This article explains the top benefits of an AI driven SOC as a Service for modern enterprises and how it improves cybersecurity outcomes through practical use cases. It discusses faster threat detection and response, reduced alert fatigue, proactive defense, and automated incident handling with SOAR. It highlights how best soc providers leverage advanced Security Operation Center (SOC) tools to overcome major SOC challenges and streamline SOC uses for better efficiency. The article also explores how a full managed SOC powered by AI enhances scalability, 24/7 monitoring, and collaboration between AI systems and human experts to strengthen enterprise security posture.
Table of Contents
Top 7 Benefits of AI Driven SOC as a Service (SOCaaS)
AI-driven SOC as a Service (SOCaaS) redefines enterprise cybersecurity by combining automation, analytics, and artificial intelligence to deliver faster detection, smarter response, and stronger resilience. Here are the top seven benefits that make AI driven SOCaaS vital for modern organizations:
1. Faster and Smarter Threat Detection
An AI driven SOC (Security Operations Center) fundamentally redefines detection speed and precision through machine learning, AI-based correlation engines, and behavioral analytics. Traditional soc services rely on static rules and manual event correlation, which limits their ability to identify sophisticated or polymorphic attacks.
By contrast, AI SOCs continuously ingest and analyze vast data streams from endpoints, firewalls, SIEM tools, cloud workloads, and threat intelligence feeds. Through unsupervised learning algorithms, they establish baselines for normal user and system behavior, instantly detecting deviations that may signal insider activity, lateral movement, or zero-day threats.
These systems learn iteratively — each detection improves the accuracy of the next — transforming raw telemetry into actionable intelligence within milliseconds. The result is early detection of threats that human analysts might overlook, drastically reducing Mean Time to Detect (MTTD).
Example: A multinational e-commerce company deployed an AI driven SOC to monitor over 5 billion daily log entries across global operations. When an abnormal spike in outbound DNS traffic was observed from a single region, the AI module correlated it with known exfiltration behavior. The system autonomously alerted analysts and blocked the transfer, preventing a large-scale data breach.
2. Reduced Alert Fatigue and Improved Accuracy
In conventional soc managed service providers environments, analysts face a daily deluge of alerts — often tens of thousands per day — with over 70% being false positives. This causes “alert fatigue,” a state where critical warnings get buried under low-priority noise.
AI-driven SOCs mitigate this through automated alert triage, powered by natural language processing (NLP) and correlation heuristics. The AI engine clusters repetitive alerts, filters benign activities, and automatically ranks incidents based on risk context, attack surface exposure, and threat confidence scores.
By integrating with historical incident data, the AI refines its correlation logic over time. Analysts receive only validated, high-risk alerts that require strategic intervention, which leads to more accurate responses and far lower burnout rates among SOC teams.
Example: A financial services provider using an AI-based SOC platform reported a 65% reduction in false positives within the first three months. The system correlated multiple low-severity alerts into a single high-confidence threat report, enabling the security team to respond efficiently to a genuine credential theft attempt.
3. Proactive Threat Defense
The defining strength of an AI driven SOC lies in its proactive defense capabilities. Instead of waiting for threats to materialize, the system predicts and prevents them using predictive analytics, attack surface modeling, and MITRE ATT&CK framework mapping.
Machine learning models analyze patterns across threat intelligence databases, dark web sources, and global malware campaigns to anticipate attacker tactics. Once identified, the system automates policy updates, deploys countermeasures (like updated firewall rules or sandboxing protocols), and strengthens the perimeter before an exploit is attempted.
This shift from reactive detection to proactive defense transforms cybersecurity from an managed soc services necessity into a strategic advantage.
Example: A healthcare organization leveraging an AI driven SOC noticed a global surge in ransomware activity targeting outdated remote desktop protocols. The system automatically updated access policies, blocked suspicious IPs, and issued preemptive patches across endpoints. As a result, no successful intrusion occurred — while several peer institutions suffered downtime.
4. Accelerated Incident Response Times
Incident response traditionally involves manual triage, containment, and remediation — steps that consume valuable time while threats spread laterally. AI-driven SOCs eliminate this lag through Security Orchestration, Automation, and Response (SOAR) integrations.
Once a threat is detected, AI-driven playbooks automatically execute predefined actions: isolating infected hosts, revoking compromised credentials, or blacklisting malicious domains. The system also updates threat intelligence repositories and notifies relevant stakeholders in real time.
By reducing Mean Time to Respond (MTTR) from hours to minutes, these systems minimize both operational disruption and financial loss.
Example: When a global manufacturer’s endpoint detection system identified abnormal encryption behavior, the AI driven SOC automatically quarantined affected devices, blocked external communication, and initiated a rollback protocol from immutable backups. The ransomware attack was fully contained within 90 seconds — preventing data loss and production downtime.
5. Cost and Resource Optimization
Building and maintaining an in-house SOC demands significant investments — including infrastructure, software licenses, and specialized staff. An AI-driven SOC as a Service (SOCaaS) model eliminates these capital expenses by providing enterprise-grade cybersecurity through a subscription-based managed model.
AI-driven automation also reduces the dependency on large analyst teams, ensuring continuous coverage with fewer resources. Routine operations such as data correlation, reporting, and patch validation are executed autonomously, freeing human experts to focus on strategic threat hunting and policy development.
Organizations gain access to a shared intelligence network, updated detection models, and advanced analytics — without incurring hardware or training overheads.
Example: A mid-sized retail enterprise replaced its legacy SOC with an AI driven SOCaaS solution. Within six months, the company reported a 50% reduction in operating costs and 40% faster threat detection cycles. Automated workflows replaced manual investigations, enabling the team to manage security across 80 stores with just two in-house analysts.
6. Scalability and 24/7 Operations
AI-driven SOCs are designed to scale horizontally across hybrid and multi-cloud infrastructures. Unlike legacy systems that struggle under data spikes, AI architectures leverage distributed processing, vectorized analytics, and cloud-native data lakes to manage terabytes of telemetry in real time.
These systems remain operational 24/7 without analyst fatigue. They adapt to global business operations — monitoring users, assets, and workloads across time zones — while maintaining consistent detection precision.
Scalability extends to evolving use cases such as IoT security, remote workforce monitoring, and multi-cloud compliance, ensuring security grows in step with organizational expansion.
Example: During a global product launch, a large e-commerce platform experienced a 40× increase in transaction volume. The AI-driven SOC auto-scaled its detection clusters using cloud orchestration, maintaining 100% uptime while processing 10 TB of security telemetry per hour — all without manual intervention.
7. Human-AI Collaboration for Advanced Security
Despite its automation capabilities, an AI-driven SOC does not replace humans — it augments them. Human analysts provide contextual understanding, ethical oversight, and interpretive judgment that AI alone cannot replicate.
In a collaborative best soc as a service model, AI agents manage repetitive, time-sensitive tasks — data ingestion, anomaly detection, and automated responses — while analysts focus on threat attribution, adversary profiling, and post-incident forensics.
Generative AI systems further enhance collaboration by generating threat summaries, suggesting containment steps, or drafting compliance reports. This human-AI synergy creates an adaptive ecosystem capable of tackling both known and emerging cyber threats.
Example: A global telecom operator deployed a hybrid SOC model where AI systems handled 95% of threat triage. When AI flagged a suspicious login from a privileged account, human analysts correlated it with HR data and discovered the account belonged to a recently terminated employee. The collaboration prevented a potential insider breach, demonstrating the irreplaceable value of human judgment combined with AI speed.
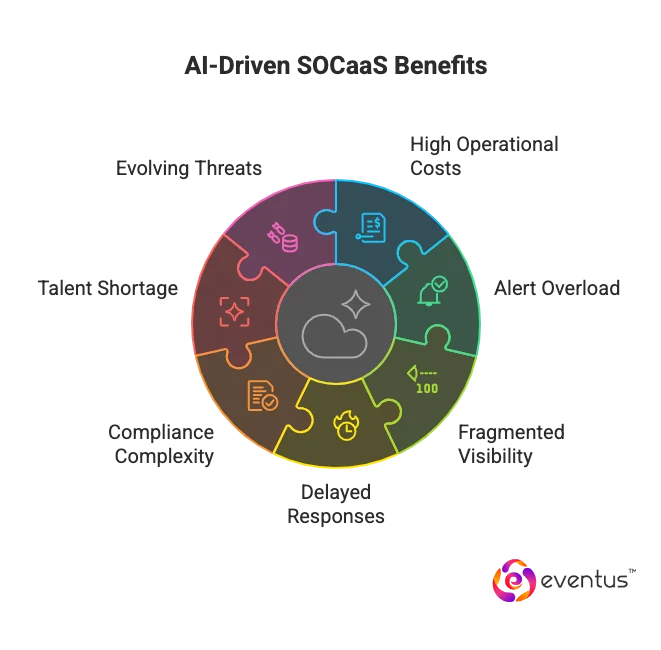
The Business Impact of AI-Driven SOC-as-a-Service
Beyond technical performance, adopting an AI-powered SOCaaS model delivers measurable business outcomes:
| Business Challenge | How AI Driven SOCaaS Helps (Eventus) |
| High operational costs | Cloud-based SOCaaS reduces CapEx and staffing costs |
| Alert overload | AI filters noise and prioritizes true positives |
| Fragmented visibility | Unified view across all threat surfaces |
| Delayed responses | Real-time detection and automated response |
| Compliance complexity | Automated reporting and continuous validation |
| Talent shortage | AI + automation reduces dependency on large teams |
| Evolving threats | Continuous learning adapts to emerging attack patterns |
What is AI-Driven SOC as a Service for Modern Enterprises ?
AI-driven SOC as a Service transforms traditional security operations by integrating artificial intelligence, machine learning, and automation into the Security Operations Centre (SOC) ecosystem. Unlike traditional SOCs that depend heavily on human analysts, AI-driven security operations analyze vast amounts of security data in real time to identify anomalies and cyber threats with superior precision.
Through AI-powered SOC platforms, enterprises can reduce mean time to detect and mean time to respond, significantly enhancing incident response effectiveness. By using behavioral analytics and threat intelligence, AI models help reduce false positives, allowing SOC teams and security analysts to focus on high-priority alerts. The automation of detection and response workflows ensures consistent oversight, strengthens the overall security posture, and minimizes the cost of maintaining traditional security operations centres.
This AI-driven approach enables modern enterprises to proactively respond to threats, optimize resources, and leverage intelligent analytics to ensure compliance, resilience, and sustained cybersecurity excellence.
What Are the Benefits of Autonomous SOC Capabilities for Global Enterprises?
Given below are the benefits:
- Always-on coverage: Continuous, machine-speed detection and response across geographies.
- Higher fidelity detection: Adaptive AI improves precision over time and reduces false positives.
- Automated decisioning: AI SOC agents handle triage, containment, and remediation, cutting MTTR and manual effort.
- Operational efficiency: Offloads repetitive tasks so teams focus on strategic initiatives; lower operating costs.
- Standardized global security: Unified visibility and consistent policy enforcement via SOC-as-a-Service.
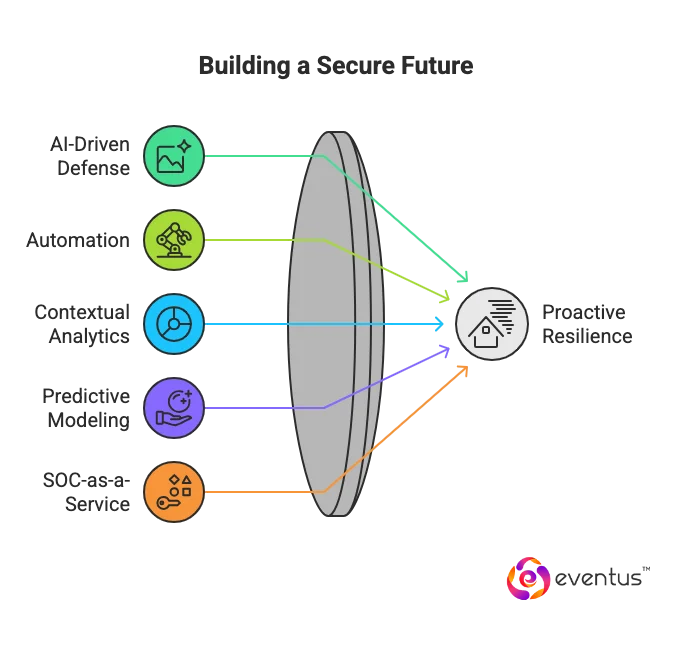
Why Modern Enterprises Choose Eventus
Eventus isn’t just another threat intelligence feed—it’s an AI-driven defense ecosystem.
By operationalizing intelligence through automation, contextual analytics, and predictive modeling, Eventus helps organizations move from reactive response to proactive resilience.
With Eventus SOC-as-a-Service, enterprises can:
✅ Detect faster
✅ Respond smarter
✅ Scale effortlessly
✅ Secure continuously
Secure Your Business with Eventus SOC-as-a-Service
Choosing the right SOC partner is crucial for safeguarding your organization. Eventus Security delivers a next-generation SOC-as-a-Service designed for scalability, speed, and precision. Our experts provide continuous threat monitoring, real-time incident response, and actionable insights to protect your business from evolving cyber risks.
Partner with Eventus to strengthen your security posture — because your business deserves intelligent, end-to-end protection.
FAQ
Q1. What is AI-driven SOC-as-a-Service?
Ans: A cloud-based security model that uses AI and automation to detect, analyze, and respond to cyber threats in real time—without the cost of a traditional SOC.
Q2. How does Eventus redefine the SOC model?
Ans: Eventus shifts from data collection to intelligent action, using AI, ML, and contextual analytics to deliver faster, smarter, and proactive threat defense.
Q3. What are the top benefits of Eventus SOC-as-a-Service?
- Real-time detection and response
- Unified visibility
- Fewer false positives
- Cost efficiency
- Proactive threat hunting
- Compliance automation
- Scalable, AI-powered defense
Q4. How does Eventus help reduce SOC costs?
Ans: As a cloud-based service, Eventus removes infrastructure expenses and reduces manual workloads through automation, improving ROI.