This article provides a comprehensive overview of cybersecurity, explaining its definition, history, and why cyber security is important in today’s digital environment. It outlines the aspects of cyber security, including key security domains and foundational principles, while highlighting common cyber threats like malware, phishing, and ransomware. The content also explores the challenges organizations face in implementing security, the career opportunities available in this growing field, and best practices to enhance security. Together, these sections offer a structured guide to understanding and navigating cybersecurity 2025.
Table of Contents
What is Cybersecurity?
Cybersecurity, also referred to as cyber security or computer security, is the practice of protecting computer networks, systems, and data from cyberattacks, unauthorized access, and malicious activities carried out by a hacker or automated threats. It combines policies, processes, and technologies to ensure confidentiality, integrity, and availability of information across digital environments.
At its core, cybersecurity safeguards both individuals and enterprises from risks such as malware, phishing attacks, ransomware, social engineering, and large-scale disruptions like DDoS attacks. These threats often exploit weaknesses in a computer network, target sensitive resources in a data center, or abuse gaps in identity and access management (IAM) systems.
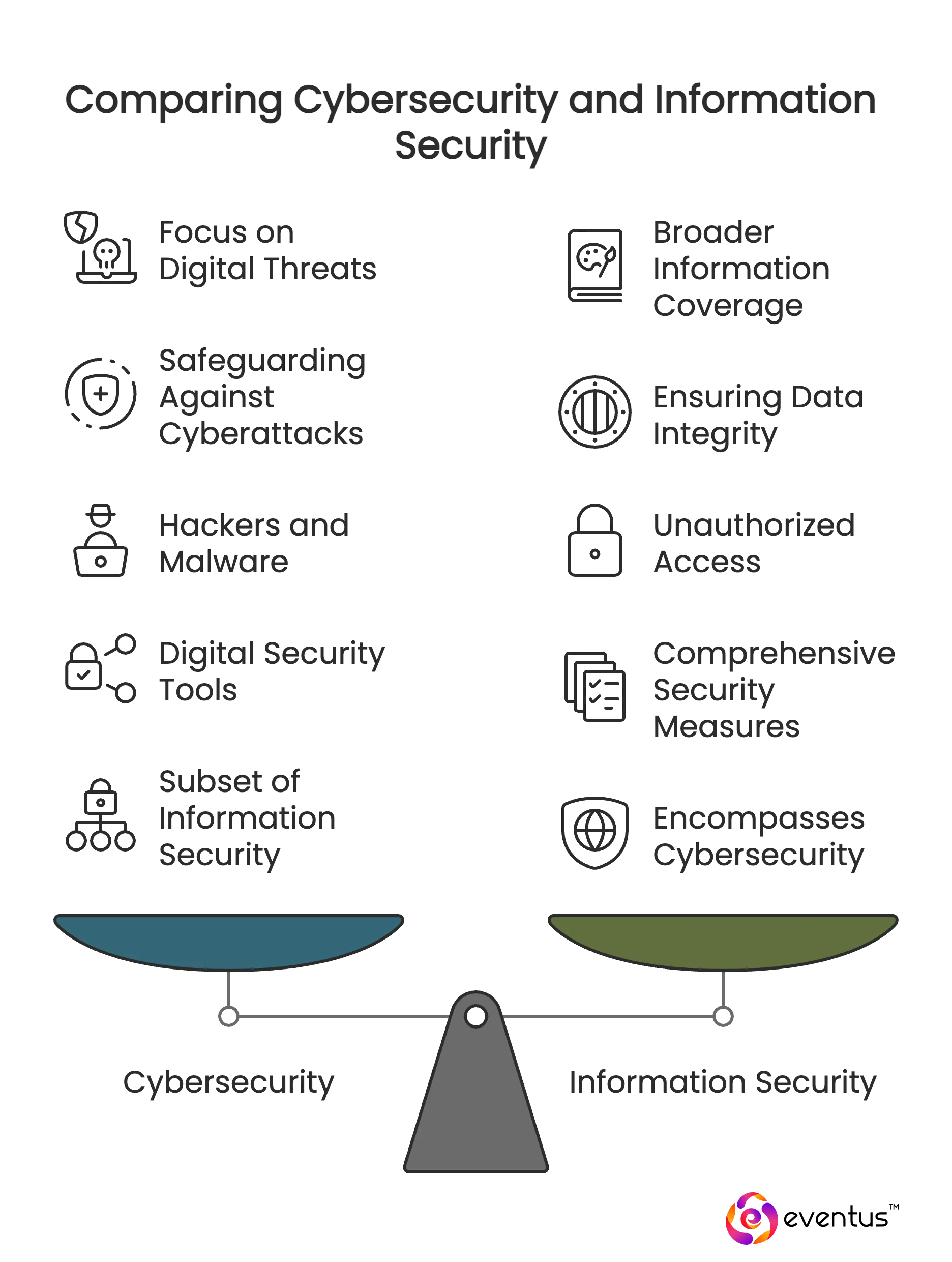
What is the difference between cybersecurity and information security?
| Aspect | Cybersecurity | Information Security |
| Definition | Protects systems, networks, applications, and data from cyberattacks and digital threats. | Protects all forms of information—digital, physical, or verbal—from unauthorized access, misuse, or destruction. |
| Scope | Focused on online environments, digital platforms, and cybersecurity domains like cloud, IoT, and application security. | Broader scope, covering information in any medium (digital files, printed documents, or physical records). |
| Primary Goal | Safeguard against cyberattacks such as malware, phishing, ransomware, and denial-of-service. | Ensure confidentiality, integrity, and availability of information across all storage and transmission formats. |
| Threat Focus | Hackers, malware, phishing attacks, ransomware, DDoS, and advanced persistent threats. | Unauthorized access, insider misuse, theft of physical documents, and digital data breaches. |
| Techniques & Solutions | Firewalls, encryption, IAM, MFA, cloud security, cybersecurity solutions, and endpoint defense. | Access control, data classification, risk management, disaster recovery, and compliance frameworks. |
| Relation | Considered a subset of information security, focused on cyberspace risks. | Encompasses cybersecurity while also covering offline and non-digital risks. |
| Example | Preventing a hacker from exploiting IoT devices in a corporate network. | Securing confidential HR records stored in a locked cabinet and encrypted servers. |
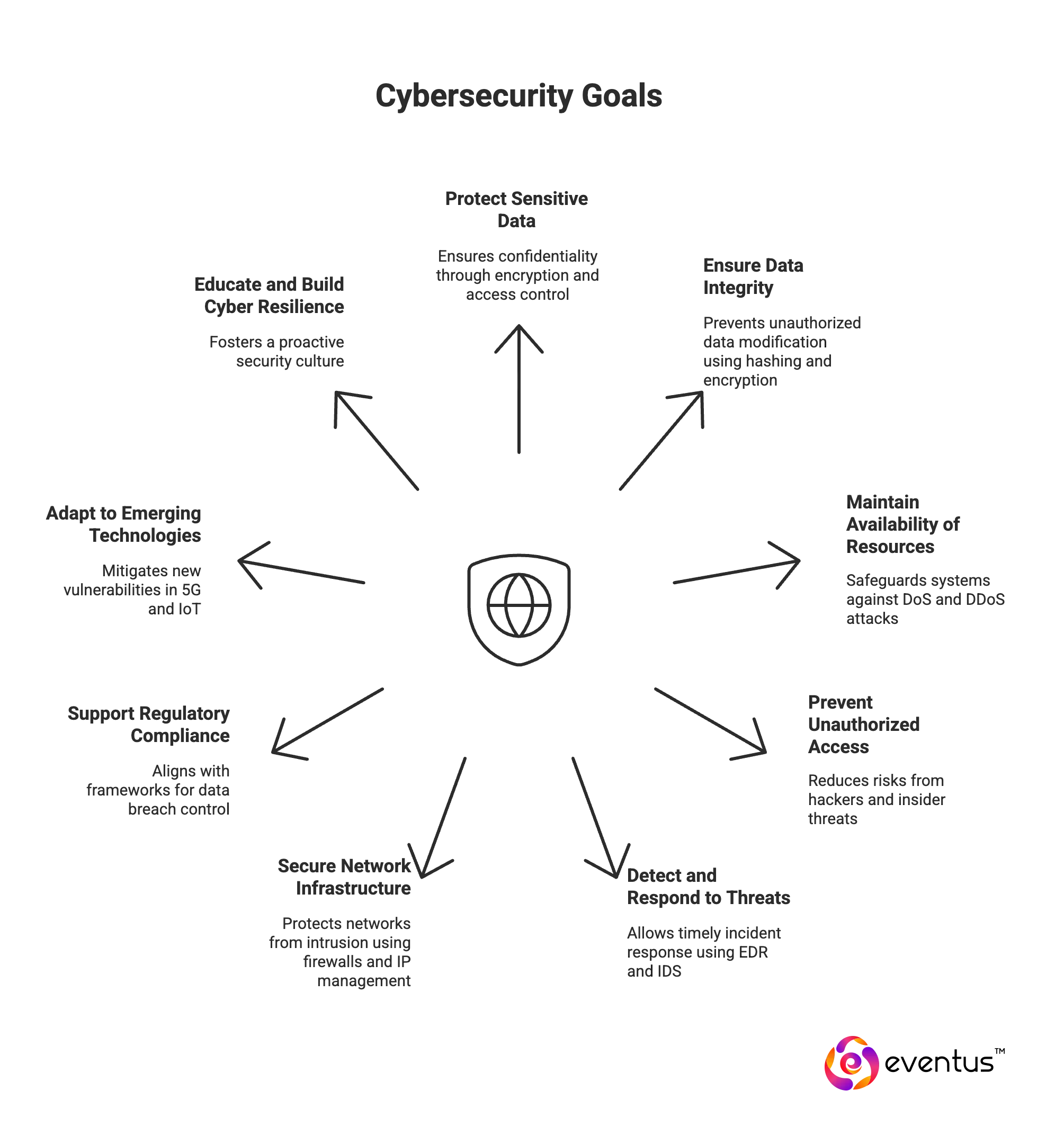
What are the main goals of cybersecurity in an organization?
The main goals of cybersecurity in an organization focus on maintaining the confidentiality, integrity, and availability of data while defending against evolving threats and vulnerabilities across digital systems:
- Protect Sensitive Data: Cybersecurity ensures the confidentiality of information by implementing encryption, firewall, VPN, and access control systems to prevent unauthorized access, theft, or leakage
- Ensure Data Integrity: It prevents unauthorized data modification using technologies like hashing, encryption algorithms, and security protocols from the OSI model and TCP/IP model. This preserves trust in digital systems and supports compliance
- Maintain Availability of Resources: Cybersecurity safeguards systems against denial of service (DoS) and DDoS attacks, helping to maintain service uptime and prevent operational disruptions, especially in data centers and cloud infrastructure
- Prevent Unauthorized Access: Tools like IAM, multi-factor authentication (MFA), single sign-on (SSO), and segmentation reduce risks from hackers, insider threats, and phishing attacks, thereby reinforcing identity and access control
- Detect and Respond to Threats: Early detection of malware, ransomware, social engineering, and other cyberattacks allows timely incident response, using tools such as EDR, IDS, and threat intelligence platforms
- Secure Network Infrastructure: By deploying firewalls, configuring IP address classes, managing DHCP servers, and enforcing OSI model layers like the network and transport layers, organizations can protect the computer network from intrusion
- Support Regulatory Compliance: Effective cybersecurity aligns with frameworks that demand control over data breaches, phishing meaning, and secure data flows, often through encryption meaning, DLP, and access definitions
- Adapt to Emerging Technologies: As organizations adopt 5G, IoT devices, cloud computing, edge computing, and SaaS platforms, cybersecurity must evolve to mitigate new vulnerabilities tied to increased latency, virtual private clouds, and distributed architectures
- Educate and Build Cyber Resilience: Awareness of phishing in cyber security, malware meaning, and define threats fosters a proactive security culture, making users the first line of defense in any organizational cybersecurity strategy
In essence, cybersecurity in organizations isn’t just about protection—it’s about enabling secure digital operations across internet protocols, computer networks, and cloud environments in a threat-prone landscape.
Why is cybersecurity important?
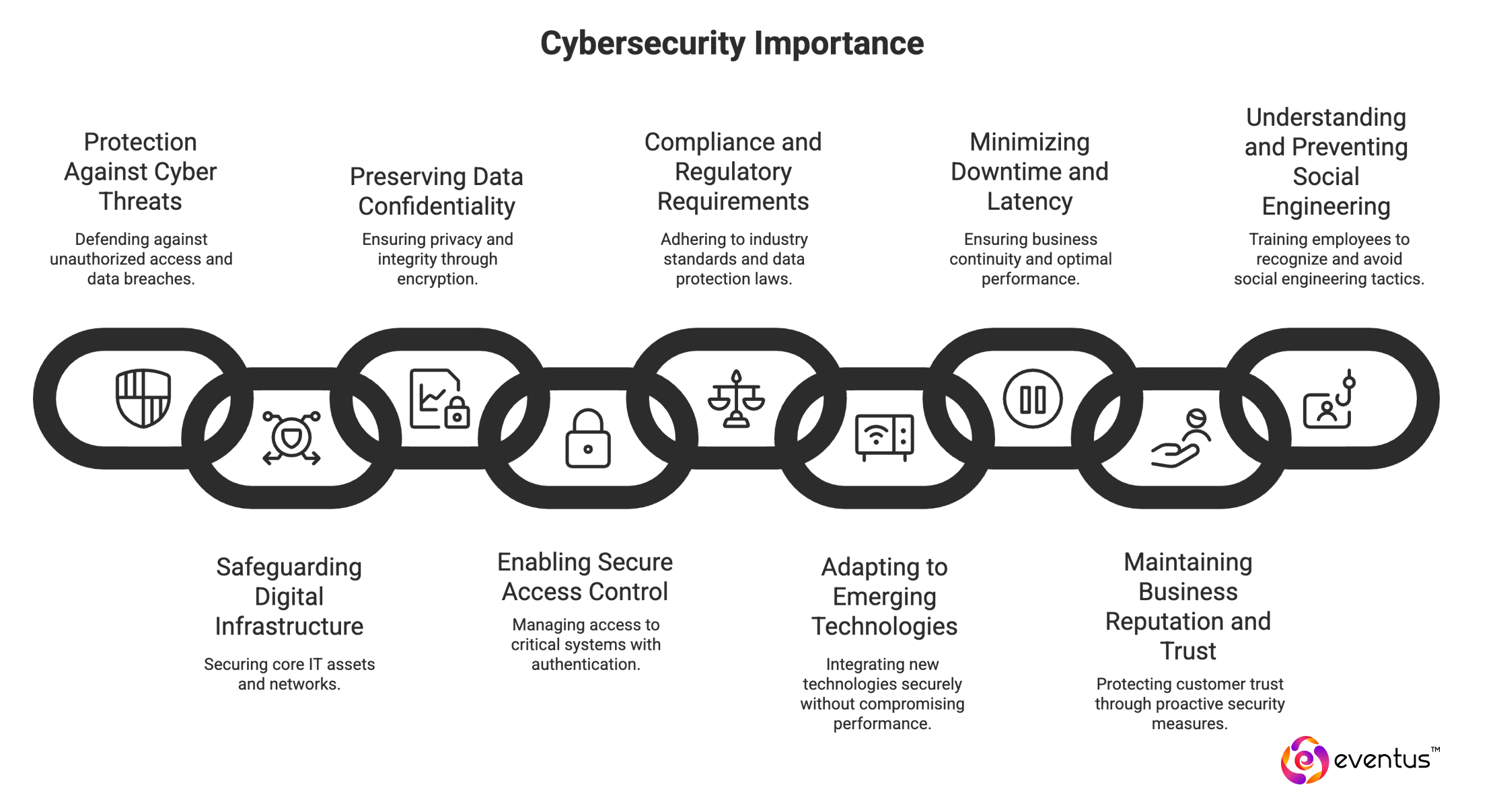
Cybersecurity is critically important for B2B organizations because it safeguards digital assets, infrastructure, and sensitive information from increasingly sophisticated threats. Here’s why it matters with technical relevance:
- Protection Against Cyber Threats: With the rise in cyberattacks, including phishing, malware, ransomware, and DDoS attacks, robust cyber security measures help defend against unauthorized access and data breaches
- Safeguarding Digital Infrastructure: Core IT assets like data centers, computer networks, and cloud environments (e.g., virtual private cloud) require active network security and firewall configurations to protect against internal and external threats
- Preserving Data Confidentiality: Through technologies such as encryption (see: encryption meaning, encryption definition), data at rest and in transit is secured, ensuring privacy and integrity. This is essential for protecting customer information and intellectual property
- Enabling Secure Access Control: Systems like IAM (Identity and Access Management), SSO (Single Sign-On), MFA (Multi-Factor Authentication), and 2FA help ensure that only authorized personnel can access critical systems, thereby reducing the attack surface
- Compliance and Regulatory Requirements: Organizations must adhere to industry standards and data protection laws. Strong information security frameworks and tools like DLP (Data Loss Prevention) support compliance by controlling access and preventing data exfiltration
- Adapting to Emerging Technologies: The adoption of IoT devices, 5G networks, edge computing, and SaaS platforms introduces new vulnerabilities. Effective cybersecurity strategies enable secure integration of such innovations without compromising performance or security
- Minimizing Downtime and Latency: Cyberattacks can cause significant service interruptions and impact latency. Secure computer networks and resilient architectures ensure business continuity and optimal performance
- Maintaining Business Reputation and Trust: A data breach or successful hacker intrusion can damage customer trust. Proactive IT security and incident response mechanisms help mitigate reputational risk
- Understanding and Preventing Social Engineering: Awareness and protection against tactics like social engineering attacks, phishing, and whaling are vital for employee training and defense-in-depth strategies
Cybersecurity is no longer optional; it is an operational necessity for modern enterprises to maintain trust, compliance, and uninterrupted service delivery in a threat-laden environment.
How do rising cyber threats exploit weak security?
Rising cyber threats target vulnerabilities across systems, networks, and user behavior. These threats exploit gaps in poorly implemented cybersecurity solutions, exposing businesses to damaging cyber attacks and data breaches. Common exploitation methods include:
- Unpatched Systems: Attackers exploit outdated software lacking security updates, breaching application security and enabling remote code execution
- Poor Network Configurations: Weak or misconfigured network security controls such as open ports or unsecured firewalls allow unauthorized lateral movement within corporate environments
- Insufficient Endpoint Protection: Devices without proper endpoint security become entry points for cyber threats, especially in remote work setups or BYOD environments
- Weak Authentication and Access Control: Lacking MFA or role-based access enables attackers to escalate privileges after compromising basic credentials
- Lack of Employee Vigilance: Absence of security awareness training leads to exploitation via social engineering, phishing, or business email compromise (BEC)
- Insecure Cloud Deployments: Misconfigured cloud security settings, such as public buckets or exposed keys, provide attackers direct access to sensitive data
- No Data Protection Measures: Missing data security and information security controls allow for unmonitored exfiltration of intellectual property and PII
- Inadequate Monitoring: Organizations without effective security operations, security tools, or logging fail to detect and respond to evolving threats in time
- Lack of Strategy: An undefined security strategy results in disjointed defenses, making it easier for a security threat to escalate
To reduce the risk, companies must apply best practices across infrastructure and operations, using integrated security services and layered defense mechanisms.
What is the cost and impact of security breaches?
A security breach creates significant financial and operational strain on organizations. The cost extends beyond immediate recovery, affecting long-term trust, compliance, and competitiveness.
| Aspect | Cost Impact (Benchmarks) | Operational / Strategic Impact |
| Direct Financial Losses | Average global cost of a security breach: $4.45M (IBM 2023). Ransomware-specific incidents: $5.13M average. | Higher spend on security technologies, security measures, and managed security services to mitigate recurring risks. |
| Reputation and Trust | Brand value loss estimated at 5–10% of annual revenue after a severe breach. | Loss of long-term contracts and customer attrition due to weakened trust in cyber safety. |
| Operational Disruption | Average downtime: 23 days per major incident. Estimated productivity loss: $600K–$1M per week. | Interruptions to workflows, project delays, and weakened system security resilience. |
| Compliance and Regulation | GDPR non-compliance fines: up to €20M or 4% of global turnover (whichever is higher). | Heightened scrutiny from regulators like Cybersecurity and Infrastructure Security Agency and National Cyber Security Centre. |
| Long-Term Cyber Risk Management | Annual spend on breach response and resilience improvements rises 15–25% post-incident. | Mandatory adoption of zero-trust security, tighter security architecture, and stronger security posture across IT. |
| Human and Organizational Impact | Overtime and retention costs for IT/security staff increase 20–30% post-breach. | Continuous cyber security awareness and security practices training required to respond to threats effectively. |
What are the types of cybersecurity?
Understanding the different types of cybersecurity is crucial to protecting computer networks, systems, and data from evolving threats. Each type focuses on specific areas of risk and defense within an organization’s overall security strategy:
- Network Security: Protects the integrity and usability of computer networks by implementing firewalls, intrusion prevention systems (IPS), and access controls to block unauthorized access and malicious traffic. This layer is foundational in defending against DDoS attacks and other threats
- Application Security: Application Security that software and apps are developed and maintained with robust security measures. This includes secure coding practices, vulnerability testing, and patch management to prevent exploitation through application-layer weaknesses
- Information Security: Focuses on safeguarding the confidentiality, integrity, and availability of data, both in transit and at rest. Encryption plays a vital role here—knowing the encryption definition and encryption meaning helps ensure effective implementation
- Endpoint Security: Defends individual devices such as laptops, desktops, and mobile devices against cyber threats. Tools like antivirus software, EDR (Endpoint Detection and Response), and patch management help mitigate risks from malware and ransomware
- Cloud Security: Addresses security concerns in cloud environments by securing cloud infrastructure, applications, and data. This includes managing IAM (Identity and Access Management), encryption, and configurations to reduce the risk of breaches in virtual private cloud and SaaS platforms
- IoT Security: Protects IoT devices and networks against vulnerabilities that arise from the interconnected nature of smart technologies. Measures include securing internet of things endpoints, firmware updates, and network segmentation to prevent lateral movement
- Operational Technology (OT) Security: Safeguards industrial control systems and hardware in critical infrastructure sectors. With the adoption of 5G and edge computing, OT environments face increased exposure to threats
- Identity and Access Management (IAM): Governs user identities and their access to systems and data. IAM solutions—including multi factor authentication (MFA) and single sign on (SSO)—help define access policies and enforce strict user authentication protocols
- Mobile Security: Protects smartphones and tablets against threats like phishing, malware, and data leakage. With the increase in BYOD policies, mobile device management is key to maintaining cyber safety
- Disaster Recovery and Business Continuity: Ensures that systems and data can be restored quickly after a cyber attack or system failure. Effective planning helps maintain data center operations and reduce downtime
- Infrastructure Security: Involves the protection of core IT infrastructure, including servers, routers, and computer networks. This type includes implementing secure configurations, patching vulnerabilities, and monitoring traffic using security tools
A 700-employee healthcare diagnostics provider nearly suffered a ransomware outage after a staffer fell for a phishing email. The attacker used stolen credentials to reach a legacy VPN, but a 30-day security sprint changed the outcome: the team rolled out single sign on (SSO) with multi-factor authentication (MFA) under a tighter identity and access management (IAM) program, replaced antivirus with endpoint detection & response (EDR), tightened firewall rules and network segmentation, and enforced TLS encryption and just-in-time training. The next phish failed—MFA blocked access; EDR contained the dropper in minutes. Metrics improved sharply: MTTD fell from 21 days to 8 minutes, MTTR from 5 days to 4 hours, and click-through dropped from 18% to 3%, averting six-figure losses.
What are the types of cybersecurity threats?
Cybersecurity threats continue to evolve in complexity and impact. These threats target vulnerabilities across networks, applications, and users, and pose risks to data integrity, confidentiality, and availability. Understanding the common types of cyber threats is critical to forming a proactive cyber security strategy that aligns with any established cybersecurity framework such as the NIST Cybersecurity Framework.
Here are the main types of cybersecurity threats:
- Malware Attacks
Includes viruses, worms, trojans, ransomware, and spyware. Malware exploits security flaws to infiltrate systems, steal data, or disrupt operations. It remains one of the most frequent security incidents globally - Phishing and Social Engineering
Threat actors trick users into revealing sensitive information such as credentials or financial details. These attacks often bypass technical controls and exploit the human element, underscoring the need for identity security and employee awareness - Ransomware
Encrypts files and demands payment for decryption. It disrupts business continuity, especially when endpoint security is not properly configured. This is a rising threat in global cybersecurity trends - Insider Threats
Malicious or negligent actions from employees or contractors. This type of threat bypasses perimeter defenses and requires strong security policies, access controls, and security orchestration to detect and mitigate - Advanced Persistent Threats (APTs)
Sophisticated, long-term attacks often backed by nation-states. APTs target high-value data and systems over time, often going undetected without security information and event management (SIEM) tools - Zero-Day Exploits
Attacks that take advantage of previously unknown vulnerabilities in software or hardware before patches are released. Zero-day threats challenge conventional security models and demand real-time detection capabilities - Denial-of-Service (DoS) and Distributed DoS (DDoS)
Overwhelms systems or networks with traffic, making them unavailable. DDoS attacks are mitigated by robust network security solutions and traffic filtering strategies - Man-in-the-Middle (MitM) Attacks
Attackers intercept communication between two parties to steal or manipulate data. Secure encryption protocols and network segmentation reduce the risk of cyber interception - Credential Stuffing and Brute Force Attacks
Exploiting reused passwords or weak authentication mechanisms to gain unauthorized access. Implementing zero trust security, MFA, and credential monitoring significantly reduces exposure - Cloud Threats
Misconfigured cloud storage, exposed APIs, or insecure integrations increase attack surfaces. These must be addressed through cloud governance, information technology security, and continuous security audits - IoT-Based Threats
Exploits targeting form of cyber weaknesses in connected devices. These threats can cascade into broader network breaches due to weak security in IoT architecture - Supply Chain Attacks
Infiltration via third-party vendors or software updates. These attacks bypass direct controls, requiring extended cybersecurity capabilities across vendor ecosystems
What is cryptojacking?
Cryptojacking is a form of cyberattack in which threat actors secretly use a victim’s computing resources—such as CPUs, GPUs, or cloud instances—to mine cryptocurrency without their consent. This attack is covert and typically operates in the background, making detection difficult while degrading system performance.
What are the best practices for cybersecurity?
Here are the best practices for maintaining a strong cybersecurity posture:
- Implement Strong Access Controls
Limit user access based on roles and responsibilities. Security focuses on protecting critical systems by enforcing least privilege and multi-factor authentication - Keep Software and Systems Updated
Apply patches and updates regularly to fix known vulnerabilities. This is a foundational step in responding to cyber threats proactively - Conduct Regular Security Audits
Periodic assessments help identify weaknesses, evaluate security capabilities, and ensure compliance with internal and regulatory standards - Use Endpoint and Application Security
Endpoint security protects devices such as laptops and phones, while application security focuses on securing software at the code and deployment level - Monitor Networks Continuously
Real-time monitoring allows early detection of anomalies and cyber security threats. Integration of tools across security and networking layers is essential - Train Employees on Cybersecurity Awareness
Human error is a top cause of breaches. Cyber safety tips and awareness programs reduce the chances of phishing, social engineering, and credential misuse - Back Up Data Regularly
Offsite and encrypted backups enable recovery after ransomware attacks or data loss - Segment Networks and Use Firewalls
Network segmentation limits lateral movement during breaches. Firewalls act as a barrier against unauthorized access - Use Encryption for Data at Rest and in Transit
Encryption protects data from cyber threats by ensuring it cannot be read even if intercepted or stolen - Develop an Incident Response Plan
Be prepared to act quickly in case of a breach. Clear procedures ensure rapid containment and recovery, enhancing defense against cyber attacks - Adopt a Risk-Based Cybersecurity Strategy
Prioritize actions based on risk exposure, asset value, and potential business impact. This aligns with key types of cyber security best suited for the organization - Stay Informed of Cyber Security Trends
Understanding top 10 cyber threats and adapting to emerging attack vectors strengthens preparedness and future-proofing
What are the main challenges in cybersecurity?
Cybersecurity faces several persistent and emerging challenges that hinder an organization’s ability to protect its assets effectively. These challenges span technological, human, and operational dimensions:
- Evolving cyber threats like ransomware, advanced persistent threats (APTs), and zero-day exploits outpace traditional defenses, requiring continuous adaptation of security strategies
- Security refers not only to technical safeguards but also to the people and processes involved—human error and lack of awareness remain critical vulnerabilities
- The complexity and fragmentation of IT environments, including cloud, on-premises, and hybrid infrastructures, increase the difficulty of implementing security consistently across all layers
- Limited budgets and skilled workforce shortages constrain the ability to enhance security posture, especially in small to mid-sized enterprises
- Fragmented aspects of cyber security—from endpoint protection to identity management—often operate in silos, reducing overall threat visibility and response efficiency
- Rising regulatory and compliance pressures require more robust controls and documentation, which many organizations struggle to maintain
- Lack of centralized threat intelligence and automation delays response time, weakening defense against fast-moving threats and security breaches
- Despite available security provides and frameworks, adoption of modern solutions is inconsistent, leading to gaps in defense
- These challenges underscore why cyber security is important and demand ongoing evaluation of key security capabilities to maintain resilience
What are the top cybersecurity tools and technologies?
Top cybersecurity tools and technologies are essential for defending against evolving cyber threats and ensuring data protection across networks, systems, and endpoints. Here's a look at the most impactful solutions used in the field of cyber security:
- Firewall: A firewall in computer network security acts as a barrier between trusted internal networks and untrusted external ones. It filters traffic based on predefined security rules and is vital for preventing unauthorized access and threats like malware, phishing, and ransomware
- Encryption: Encryption refers to the process of converting data into unreadable code to prevent unauthorized access. Commonly used encryption algorithms protect sensitive data at rest and in transit. Understanding encryption meaning and the encryption definition is crucial in securing communications and cloud services
- Endpoint Detection and Response (EDR): EDR tools monitor endpoint activities, detect suspicious behaviors, and respond to threats. These are essential for identifying and mitigating advanced threats such as zero-day exploits and malicious software
- Intrusion Detection and Prevention Systems (IDS/IPS): These systems monitor traffic across a computer network, detect suspicious patterns, and block potential attacks like DDoS and SQL injection in real-time
- Identity and Access Management (IAM): IAM solutions control and define access privileges. The IAM full form highlights its core role: Identity and Access Management. IAM is especially important in SaaS and cloud security environments, using tools like multi-factor authentication (MFA) and single sign-on (SSO) to enhance security
- Antivirus and Anti-malware Software: These tools scan for and eliminate malware, viruses, and spyware. Recognizing malware meaning is key to deploying effective defenses against this type of cyber threat
- SIEM (Security Information and Event Management): SIEM platforms collect and analyze log data from across systems to provide real-time analysis of security alerts. It’s a central part of many modern cybersecurity strategies
- DLP (Data Loss Prevention): DLP tools prevent unauthorized sharing, leakage, or transmission of sensitive data. DLP full form stands for Data Loss Prevention, and it's critical in enforcing data handling policies
- VPN (Virtual Private Network): A VPN creates a secure, encrypted tunnel for data transmission, especially important in wide area network (WAN) or remote access contexts. It hides IP addresses and masks user activity from cyber threats
- Vulnerability Scanners: These tools scan networks, applications, and devices to identify weaknesses. Regular scans help in implementing security practices to reduce risk exposure
- Cloud Security Solutions: With the rise of IoT and 5G technologies, cloud security has become increasingly important. Tools within this category offer data encryption, access control, and threat intelligence tailored for cloud environments
- Ethical Hacking Tools: Also known as penetration testing tools, these simulate hacker techniques to find vulnerabilities. They're vital in understanding and preparing against real-world cyberattacks
- Network Segmentation: Implementing segmentation helps isolate parts of a network to prevent lateral movement by attackers, reducing the impact of breaches
- MFA (Multi-Factor Authentication): By requiring more than one method of identity verification, MFA significantly improves authentication security
What are the latest cybersecurity trends in 2025?
The latest cybersecurity trends in 2025 reflect the fast-paced evolution of threats, technology, and global digital infrastructure. As organizations expand their dependence on cloud computing, IoT, and 5G, the landscape of cyber security continues to shift. Below are the most prominent trends:
- Zero Trust Architecture: “Never trust, always verify” remains central. Zero trust security models are now widely adopted, minimizing lateral movement within a computer network and improving network segmentation
- AI and ML for Threat Detection: Artificial intelligence in cyber security is used for real-time malware detection, anomaly detection, and predictive threat intelligence, reducing latency in response times
- Rise of 5G-Specific Threats: The global rollout of 5G networks introduces new vectors for cyberattacks. Due to its low latency and increased bandwidth, 5g expands the attack surface across IoT and edge devices
- Expansion of IoT Security: The proliferation of IoT devices—from smart homes to industrial systems—has made IoT a major security concern. Securing these endpoints requires enhanced firewall configurations, updated internet protocol standards, and real-time monitoring
- Cloud Security and SaaS Protection: As businesses rely more on SaaS platforms and virtual private cloud environments, protecting these services from phishing attacks, misconfigurations, and insider threats becomes a priority
- Identity and Access Management (IAM): With distributed workforces, IAM solutions like MFA and SSO (single sign on) are critical. IAM ensures users can define access securely while preventing unauthorized logins and hacker entry points
- Phishing Gets More Sophisticated: Phishing—especially deepfake-enabled and AI-powered variants—remains a top threat. Understanding phishing meaning and deploying robust email and network security tools are now essential
- Ransomware-as-a-Service (RaaS): Ransomware continues to evolve with professionalized distribution. Ransomware attacks target data centers, critical infrastructure, and cloud services, requiring stronger backup and encryption protocols
- Wider Use of Encryption: Modern encryption algorithms protect data in transit and at rest. Knowing the encryption definition and implementing the right tools is vital for both compliance and defense
- Edge Computing Security: With data processed closer to where it’s generated, edge computing brings efficiency but also new vulnerabilities. Securing edge networks relies on hardened OSI model layers, strict access control, and integrated threat detection systems
- IoT in OT Environments: In sectors like manufacturing, IoT blends with operational technology (OT), exposing systems to cyber threats like DDoS (ddos attack) and malware. Define security frameworks that bridge IT and OT are in demand
- Data-Centric Security Models: Organizations now define cyber security goals around data itself—protecting the asset rather than just the perimeter
These trends underline why understanding what is cyber security and staying updated on evolving threats is no longer optional—it is critical. Implementing adaptive network security strategies ensures resilience in a world where cyber threats grow more complex daily.
What are the career opportunities in cybersecurity?
Career opportunities in cybersecurity span across industries due to the increasing volume and complexity of cyber threats. As organizations recognize why cyber security is important, they seek skilled professionals to protect critical systems and data. Key roles include:
- Security Analyst – Monitors networks for suspicious activity and investigates security incidents. This role is often a gateway into the field
- Penetration Tester (Ethical Hacker) – Simulates attacks to identify vulnerabilities before malicious actors do
- Security Engineer – Designs and implements secure network solutions and develops systems to defend against intrusion
- Incident Responder – Handles breaches and minimizes damage during security incidents, ensuring rapid containment and recovery
- Security Architect – Builds and maintains a company’s security infrastructure, including policies, protocols, and technologies
- Chief Information Security Officer (CISO) – A senior executive responsible for strategic security planning and compliance
- Governance, Risk, and Compliance (GRC) Analyst – Ensures that security practices align with regulatory standards and internal policies
- Threat Intelligence Analyst – Studies threat actors, emerging vulnerabilities, and attack trends to anticipate future risks
- Security Software Developer – Creates tools and platforms for detecting and preventing cyber threats
- Cloud Security Specialist – Focuses on securing cloud infrastructure, particularly critical as businesses transition to cloud environments
What resources are available for businesses in cybersecurity?
Businesses have access to a wide range of cybersecurity resources designed to help them protect organisations from cyber threats and strengthen their security posture. These resources span training, frameworks, tools, and professional services aligned with various cybersecurity domains.
Key resources include:
- Cybersecurity Frameworks
• NIST Cybersecurity Framework
• ISO/IEC 27001
• CIS Controls
These frameworks provide structured approaches for managing cybersecurity risks - Cybersecurity Solutions and Tools
• Endpoint protection platforms (e.g., CrowdStrike, SentinelOne)
• Firewalls, intrusion detection/prevention systems (IDS/IPS)
• SIEM (Security Information and Event Management) tools
These are essential for real-time monitoring, threat detection, and response - Managed Security Service Providers (MSSPs)
Businesses lacking internal expertise can outsource to MSSPs for continuous monitoring, threat intelligence, and incident response - Government and Nonprofit Resources
• Cybersecurity and Infrastructure Security Agency (CISA) – Offers alerts, tools, and training
• National Cyber Security Centre (NCSC) – Provides guidance, best practices, and incident handling resources
• SANS Institute – Offers industry-respected training and research
• OWASP – Focuses on application security, providing open-source tools and best practice - Cybersecurity Foundations and Training Programs
• CompTIA Security+, CISSP, CEH – Recognized certifications for building knowledge in different areas of cybersecurity
• Training platforms such as Cybrary, TryHackMe, and Coursera provide flexible learning path - Cyber Insurance Providers
Helps businesses transfer residual cyber risk and recover from financial losses due to breaches or ransomware attacks - Open-Source Intelligence and Threat Feeds
Resources like VirusTotal, Shodan, and MISP enable proactive threat detection and monitoring - Industry-Specific Guidelines
Healthcare, finance, and critical infrastructure sectors often follow domain-specific cybersecurity regulations and standards.
What are the major recent cybersecurity developments?
1. India Emerging as a Cyberthreat Hotspot
Acronis' H1 2025 Cyberthreats Report identifies India as ground zero for global cyberthreats, signaling rapidly increasing attacks and vulnerabilities in the region.
2. QuirkyLoader: New Malware on the Radar
A sophisticated malware loader named QuirkyLoader is making rounds, actively distributing infostealers and Remote Access Trojans (RATs)—posing a serious risk to endpoint security.
3. The Rise of the 'AI Hacking Era'
Recent reports suggest both attackers and defenders are embracing AI—including LLMs like ChatGPT—for tasks like phishing, social engineering, and automated vulnerability research. Experts debate whether this truly represents an "AI hacking era" or is more hype than reality.
4. India’s Tac Infosec Eyes Nasdaq with CyberScope IPO Plans
Indian cybersecurity firm Tac Infosec saw its stock skyrocket after announcing its U.S.-based subsidiary, CyberScope, plans to pursue a Nasdaq IPO—a possible first for an India-listed cybersecurity company.
Is cyber security hard?
Yes, cybersecurity can be hard—but it depends on the level of expertise you're aiming for and the area within cybersecurity. It requires continuous learning across areas like network security, cloud security, and threat detection. However, it’s not inaccessible—structured training, specialized roles, and modern tools make it manageable for those committed to learning and adapting.