If you’re trying to decide whether you really need a SOC or SOC-as-a-Service, you’re not alone. This guide starts by explaining what SOC services are and what SOC as a Service actually means, then walks you through how a complete SOC-as-a-Service solution works in practice, from onboarding and integration to day-to-day monitoring and incident handling. It breaks down core and advanced SOC services such as continuous threat detection, security monitoring, and incident response.
Table of Contents
You’ll also see the key business benefits, how SOC-as-a-Service compares with building an in-house SOC (including their cost structures), and what to evaluate when choosing the right SOC services provider for your environment and security requirements.
What Are SOC Services and What Does SOC as a Service Mean?
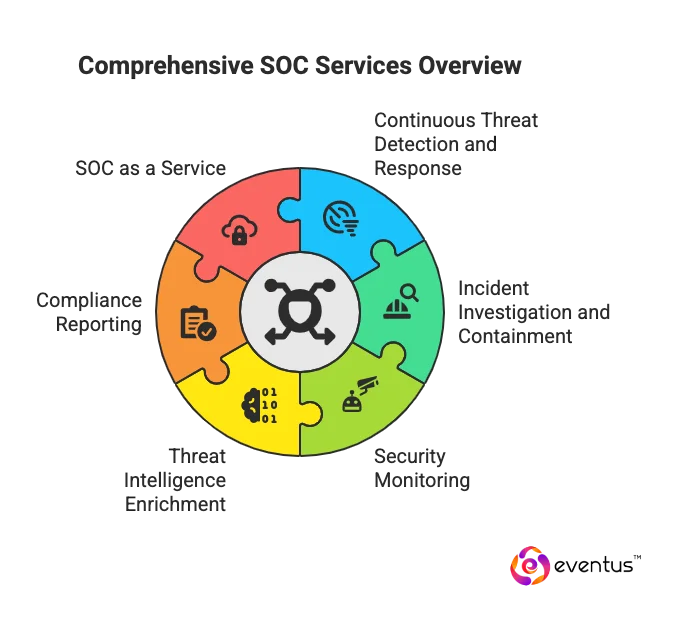
SOC services are the functions a Security Operations Center delivers to protect an organization from cyber threats. A SOC uses SIEM, analytics, and security tools to provide:
- Continuous threat detection and response
- Incident investigation and containment
- Security monitoring
- Threat intelligence enrichment
- Compliance reporting
These services may be delivered by in-house teams or SOC managed service providers, forming a complete security solution that improves security posture and reduces the impact of attacks.
SOC as a Service (SOCaaS) is a managed model where a third-party SOC as a Service provider runs your SOC capabilities. Instead of building an internal SOC, you outsource to a managed SOC that provides 24/7 monitoring, SIEM-as-a-Service, MDR, and complete threat detection.
This gives you access to real experts, scalable solutions, and full SOC coverage—without the overhead of running your own operations center.
How SOC Services and SOC-as-a-Service Works?
- Start with discovery and scoping to map assets, data sources, and key risks.
- Onboard and integrate log sources, sensors, and security tools into the SOC platform.
- Tune detection use cases and playbooks to match your environment, policies, and priorities.
- Provide 24/7 monitoring where analysts validate alerts, investigate incidents, and escalate with clear recommendations.
- Use automated workflows to contain and remediate threats quickly where possible.
- Run regular review calls and reporting to refine rules, align with new threats, and maintain compliance as the business changes.
How Does SOC as a Service Differ from Traditional SOC Services?
Here’s how:
| Aspect | Traditional SOC (Internal SOC) | SOC as a Service (SOC-as-a-Service) |
| Delivery model | Built and run in-house as a permanent security function. | Delivered by a third-party provider as a managed service or managed SOC service. |
| Ownership of infrastructure | The organization owns and maintains SIEM or other security information and event management platforms, servers, and security tools. | A SOC-as-a-Service provider hosts the best SOC as a Service capabilities without having to build and operate a SOC in-house. |
| Staffing and expertise | Internal security team handles monitoring, investigation, and response; you own hiring and retention. | Provider’s SOC team handles monitoring and response, so you get specialized talent without adding headcount. |
| Scope of security services | Coverage depends on team maturity and is often uneven across monitoring, response, and advanced detection. | Managed SOC-as-a-Service provides SOC monitoring, threat monitoring, and advanced threat detection as a single service. |
| Scalability and flexibility | Scaling requires adding tools, licenses, and analysts; changes are slower and capital-intensive. | SOC-as-a-Service scales coverage up or down and tailors services to your changing security needs. |
| Integration with existing security | Internal SOC must engineer and maintain integration with firewalls, endpoints, cloud, and identity systems. | SOC-as-a-Service providers integrate with existing security controls and policies and align with your environment as part of onboarding. |
| Threat handling | The internal team must keep pace with an evolving threat landscape and design processes to identify and mitigate security threats. | SOC-as-a-Service delivers proactive monitoring to detect, contain, and resolve security threats using proven playbooks. |
| Governance and compliance | Organization is responsible for designing controls and aligning with standards; may require extra effort for audits and certifications. | Many SOC providers operate against frameworks such as SOC 2 and support governance and audit needs as part of the managed security model. |
| Cost and maintenance | Higher fixed costs for building, maintaining SOC infrastructure, and continuous training. | Subscription-based model where SOC as a Service provides an effective SOC with lower upfront costs and predictable ongoing spend. |
What Core SOC Services are Included in a Complete SOC-as-a-Service Solution?
The following points are related to core SOC services in a complete SOC-as-a-Service solution:
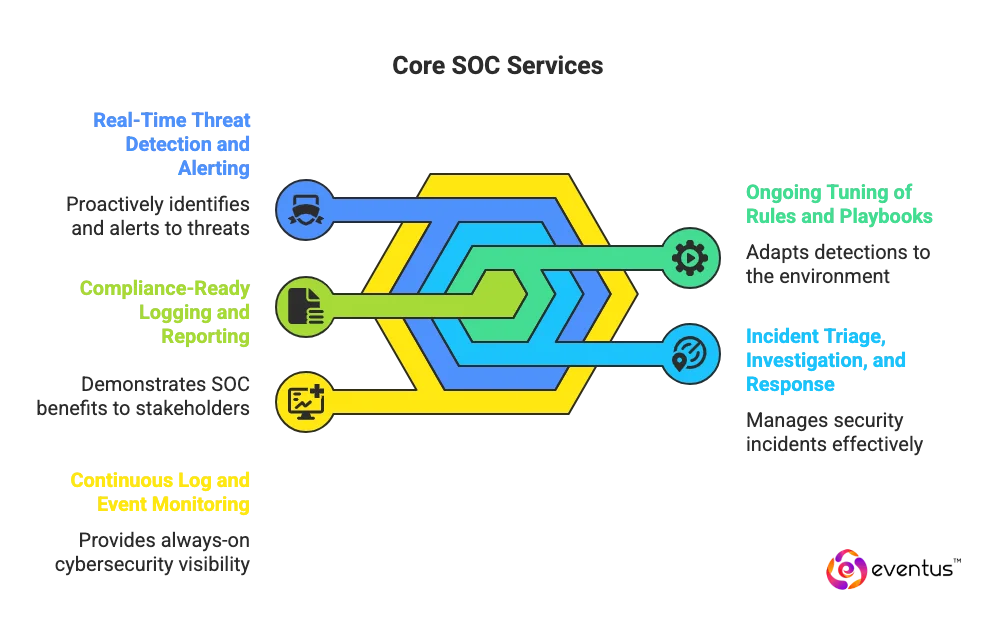
- Continuous log and event monitoring across networks, endpoints, and cloud to give always-on cybersecurity visibility as part of a production-grade soc solution.
- Real-time threat detection, correlation, and alerting using modern cybersecurity solutions so analysts can proactively stop attacks early.
- Incident triage, investigation, and response run by a specialist team in a dedicated security operations center, maintaining robust security.
- Ongoing tuning of rules, use cases, and playbooks by socaas providers or managed soc providers so detections match your environment and risks.
- Compliance-ready logging and reporting that demonstrate the operational benefits of soc to security and business stakeholders.
- Follow-the-sun coverage via a global soc, ensuring there are no monitoring gaps across time zones.
What is SOC-as-a-Service Solutions by Eventus?
Eventus SOC-as-a-Service replaces the cost and complexity of building your own SOC with an expert-led, always-on operations team. Eventus integrates with cloud, on-prem, endpoint, identity, and SaaS systems to centralize telemetry, then uses analytics and threat intelligence to detect attacks faster. The Eventus SOC team handles 24/7 monitoring, triage, and response guidance so internal teams can focus on remediation and business priorities.
You get:
- Predictable subscription pricing
- Defined SLAs
- Compliance-ready reporting
- Measurable reduction in breach risk
Eventus is trusted among the top MSSP companies, SOC providers, SOC service providers in India, and best SOC as a Service providers in India.
How do SOC Services Provide Continuous Threat Detection and Security Monitoring?
Here’s how:
- SOC services deploy sensors and log collectors across networks, endpoints, cloud, identity, and applications so all security events stream into a central monitoring platform in real time.
- These events are normalized and correlated in an analytics layer (often SIEM-like), where rules, behavioral baselines, and threat intelligence distinguish routine activity from suspicious or malicious behavior, giving the managed security service provider the context needed to prioritize, investigate, and respond to real threats.
- Continuous correlation and anomaly detection surface high-risk patterns such as lateral movement, privilege abuse, or data exfiltration that simple log review would miss.
- On-duty analysts monitor prioritized alerts 24/7, validate true positives, and quickly decide whether to contain, escalate, or dismiss activity, reducing attacker dwell time.
- Standardized playbooks and automated workflows ensure that similar threats trigger consistent responses, improving coverage and reducing human error in day-to-day security monitoring.
- Metrics on alert volumes, true-positive rates, and response times are tracked so the SOC can refine rules and detections, keeping monitoring effective as threats and the environment change—this is where the difference between SOC models (mature vs immature, in-house vs managed) becomes visible in real-world performance.
What Business Benefits Do SOC Services and SOC-as-a-Service Provider?
Given below are the benefits:
- Reduce breach impact and business risk: SOC services and ai driven soc as a service cut mean time to detect and respond, lowering the likelihood and cost of ransomware, data theft, and downtime.
- Lower, predictable security costs: You replace large upfront tool and staffing investments with a recurring fee, turning CAPEX into OPEX and stabilising the security budget.
- Immediate access to expert talent: You gain a full team of trained analysts and incident responders without the hiring, training, and retention burden of running an internal SOC.
- 24/7 monitoring without 24/7 headcount: Around-the-clock coverage is delivered by the provider, so you do not need to build shifts or a global operations model.
- Faster path to compliance and trust: Structured logging, incident handling, and reporting make it easier to satisfy auditors, insurers, and enterprise customers that require strong security controls.
- More focus on core business: Internal IT and engineering teams spend less time firefighting security incidents and more time on projects that drive revenue and product growth.
How Do SOC-as-a-Service Solutions Compare with Building and Running an in-house SOC?
SOC-as-a-Service and an in-house SOC aim for the same cybersecurity outcomes but differ mainly in cost model, time to value, and operational burden.
The following points are related to how SOC-as-a-Service compares with an in-house SOC:
- Cost and investment: SOC-as-a-Service is subscription-based with low upfront cost; an in-house SOC requires heavy capital spend on tools, infrastructure, and 24/7 staffing.
- Speed and maturity: SOC-as-a-Service typically becomes fully operational in weeks using prebuilt content and processes, while an in-house SOC can take many months to reach comparable detection and response maturity.
- Staffing and expertise: SOC-as-a-Service includes an established team of analysts and engineers; an in-house SOC must continuously hire, train, and retain scarce security talent.
- Control versus burden: An in-house SOC offers deeper control and customisation of tooling and processes, but also higher complexity and maintenance, whereas SOC-as-a-Service trades some control for reduced operational overhead and easier scalability.
What are the Problems Businesses Face?
The following points are related to Problems Businesses Face.
- Difficulty building or maturing an internal SOC with limited budget and time
- Attackers evolving faster than internal security capabilities
- Shortage of skilled security professionals and 24/7 coverage
- Tool sprawl creating visibility gaps across environments
- Alert fatigue causing important signals to be missed
- Fragmented logs making investigations slow and incomplete
- Compliance and reporting demands increasing without extra headcount
- Expanding cloud, SaaS, and remote user footprint outpacing current detection and response capabilities
How Should You Choose the Right SOC Service Provider for Complete SOC-as-a-Service Solutions?
You should choose a SOC service provider by checking how well they fit your environment, risks, and internal team.
The following points are related to choosing the right SOC service provider for complete SOC-as-a-Service solutions:
- Confirm they can monitor all critical assets you use today (cloud, on-prem, SaaS, identity) and your main attack scenarios.
- Evaluate their analyst expertise, industry experience, and 24/7 operations, including concrete SLAs and escalation paths.
- Check that their platform integrates cleanly with your existing tools (EDR, SIEM, firewalls, ticketing) and clarify who owns and manages the tech stack.
- Review how they onboard, tune detection rules, and align playbooks with your policies, risk tolerance, and approval flows.
- Verify their security and compliance posture (for example, SOC 2, ISO 27001), data handling practices, and quality of reports and dashboards.
Frequently Asked Questions (FAQs)
The following points are related to key FAQs about SOC-as-a-Service evaluation and operations:
Q1. Which types of organizations benefit most from SOC-as-a-Service compared to building an internal SOC?
Mid-sized and fast-growing organizations, or those with limited in-house security skills and budget, benefit most because they get 24x7 enterprise-grade monitoring without building and staffing a full SOC
Q2. How long does it typically take to fully onboard to a SOC-as-a-Service provider from contract signature to live monitoring?
Ans: Typical onboarding timelines range from 4–12 weeks, depending on environment size, number of log sources, and integration complexity.
Q3. How does a SOC-as-a-Service provider work with an existing in-house security or IT team on a day-to-day basis?
Ans: The provider handles continuous monitoring, alert triage, and initial investigation, while the internal team approves actions, performs remediation, and joins regular review and tuning sessions.
Q4. What SLAs and performance metrics (such as detection time and response time) should you expect in a SOC-as-a-Service agreement?
Ans: You should expect defined triage times for critical alerts (for example, 5–15 minutes) and clear MTTD/MTTR targets, plus reporting on alert volumes, use-case coverage, and response execution.
Q5. How do SOC-as-a-Service providers handle data residency, privacy, and log retention requirements for different regions and regulations?
Ans: Providers typically use region-specific storage, strong encryption, and access controls, with documented retention periods and data-processing terms aligned to regulations like GDPR or sector rules.
Q6. How can an organization measure ROI and ongoing business value from a SOC-as-a-Service engagement over time?
Ans: ROI is measured through fewer successful incidents, reduced impact and recovery costs, lower internal tooling and staffing spend, and observable improvements in detection speed and security posture.