This article explores the meaning and importance of cyber resilience, highlighting how it differs from traditional cybersecurity. It examines the core principles of anticipate, withstand, recover, and adapt, alongside real-world examples that show resilience in action. The article also discusses the need for a cyber resilience strategy and governance, the role of established frameworks such as NIST and ISO, and the key components that strengthen resilience. Finally, it addresses the goals of cyber resilience, ways to improve it, and how AI is reshaping organizational resiliency.
Table of Contents
What is Cyber Resilience?
Cyber resilience is the ability of an organization to anticipate, withstand, recover, and adapt in the face of cyber threats while maintaining critical business continuity. Unlike traditional cyber security, which focuses mainly on prevention, cyber resilience integrates defense, recovery, and adaptability into a unified posture.
It combines risk management, best practices, and frameworks to reduce the impact of a cyberattack or data breach. A resilient enterprise does not only try to stop a cyber threat but also ensures operations continue with minimal disruption even if defenses are bypassed.
What are the core principles of anticipate, withstand, recover, and adapt?
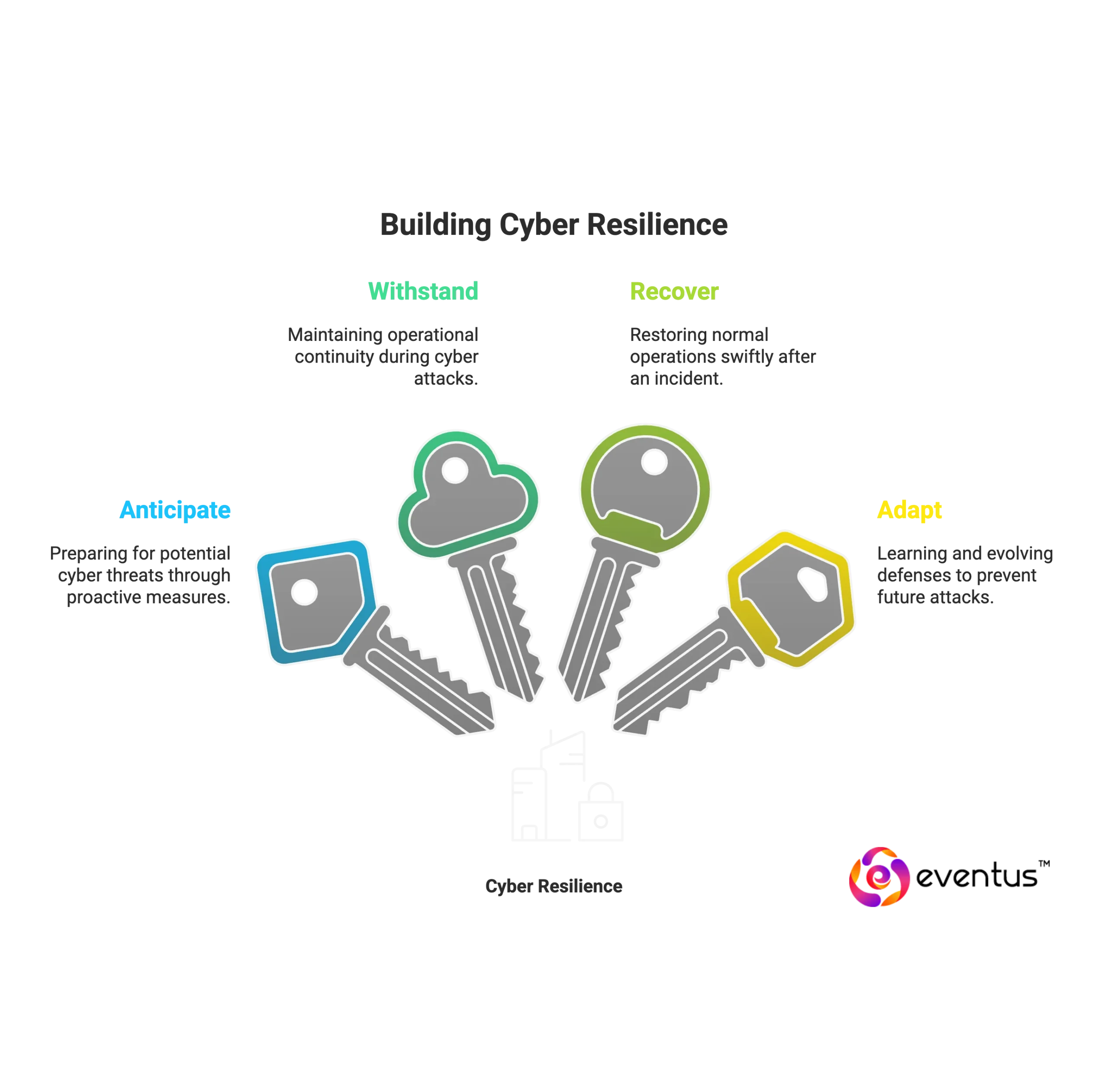
The core principles of anticipate, withstand, recover, and adapt describe how an organization builds resiliency against cyber risk. Each stage focuses on a distinct response capability to ensure continuity during and after a cyber attack.
- Anticipate: Anticipation reduces the element of surprise and prepares teams with clear playbooks.
- Withstand: This principle ensures systems continue operating even when a cyber attack occurs. It requires resilient architectures that isolate impacted areas, limit damage, and preserve essential functions.
- Recover: Recovery focuses on restoring normal operations quickly and effectively after an incident. It includes backup integrity, tested recovery procedures, and the ability to redeploy critical systems.
- Adapt: Adaptation is about learning from every incident to improve long-term resiliency. Adaptation ensures that defenses evolve faster than attackers’ tactics.
Together, these principles form a cycle that strengthens organizational resiliency, enabling businesses to anticipate evolving threats, withstand ongoing attacks, recover rapidly, and adapt to prevent future disruptions.
What are real-world examples of cyber resilience in practice?
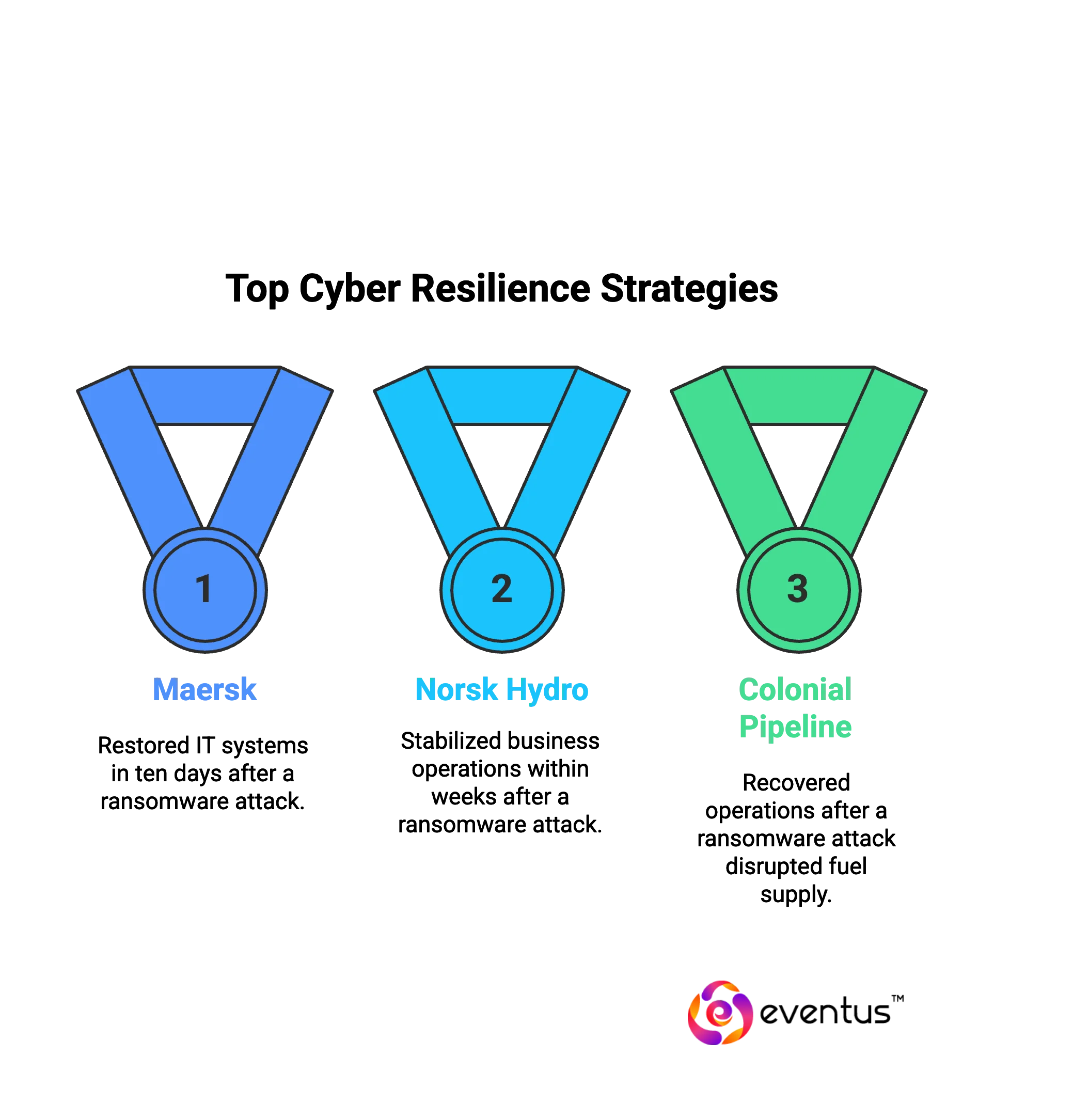
Here are some real-life examples of cyber resilience in practice that demonstrate how organizations withstand, recover, and adapt after cyberattacks or major cyber incidents:
1. Maersk (Global Shipping, 2017 NotPetya Attack)
Maersk, the world’s largest container shipping company, was hit by the NotPetya ransomware. The attack shut down booking systems and port operations across 600 locations worldwide. Thanks to a single unaffected domain controller backup, the company restored its IT systems within ten days. Despite massive disruption, Maersk’s resiliency allowed it to recover global business operations quickly and adapt its cybersecurity framework to prevent similar incidents.
2. Norsk Hydro (Manufacturing, 2019 Ransomware Incident)
Norsk Hydro, a leading aluminum producer, suffered a ransomware attack that forced a switch to manual operations across multiple plants. Instead of paying the attackers, the company deployed a structured cyber resilience plan with transparency, communication, and rapid incident response. Within weeks, business operations were stabilized, showing strong organizational resilience. The company invested heavily in improved security posture, enhanced monitoring, and stronger recovery strategies.
3. Colonial Pipeline (Energy, 2021 Ransomware Attack)
Colonial Pipeline, a major US fuel supplier, was forced to shut down operations after ransomware disrupted billing and operational networks. The shutdown led to fuel shortages across the East Coast. Recovery required deploying disaster recovery processes and collaboration with national cyber security agencies. The incident showed the critical need for robust cyber resilience in critical infrastructure sectors.
How is cyber resilience different from cybersecurity?
| Aspect | Cybersecurity | Cyber Resilience |
| Primary Focus | Preventing and detecting cyber threats through security controls and monitoring | Ensuring organizations can withstand and recover from cyber events and continue business operations |
| Objective | Reduce vulnerabilities, manage cyber risks, and prevent breaches | Maintain mission-critical operations, recover from cyber attacks, and adapt to the evolving cyber threat landscape |
| Approach | Defensive and preventive measures (e.g., firewalls, SIEM, identity and access management) | Adaptive, recovery-oriented strategies built on a cyber resilience framework and long-term planning |
| Time Horizon | Real-time prevention and immediate mitigation of security incidents | Long-term capability to recover from cyber, adapt, and improve continuously |
| Outcome | Enhanced security posture and reduced likelihood of security breaches | Reduced downtime, significant cost savings, and protection of stakeholder trust during and after incidents |
| Tools & Practices | Security information and event management, continuous security monitoring, risk assessment, security controls | Disaster recovery, business continuity, proactive cyber strategies, and resilience testing to recover from cyber attacks |
| Dependency | Effective at reducing the probability of a cyberattack or security breach | Effective only when combined with cybersecurity; cyber resilience requires strong cyber defense plus recovery planning |
| Value to Business | Strengthens data security and compliance with information security requirements | Enables a cyber resilient organization that can manage cyber disruptions, adapt to new threats, and safeguard long-term business operations |
What is the strategy?
A cyber resilience strategy is a structured approach that ensures an organization can anticipate, withstand, recover, and adapt to cyber threats and unexpected disruptions such as cyberattacks or natural disasters. While cybersecurity focuses on prevention, a cyber resilience strategy integrates security operations, recovery planning, and adaptability to maintain business continuity under pressure.
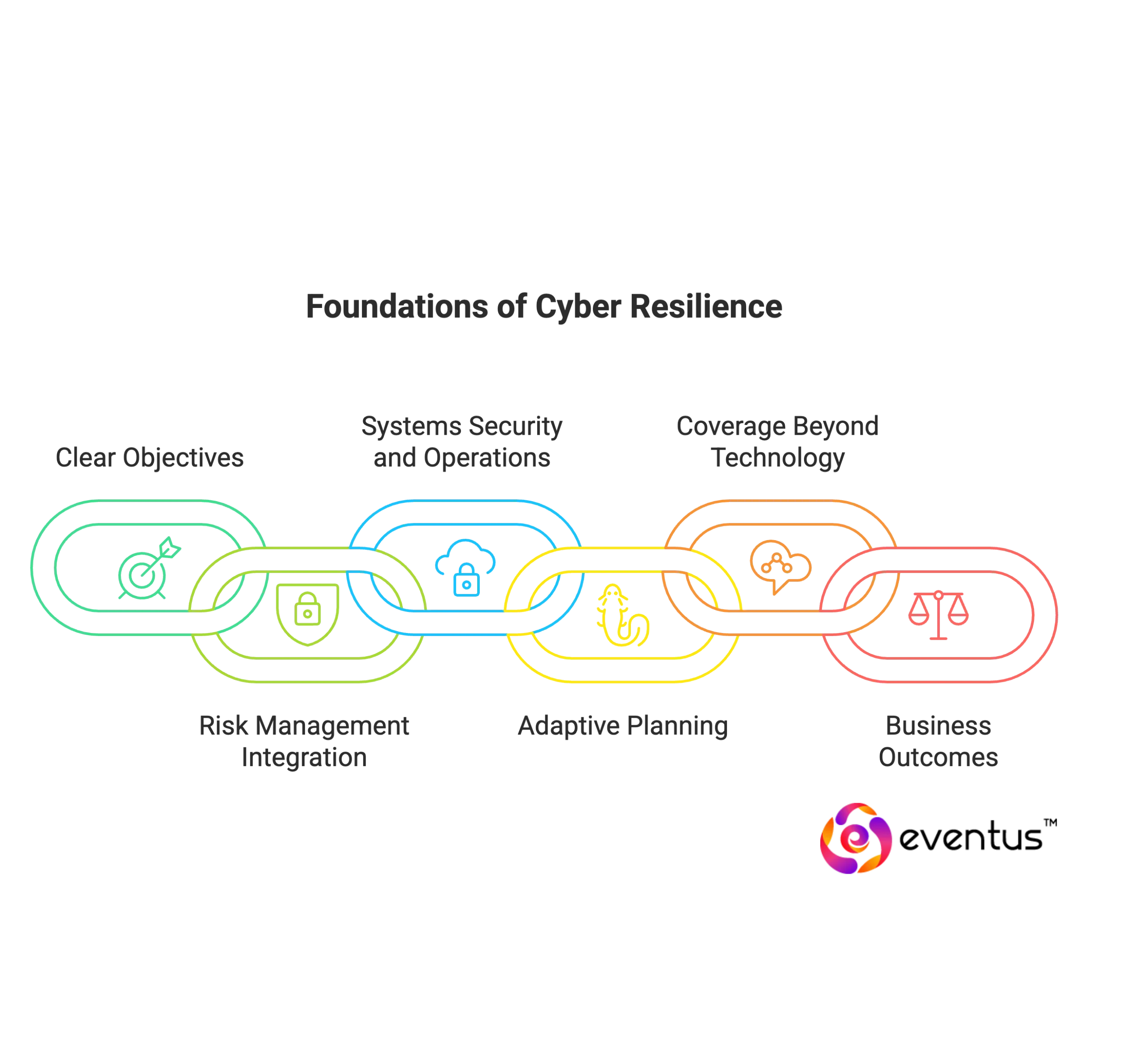
A well-designed strategy includes:
- Clear Objectives
The objective of cyber resilience is not only the ability to prevent incidents but also to recover quickly and sustain mission-critical services. - Integration with Risk Management
Cyber resilience strategies embed cybersecurity risk management and risk mitigation practices into the organization’s cyber posture. By aligning with recognized standards such as NIST SP 800-160 Vol. 2, organizations can structure controls and processes that ensure resilience. - Focus on Systems Security and Operations
A cyber resilience strategy fortifies systems security, embeds adaptive security measures, and empowers security teams to withstand advanced cyber threats. Effective cyber resilience requires coordination across security operations, business continuity, and IT recovery. - Adaptive and Proactive Planning
Cyber resilience refers to the ability to adapt to an evolving cyber threat landscape. Strategies include continuous improvement, proactive cyber readiness, and learning from past security incidents to stay ahead of future risks. - Coverage Beyond Technology
Resilience is not limited to IT. A comprehensive strategy addresses dependencies on Internet of Things (IoT) devices, supply chains, and external partners, ensuring the organization can fortify their defenses and maintain resilience across the ecosystem. - Business Outcomes
Ultimately, a cyber resilience strategy helps businesses maintain trust, reduce downtime, and achieve significant cost savings. By embedding resiliency into operations, organizations can ensure uninterrupted services and meet stakeholder expectations even during crises.
In essence, a cyber resilience strategy transforms an enterprise from being only secure to becoming cyber-resilient—prepared to manage cyber events effectively and safeguard long-term business continuity.
What governance model and RACI are needed for resilience?
A governance model for resilience defines decision rights, oversight, and accountability so the organization becomes cyber-resilient. It aligns cybersecurity and cyber resilience with enterprise risk, operations, and compliance.
Governance model
- Board sets risk appetite and oversees cyber resiliency metrics; CEO sponsors; COO chairs a Resilience Council (CISO, CIO/CTO, CRO, Legal, BU heads).
- Three lines of defense: Operations own controls; Risk and CISO challenge; Internal Audit assures.
- Cadence and KPIs: quarterly board review, monthly council; KPIs include RTO, RPO, MTTR, exercise pass rate, backup immutability, third-party coverage.
- Purpose: cyber resilience to ensure continuity; cyber resilience helps businesses reduce downtime and regulatory exposure; goal of cyber resilience is sustained operations.
RACI
- Policy and risk appetite — A: Board; R: CISO, CRO
- Strategy and roadmap — A: COO; R: CISO, CIO/CTO
- Business impact analysis — A: COO; R: BU heads
- Risk assessment and treatment — A: CRO; R: CISO, BU
- Incident response and crisis — A: COO; R: CISO, SOC
- Backup and recovery — A: CIO/CTO; R: IT-DR/BCM
- SIEM and monitoring — A: CISO; R: SOC
- Third-party resilience — A: TPRM; R: CISO, Legal
What is the framework?
A cyber resilience framework is a structured model that guides how an organization prepares for, withstands, responds to, and recovers from cyber incidents. Unlike ad hoc measures, a framework provides a repeatable and measurable structure that integrates people, processes, and technology—including cyber defense and recovery capabilities—into one cohesive program.
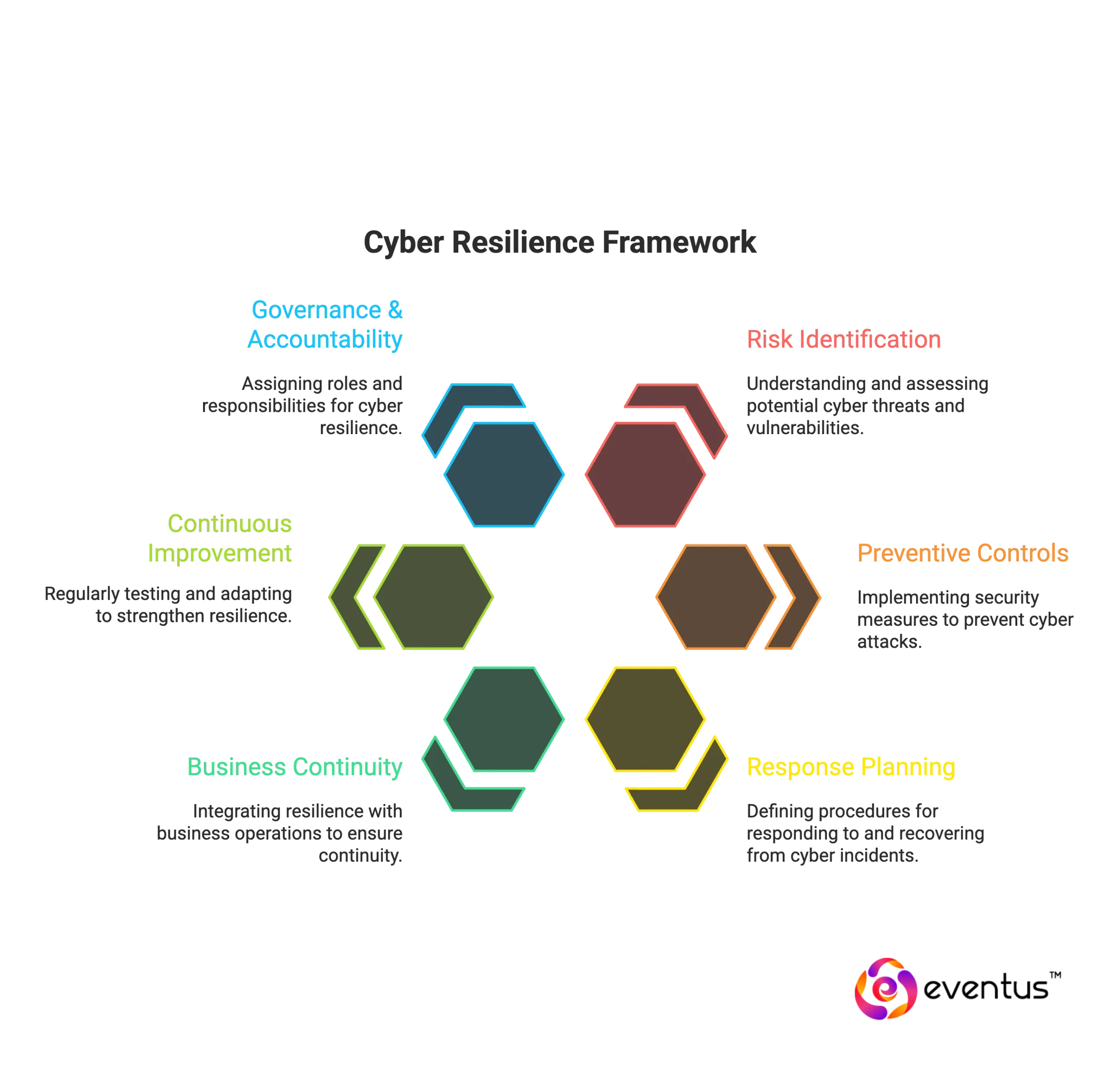
Key elements of a cyber resilience framework include:
- Risk identification and assessment
Understanding the organization’s exposure to threats, vulnerabilities, and potential disruptions. - Preventive controls
Deploying security measures to reduce the likelihood of breaches, ransomware, or other attacks. - Response and recovery planning
Defining clear procedures to respond to incidents and restore mission-critical operations within acceptable timelines. - Business continuity integration
Aligning resilience with business continuity and disaster recovery to ensure operations continue even under cyber stress. - Continuous improvement
Regular testing, post-incident reviews, and adapting to the evolving threat landscape to strengthen organizational resilience. - Governance and accountability
Assigning clear roles and responsibilities so that executives, security teams, and stakeholders are aligned with the goal of cyber resilience.
In essence, a cyber resilience framework provides organizations with a disciplined approach to fortify their defenses, ensure operational continuity, and build long-term adaptability—including cyber response and recovery as a core business function.
How does ISO 27001 align with ISO 22301 for continuity and recovery?
ISO 27001 and ISO 22301 are complementary standards that together strengthen an organization’s ability to manage cybersecurity risk, continuity, and recovery.
| Aspect | ISO 27001 (Information Security) | ISO 22301 (Business Continuity) | Alignment for Resilience |
| Primary Focus | Protecting information assets from cyber threats through an ISMS | Ensuring continuity of critical business functions through a BCMS | Combined, they safeguard both data security and operational resilience |
| Objective | Maintain confidentiality, integrity, and availability of information | Restore operations and services within agreed timeframes (RTO, RPO) | Unified objective of cyber resilience to ensure security and recovery |
| Approach | Risk-based management of cybersecurity risks with security controls | Risk-based continuity planning and recovery strategies | Shared risk assessment methods strengthen resilience |
| Controls & Measures | Identity and access management, monitoring, encryption, security operations | Disaster recovery, alternate sites, continuity playbooks, recovery testing | Complementary controls that cover both prevention and recovery |
| Governance | Policies, ISMS leadership roles, ongoing audits | Policies, continuity governance roles, regular continuity reviews | Governance models align to provide accountability across security and recovery |
| Testing & Improvement | Regular audits, vulnerability testing, continuous security monitoring | Continuity drills, tabletop exercises, crisis simulations | Continuous improvement cycle integrates both prevention and recovery testing |
| Outcome | Enhanced systems security, reduced cybersecurity risk, compliance | Reliable recovery of business operations, minimized disruption | A cyber-resilient organization that can withstand and recover from disruptions |
What are the components?
The components of cyber resilience are the foundational elements that enable an organization to anticipate, withstand, recover, and adapt during and after cyber disruptions. Each component strengthens overall resiliency and ensures that critical operations continue with minimal impact.
- Risk Management: Identifying, assessing, and mitigating cybersecurity risks to reduce the likelihood and severity of cyber incidents.
- Threat Detection and Response: Implementing monitoring tools, threat intelligence, and security operations to detect and respond to cyberattacks in real time.
- Identity and Access Management (IAM): Controlling who can access systems and data, ensuring least privilege, and preventing unauthorized use of credentials.
- Data Protection and Backup: Encrypting sensitive data, securing storage, and maintaining immutable backups to guarantee recovery after a breach or ransomware attack.
- Business Continuity and Disaster Recovery (BC/DR): Ensuring mission-critical processes remain functional and that systems can be restored within recovery time objectives (RTO) and recovery point objectives (RPO).
- Systems Security Architecture: Designing resilient IT and OT infrastructures with segmentation, redundancy, and zero trust principles to withstand attacks.
- Incident Response Planning: Defining structured processes and playbooks for managing security incidents, including communication with stakeholders and regulators.
- Third-Party and Supply Chain Resilience
Managing risks introduced by vendors, partners, and supply chain dependencies, including contractual obligations and resilience testing. - Continuous Monitoring and Improvement
Using security information and event management (SIEM), vulnerability assessments, and post-incident reviews to adapt resilience measures. - Employee Awareness and Training
Building a culture of resilience by training staff to recognize threats, follow incident procedures, and participate in drills.
Why it is important?
Cyber resilience is important because it ensures that an organization can continue to operate and recover quickly in the face of cyber threats. While cybersecurity focuses on prevention, cyber resilience prepares businesses to withstand and adapt when prevention fails.
- Business Continuity
Cyber resilience ensures that mission-critical operations remain functional even during disruptions, safeguarding productivity and service delivery. - Financial Protection
By reducing downtime and recovery costs after a cyberattack, organizations avoid significant financial losses. - Reputation and Trust
Stakeholders, customers, and partners expect reliable protection. Resilience builds confidence by showing the organization can withstand and recover from security incidents. - Adaptability to Emerging Threats
As the cyber threat landscape evolves, resilience enables continuous improvement, ensuring defenses adapt to new attack methods. - Regulatory and Compliance Readiness
Many industries require demonstrable resilience for audits and legal obligations, making it a critical compliance factor. - Risk Mitigation Beyond Prevention
Preventive measures alone cannot eliminate cybersecurity risk. Resilience integrates prevention, response, and recovery to cover the full cycle of protection. - Long-Term Value
Effective resilience strengthens overall business stability, provides competitive advantage, and helps organizations stay ahead in an environment where cyber disruptions are inevitable.
In essence, cyber resilience helps businesses not just survive cyberattacks but thrive despite them, turning resilience into a strategic advantage.
How can it be improved?
Cyber resilience can be improved by strengthening prevention, detection, response, and recovery across the entire organization. Improvement requires structured planning, proactive measures, and continuous adaptation.
- Conduct Comprehensive Risk Assessments
Regularly identify vulnerabilities, evaluate potential impacts, and update the risk profile to reflect the evolving threat landscape. - Strengthen Security Controls
Deploy layered security measures including access controls, encryption, network segmentation, and continuous patch management to reduce exposure. - Enhance Threat Detection and Monitoring
Use security information and event management (SIEM), real-time monitoring, and threat intelligence to detect and contain incidents quickly. - Develop and Test Incident Response Plans
Establish clear playbooks and conduct regular simulations, tabletop exercises, and breach-and-attack tests to validate readiness. - Improve Data Protection and Recovery
Maintain immutable backups, validate recovery time objectives (RTO) and recovery point objectives (RPO), and perform regular disaster recovery drills. - Invest in Security Operations
Mature SOC capabilities, automation, and orchestration can shorten response times and help withstand advanced attacks. - Build Organizational Awareness
Train employees to recognize threats, report suspicious activity, and follow best practices, creating a culture of resilience. - Ensure Supply Chain and Third-Party Resilience
Assess vendor dependencies, include resilience clauses in contracts, and monitor external risks. - Adapt and Improve Continuously
After every cyber incident, perform post-incident reviews, analyze root causes, and adapt policies, controls, and procedures accordingly. - Integrate Business Continuity and Cybersecurity
Align cyber resilience with business continuity management so the organization can withstand both cyberattacks and non-cyber disruptions such as natural disasters.
How does AI change cyber resilience?
AI changes cyber resilience by expanding both the threat landscape and the defensive capabilities available to organizations. It introduces new risks through adversarial use of machine learning but also strengthens resilience through automation, intelligence, and adaptability.
- AI-powered cyberattacks: Attackers use generative AI to create more convincing phishing campaigns, deepfakes, and automated malware, making traditional defenses less effective.
- Exploiting vulnerabilities faster: Automated tools driven by AI can scan for and exploit vulnerabilities at a scale that outpaces human defenders.
- Adversarial AI: Attackers may poison data models or manipulate algorithms to bypass detection systems.
- Real-time threat detection: AI enhances monitoring through anomaly detection and predictive analytics, improving the ability to anticipate incidents before they escalate.
- Faster response and recovery: AI-driven security operations (e.g., SOAR and AIOps) automate containment, triage, and recovery steps, reducing mean time to detect (MTTD) and mean time to recover (MTTR).
- Adaptive defenses: Machine learning models continuously evolve, helping organizations withstand and recover from emerging attack patterns.
- Resilience at scale: AI supports continuous security monitoring across large, complex infrastructures such as IoT, cloud, and critical infrastructure systems.
- Stronger cyber resiliency posture: AI shifts organizations from reactive to proactive resilience by providing predictive insights.
- Improved decision-making: AI analyzes vast security information datasets to guide executive-level risk management.
- Continuous learning: Each incident becomes training data, enabling organizations to adapt resilience strategies faster than attackers can adjust.