Top 10 MSSP services strengthen enterprise cybersecurity through 24/7 security monitoring, SIEM integration, threat intelligence, vulnerability management, firewall and endpoint protection, cloud security monitoring, device management, compliance support, and user training. It highlights the importance of each service in reducing risk, enhancing detection, ensuring compliance, and supporting incident response. Key themes include proactive threat defense, secure infrastructure management, regulatory readiness, and employee awareness - all essential for maintaining a resilient and compliant security posture in today’s evolving threat landscape. Top ten mssp services are listed below:
Table of Contents
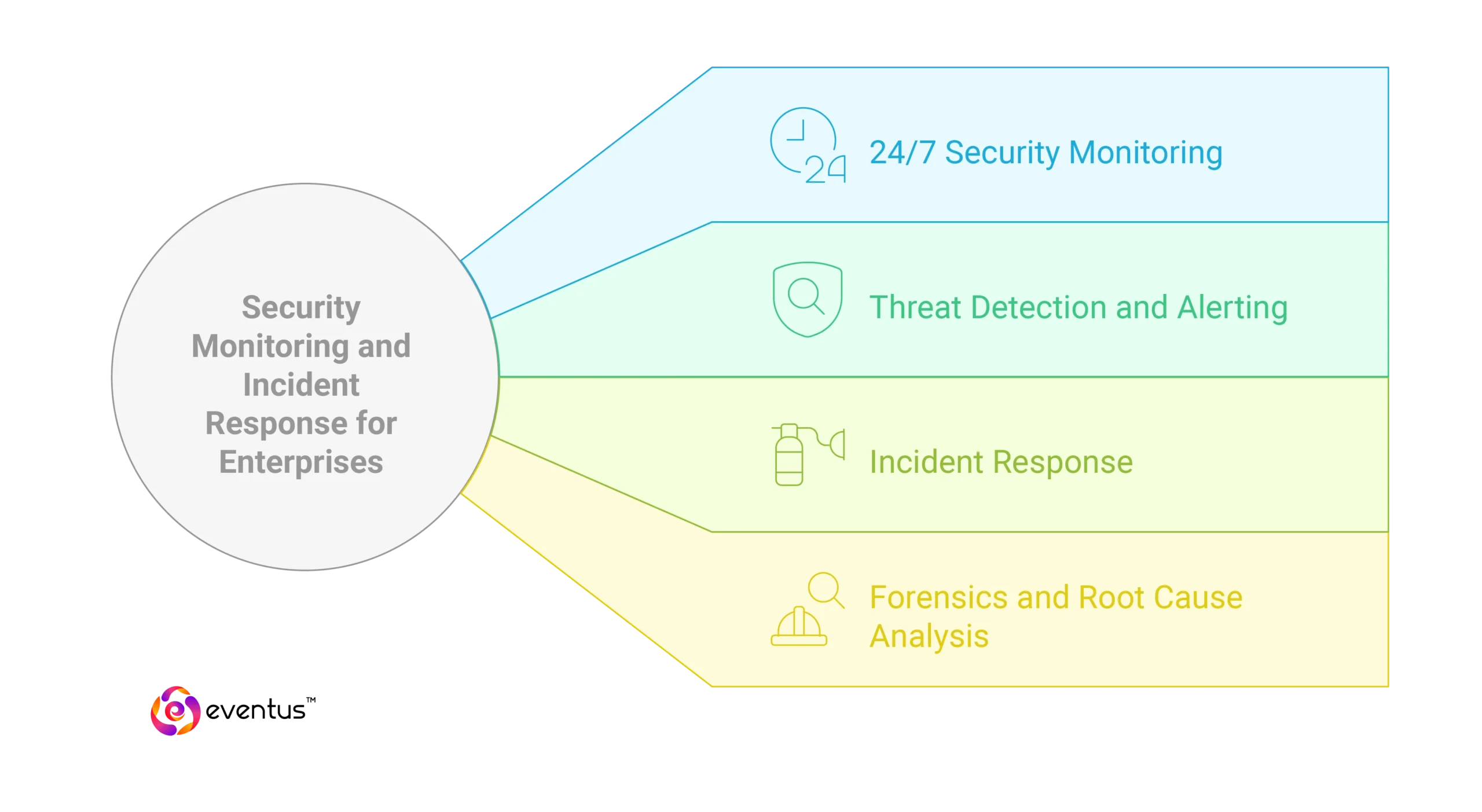
1. Security Monitoring and Incident Response for Enterprises
As cyber threats grow in scale and sophistication, Security Monitoring and Incident Response has become a mission-critical function for businesses. For organizations, this capability ensures operational continuity, regulatory compliance, and reputational resilience in the face of increasing attack vectors. Managed Security Service Providers (MSSPs) deliver these services as part of a holistic security strategy.
24/7 Security Monitoring
Security monitoring refers to the continuous, real-time surveillance of your IT infrastructure—including network traffic, endpoints, cloud platforms, and on-premise servers—to identify suspicious activity, policy violations, or system misconfigurations.
- Network Monitoring: Tracks ingress and egress traffic for anomalies or known malicious patterns.
- Endpoint Monitoring: Uses EDR (Endpoint Detection and Response) tools to detect fileless malware, lateral movement, and insider threats.
- Cloud Monitoring: Watches cloud-native environments (AWS, Azure, Google Cloud) for unauthorized access and API abuse.
Threat Detection and Alerting
This involves correlating logs, telemetry, and behavioral signals using SIEM platforms, AI-driven analytics, and threat intelligence feeds to detect potential compromises. MSSPs typically use tools like Splunk, QRadar, or Microsoft Sentinel to:
- Detect zero-day exploits and advanced persistent threats (APTs)
- Identify misconfigured firewalls, access controls, or software
- Trigger alerts with confidence scoring and risk context
Incident Response
Once a threat is confirmed, Incident Response (IR) procedures kick in to contain and neutralize the threat. This may include:
- Isolating infected systems or accounts
- Blocking IPs and closing ports
- Revoking credentials or enforcing MFA
- Deploying reverse engineering or malware sandboxing if needed
Forensics and Root Cause Analysis
Post-incident, forensic investigation uncovers how the breach occurred, what assets were affected, and which vulnerabilities were exploited. Deliverables often include:
- Timeline of the incident
- Identity of the threat actor (if possible)
- Entry points and compromised systems
- Recommendations for remediation and prevention
Why Is Security Monitoring and Incident Response Essential for Businesses?
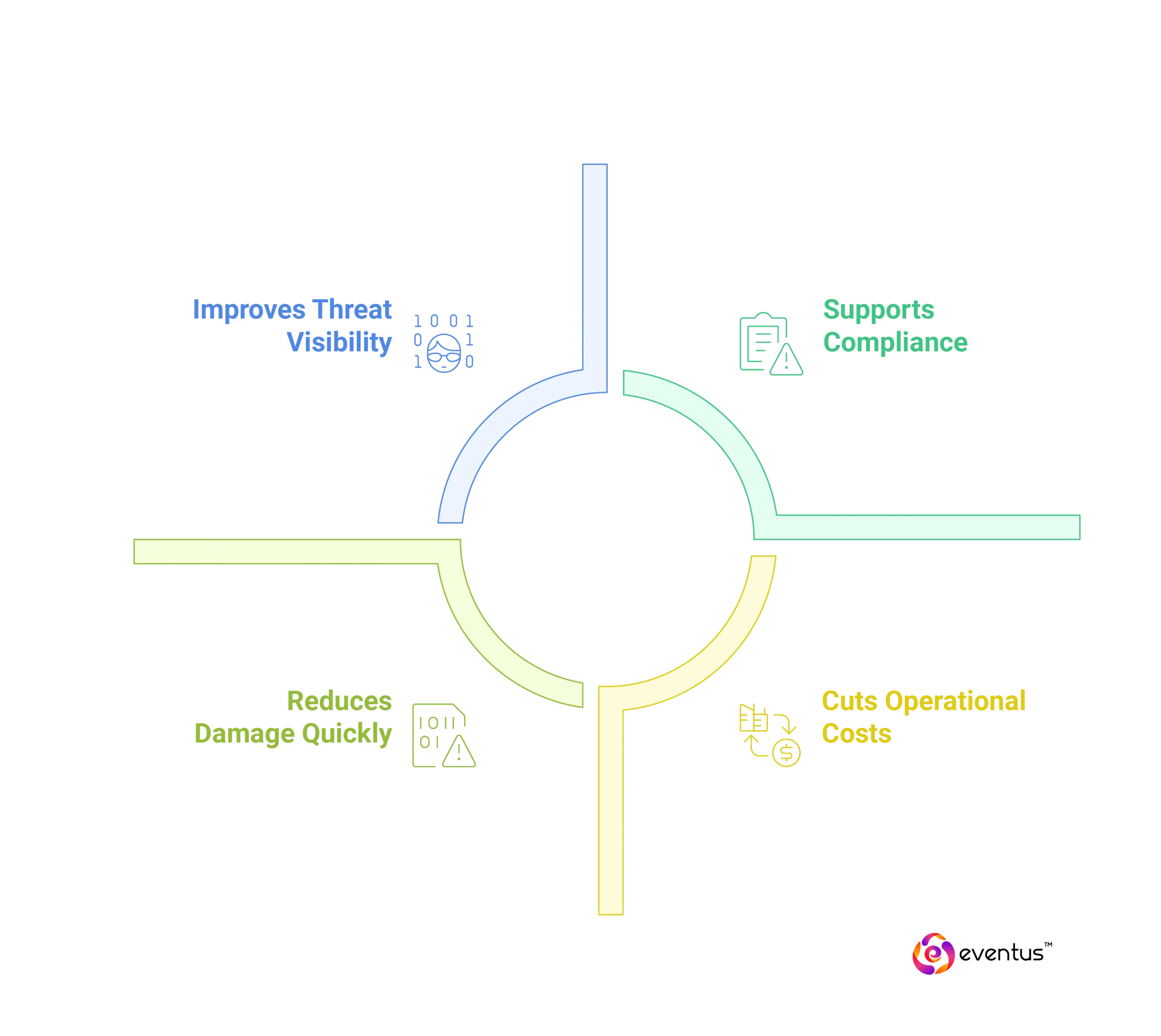
- Reduces Damage Quickly: Breach containment takes months without monitoring. MSSPs cut this time, minimizing financial and reputational loss.
- Supports Compliance: Meets mandatory standards like GDPR, HIPAA, and PCI-DSS by providing audit-ready logs and response protocols.
- Improves Threat Visibility: Offers real-time insights for faster, informed decisions—especially across hybrid and cloud environments.
- Cuts Operational Costs: Avoids the high cost of building an in-house SOC by leveraging MSSP expertise and 24/7 coverage.
How Do MSSPs Deliver Security Monitoring and Incident Response?
- Deploy Security Tools: MSSPs manage SIEM (log correlation), SOAR (automated responses), and EDR/XDR (endpoint analytics) for full threat coverage.
- Enable Expert Oversight: Analysts validate alerts, reduce false positives, and ensure fast response to real threats.
- Use Threat Intelligence: Integrates real-time feeds—zero-day data, dark web scans, and MITRE ATT&CK—for smarter detection.
- Provide Root Cause Reports: Delivers post-incident analysis with timelines, impacted assets, control gaps, and fix recommendations.
- Offer SLA-Based Guarantees: Ensures rapid response times with measurable performance commitments.
2. Security Information and Event Management (SIEM)
Security Information and Event Management (SIEM) is a core component of any modern cybersecurity strategy, especially in enterprise and regulated environments. SIEM consolidates security data, analyzes events, and triggers alerts to help detect threats early and support compliance mandates.
Why Is SIEM Important for Businesses?
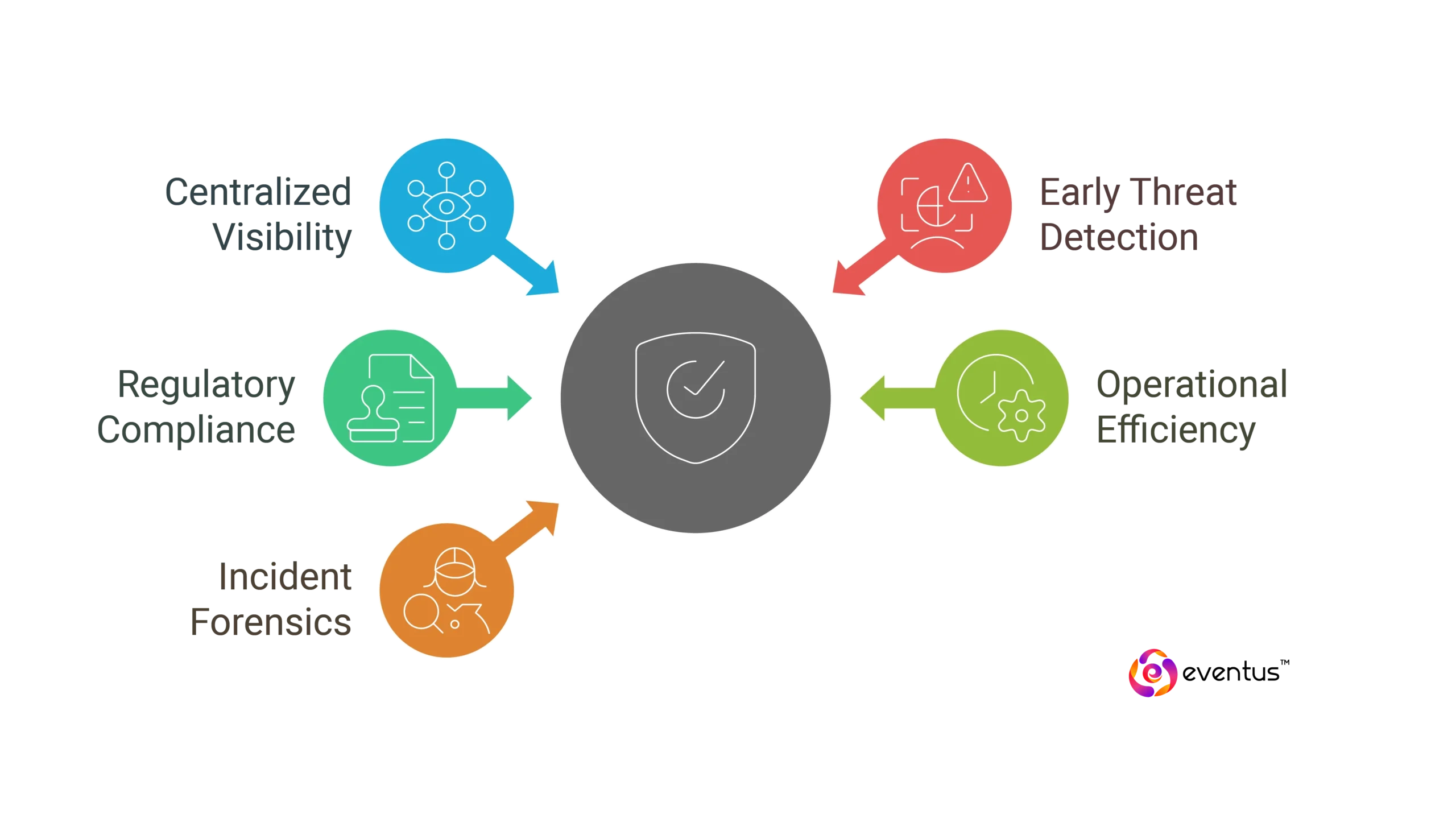
- Centralized Visibility: Provides a unified view of security across on-prem, cloud, and hybrid systems.
- Early Threat Detection: Correlates events to quickly spot insider threats, credential misuse, and anomalies.
- Regulatory Compliance: Automates log retention and reporting for GDPR, HIPAA, PCI-DSS, and other standards.
- Operational Efficiency: Reduces alert fatigue by filtering noise and prioritizing real threats.
- Incident Forensics: Supports breach investigations with detailed logs and attack timelines.
How Do MSSPs Deliver SIEM as a Managed Service?
- Tool Setup: Deploy and configure platforms like Splunk, QRadar, or Sentinel based on business and compliance needs.
- Log Integration: Connects sources like AD, firewalls, SaaS apps, and cloud platforms for complete data coverage.
- Custom Rules: Builds correlation rules using threat intel, MITRE ATT&CK, and behavior analytics.
- Alert Handling: Monitors alerts, filters false positives, and automates response via SOAR when needed.
- Reporting: Provides compliance reports, CISO dashboards, and performance metrics like MTTD/MTTR.
- Ongoing Optimization: Continuously tunes detection logic and parsers as threats and environments evolve.
3. Threat Intelligence for Enterprise Cybersecurity
Threat Intelligence is the process of collecting, analyzing, and applying data about potential or existing cyber threats. It transforms external threat feeds, behavioral indicators, and attacker tactics into contextual knowledge, empowering security teams to make faster, more informed decisions.
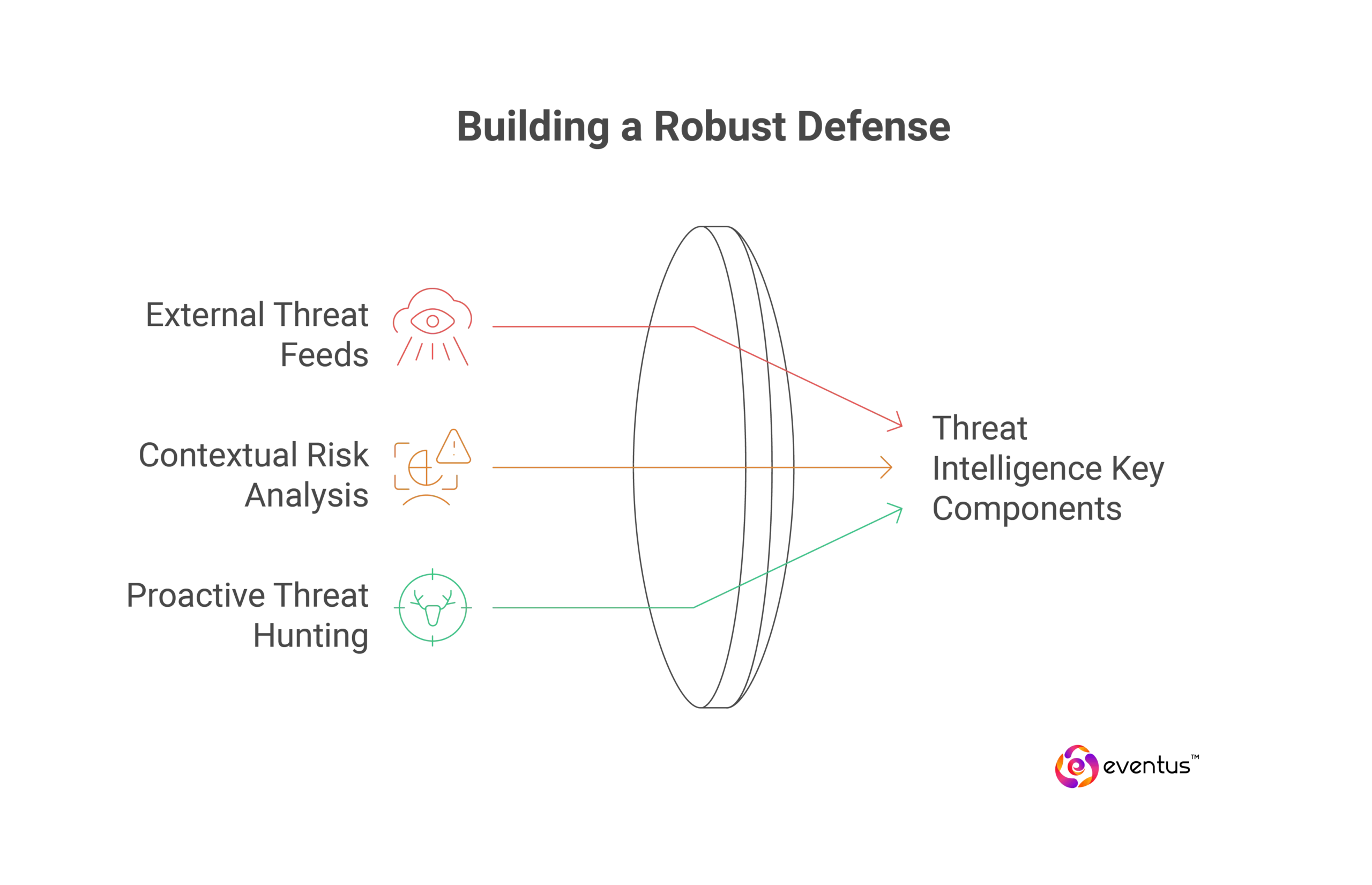
Key Components:
External Threat Feeds
Real-time data from global sources such as:
- Open-source intelligence (OSINT)
- Commercial threat intel vendors (e.g., Recorded Future, Mandiant)
- Government and ISAC feeds (e.g., US-CERT, FS-ISAC): These feeds provide Indicators of Compromise (IoCs), malware signatures, exploit patterns, domain/IP blacklists, and zero-day alerts.
Contextual Risk Analysis
Raw data alone is insufficient. Threat intelligence platforms (TIPs) enrich this data by:
- Mapping threats to organizational assets
- Identifying which systems are at risk
- Providing priority scores based on relevance and exploitability
Proactive Threat Hunting
Combines human expertise and AI-based analysis to uncover threats not detected by automated systems. Threat hunters look for:
- Lateral movement
- Living off the land (LotL) techniques
- Emerging attack vectors that bypass conventional defenses
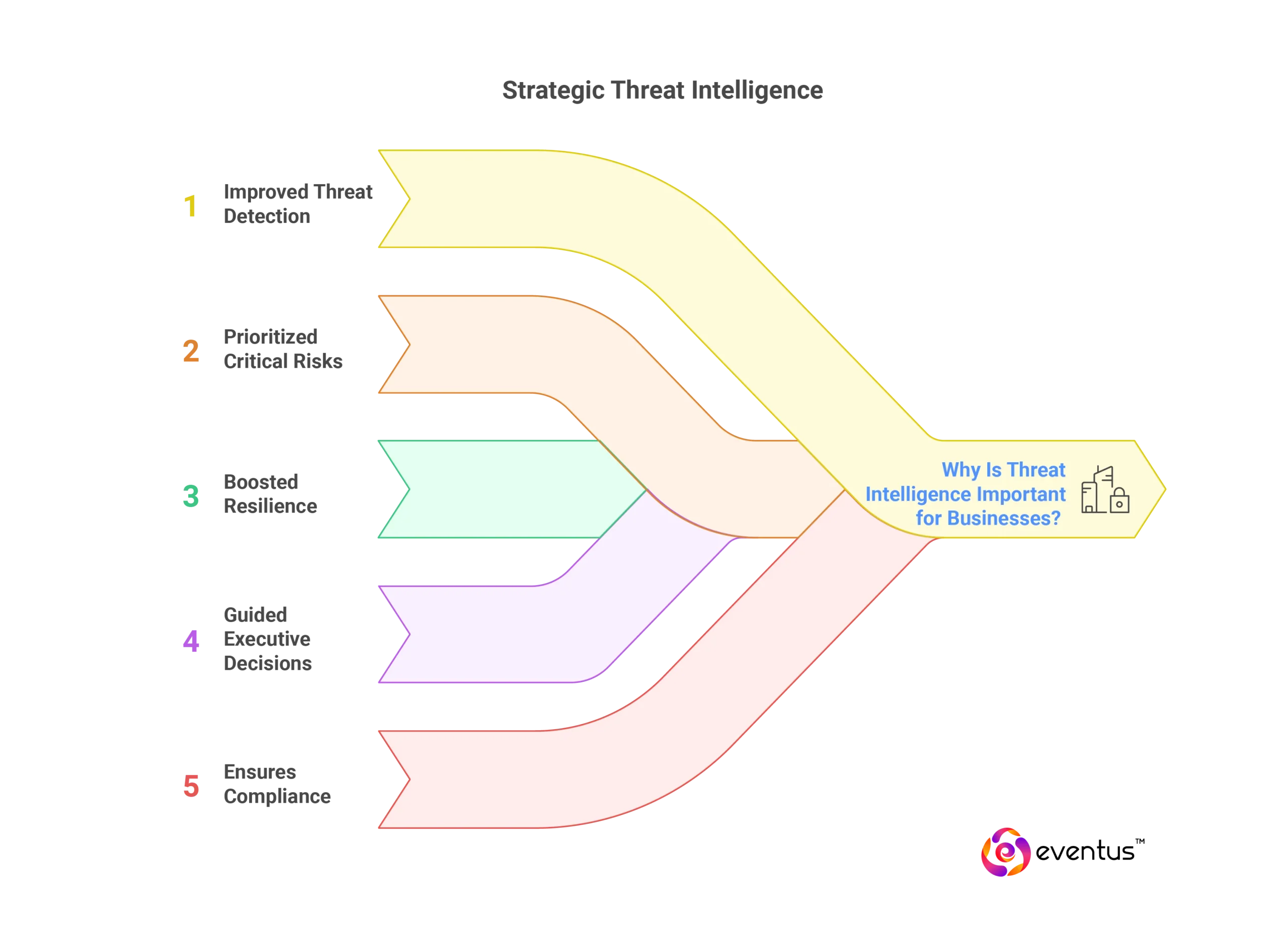
Why Is Threat Intelligence Important for Businesses?
- Improves Threat Detection: Speeds up identification of phishing, ransomware, and supply chain attacks via SIEM, SOAR, and EDR.
- Prioritizes Critical Risks: Enables faster triage, targeted patching, and alert noise reduction.
- Boosts Resilience: Shifts security from reactive to proactive by forecasting attacker tactics and refining defenses.
- Guides Executive Decisions: Helps CISOs align security spend with business risks and communicate priorities to leadership.
- Ensures Compliance: Supports audit readiness and regulatory mandates with real-time threat reporting and documentation.
How Do MSSPs Deliver Threat Intelligence Services?
- Use TIPs for Contextual Data: Leverage platforms like Anomali or ThreatConnect to deliver enriched, industry-specific threat feeds mapped to client assets.
- Integrate with Security Tools: Embed threat intel into SIEM, SOAR, and IDS/IPS for automated detection and response.
- Employ Threat Analysts: Experts analyze attacker behavior, reverse malware, and monitor dark web activity.
- Provide Actionable Reports: Deliver regular briefings with threat trends, industry risks, and recommended defenses.
4. Vulnerability Management
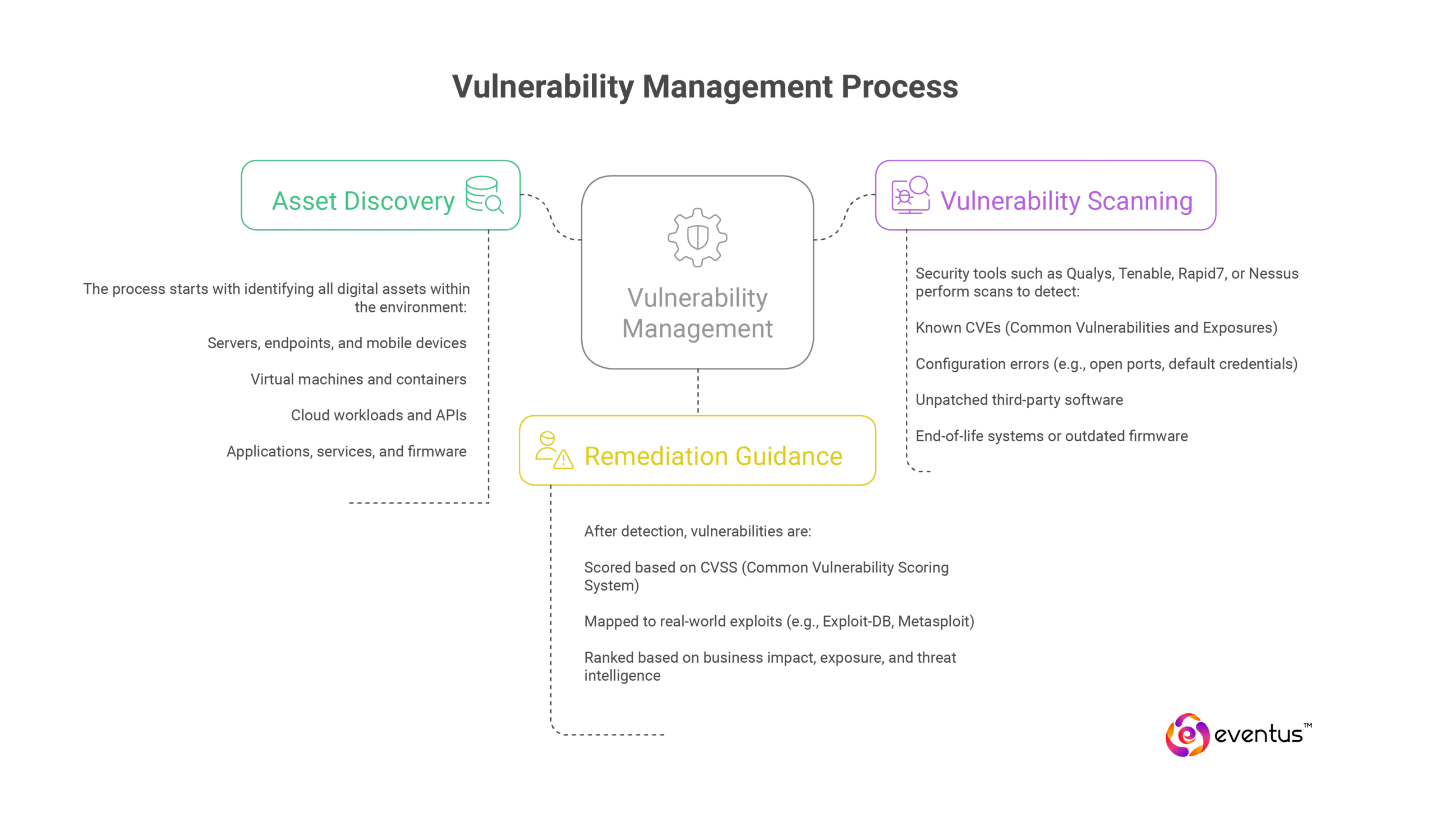
Vulnerability Management (VM) is a continuous, structured process that involves identifying, evaluating, treating, and reporting security weaknesses across an organization's infrastructure. It helps security teams prioritize and remediate flaws before attackers can exploit them.
Asset Discovery
The process starts with identifying all digital assets within the environment:
- Servers, endpoints, and mobile devices
- Virtual machines and containers
- Cloud workloads and APIs
- Applications, services, and firmware
Vulnerability Scanning
Security tools such as Qualys, Tenable, Rapid7, or Nessus perform scans to detect:
- Known CVEs (Common Vulnerabilities and Exposures)
- Configuration errors (e.g., open ports, default credentials)
- Unpatched third-party software
- End-of-life systems or outdated firmware
Remediation Guidance
After detection, vulnerabilities are:
- Scored based on CVSS (Common Vulnerability Scoring System)
- Mapped to real-world exploits (e.g., Exploit-DB, Metasploit)
- Ranked based on business impact, exposure, and threat intelligence
Why Is Vulnerability Management Important for Businesses?
- Blocks Known Exploits: Closes security gaps attackers commonly use by patching known vulnerabilities on time.
- Shrinks Attack Surface: Limits entry points by continuously identifying and fixing weaknesses.
- Strengthens Security Posture: Eliminates weak spots across on-prem, cloud, and hybrid environments.
- Enables Smarter Risk Decisions: Helps prioritize patches based on exploitability and asset value.
- Meets Compliance Standards: Supports audits for PCI-DSS, HIPAA, ISO 27001, NIST, SOX, and FISMA.
How Do MSSPs Deliver Vulnerability Management Services?
- Asset Discovery: Use tools like NMAP or Qualys to continuously map all on-prem, cloud, and shadow assets.
- Automated Scanning: Run credentialed scans across systems, cloud, containers, and apps with minimal false positives.
- Prioritized Remediation: Rank vulnerabilities using threat intel, exploit data, and asset value; provide fix plans and mitigation steps.
- Ongoing Monitoring: Track trends, unpatched issues, and SLA performance; deliver compliance-ready reports and dashboards.
- Ops Integration: Feed VM data into SIEM, SOAR, and ITSM for full visibility and automated containment workflows.
5. Firewall and Network Security Management
Firewall and Network Security Management refers to the deployment, configuration, monitoring, and optimization of network security controls to prevent unauthorized access, detect malicious activity, and maintain secure communications across digital infrastructure.
Core components include:
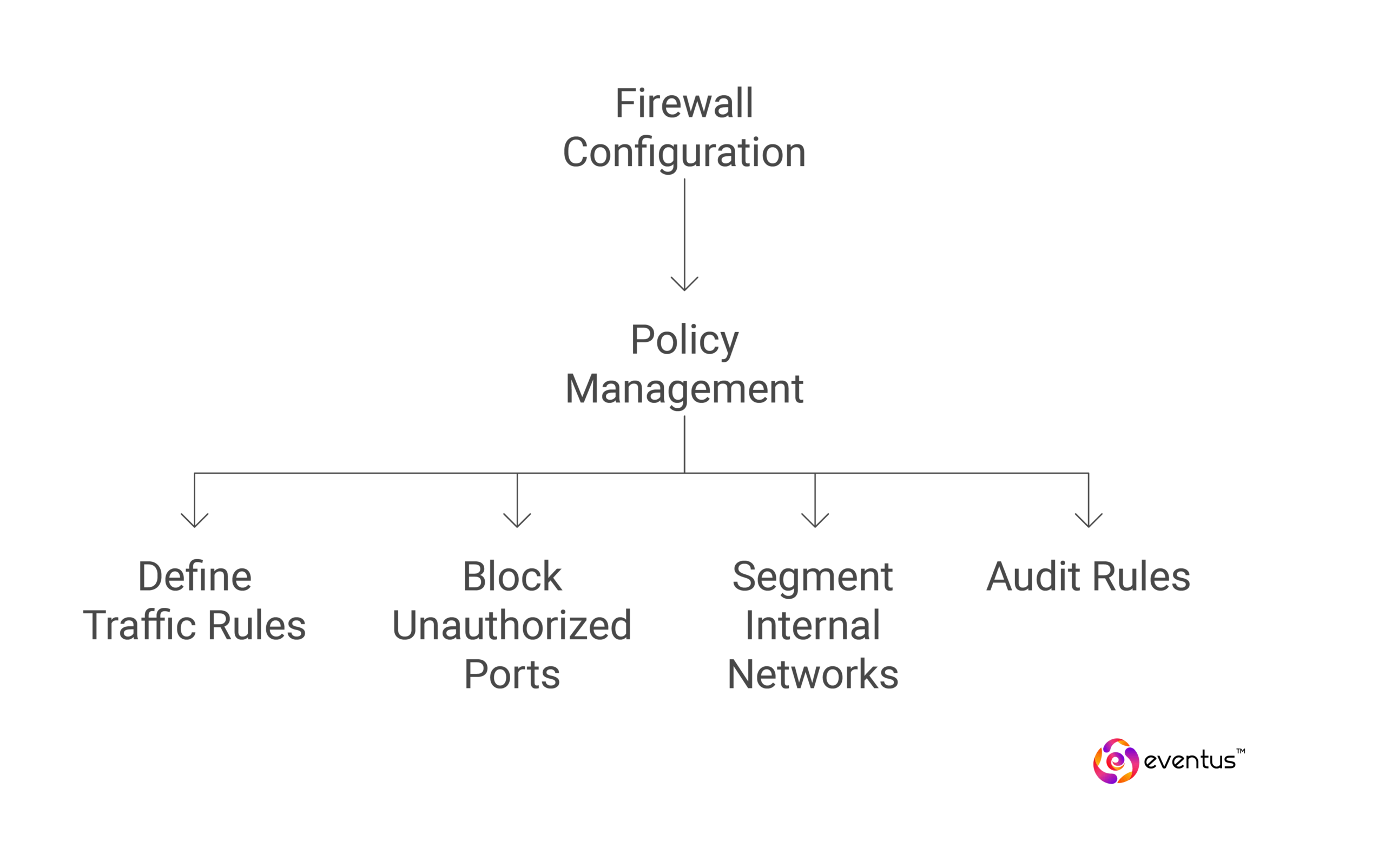
Firewall Configuration & Policy Management
Firewalls enforce access control between trusted and untrusted networks. Policy management involves:
- Defining inbound/outbound traffic rules
- Blocking unauthorized ports and protocols
- Segmenting internal networks by role or trust level
- Regularly auditing rules to eliminate redundancy or misconfigurations
MSSPs help configure both Next-Generation Firewalls (NGFWs) and Unified Threat Management (UTM) devices to balance security, compliance, and performance.
Intrusion Detection and Prevention Systems (IDS/IPS)
IDS/IPS technologies monitor network traffic for suspicious patterns:
- IDS: Detects and alerts on malicious activity without taking action.
- IPS: Detects and blocks in real-time, enforcing predefined rules.
These systems use signature-based, anomaly-based, and behavioral detection techniques to prevent data exfiltration, malware infiltration, and lateral movement.
Web and Email Security
Web and email gateways are frequent entry points for cyberattacks, including:
- Phishing
- Ransomware
- Business Email Compromise (BEC)
Security controls include: - Anti-phishing engines
- Spam filters
- URL filtering
- Attachment sandboxing and malware scanning
6. Endpoint Detection and Response (EDR) and Managed Detection and Response (MDR)
EDR is a cybersecurity solution focused on detecting, investigating, and responding to threats at the endpoint level (laptops, desktops, servers). Unlike legacy antivirus, EDR provides real-time visibility, forensic context, and automated remediation capabilities.
Key Capabilities:
- Behavioral Analytics: Uses machine learning to detect anomalies like credential misuse, lateral movement, and fileless attacks.
- Threat Containment: Automatically isolates compromised devices from the network to prevent lateral spread.
- Forensics and Root Cause Analysis: Logs every process, connection, and behavior on the endpoint for detailed investigation.
Managed Detection and Response (MDR)
MDR is a fully managed service that combines EDR technology with 24/7 monitoring, threat hunting, incident response, and expert support.
Key MDR Features:
- Continuous monitoring of EDR telemetry by cybersecurity professionals
- Proactive threat hunting to detect stealthy or novel attacks
- Expert-guided incident response with remediation recommendations
- Integration with SIEM, SOAR, and threat intelligence platforms
Popular EDR/MDR vendors include CrowdStrike Falcon, SentinelOne, Microsoft Defender for Endpoint, Sophos Intercept X, and Arctic Wolf.
Why Are EDR and MDR Important for Businesses?
- Secures Remote Endpoints: Protects devices outside the corporate network with always-on, agent-based security.
- Detects Advanced Threats: Identifies fileless malware, zero-days, and stealthy attacker tactics using behavioral analytics.
- Enables Rapid Response: MDR teams contain threats quickly to limit spread and damage.
- Cuts Internal Burden: Delivers SOC-as-a-Service, reducing the need for in-house security staff.
- Ensures Compliance: Supports PCI-DSS, HIPAA, NIST, and ISO with endpoint visibility and incident logs.
How Do MSSPs Deliver EDR/MDR Services?
- Agent Deployment: Install lightweight agents on all endpoints to capture activity logs and network behavior.
- Threat Detection: Use AI, MITRE mapping, and rules to identify suspicious behavior and potential compromises.
- Threat Containment: Automatically or manually isolate devices, stop malicious processes, and quarantine files.
- 24/7 Monitoring & Hunting: MDR teams continuously monitor, hunt threats, and investigate attacker movement.
- Incident Reports & Guidance: Provide root cause analysis, response steps, and executive-ready summaries, often integrated with SOAR and ITSM systems.
7. Cloud Security Monitoring
Cloud Security Monitoring is the continuous process of observing and analyzing cloud infrastructure, workloads, APIs, identities, and data flows to detect misconfigurations, anomalies, unauthorized access, and threats in real time.
Core components include:
SaaS, IaaS, and PaaS Coverage
Monitoring is not limited to infrastructure—it extends to application and platform layers:
- IaaS (Infrastructure-as-a-Service): AWS, Azure, Google Cloud
- PaaS (Platform-as-a-Service): Azure App Service, Google App Engine
- SaaS (Software-as-a-Service): Microsoft 365, Salesforce, Google Workspace. Coverage ensures visibility across compute, storage, identity, and services, whether containerized, serverless, or VM-based.
Cloud Posture Management
Also known as Cloud Security Posture Management (CSPM), this involves:
- Continuous evaluation of configurations
- Detection of policy violations (e.g., public S3 buckets, open ports)
- Identification of drift from compliance baselines (e.g., CIS Benchmarks, NIST CSF). CSPM tools like Prisma Cloud, AWS Security Hub, and Microsoft Defender for Cloud help detect and correct risks before exploitation.
API & Data Access Monitoring
Modern cloud environments are API-driven. Monitoring focuses on:
- Tracking API calls to detect misuse or abnormal patterns
- Validating access permissions for users, applications, and services
- Inspecting data transfer logs to identify unauthorized downloads or exfiltration attempts. This ensures principle of least privilege (PoLP) and zero trust enforcement at the cloud level.
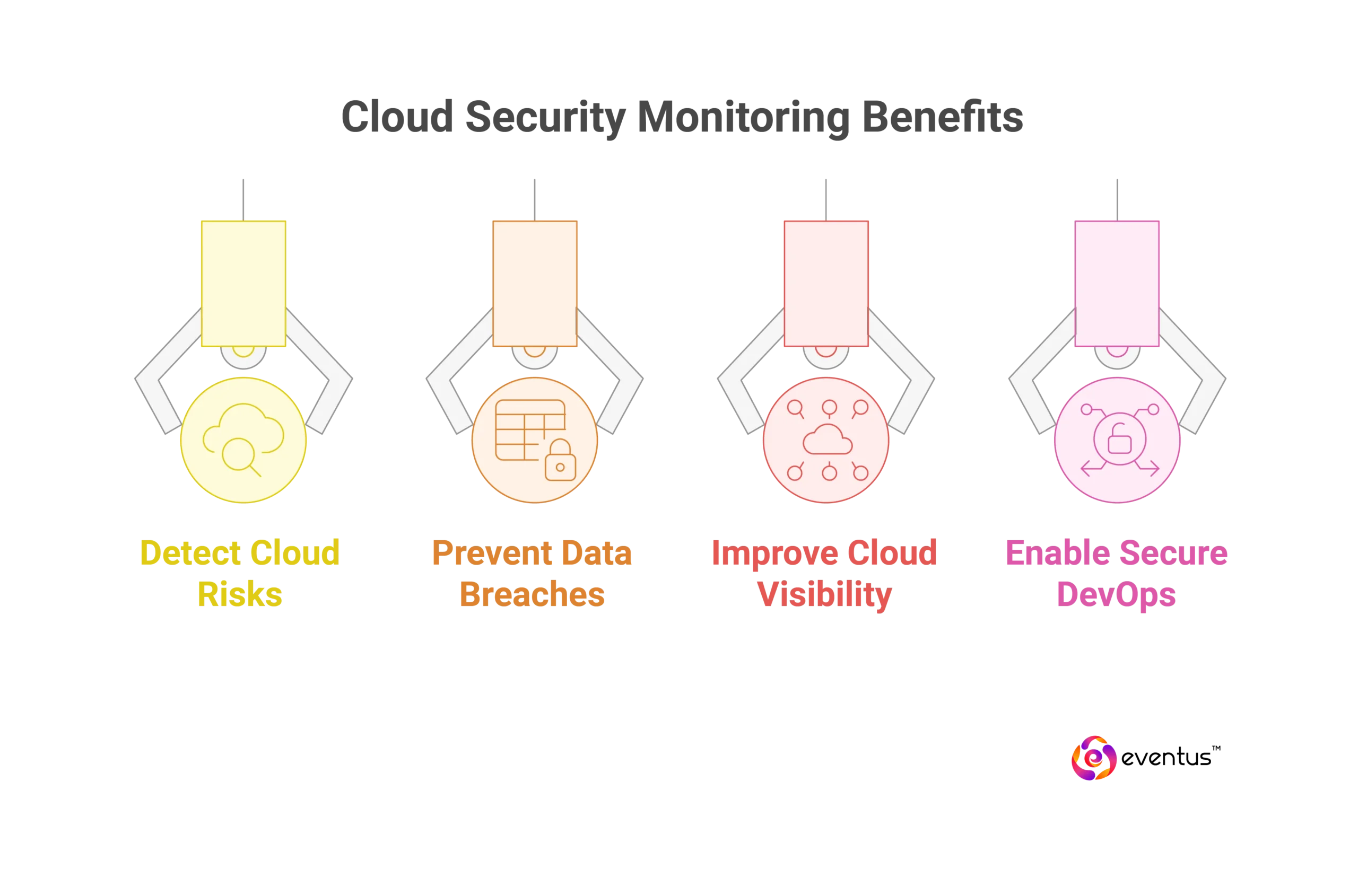
Why Is Cloud Security Monitoring Important for Businesses?
- Detects Cloud-Specific Risks: Identifies IAM misconfigurations, exposed services, and shared responsibility gaps before they're exploited.
- Prevents Data Breaches: Flags unauthorized API calls and abnormal data transfers to stop exfiltration.
- Ensures Compliance: Delivers audit trails, alerts, and documentation for HIPAA, GDPR, ISO 27017, and SOC 2.
- Improves Multi-Cloud Visibility: Consolidates monitoring across AWS, Azure, and GCP to eliminate blind spots.
- Enables Secure DevOps: Integrates with CI/CD to enforce IaC security and prevent misconfigurations pre-deployment.
How Do MSSPs Deliver Cloud Security Monitoring Services?
- Platform Integration: Connect with AWS, Azure, GCP, and tools like Datadog or Lacework to ingest logs, events, and API data.
- Posture & Policy Enforcement: Use CSPM tools to detect misconfigurations, benchmark against CIS/NIST, and generate compliance reports.
- Access Monitoring: Track IAM roles, login anomalies, and API token use; enforce least-privilege and detect privilege abuse.
- API Security: Monitor API behavior, block excessive/shadow calls, and manage token access controls.
- 24/7 Threat Detection: Detect insider threats and automation abuse; escalate via SIEM/SOAR for quick response.
- Executive Reporting: Deliver alerts, risk dashboards, and compliance summaries to guide security decisions.
8. Security Device Management
Security Device Management involves the centralized administration, configuration, maintenance, and performance monitoring of network and security appliances—both physical and virtual. These devices form the backbone of perimeter and internal security architectures.
Key components include:
UTM, NGFW, and WAF Configuration
- Unified Threat Management (UTM): Combines firewall, antivirus, content filtering, and intrusion detection in one device.
- Next-Generation Firewall (NGFW): Offers deep packet inspection, application awareness, and integration with threat intelligence feeds.
- Web Application Firewall (WAF): Protects web applications by filtering and monitoring HTTP traffic for SQL injection, XSS, and more.
MSSPs handle:
- Rule configuration and policy management
- SSL inspection and decryption
- Application and user-based controls
- Real-time signature and ruleset updates
Patch Management
Applies to security devices’:
- Firmware, operating systems, and security modules
- Updates for bug fixes, new features, or critical vulnerabilities
Without consistent patching, devices can become entry points for attackers—especially if exposed to the internet.
Health Checks and Optimization
- CPU/memory monitoring
- Throughput and latency checks
- Log analysis
- Rulebase tuning: Regular assessments prevent performance bottlenecks, hardware failures, and policy misconfigurations that can degrade protection or disrupt business operations.
Why Is Security Device Management Important for Businesses?
- Secures the Network Perimeter: Prevents gaps from misconfigurations or outdated firewall rules.
- Closes Known Vulnerabilities: Regular patching stops attackers from exploiting unpatched firmware or OS flaws.
- Meets Compliance Standards: Supports PCI-DSS, ISO 27001, and NIST with updates, config control, and audit logs.
- Prevents Downtime: Ensures devices run optimally, avoiding network slowdowns or outages.
- Enforces Zero Trust Policies: Applies strict access controls and segmentation to limit lateral movement.
How Do MSSPs Deliver Security Device Management Services?
- Device Onboarding & Policy Setup: Configure firewalls and WAFs (e.g., Fortinet, Palo Alto, AWS) with policies tailored to business needs.
- Scheduled Patching: Apply firmware and OS updates based on CVEs and vendor advisories, minimizing downtime.
- Continuous Monitoring: Track device health, performance, and availability for early issue detection.
- Optimization & Tuning: Refine rules, reduce false positives, and adjust settings for better performance and protection.
- Backup & Rollback: Maintain regular backups and enable fast recovery from failed updates or outages.
- Reporting & Compliance: Deliver dashboards, patch reports, and audit logs to support governance and security tracking.
9. Compliance and Risk Management
Compliance and Risk Management refers to the processes, tools, and frameworks that help organizations adhere to relevant laws and regulations while identifying, assessing, and mitigating security risks that could impact business operations.
Key Components:
Audit Preparation
MSSPs and internal compliance teams help organizations prepare for:
- Regulatory audits (e.g., HIPAA, PCI-DSS, GDPR, ISO/IEC 27001, SOX)
- Third-party assessments and vendor risk reviews
- Internal audits and board-level security evaluations
This involves gathering documentation, verifying technical controls, and producing compliance evidence such as logs, policies, and incident records.
Policy & Governance Support
Establishes and maintains:
- Security policies (access control, data handling, encryption, etc.)
- Governance frameworks (e.g., NIST Cybersecurity Framework, COBIT)
- Role-based access and escalation procedures
Policies are aligned with both business needs and industry standards, ensuring enforceability and audit readiness across NOC and SOC operations for consistent security and compliance management.
Risk Assessments
A comprehensive risk assessment evaluates:
- IT assets and data sensitivity
- Threat likelihood and potential impact
- Current security controls and gaps
- Business continuity dependencies
This results in a risk register, prioritized mitigation plan, and risk acceptance documentation, all aligned to support strategic security investment and readiness for SOC audit requirements.
Why Is Compliance and Risk Management Important for Businesses?
- Prevents Regulatory Fines: Ensures alignment with laws like GDPR, HIPAA, and PCI-DSS to avoid penalties.
- Builds Trust: Demonstrates credibility to customers and partners through certifications like ISO 27001 or SOC 2.
- Strengthens Business Continuity: Identifies and mitigates risks that could disrupt operations or lead to data loss.
- Supports Strategic Decisions: Helps leaders prioritize security investments based on risk exposure.
- Improves Insurance Standing: Lowers premiums and liability by meeting insurer compliance requirements.
How Do MSSPs Deliver Compliance and Risk Management Services?
- Gap Analysis: Compare existing controls with standards like NIST, PCI-DSS, HIPAA, and GDPR; identify gaps and plan fixes.
- Policy Management: Create and update key policies (AUP, IRP, data retention) for consistent governance and enforcement.
- Risk Assessment: Perform asset classification, threat modeling, and impact analysis to prioritize mitigation.
- Control Implementation: Deploy controls like MFA, DLP, encryption, and logging to meet compliance and security needs.
- Audit Support: Organize documentation, conduct mock audits, and assist with regulatory reviews.
- Reporting: Provide dashboards, risk heatmaps, and policy effectiveness reports for CISO and board visibility.
10. Security Awareness and Training
Security Awareness and Training refers to the systematic education of employees, contractors, and third-party users about cybersecurity threats, safe digital behavior, organizational policies, and regulatory obligations. It equips users to recognize and respond to threats, reducing the risk of social engineering, phishing, and data breaches.
Core components include:
Phishing Simulations
Simulated phishing campaigns test how employees respond to:
- Malicious links
- Credential harvesting attempts
- Business Email Compromise (BEC) lures
These campaigns raise awareness and improve user vigilance in real-world scenarios.
Custom Security Training Modules
Tailored content is created based on:
- Employee roles (e.g., finance, IT, HR, executives)
- Industry-specific threats (e.g., healthcare vs fintech)
- Risk exposure levels (e.g., high-privilege users, remote workers)
Modules cover topics like:
- Password hygiene and MFA
- Data handling and classification
- Secure use of email and cloud tools
- Incident reporting procedures
Reporting Dashboards
Security teams and leadership get visibility into:
- Completion rates
- Simulation failure rates
- Knowledge retention over time
These dashboards help identify high-risk individuals, departments, or trends needing attention.
Why Is Security Awareness and Training Important for Businesses?
- Minimizes Human Error: Addresses the leading cause of breaches by training users to avoid risky behavior.
- Empowers Employees: Turns staff into active defenders—reporting threats and following secure practices.
- Ensures Compliance: Meets mandatory training requirements for HIPAA, PCI-DSS, GDPR, and more.
- Improves Incident Response: Increases early detection and reporting of suspicious activity.
- Promotes Security Culture: Embeds cybersecurity awareness into daily business operations.
How Do MSSPs Deliver Security Awareness and Training Services?
- Custom Curriculum Design: Tailor content to industry risks, past incidents, and compliance needs.
- Phishing Simulations: Run targeted campaigns with realistic lures to test and train users.
- Role-Based Modules: Deliver interactive training via LMS—accessible, multilingual, and SCORM-compliant.
- Analytics & Reporting: Track user risk scores, training progress, and simulation outcomes for audits.
- Ongoing Updates: Refresh content based on threat trends, policy changes, and regulatory shifts.