Patch management is essential for reducing security risks, maintaining system performance, and achieving compliance. This article explores the fundamentals of patch management, its lifecycle, key challenges, best practices, software types (cloud-based, on-premises, automated), and specific strategies for Windows environments. It also helps organizations evaluate and choose the right patch management software while distinguishing it from broader vulnerability management practices.
Table of Contents
What is patch management?
Patch management is the systematic process of identifying, acquiring, testing, and deploying software patches to address security vulnerabilities, fix bugs, and enhance system performance. These patches are critical for maintaining the integrity and security of operating systems and applications. Effective patch management reduces security risks by ensuring that known vulnerabilities are promptly addressed, thereby strengthening an organization's security posture. Utilizing patch management software or tools can automate the patching process, streamline patch deployment, and ensure compliance with security policies. Regularly updating systems through a structured patch management process is essential for protecting against cyber threats and maintaining optimal system functionality.
What is the purpose of patching?
The purpose of patching is to apply security patches and software updates that fix known vulnerabilities, enhance system stability, and improve performance. It helps organizations reduce attack surfaces, support vulnerability management efforts, and maintain compliance. By using a reliable patch management solution or automated patch tools, security teams can streamline the patching lifecycle and protect endpoints effectively, especially during critical events like Microsoft’s Patch Tuesday.
Why is patch management important?
Patch management is important because it safeguards systems from known vulnerabilities, enhances software performance, and ensures business continuity. As cyber threats evolve, unpatched systems become prime targets. Implementing patch management best practices helps organizations reduce security risks, maintain compliance, and improve endpoint management efficiency. A robust patch management system or tool enables security teams to automate patch management, ensuring timely updates across all devices. Whether using a patch manager for Microsoft environments or enterprise-wide deployments, effective patching is critical for protecting digital assets and preserving organizational integrity. Patch management is the process that transforms reactive defense into proactive resilience.
How does patch management work?
Patch management works through a structured, multi-stage process that ensures the timely deployment of security updates across all software and devices, often integrating SOAR tools to automate threat detection and streamline remediation workflows.
The patch management lifecycle typically includes the following steps:
- Assessment: Identify systems requiring updates through patch status checks.
- Prioritization: Evaluate the criticality of each patch based on your risk-based patch management strategy.
- Testing: Validate patches in a controlled environment to avoid disruptions.
- Deployment: Use tools like ManageEngine Patch Manager Plus, SolarWinds Patch Manager, or cloud-based patch management solutions for automated patch deployment.
- Verification: Confirm successful installation and system functionality.
- Documentation: Maintain patch compliance records to support audits and broader vulnerability management.
Comprehensive patch management is a critical component of any vulnerability management program. By implementing proper patch management policies, businesses reduce security risks and downtime, while centralized patch management solutions support unified endpoint management across Windows, Linux, and third-party platforms.
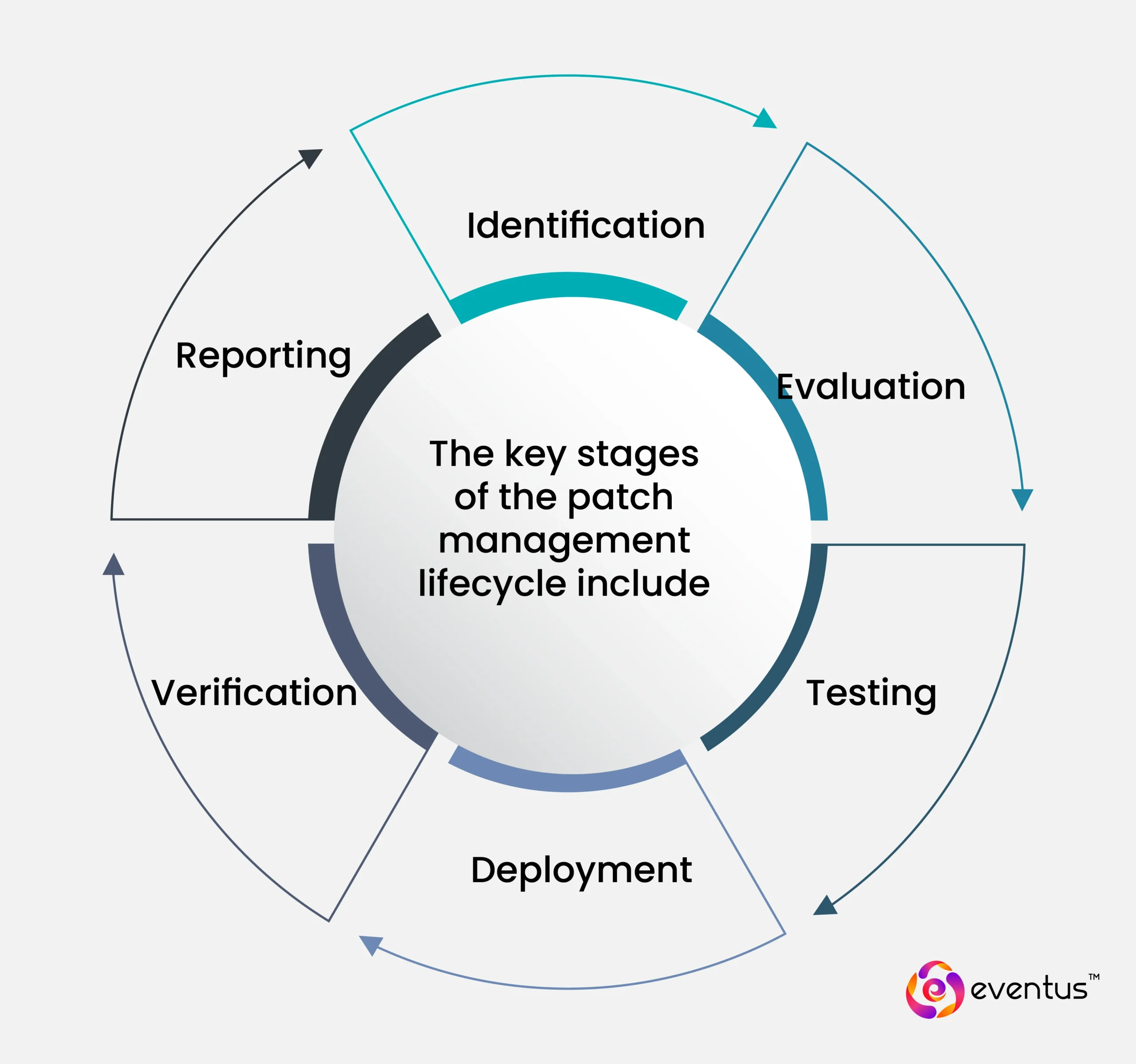
What is the patch management lifecycle?
The patch management lifecycle is a structured sequence of actions that organizations follow to ensure security patches and software updates are effectively applied across all hardware and software assets. It’s a core component of any secure patch management program and supports broader vulnerability management strategies, especially among SOC companies in India that prioritize continuous threat mitigation and compliance.
The key stages of the patch management lifecycle include:
- Identification: Detect missing patches using tools and best practices across Windows, Linux, and third-party applications.
- Evaluation: Assess the relevance and severity of each patch using vulnerability management tools.
- Testing: Validate updates in a sandbox to prevent compatibility issues or downtime.
- Deployment: Use solutions like Windows Server Update Services or an effective patch management solution to automate and streamline patch rollout.
- Verification: Confirm successful installations to maintain patch compliance.
- Reporting: Document patch status and generate compliance reports for audits and review.
Following a formal patch management approach minimizes the time to patch, reduces downtime by streamlining patch deployment, and addresses the ongoing challenges of patch management.
What are the challenges of patch management?
Patch management poses several challenges that can compromise security and operational efficiency if not addressed properly. One major issue is managing diverse environments—organizations often rely on a mix of Windows, Linux, and third-party applications, each requiring different patch management capabilities, particularly when aligning with compliance frameworks like SOC1.
Limited visibility, inconsistent deployment, and lack of automation hinder the entire patch management process.
Here is a complete list of patch management challenges:
- Patch overload – Managing a high volume of security patches across numerous systems.
- Assessing patching requirements – Identifying which patches are relevant to specific environments.
- Compatibility issues – Risk of patches disrupting existing applications or hardware.
- Visibility gaps – Incomplete insight into patch status across endpoints and servers.
- Vulnerability management alignment – Difficulties in integrating patching with broader risk-based vulnerability strategies.
- Automating patching processes – Challenges in deploying automated systems that work across diverse IT infrastructures.
- Coordinating patch deployment – Synchronizing patch rollouts across departments, devices, and time zones.
- Diverse systems and applications – Managing patches for Windows, Linux, macOS, and third-party applications.
- Hybrid or remote employees – Ensuring patch compliance across off-network or mobile endpoints.
- Patch failures – Patches that don’t install properly or introduce new bugs.
- Patch testing – Lack of dedicated environments for validating updates before deployment.
- Resource constraints – Limited bandwidth, storage, or system availability during patching windows.
- Shortages of IT staff – Inadequate personnel to manage the entire patch management process effectively.
- Compliance overhead – Managing audit trails and documentation for regulatory reporting.
- False positives on vulnerabilities – Misidentified threats that lead to unnecessary patching.
- Patch prioritization – Difficulty determining which patches to deploy first based on risk.
- Remote workforce – Ensuring secure, timely patching without access to on-site infrastructure.
- Time-consuming processes – Manual or inefficient workflows increase the time to patch.
- Vulnerability fatigue – Repeated alerts and urgent patches causing burnout and missed priorities.
These challenges underscore the need for adopting an enterprise-grade patch management solution that enables automation, centralization, and actionable insights—a capability increasingly offered by leading cyber security companies to help organizations maintain resilience against evolving threats.
What are the best practices for patch management?
Effective patch management is essential to protect enterprise systems from known vulnerabilities, maintain compliance, and ensure business continuity, often working in tandem with SIEM systems to correlate patch status with threat intelligence and security events.
To optimize results, organizations must follow best practices tailored to their infrastructure and risk profile:
- Establish a formal patch management policy aligned with business objectives and regulatory requirements.
- Classify assets by criticality to prioritize patching based on risk exposure.
- Test patches before deployment to avoid disruptions, especially in production environments.
- Schedule regular patch cycles, including emergency deployments for zero-day vulnerabilities.
- Automate wherever possible using best patch management software that supports Windows, Linux, and third-party patch management.
- Use patch management services or tools that integrate with active management technology for unified visibility.
- Track patch compliance and maintain documentation for audits.
- Incorporate patching as a component of your broader vulnerability management strategy.
- Choose the right patch management software that offers real-time dashboards, reporting, and rollback options.
- Review and improve the approach to patch management regularly to adapt to evolving threats.
Whether you use standalone patch management tools or enterprise-grade platforms, following these practices ensures that patch management is critical, secure, and operationally efficient.
What are the types of patch management software?
Patch management software can be categorized based on deployment model, functionality, and patching capabilities, and is often integrated into the broader security infrastructure by a managed SOC provider to ensure real-time monitoring and timely remediation of vulnerabilities.
Each type supports specific operational needs, whether managing Windows patch management, Linux environments, or ensuring security patch management as part of a broader vulnerability management strategy.
- Cloud-Based Patch Management
Hosted on platforms like AWS or Azure, these solutions offer scalability, easy setup, and remote access.
Examples: NinjaOne, Atera - On-Premises Patch Management
Installed on local servers, ideal for organizations requiring tighter control and deeper integration.
Examples: Microsoft Configuration Manager, ManageEngine Patch Manager Plus - Automated Patch Management
Detects, downloads, and installs patches automatically, reducing manual errors and accelerating the patching lifecycle.
Examples: Automox, ITarian - Centralized Patch Management
Enables unified control and visibility across all endpoints through a single dashboard.
Examples: SolarWinds Patch Manager, Microsoft Configuration Manager - Remote Patch Management
Allows teams to manage devices outside the corporate network—ideal for hybrid and distributed workforces.
Examples: Kaseya VSA, NinjaOne
What is Windows patch management?
Windows patch management is the process of identifying, acquiring, testing, and deploying security updates and software patches specifically for Microsoft Windows environments. It ensures protection against vulnerabilities, system stability, and compliance across endpoints. Tools like Windows Server Update Services (WSUS) or Microsoft Configuration Manager help automate patching, streamline patch deployment, and maintain visibility. Effective Windows patch management is critical for IT teams managing large-scale infrastructure and ensuring operational continuity.
How to choose the right patch management software?
How to choose the right patch management software:
- ✅ Assess Infrastructure Needs: Ensure the software supports your OS mix (Windows, Linux, third-party apps) and scales with your network.
- ✅ Automation Capabilities: Look for solutions with automated patch detection, deployment, and rollback features.
- ✅ Integration with Security Operations: Choose tools that enhance SOC cybersecurity by minimizing exploitable vulnerabilities.
- ✅ Audit Readiness: Ensure the software supports detailed reporting for easier SOCs audit and regulatory compliance.
- ✅ Vendor Reliability: Consider providers known for managed SOC services in India with proven patching and response capabilities.
- ✅ Real-Time Visibility: Opt for centralized dashboards and reporting for complete endpoint oversight.
- ✅ Cost and Licensing: Evaluate pricing models and ensure they match your budget and device volume.
What is the difference between patch management and vulnerability management?
| Aspect | Patch Management | Vulnerability Management |
| Definition | The process of acquiring, testing, and applying software patches or updates | The continuous process of identifying, evaluating, prioritizing, and mitigating threats |
| Primary Goal | Fix known issues and close security gaps by updating software | Reduce overall risk exposure by managing all types of vulnerabilities |
| Scope | Focused on applying software updates | Broader—includes misconfigurations, outdated software, and unpatched systems |
| Process Includes | Patch identification, testing, deployment, and reporting | Scanning, assessment, risk analysis, remediation planning, and verification |
| Tools Used | Patch management tools (e.g., WSUS, ManageEngine Patch Manager Plus) | Vulnerability scanners (e.g., Nessus, Qualys) and risk prioritization tools |
| Relation to SOC Cybersecurity | Tactical execution aligned with SOC recommendations | Strategic process used by SOC teams for proactive defense |
| Integration | Part of the remediation step in vulnerability management | Informs the need for patch management among other security controls |
| Frequency | Typically monthly or as needed (e.g., Patch Tuesday) | Continuous or scheduled scans with dynamic remediation workflows |