Choosing between SOC as a Service and a Managed Security Service Provider (MSSP) requires clarity on outcomes, ownership, integration, risk, and cost. This article compares both models across service scope, detection and response capabilities, pricing structures, and fit for different organizational profiles. It also outlines how to evaluate providers, the implementation roadmap after selection, and available BOT or hybrid options. By reviewing key differences, strengths, and readiness requirements, readers gain a practical framework to decide which security operating model aligns best with their needs
Table of Contents
Which strategic lens should you use to compare soc as a service and MSSP
Use a strategic lens of outcomes, ownership, integration, risk, and economics.
- Outcomes and coverage: Compare measurable results: threat detection and response quality, response times, alert fidelity, and overall security posture across cloud, endpoint, identity, and network.
- Operating model and ownership: Clarify who manages 24×7 security monitoring, runbooks, and post-incident actions. SOC as a Service = provider-operated SOC; MSSP services = broader coverage across multiple security technologies.
- Integration depth and tooling control: Assess integration with existing security tools, telemetry, and automation. Determine flexibility to bring your own stack vs adopting the provider’s.
- Governance and compliance: Evaluate compliance reporting, audit trails, and incident evidence. Check role-based access, data handling, and regulatory requirements coverage.
- Risk and resilience: Review SLAs, escalation, continuity, and surge handling. Ensure resilience against alert fatigue and advanced security needs.
- People and capability lift: Balance in-house SOC skills vs MSSP outsourcing. Decide what remains internal and how soc analysts collaborate with your team.
- Economics and scalability: Compare total cost of ownership: upfront investment, licensing, data volume, scalability for enterprise or small to medium-sized environments.
- Fit to security requirements: Align with your industry, threat profile, and tool maturity. Use an explicit SOC vs MSSP scorecard to map key differences for your security solution.
How do service scope and operating model differ between SOC as a service and MSSP?
SOC as a Service is a provider-operated security operations center focused on continuous threat detection and response outcomes, while an MSSP is a broader managed security service provider that operates and maintains security technologies across many domains. The key differences are in ownership, depth of detection engineering, response execution, and how the service model integrates with your team and tools.
| Dimension | SOC as a Service | MSSP (Managed Security Service Provider) |
| Primary Scope | 24×7 security monitoring, alert triage, threat detection and response, incident response workflows, and tuning to reduce noise. | Broader managed security services: firewall/endpoint management, email security, vulnerability management, compliance support, optional SOC functions. |
| Platform and Tooling | Opinionated provider stack ingesting your telemetry, enhanced with threat intelligence and automation for faster response times. | Manages your existing security tools or supplies them; emphasizes operation and maintenance over deep detection engineering. |
| Alert Handling & Detection Engineering | Owns alert fidelity, writes/tunes detections, tracks MTTD/MTTR, and drives measurable outcomes against cyber threats. | Routes alerts via ticketing, escalates to your security team, variable depth in custom rule creation. |
| Incident Response Execution | Performs containment and guided remediation under approved runbooks. | Escalates incidents to you or an external IR retainer; focuses on coordination, not hands-on containment. |
| Governance & Compliance | Provides SOC case evidence, audit support, timelines, and mapped controls for compliance reporting. | Extends coverage for regulatory requirements across managed controls but less depth of SOC case evidence without add-ons. |
| Ownership & Collaboration | Embeds with your SOC team as an extension of in-house security operations. Outcome-driven. | Operates on service catalogs/SLAs across multiple clients. Requires more internal ownership for complex security decisions. |
| Service Model Fit | Best for organizations needing focused, continuous detection and response in a cost-effective way without maintaining a full in-house SOC. | Best for enterprises or SMBs seeking comprehensive outsourced management across multiple security controls. |
| Economics & Investment | Lower upfront investment; provider scale accelerates access to advanced detection and response capabilities. | Can consolidate vendors and tools; may add cost for deeper SOC outcomes. |
Which capabilities are stronger in SOC as a service v/s an MSSP?
| Capability | Stronger in SOC as a Service | Stronger in MSSP |
| Detection & Analytics | Deeper detection engineering, rule tuning, cross-domain correlation, higher alert fidelity. | Broader monitoring across many tools, but less depth in detection engineering. |
| Response Execution | Faster containment and guided remediation within the service model. | Escalates incidents; response often handled externally or by client team. |
| Content & Automation | Central playbooks, curated threat intelligence, continuous tuning. | Broader tool support, less emphasis on custom SOC playbooks. |
| Case Management & Evidence | Unified timelines, artifacts, audit-ready evidence for compliance. | Compliance coverage across multiple domains, less SOC case depth. |
| Time to Value | Lower upfront investment, faster access to advanced SOC outcomes without in-house SOC. | Cost consolidation by outsourcing multiple security technologies. |
| Breadth of Managed Controls | Focused on SOC operations. | Wide coverage: firewall, endpoint, email, vulnerability management, etc. |
| Tool Flexibility | Usually provider stack, optimized for SOC outcomes. | Adapts to client’s existing tools and processes. |
| Operational Outsourcing | Outcome-driven SOC partnership. | Day-to-day tool management outsourced; client retains complex security decisions. |
How do pricing packaging and contracts differ between the two models?
| Aspect | SOC as a Service | MSSP |
| Pricing Basis | Data ingest (GB/day, EPS) and response scope. Fewer line items, outcome-driven SLOs. | Per device, user, or site. Separate fees for monitoring and changes. |
| Packaging | Bundled (SIEM, SOAR, case mgmt, 24×7 monitoring). | Modular services. SOC optional. |
| Licenses & Costs | Platform included, predictable tiers. | Pass-through vendor licenses, variable project fees. |
| Response Scope | Containment and playbooked actions included. | Notify-and-escalate; remediation often extra. |
| Contracts | 12–36 month terms, clear exit/data handoff. | Multi-year MSAs, varied SLAs, complex true-ups. |
Which organizational profiles align better with each model?
| Factor | SOC as a Service | MSSP | Dedicated SOC |
| Best Fit | SMEs needing strong detection & response without in-house SOC. SLA-backed, outcome-driven, faster time-to-value. | Enterprises with broad multi-vendor needs, outsourcing device mgmt/monitoring but keeping strategy in-house. Flexible, modular coverage. | Regulated/high-risk orgs needing bespoke playbooks, deep integrations, and full operational control. |
| Buyer Effort | Low lift: provider normalizes telemetry, refines playbooks, bundles tools. Light staffing (1 owner + IT/infra resolvers). | Higher lift: you/MSSP manage SIEM/EDR/firewall, define workflows, coordinate across vendors. Requires platform owners + service manager. | Highest lift: build and maintain full SOC stack, staff, and processes internally. |
| Integration | Opinionated platform; easy if adopting vendor stack. | Complex integrations across many tools and controls. | Fully customized integrations, high control. |
| Response Execution | Containment + playbooked remediation included. | Mostly notify-and-escalate; remediation may need IR retainer. | Direct, hands-on response tailored to environment. |
| Compliance & Evidence | Unified timelines, artifacts, and audit-ready reporting. | Compliance breadth via managed controls; less SOC case depth. | Deep, bespoke evidence aligned with regulatory demands. |
| Economics | Subscription tied to ingest & response scope; fewer line items, clear SLOs. | Mixed pricing (device, user, site) with more variable costs. | High upfront and ongoing cost (tools, staff, facilities). |
| BOT/Hybrid Options | BOT or hybrid models available (tiered split, day/night, IR overlay, AI co-pilot). | Shared-service SLAs; less BOT flexibility. | BOT/hybrid possible but usually custom-built. |
How should you evaluate providers across both models?
- Outcomes – Ask for MTTD/MTTR, alert precision, false positive reduction, and mapped detection coverage.
- Integration – Confirm native support for your stack; test log ingestion and parser maintenance.
- Detection Quality – Review sample detection rules, validation process, and regression checks.
- Response Execution – Inspect playbooks, approval matrices, and 24×7 containment coverage.
- Threat Intel & Hunting – Verify TI sources, curation, hunt cadence, and examples of hunts turned detections.
- Reliability – Check uptime SLAs, DR plans, backlog SLOs, and failover evidence.
- Reporting & Transparency – Require dashboards for MTTD/MTTR and case timelines; ensure raw evidence export.
- Governance & Compliance – Map controls to frameworks; review chain of custody, audit reports, and pen test results.
- Service Security – Validate staff vetting, least-privilege practices, tenant separation, and secrets management.
- Team & Operating Model – Meet delivery pod, confirm certifications, shift coverage, and escalation paths.
- Economics & Scalability – Model TCO; simulate log spikes to test scale and costs.
- References & Proof – Speak with peer customers; run a time-boxed pilot with clear success criteria.
- Contract & Exit – Ensure measurable SLOs, service credits, data export rights, and knowledge-transfer terms.
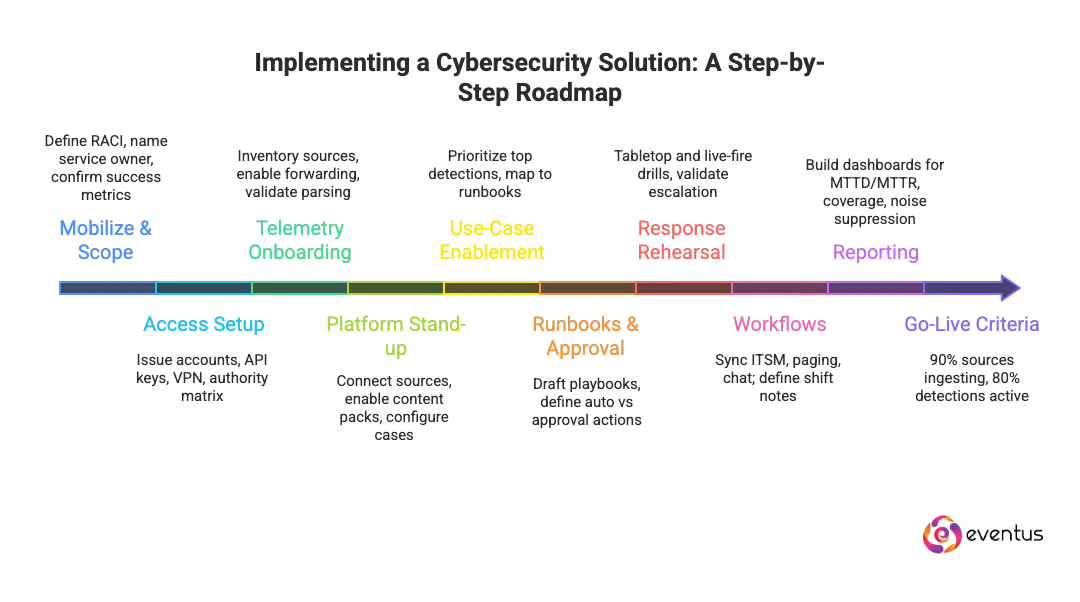
What implementation roadmap should you follow after selection?
Implementation roadmap after selection
- Mobilize & Scope – Define RACI, name service owner, confirm success metrics (MTTD, MTTR, alert precision), freeze phase-one scope.
- Access Setup – Issue accounts, API keys, VPN, authority matrix, change windows, and contacts.
- Telemetry Onboarding – Inventory sources (identity, endpoint, cloud, network), enable forwarding, validate parsing, retention, and residency.
- Platform Stand-up –
- SOC as a Service: connect sources, enable content packs, configure cases and exports.
- MSSP: deploy SIEM/EDR/email/firewall tools, agents, define parser ownership.
- Use-Case Enablement – Prioritize top 10–15 detections, map to runbooks and response paths.
- Runbooks & Approval – Draft playbooks (containment, resets, MFA, blocklists); define auto vs approval actions.
- Response Rehearsal – Tabletop and live-fire drills, validate escalation, measure MTTD/MTTR.
- Workflows – Sync ITSM, paging, chat; define shift notes and major-incident protocol.
- Reporting – Build dashboards for MTTD/MTTR, coverage, noise suppression, SLA attainment.
- Go-Live Criteria – 90% sources ingesting, 80% detections active, <10% noise, successful containment drill.
- Stabilization (30 days) – Tune noisy rules, close parser gaps, review cases, confirm DR tests.
- Phase Two – Expand detections (identity hunting, lateral movement, cloud posture), onboard new regions.
- Compliance – Map evidence to frameworks, lock retention, schedule quarterly tests, archive timelines.
- Continuous Improvement – Monthly tuning, quarterly red/purple-team driven detection updates.
- BOT/Hybrid Evolution – Define transfer or hybrid split model with SLAs if scaling in-house.
- Exit Readiness – Maintain content repos, playbooks, asset lists, export procedures for smooth switch.
FAQs
Is SOC as a Service the same as an MSSP?
No. SOC as a Service is a provider-run security operations center focused on detection and response outcomes; an MSSP is a broader managed-security catalog that operates multiple security tools and controls.
Which model delivers faster incident response?
Typically SOC as a Service, because containment playbooks and authority are built into the platform; many MSSPs notify and escalate unless you add a separate IR scope.
Which is better for complex multi-vendor environments?
An MSSP usually fits better due to tool flexibility and breadth across firewalls, EDR, email, cloud, and network.
Which is better if I have a small team and no SIEM expertise?
SOC as a Service. It reduces engineering lift and time to value with an opinionated stack and curated detections.
Do I still need in-house staff?
Yes. You need a service owner, resolvers for remediation, and someone to own policy and approvals—regardless of model.