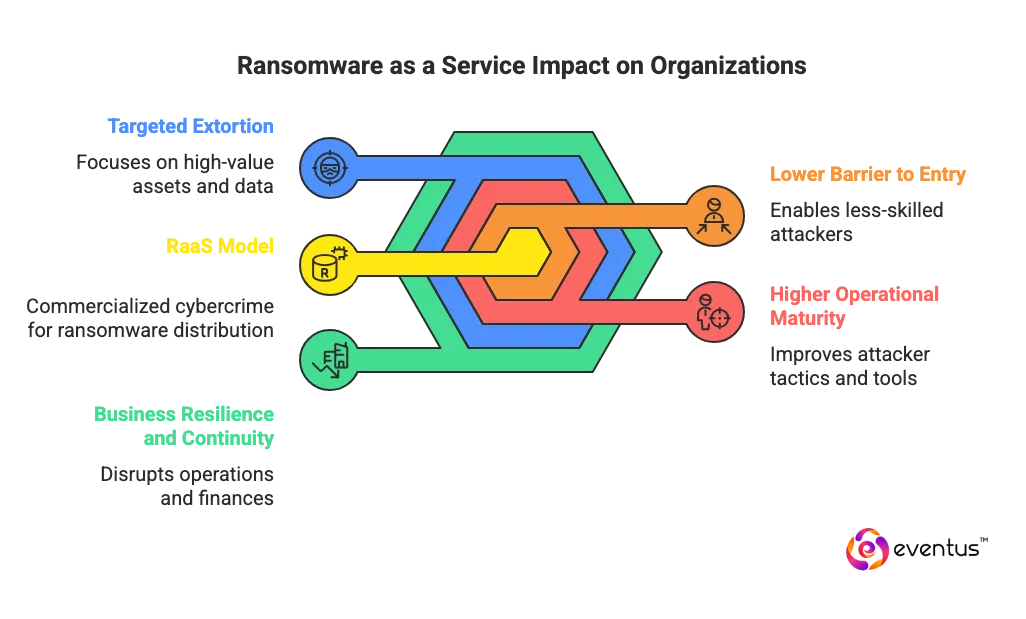
RaaS matters for modern organizations because Ransomware as a Service industrialisers and scales ransomware in three critical ways:
- Lower barrier to entry for attackers
RaaS allows less-skilled criminals to launch sophisticated attacks by renting tools and infrastructure instead of building them. This widens the pool of active attackers and increases the frequency of incidents against businesses of all sizes, including mid-market and smaller enterprises that once assumed they were “too small” to be targeted. - Higher operational maturity on the attacker side
RaaS groups continuously update their malware, command-and-control infrastructure, and extortion tactics in response to security controls and law-enforcement actions. This creates a professional feedback loop where attackers improve reliability (encryption that “works”), evasion techniques, and negotiation strategies, making each wave of campaigns harder to defend against. - Shift from opportunistic to targeted extortion
Modern Ransomware as a Service (RaaS) campaigns often combine data exfiltration, double or triple extortion, and disruption of critical systems. Instead of simply encrypting endpoints, RaaS affiliates target high-value assets such as file servers, hypervisors, ERP systems, and backups, then threaten to leak sensitive data or contact customers and regulators. This directly impacts revenue, operations, contractual obligations, and regulatory exposure. - Direct impact on business resilience and continuity
For a modern organization that depends on digital operations, a successful RaaS attack can halt production lines, interrupt online services, delay financial transactions, and block access to critical data. Recovery costs include incident response, forensics, legal counsel, regulatory notifications, system rebuilds, and long-term brand damage—not just the ransom itself. - Increased pressure on security, IT, and leadership teams
Because RaaS attacks are frequent, fast-moving, and often cross multiple environments (on-premises, cloud, SaaS), security and IT teams must maintain continuous monitoring, tested recovery plans, and executive-level incident playbooks. Boards and regulators now treat ransomware risk as a core business risk, not just an IT problem, which raises expectations around preparedness, reporting, and due diligence, and pushes many organisations to partner with the best SOC as a Service provider they can find to meet those expectations.
To understand attacker behavior in more technical depth, refer to Ransomware analysis tutorial
How do Eventus Security RaaS protection solutions defend against these threats?
Eventus Security Ransomware as a Service (RaaS) protection solutions, as one of the leading Managed SOC service, defend against these threats:
- Eventus Security runs an AI-driven 24/7 SOC that monitors endpoints, network, cloud, and identity for RaaS behaviours in real time.
- It correlates telemetry from EDR, SIEM, firewalls, and identity systems to catch early signs of ransomware like lateral movement and mass encryption activity.
- Ransomware-specific playbooks mapped to the kill chain isolate infected hosts, block malicious accounts, and cut C2 traffic as soon as alerts are confirmed.
- Continuous vulnerability management and attack surface reduction harden common RaaS entry points such as exposed RDP/VPN, unpatched servers, and phishing paths.
- Dedicated ransomware response teams (Ransomware Combat) move within minutes to contain active incidents, investigate root cause, and reduce downtime and legal fallout.
- Resilient backup architectures (for example, 3-2-1 with immutable copies) are designed and tested so businesses can recover without paying ransom.
- Threat intelligence and ransomware-focused cyber drills keep detections, playbooks, and leadership decision-making aligned with the latest RaaS tactics.
To understand how this fits into continuous defense, see Cyber Resilience Against Ransomware
Want to see how an AI-driven SOC can stop RaaS? Schedule a live RaaS protection demo
How does the Eventus Security SOC detect and disrupt RaaS attacks across the kill chain?
Here’s how Eventus Security SOC, as a Best SOC provider companies, detects and disrupts Ransomware as a Service (RaaS) attacks across the kill chain:
- Correlates endpoint, network, cloud, and identity logs against the RaaS kill chain to flag ransomware patterns before encryption starts.
- Detects initial access by profiling VPN, SSO, MFA, and email activity to catch phishing logins, MFA fatigue, and abuse of exposed services.
- Spots privilege escalation and recon through analytics on abnormal admin role changes, tool use, and directory scanning on critical systems.
- Blocks lateral movement by monitoring East–West traffic and identity behaviour, then auto-isolating risky endpoints or revoking sessions.
- Cuts off command-and-control by sweeping for known RaaS infrastructure, loaders, and beacons mapped to MITRE ATT&CK and threat intel.
- Interrupts encryption and data exfiltration by detecting mass file changes, suspicious encryption processes, and unusual outbound flows in real time.
- Orchestrates rapid containment with ransomware runbooks that disable compromised accounts, block C2 domains, enforce segmentation, and guide eradication.
- Uses every RaaS incident to improve detections, playbooks, and recovery KPIs (MTTD, MTTR, backup readiness), strengthening future defence.
Small Reference Table: RaaS Kill Chain Breakdown
| Kill Chain Stage | What Attackers Do | How Eventus Security Disrupts It |
| Initial Access | Phishing, stolen credentials | MFA analytics, exposure scans |
| Privilege Escalation | Admin abuse, token theft | UEBA alerts |
| Reconnaissance | File server mapping | Network visibility |
| Lateral Movement | Pivoting across hosts | Auto-isolation |
| C2 Communication | Beaconing to RaaS servers | IOC blocking |
| Exfiltration | Data transfer | DLP detection |
| Encryption | Mass file tampering | Real-time encryption alerting |
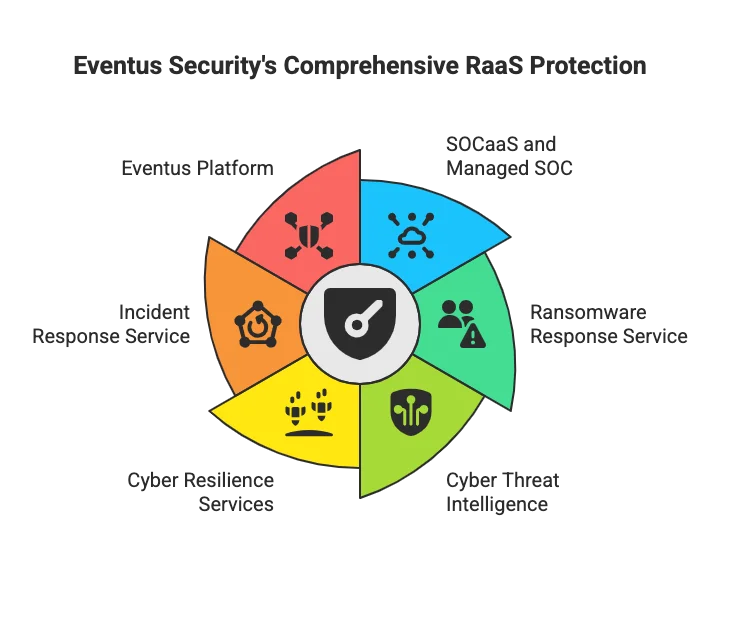
Which Eventus Security services provide continuous RaaS protection for customers?
Eventus Security services, delivered as a comprehensive SOC-as-a-Service, provide continuous RaaS protection for customers:
- SOC as a Service (SOCaaS) and Managed SOC – Core continuous RaaS protection comes from Eventus Security SOCaaS / Managed SOC, which provides 24/7 monitoring, detection, and response across endpoints, network, cloud, and identity, using AI-driven analytics and runbooks to catch ransomware activity before encryption.
- Ransomware Response Service / Ransomware Combat Services – While activated during incidents, this specialized service is tightly always integrated with the SOC and on standby, giving customers an always-available ransomware emergency team to contain RaaS attacks quickly, limit legal exposure, and harden the environment after each incident.
- Cyber Threat Intelligence Services (Eventus Threat Labs) – Continuous cyber threat intelligence feeds (including dark-web and RaaS ecosystem insight) are used to update detections, IOCs, and hunting queries in the SOC, so new RaaS groups and affiliates are recognised and blocked earlier.
- Cyber Resilience Services (Red Teaming, Cloud Security, Breach & Attack Simulation, Application Security) – These ongoing resilience services reduce the initial access paths RaaS affiliates rely on (misconfigurations, exposed services, unpatched apps) and are used periodically to validate and strengthen Ransomware as a Service (RaaS) defences over time.
- Incident Response Service – Eventus Incident Response is available as a standing capability, giving customers rapid, expert-led containment and recovery when RaaS activity is detected by the SOC, and feeding lessons learned back into continuous monitoring and hardening.
- Eventus Platform (Unified SecOps Platform) – The Eventus Platform underpins these services by continuously aggregating telemetry, correlating events, and orchestrating SOAR playbooks, which together provide an always-on control layer for detecting and disrupting RaaS across the kill chain.
If you want these RaaS defences mapped to your own environment, contact the Eventus Security team
How does Eventus use AI driven analytics to identify RaaS patterns and anomalies?
Here is how Eventus, operating a managed SOC service, uses AI-driven analytics to identify RaaS patterns and anomalies:
- Uses the Eventus Platform’s AI analytics to baseline normal endpoint, network, cloud, and identity activity, then flag deviations consistent with Ransomware as a Service (RaaS) behaviour.
- Applies user and entity behaviour analytics (UEBA) to detect precursors such as odd VPN/SSO usage, privilege escalation, and abnormal access to file servers or hypervisors.
- Correlates multiple weak signals (failed logins, lateral movement, encryption-like file changes) into a single high-confidence ransomware incident, reducing false positives.
- Enriches anomalies with threat intelligence on active RaaS groups, matching their tools, infrastructure, and TTPs to prioritise investigations.
- Uses AI-driven risk scoring to trigger SOAR playbooks that isolate endpoints, block C2, and revoke credentials when activity crosses a ransomware risk threshold.
- Continuously retrains detection logic based on real incidents and new techniques, so AI models stay aligned with evolving RaaS campaigns.
What RaaS focused response playbooks and runbooks does Eventus deploy during incidents?
- Ransomware triage and classification playbook – Guides the SOC through confirming it is a ransomware/RaaS event, identifying the strain, scoping affected hosts and data, and formally declaring a major incident so the right technical and business stakeholders are activated.
- Containment and isolation playbook – Defines exactly how to quarantine infected endpoints and servers, block malicious IPs/domains, cut C2 channels, and lock down high-risk segments, using predefined rules for automated vs. human-approved actions (for example, “containment, resets, MFA, blocklists”).
- Identity and access reset runbook – Provides step-by-step instructions to revoke tokens and sessions, reset passwords, re-enroll MFA, and re-issue privileged accounts so RaaS affiliates cannot reuse compromised credentials during or after the incident.
- Backup validation and recovery runbook – Details how to locate known-good, uncompromised backups, test restore points, prioritise which applications and data sets come back first, and coordinate with infrastructure teams to bring services online without re-introducing the ransomware payload.
- Forensics and evidence preservation runbook – Standardises how Eventus collects disk images, memory captures, logs, and timeline data, while preserving chain of custody for possible legal or regulatory follow-up, and feeding Indicators of Compromise (IOCs) back into detections.
- Communication and escalation playbook – Outlines who communicates what, to whom, and when: SOC to IT, CISO and executive briefings, legal and compliance notifications, and, where required, regulator or customer communications, all aligned with an incident-severity matrix.
- Post-incident hardening and resilience playbook – After encryption is stopped and systems are restored, this playbook drives patching of exploited vulnerabilities, configuration changes, control gaps closure, and updates to SOC detections and runbooks so the same RaaS path cannot be used again.
- Client-specific ransomware playbooks – Eventus also builds personalised ransomware playbooks and runbooks per customer environment (critical apps, regulatory scope, business priorities), so every Ransomware as a Service (RaaS) incident follows a tested, organisation-specific response path rather than a generic template.
Which RaaS groups techniques and attack trends should security teams watch in 2026?
- Fragmented, affiliate-driven landscape – Current telemetry shows a long tail of smaller groups, many with fewer than ten victims each on leak sites, indicating a trend toward fragmented, rebranded or short-lived RaaS crews rather than a few mega-brands; defenders should track behaviours and TTPs more than names.
- Higher value targets and bigger payments – Average ransom payments have climbed sharply, with recent quarters seeing seven-figure averages driven by larger enterprise victims and data-theft-first operations; expect 2026 crews to continue focusing on mid-to-large organisations with rich data and tight downtime tolerances.
- Deeper focus on OT, manufacturing and services – Industrial and manufacturing environments feature heavily in recent ransomware reports, especially where IT-OT interconnectivity and remote access create reliable footholds; OT-aware RaaS toolchains are likely to expand.
- Social-engineering-heavy playbooks – Several high-impact campaigns now blend RaaS tooling with sophisticated social engineering against help desks, third-party providers and insiders, particularly in professional services and healthcare; expect more hybrid “RaaS + human ops” campaigns in 2026.
- Pressure from law enforcement and sanctions driving rebrands – Operations against LockBit and sanctions on infrastructure providers show that 2026 will likely bring more takedowns and infrastructure seizures; historically, this pushes groups to splinter, rebrand and adopt new RaaS branding while keeping similar TTPs.
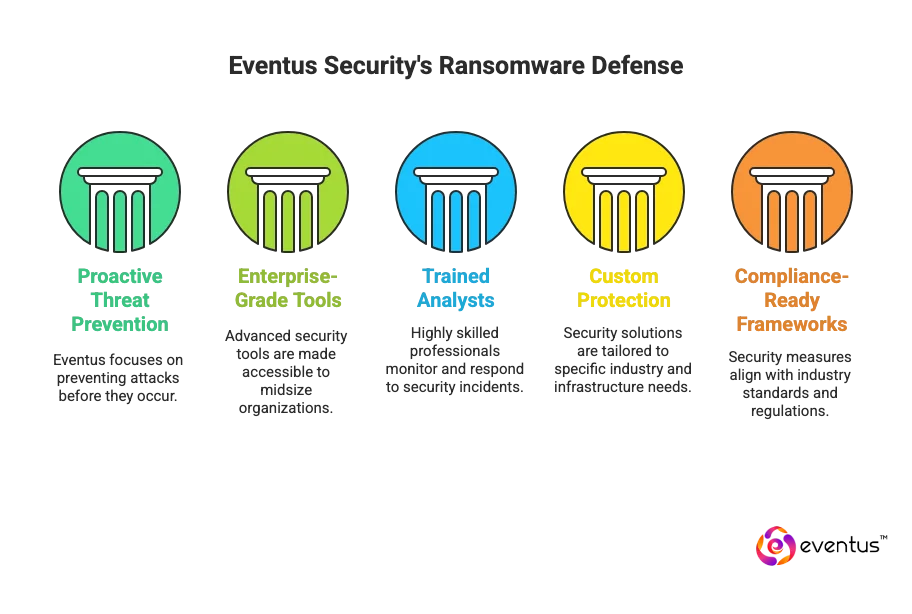
Why Organizations Trust Eventus Security Against Ransomware as a Service
Eventus Security provides businesses with:
- Proactive threat prevention, not just reactive cleanup
- Enterprise-grade tools accessible to midsize organizations
- Highly trained SOC analysts and incident responders
- Custom protection tailored to your industry and infrastructure
- Compliance-ready security frameworks
Whether you’re protecting a distributed workforce, critical infrastructure, or sensitive customer data, Eventus delivers the layered security needed to defend against modern ransomware threats.
For a practical defensive roadmap, you can also Download the Ransomware Guide
Final Thoughts
Ransomware as a Service has transformed cybercrime into a scalable, global business. To defend against this rapidly evolving threat landscape, organizations must adopt a proactive, intelligence-driven, and multi-layered security strategy.
With Eventus Security’s comprehensive Ransomware as a Service (RaaS) protection solutions, your business can stay ahead of attackers, maintain operational continuity, and ensure your data remains in your control—not theirs.
FAQs
Q1 – Is Ransomware as a Service only a concern for large enterprises?
No. RaaS lowers the barrier for attackers, so mid-market and smaller organizations are frequently targeted, especially if they have weak controls, valuable data, or limited security staffing.
Q2 – How should we quantify the business impact of a potential RaaS attack?
Estimate direct costs (downtime per hour, recovery, legal, notifications) plus indirect costs (lost deals, reputational damage, regulatory risk). Many teams model “worst day of the year” scenarios for key systems and use that as a baseline.
Q3 – How does cyber insurance interact with RaaS protection services?
Insurers increasingly expect strong controls: 24/7 monitoring, MFA, patching, and tested backups. Working with a soc as a service provider like Eventus can help meet underwriting requirements and provide the forensic evidence and documentation insurers request during a claim.
Q4 – What should non-technical staff do differently to reduce RaaS risk?
They should follow strict MFA hygiene, verify unexpected requests out-of-band, avoid enabling macros or sideloading software, and report suspicious emails or pop-ups immediately rather than trying to “fix” issues themselves.
Q5 – How quickly can an organization see measurable improvement after engaging Eventus?
Typically, risk reduction appears in phases: rapid wins in the first 30–60 days (visibility, high-risk misconfigurations, critical patches), followed by deeper improvements over 3–6 months as monitoring, playbooks, and backup strategies are tuned to your environment.