Identity and Access Management (IAM) is a key cybersecurity system that helps organizations manage user identities and control who can access digital resources. This article explains the main parts of IAM, like multi-factor authentication and role-based access control, and how it's used in cloud environments. It also covers top IAM tools such as AWS IAM and Okta, showing how IAM strengthens security and supports compliance.
Table of Contents
What is identity and access management?
Identity and Access Management (IAM) is a cybersecurity framework that enables organizations to manage user identities and control access to digital systems. It ensures that only authorized users have the right level of access to critical resources, protecting against data breaches and unauthorized activity. An effective IAM system combines identity management with access control mechanisms, such as role-based access control, to enforce policies across users and devices. By validating users and managing user access throughout the lifecycle, IAM enhances security, streamlines operations, and ensures compliance. Ultimately, IAM safeguards access to resources by aligning permissions with user roles and responsibilities.
What is the difference between identity management and access management?
| Aspect | Identity Management | Access Management |
| Purpose | Manage digital identities and user identity information | Regulate access rights and access to sensitive data |
| Core Function | Verify a user’s identity, store credentials, and assign roles | Grant and restrict access based on roles and permissions |
| Tools and Systems | Identity provider, identity management system, identity governance | Access management systems, IAM policies, and attribute-based access control |
| Scope | Handles the creation and lifecycle of identities | Defines what users can access after authentication |
| Integration with IAM | Forms the “identity” layer of identity access management (IAM) | Forms the “access” layer of IAM solutions |
| Security Contribution | Prevents identity fraud through identity federation and verification | Ensures secure access by controlling permissions and privileged access |
| Example in AWS Context | AWS IAM Identity Center manages user identities | IAM policies define access to AWS services and resources |
Why is identity and access management important?
Identity and Access Management (IAM) is essential for securing modern enterprises. It ensures that only verified users gain access to corporate resources and that access privileges align with business roles. IAM helps prevent unauthorized access, enforces permissions management, and maintains consistent access control across systems. When integrated with a cybersecurity SOC, IAM enhances real-time visibility into identity-related threats and supports faster incident response. With federated identity management and privileged access management, IAM strengthens your organization’s security posture. It supports compliance, enables fine-grained access, and reduces the risk of identity threat detection failures. By implementing IAM, businesses can grant access to the right users while safeguarding access to sensitive information and enhancing operational trust.
What are the core components of an IAM system?
An effective Identity and Access Management (IAM) system is built on a combination of technical and administrative components that ensure secure access to resources, maintain identity security, and support regulatory requirements, aligning closely with the broader Security Operations Center framework to enhance centralized monitoring and incident response.
The core components include:
- Identification – Recognizes and registers individuals or devices within a system.
- Authentication – Confirms the identity of a user attempting to access a resource.
- Authorization – Grants or denies access based on predefined roles or policies.
- Multi-Factor Authentication (MFA) – Adds extra verification layers beyond passwords.
- Identity Management – Creates, stores, and maintains user identity records.
- Access Management – Regulates how and when users access systems and data.
- Access Control – Applies security rules to restrict access to sensitive resources.
- Role-Based Access Control (RBAC) – Assigns permissions based on user roles.
- Granular Permissions – Enables fine-tuned control over individual actions and data.
- Attribute-Based Access Control (ABAC) – Makes access decisions based on user and resource attributes.
- Identity Governance – Ensures user access aligns with compliance and security policies.
- Compliance Management – Supports audit, legal, and regulatory requirements.
- Access Monitoring – Tracks user access activity for anomalies or misuse.
- Federation / Federated Identity Management – Allows identity sharing across trusted domains or systems.
- Single Sign-On (SSO) – Permits one-time login to access multiple applications.
- Privileged Access Management (PAM) – Secures and monitors high-level administrative access.
- Administration – Manages IAM policies, users, roles, and configurations.
- User Management – Handles onboarding, modification, and deactivation of user accounts.
- Identity as a Service (IDaaS) – Delivers cloud-based identity services on demand.
- Artificial Intelligence Integration – Automates threat detection and policy enforcement using AI.
- Digital Identity Repository – Centralized storage of all digital identities.
- Identity Governance and Administration (IGA) – Integrates identity lifecycle with policy enforcement.
- Access Attempt Logging and Reporting – Captures and reports access behaviors and violations.
- Authorization to Relevant Resources – Ensures users only access data necessary for their role.
- IAM Tools and Technologies – Software solutions (e.g., AWS IAM, Azure AD) that power IAM functions.
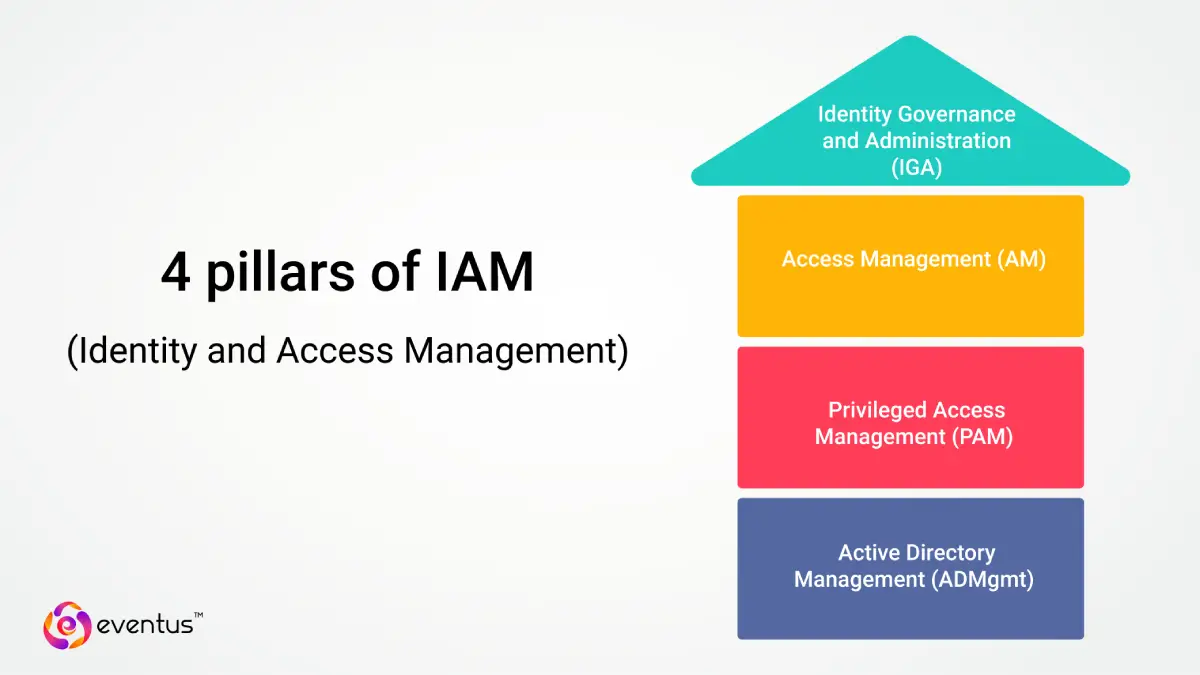
What are the 4 pillars of IAM?
The 4 pillars of IAM are as follows:
- Identity Governance and Administration (IGA)
Manages the entire identity lifecycle, including provisioning, deprovisioning, policy enforcement, and compliance reporting, ensuring the identity of the user is consistently governed across systems—a capability often evaluated alongside SOC as a Service pricing when organizations assess end-to-end security and compliance solutions. - Access Management (AM)
Controls how users access applications and systems, using mechanisms like SSO, MFA, and access permissions to ensure secure access to resources—features that are often reinforced by SOC solution providers to enhance identity security within a broader threat detection and response strategy. - Privileged Access Management (PAM)
Protects and monitors user access to critical information and systems by managing elevated credentials, reducing the risk of unauthorized access and insider threats. - Active Directory Management (ADMgmt)
Centralizes identity control via directory services such as Microsoft AD or Azure AD, enabling organizations to verify their identities, manage access, and enforce policies across the enterprise.
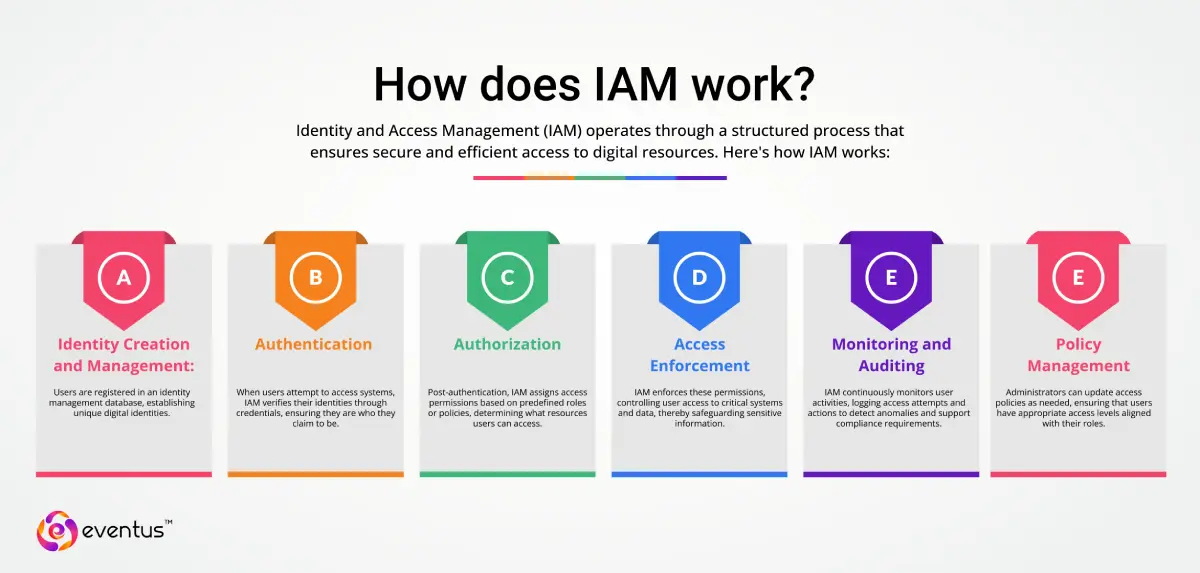
How does IAM work?
Identity and Access Management (IAM) operates through a structured process that ensures secure and efficient access to digital resources. Here's how IAM works:
- Identity Creation and Management: Users are registered in an identity management database, establishing unique digital identities.
- Authentication: When users attempt to access systems, IAM verifies their identities through credentials, ensuring they are who they claim to be.
- Authorization: Post-authentication, IAM assigns access permissions based on predefined roles or policies, determining what resources users can access.
- Access Enforcement: IAM enforces these permissions, controlling user access to critical systems and data, thereby safeguarding sensitive information.
- Monitoring and Auditing: IAM continuously monitors user activities, logging access attempts and actions to detect anomalies and support compliance requirements.
- Policy Management: Administrators can update access policies as needed, ensuring that users have appropriate access levels aligned with their roles.
- By implementing IAM, organizations enhance their security posture, streamline access management, and ensure that only authorized individuals can access critical resources.
What are IAM tools and solutions?
Identity and Access Management (IAM) tools are essential solutions that help organizations manage digital identities and control user access to critical systems and data. These tools ensure that only authorized individuals can access specific resources, enhancing security and compliance, especially when integrated with services from a managed SOC provider to enable continuous monitoring and rapid incident response.
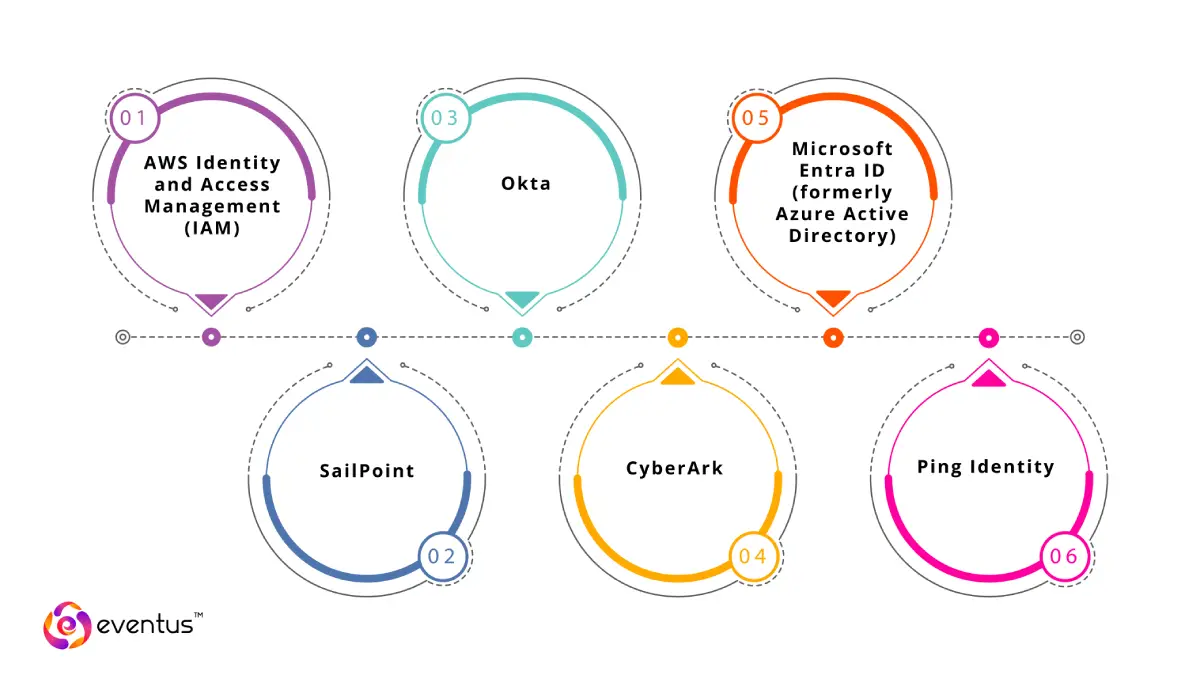
Popular IAM Solutions:
- AWS Identity and Access Management (IAM): Provides fine-grained access control across AWS services, enabling secure management of AWS resources.
- Okta: Offers a comprehensive identity platform with features like SSO, MFA, and lifecycle management, suitable for cloud and on-premises applications.
- Microsoft Entra ID (formerly Azure Active Directory): Delivers identity services for Microsoft environments, including SSO, conditional access, and identity protection.
- SailPoint: Focuses on identity governance, providing tools for compliance, access certifications, and policy enforcement.
- CyberArk: Specializes in privileged access management, securing high-level accounts and sensitive systems.
- Ping Identity: Provides solutions for SSO, MFA, and identity federation, supporting hybrid IT environments.
How is IAM implemented in cloud environments?
Implementing Identity and Access Management (IAM) in cloud environments involves configuring secure resource access controls and managing IAM users across distributed systems.
- Provisioning Identities: Cloud IAM begins by creating and managing IAM users and roles to represent every identity that needs access to systems.
- Policy-Based Access Control: Admins define who can access which resources using IAM products that enforce access to the resources through roles, groups, and permissions.
- Granular Permissions: Fine-tuned resource access is granted based on roles, reducing risk and limiting access to sensitive information.
- Monitoring Access: Continuous monitoring access ensures visibility into usage, helping detect anomalies and maintain a secure security system.
- Centralized Governance: Cloud IAM enables IAM and compliance by unifying access control policies across multi-cloud or hybrid environments.
- Automated Lifecycle Management: Automates onboarding and offboarding to eliminate unused access and reduce human error.
- Scalability and Flexibility: Cloud-native IAM technologies adapt to dynamic enterprise needs, supporting thousands of identities across global infrastructures.
- Audit and Compliance Support: Logs and reports generated through IAM platforms support audits and meet regulatory standards.
- Enhanced Security Posture: IAM implementation in the cloud improves visibility, enforces least privilege, and secures critical resources effectively.
How does IAM support cybersecurity?
Identity and Access Management (IAM) supports cybersecurity by ensuring that only authenticated users can access critical systems and data, significantly reducing the risk of unauthorized activity.
Here’s how IAM supports cybersecurity:
- Restricts Unauthorized Access: IAM ensures only verified users can access critical systems, reducing the attack surface.
- Enforces Least Privilege: Grants users only the permissions they need, helping prevent internal threats and privilege escalation.
- Supports Real-Time Monitoring: When integrated with a 24/7 managed SOC, IAM provides user access logs that help detect anomalies and threats.
- Enables Effective SOC Audits: IAM logs and identity records support compliance checks and detailed SOC audits.
- Improves Incident Response: IAM helps SOC as a Service vendors and top SOC service providers quickly trace suspicious activity to specific identities.
- Aligns with Compliance Requirements: IAM enforces access policies that meet security regulations and audit standards.
- Enhances Visibility Across Environments: Centralizes access control, helping SOC as a Service MSSPs monitor identity-based threats across hybrid infrastructures.
What are the leading IAM vendors and products?
Here are the leading IAM vendors and their products, often integrated with SOC environments to enhance identity-driven threat detection and access control.
- Okta Identity Cloud
A cloud-native IAM platform offering SSO, MFA, and user lifecycle management for workforce and customer identities. - Microsoft Entra ID (formerly Azure Active Directory)
Provides identity services, conditional access, identity protection, and seamless integration with Microsoft 365 and Azure. - Ping Identity Platform
Delivers adaptive authentication, SSO, and MFA for hybrid IT environments and enterprise-scale identity needs. - OneLogin
Offers unified access management with SSO, MFA, and automated user provisioning for fast and secure deployments. - SailPoint Identity Security Cloud
Focuses on identity governance with AI-driven access reviews, policy enforcement, and compliance reporting. - CyberArk Privileged Access Management
Specializes in securing privileged accounts, session isolation, credential management, and real-time threat detection. - Saviynt Identity Cloud
A converged identity platform combining governance, access management, and privileged access for complex enterprises. - IBM Security Identity Governance and Intelligence (IGI)
Offers centralized user lifecycle management, access certifications, and compliance monitoring for large organizations. - Oracle Identity Governance
Delivers scalable IAM with automated provisioning, policy enforcement, and detailed access control capabilities. - ForgeRock Identity Platform
Provides identity management, directory services, access management, and an identity gateway in a unified platform.