This article explains what mobile security is, why it’s critical for modern businesses, and how to defend against mobile threats like malware, phishing, spyware, and insecure networks. It outlines best practices such as encryption, VPNs, 2FA, and app control, while also exploring enterprise risks, BYOD challenges, and compliance concerns. The article includes 2025 updates like Android 16’s stingray detection and SK Telecom’s data breach to highlight evolving mobile security needs.
Table of Contents
What is Mobile Security?
Mobile security in cybersecurity refers to the strategies, technologies, and practices used to protect mobile devices—including smartphones, tablets, and laptops—from threats that can compromise data integrity, user privacy, and device functionality. As mobile devices have become essential tools in personal, corporate, and government operations, they have also become prime targets for cyber threats—requiring continuous monitoring and response through integrated systems such as a Security Operations Center (SOC).
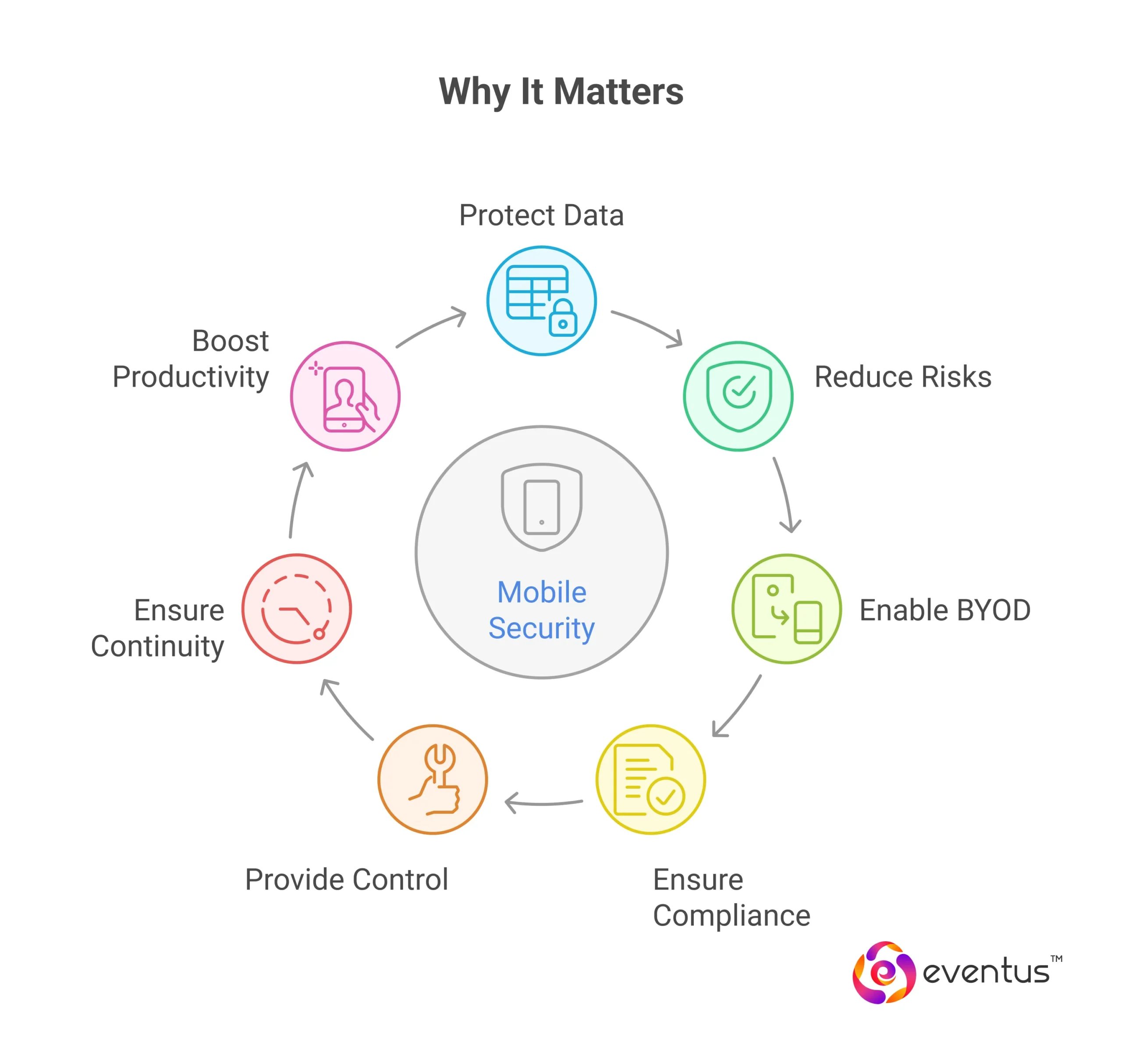
Why It Matters?
With the number of mobile phone users globally exceeding 6 billion, and with many businesses relying on mobile computing for operations, the mobile threat landscape has grown significantly. To address this, enterprises are increasingly adopting SOC as a service to monitor mobile endpoints, detect anomalies in real time, and respond to incidents more efficiently. Failing to secure mobile devices exposes individuals and enterprises to cyber threats, data breaches, and financial loss.
- Protects sensitive data across mobile devices through encryption and secure access controls.
- Reduces cybersecurity risks by preventing malware, phishing, ransomware, and other mobile threats—especially when supported by a managed SOC provider capable of real-time threat detection and incident response.
- Enables secure BYOD and remote work by isolating corporate data and enforcing device-level policies.
- Supports regulatory compliance (e.g., GDPR, HIPAA) by safeguarding personal and client information.
- Provides IT teams with control and visibility via MDM tools for device monitoring, remote wipe, and app management.
- Ensures business continuity by minimizing downtime and mitigating risks from mobile-based attacks.
- Boosts employee productivity and confidence by allowing secure use of mobile apps and business tools.
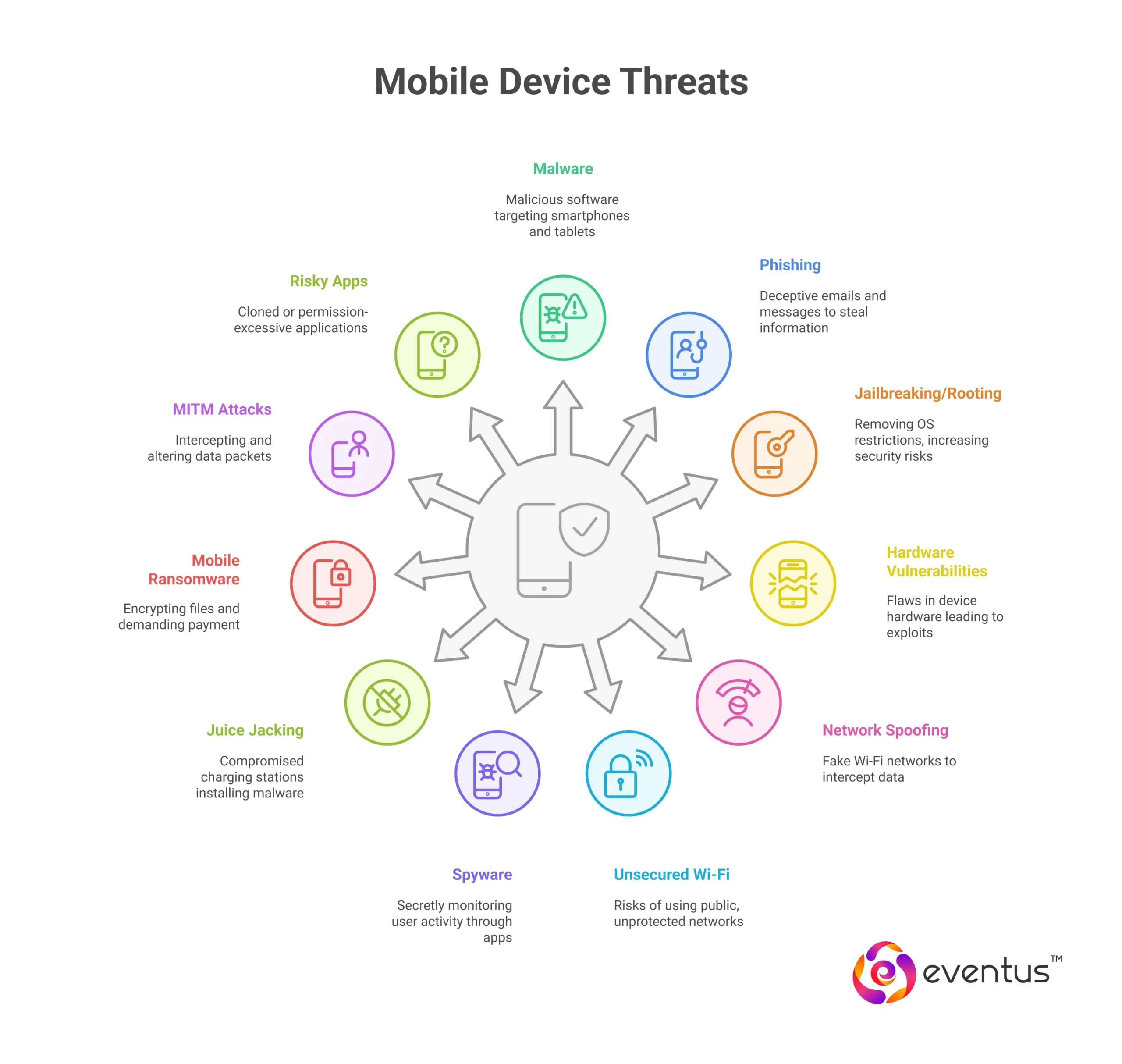
What types of threats target mobile devices?
Modern mobile devices face a wide array of attack vectors, including
1. Malware on smartphones
Mobile malware refers to malicious software specifically designed to target smartphones and tablets. Common forms include:
- Trojans that masquerade as legitimate apps.
- Worms and viruses that spread through infected files or downloads.
- Ransomware that locks users out of their device or files until a payment is made.
2. Phishing attacks
Phishing on mobile is especially dangerous due to limited screen size and user distraction. Attackers send deceptive:
- Emails with malicious links.
- SMS messages with shortened URLs.
- In-app messages posing as legitimate prompts.
3. Dangers of jailbreaking or rooting devices
Jailbreaking (iOS) or rooting (Android) removes operating system restrictions, allowing for customization—but at the cost of security features. Risks include:
- Disabling built-in security software and encryption.
- Installing apps without app store verification.
- Creating unauthorized access points for cyber threats.
4. Hardware vulnerabilities
Mobile phones can also suffer from hardware-level flaws such as:
- Firmware exploits targeting chipsets.
- Flaws in baseband processors used for cellular communication.
- Lack of security updates for older devices.
5. Network spoofing
Network spoofing involves attackers setting up fake Wi-Fi networks to trick users into connecting. Once connected:
- Data can be intercepted and manipulated.
- Login credentials and session cookies are stolen.
- Devices can be infected with malware or redirected to malicious websites.
6. Risks of unsecured Wi-Fi networks
Using unsecured Wi-Fi networks exposes devices to various security risks, including:
- Man-in-the-middle (MITM) attacks.
- Unencrypted data transmission.
- Unauthorized access to apps and personal data.
7. Spyware infiltrating mobile devices
Spyware is a type of malware that secretly monitors user activity. It can be introduced through:
- Infected apps.
- Phishing links.
- Malicious websites.
8. Juice Jacking
Juice jacking occurs when a compromised USB charging station is used to:
- Install malicious software on a mobile device.
- Extract sensitive data during charging.
To prevent juice jacking:
- Use USB data blockers or charging-only cables.
- Avoid public charging stations.
- Charge with a personal power bank or outlet adapter.
9. Mobile Ransomware
Mobile ransomware encrypts device files or locks the screen, demanding payment for release. It typically:
- Spreads through malicious links or fake updates.
- Exploits unpatched security vulnerabilities.
- Can affect both Android and iOS platforms.
10. Man-In-The-Middle (MITM) attacks
MITM attacks occur when a hacker positions themselves between a device and the network. This allows:
- Intercepting of private communications.
- Altering of data packets.
- Credential theft from apps or websites.
11. Applications introduce mobile threats
Risky apps come in several forms:
- Cloned apps mimicking legitimate ones from the Google Play Store.
- Apps asking for excessive or unrelated permissions.
- Apps that transmit unencrypted data or lack security compliance.
How to Protect Your Business from Mobile Security Threats?
Here’s a structured overview of security best practices and strategies to protect your enterprise from mobile security threats. Verizon’s 2024 Mobile Security Index shows that 79% of organizations had to make changes to their mobile security posture after experiencing a mobile-related compromise.
Mobile Device Encryption
Encryption is a foundational layer of security for mobile computing:
- Encrypt Internal Storage: Both iOS and Android offer native encryption capabilities. Ensure it is enabled by default.
- Use Encrypted Communication Protocols: Enforce HTTPS and secure email protocols (e.g., SSL/TLS) to protect sensitive data in transit.
- Full-Disk Encryption via MDM: For enterprise Android devices, enforce full-disk encryption using your MDM solution, ensuring corporate data is safeguarded even if the device is lost or stolen.
Two-Factor Authentication (2FA) for Mobile Access
Two-factor authentication adds an essential layer of security for mobile access:
- Combats Credential Theft: Even if a hacker obtains a user’s password, 2FA ensures they can't access corporate apps or systems without a second verification factor.
- Reduces Attack Surface: Particularly effective against phishing and brute-force attacks that target mobile users.
- Methods: Use authenticator apps, biometric verification, or hardware tokens instead of relying solely on SMS-based verification, which can be intercepted.
VPN In Mobile Security
Using a Virtual Private Network (VPN) is a critical defense mechanism for mobile security threats:
- Protects Data on Unsecured Networks: Encrypts traffic on public Wi-Fi, preventing interception by attackers.
- Maintains Anonymity and Privacy: Ensures mobile phone users’ activities are shielded from malicious actors and unauthorized access.
- Enterprise VPN Configuration: Deploy per-device VPN profiles to enforce secure tunnels for work-related mobile apps and services.
Manage Device Access for Remote Employees
In 2023, the City of Oakland reported a ransomware attack that disrupted operations after attackers gained initial access through a compromised mobile device used for remote access. Remote access introduces new vectors for mobile threat actors. Effective access control is essential:
- Segment Access by Role and Device Type: Limit access to data based on employee roles and whether they are using a corporate-managed device.
- Zero Trust Model: Assume no device is secure by default. Authenticate every session and limit lateral movement in the network.
- Remote Wipe and Lock Capabilities: Ensure the ability to remotely disable lost or stolen devices using endpoint security tools.
Policies To Be Included in a Mobile Security Strategy
A robust mobile device security policy should include:
- Acceptable Use Guidelines: Define which apps, websites, and device types are allowed for business use.
- Bring Your Own Device (BYOD) Rules: Clarify the responsibilities of employees who use personal mobile devices to access company systems.
- Incident Response Procedures: Detail steps for handling security incidents involving mobile phones, such as ransomware attacks or phishing attempts. According to Zimperium’s 2023 Mobile Threat Report, 60% of phishing attacks now target mobile devices, and 1 in 5 enterprise devices encounter at least one mobile threat each quarter.
Enforcement Of App Permission Restrictions
Controlling app permissions reduces exposure to threats like malware and data leaks:
- Pre-Approve Apps: Use mobile security software or MDM to vet and whitelist trusted applications.
- Restrict Unnecessary Permissions: Prevent apps from accessing location, microphone, or contacts unless explicitly needed.
- Monitor App Behavior: Regularly audit app permissions and flag apps that request excessive access or behave anomalously.
Educating Employees on Mobile Security Hygiene
Awareness remains the most effective defense against social engineering and malicious links:
- Conduct Cyber Hygiene Training: Educate employees on recognizing phishing messages, malicious websites, and app store scams.
- Simulate Attacks: Run mobile-specific phishing simulations to assess and improve user response.
- Promote Updates: Encourage prompt installation of security patches and mobile operating system updates.
Tools Monitoring Mobile Device Behavior and Anomalies
Advanced monitoring tools help identify unusual behavior on mobile endpoints:
- Mobile Threat Defense (MTD) Platforms: These tools analyze device, network, and app behavior for signs of mobile malware or compromise.
- Behavioral Analytics: Use AI-powered tools that learn user behavior to detect anomalies that may indicate malicious activity.
- Security Information and Event Management (SIEM) Integration: Feed mobile logs into your SIEM for centralized threat detection.
Securing Mobile Operating Systems and Firmware Updates
Maintaining up-to-date software is essential for resilience against emerging mobile security threats:
- Enforce Update Compliance: Mandate regular patching of OS and security features using your MDM platform. In 2022, Austrian Post was fined €9.5 million for failing to secure location and device data collected via their mobile application without adequate user consent.
- Block Jailbroken or Rooted Devices: These often bypass OS-level protections and are prime targets for mobile ransomware.
- Vet Firmware Versions: Ensure device firmware has not been tampered with, especially in BYOD environments. In 2021, attackers exploited unsecured BYOD devices to breach the UK Ministry of Defence, exposing sensitive internal documents shared over personal mobile networks.
What Are the Enterprise Risks of Inadequate Mobile Security?
Inadequate mobile security exposes enterprises to a range of operational, financial, legal, and reputational risks that can severely undermine organizational resilience. Below, we examine the most critical consequences of poor mobile security practices.
Business consequences of mobile breaches
- Operational disruptions from ransomware or malware can halt access to email, VPNs, and enterprise apps.
- Intellectual property loss occurs when sensitive business data is extracted from compromised mobile devices.
- Customer trust deteriorates after publicized breaches involving personal or client information. Under GDPR, failure to secure personal data on mobile devices can lead to fines of up to €20 million or 4% of annual global turnover—whichever is higher.
- Attack surfaces increase when outdated mobile operating systems, especially on Android devices, are exploited.
Data leakage affecting enterprise compliance
- Data breaches through unsecured mobile apps or Wi-Fi lead to non-compliance with GDPR, HIPAA, and other regulations.
- Failed audits due to weak mobile security practices jeopardize vendor relationships and certifications.
- Regulatory obligations mandate breach disclosures, resulting in reputational damage and legal scrutiny.
Financial impacts of mobile-related cyberattacks
- Remediation and forensic analysis post-breach demand significant security team and financial resources.
- Downtime caused by malware infections on mobile devices reduces productivity across departments.
- Legal costs, settlements, and compliance penalties result from mishandled mobile security incidents.
- Repeated incidents tied to mobile endpoint failures may lead to increased cybersecurity insurance premiums.
Attackers exploiting enterprise mobile communication networks
- Unsecured public Wi-Fi allows attackers to intercept unencrypted mobile communications.
- Man-in-the-middle (MITM) attacks compromise app and email data when VPNs are not enforced.
- Malicious apps downloaded outside trusted app stores such as Google Play exploit OS-level permissions.
- SMS phishing and malicious links in messaging apps remain high-frequency mobile attack vectors.
Legal liabilities arising from unsecured employee devices
- Organizations can be held negligent for not enforcing mobile device security best practices.
- Data privacy violations occur when personal mobile phones access corporate data without encryption.
- Liability extends to third-party damages when a compromised mobile device triggers downstream breaches.
Impact of BYOD (Bring Your Own Device) policies
- BYOD environments often lack consistency in security software, especially across different device types.
- Shadow IT emerges as employees install unapproved mobile apps that bypass enterprise security.
- Data segregation fails when business and personal data share space on unmanaged mobile devices.
- Apps with excessive permissions on native or Android platforms introduce high leakage potential.
Compromised devices affecting overall network security
- Infected mobile phones can be leveraged for lateral movement within enterprise networks.
- Credential harvesting through spyware or phishing apps exposes critical systems to unauthorized access.
- Malware introduced via mobile spreads to other endpoints, increasing infection scope.
- Devices lacking endpoint protection weaken the organization’s overall cybersecurity posture.
What Are the Latest Mobile Security Developments in 2025?
The mobile security landscape is constantly evolving, and recent developments highlight the growing urgency to address advanced threats targeting mobile users.
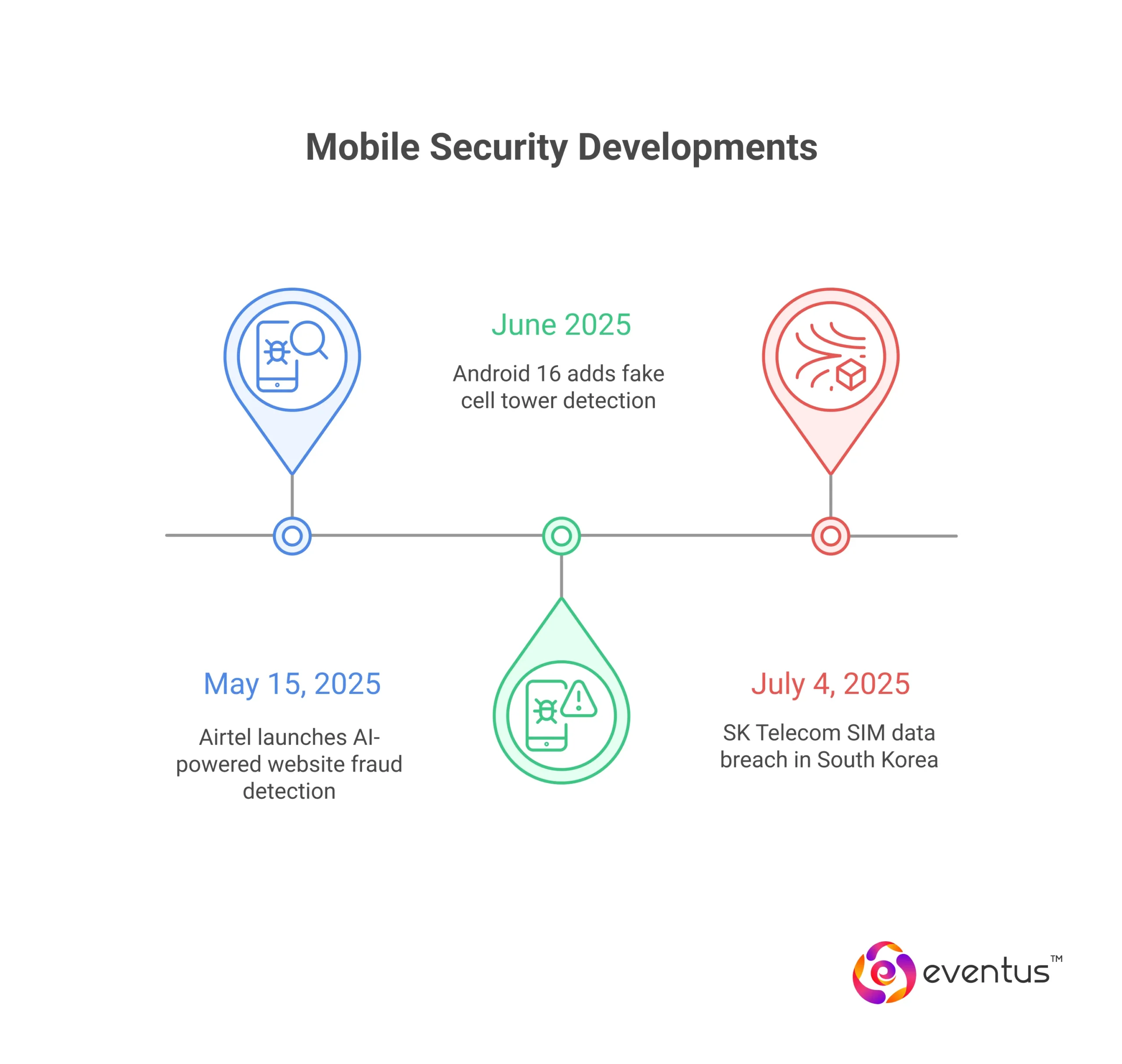
1. Android 16 Adds Fake Cell Tower Detection
In June 2025, Google announced a major security enhancement in Android 16 that will warn users when connecting to fake or suspicious cell towers—commonly known as “stingrays”. These fake towers are used to intercept calls, texts, and device identifiers without user consent. Android 16’s new network security flag will help users detect and avoid such surveillance threats, especially in high-risk locations or during travel.
2. SK Telecom SIM Data Breach (July 2025, South Korea)
In a parallel development, the South Korean government fined SK Telecom on July 4, 2025, after attackers breached their systems and leaked nearly 27 million USIM records. This incident sparked global concern over mobile SIM data security and led to mandatory security upgrades, including enhanced encryption and routine third-party audits.
These cases reinforce a critical truth: modern mobile security must evolve beyond app-level protection to include network behavior monitoring, SIM-level encryption, and proactive threat detection. Enterprises should monitor OS-level developments, carrier-level risks, and supply-chain vulnerabilities as part of their mobile defense strategy.
3. Airtel Launch es AI‑Powered Website Fraud Detection
On May 15, 2025, Airtel (a leading Indian telecom operator) rolled out a real-time, AI-driven fraud detection system for both mobile and broadband users. This network-based solution blocks malicious websites on the fly, marking a first-of-its-kind initiative for large-scale telecom security
How Does Mobile Security Work in a Business Environment?
Mobile security in business environments relies on a layered approach, integrating tools like Mobile Device Management (MDM), Unified Endpoint Management (UEM), and Mobile Threat Defense (MTD). These platforms enforce security policies, monitor endpoints, and detect threats using AI and behavioral analytics.
Mobile Endpoint Detection and Response (EDR) tools collect telemetry, detect threats like ransomware or phishing, and trigger automated responses. MDM and UEM solutions allow remote wipe, app control, and encryption enforcement across mobile devices, ensuring compliance and visibility.
Cloud-native platforms add scalability with real-time analytics and zero-trust enforcement, while device manufacturers strengthen protection with biometric access, secure boot, and hardware encryption.
Many enterprises also work with cybersecurity providers to implement tailored mobile protection and compliance strategies.