This article explores risk assessment and mitigation with a focus on 2025 strategies and tools. It defines key processes, from risk identification to continuous monitoring, and presents actionable frameworks aligned with ISO 31000. The guide outlines four major mitigation strategies—avoidance, reduction, transference, and acceptance—backed by examples from global enterprises. Featured case studies include GenAI risk governance by U.S. federal agencies, Co-op Retail’s cyberattack response, and Gujarat’s industrial digital risk controls. The article also highlights top tools like GRC platforms, SIEM systems, and SOAR automation to streamline decision-making and ensure proactive, adaptive risk management in high-stakes environments.
Table of Contents
What is Risk Assessment?
Risk assessment, as outlined by the ISO 31000 Risk Management Standard, is the structured process of identifying, analyzing, and evaluating threats that may compromise organizational assets, operations, or reputation. In fact, businesses with mature risk assessment processes are 50% more likely to financially outperform their peers (PwC Global Risk Survey 2024). A prime example is how financial institutions routinely conduct quarterly risk assessments to stay compliant with evolving regulatory frameworks like Basel III. In modern cybersecurity landscapes, Security Operations Centers (SOC) play a crucial role by offering SOC benefits such as continuous threat monitoring, rapid incident response, and proactive risk mitigation aligned with the broader risk management strategy. Evaluating SOC as service pricing models enables organizations to balance robust monitoring capabilities with budgetary constraints, ensuring both security effectiveness and cost efficiency.
What is Risk Mitigation?
Risk mitigation is the process of developing strategies and actions to reduce the impact or likelihood of identified risks. It focuses on proactive measures to protect business operations, assets, and objectives from potential threats, and can be significantly bolstered by enlisting a managed security service provider to deliver continuous threat oversight and rapid incident response. Organizations can further enhance their defenses by deploying SOAR tools to automate incident response playbooks, orchestrate workflows across security teams, and accelerate threat containment.
Why is Risk Assessment and Mitigation important?
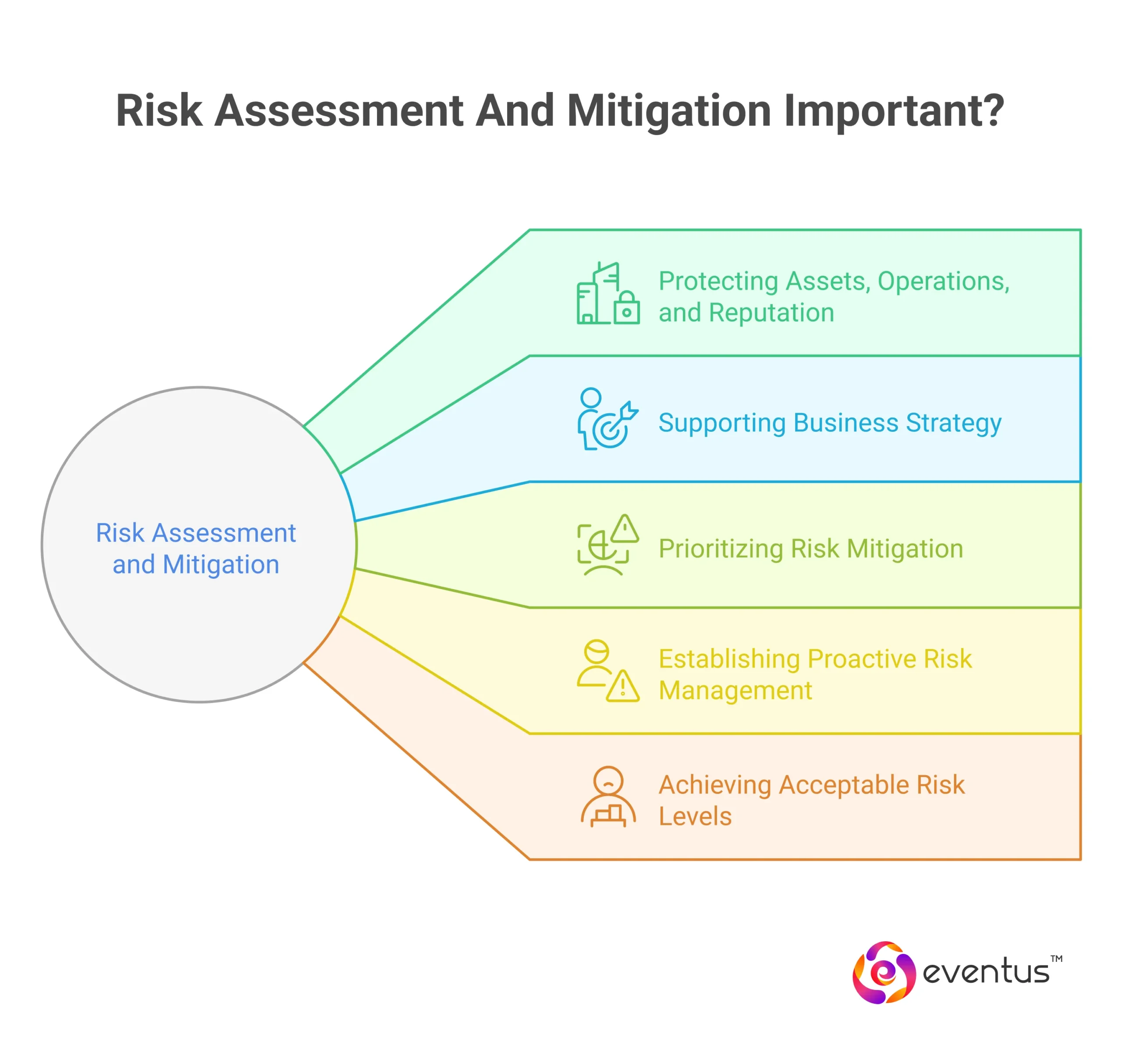
The primary goal of risk assessment and mitigation is to identify potential risks, analyze their impact, and implement appropriate measures to reduce their severity or likelihood. Engaging a managed soc provider can enhance these efforts by delivering specialized expertise and continuous security oversight.
Key objectives include:
- Protecting assets, operations, and reputation from identified risks.
- Supporting the business strategy by ensuring operational continuity.
- Prioritizing risk mitigation based on the potential impact of each risk.
- Establishing a risk management process that remains proactive and adaptive.
- Achieving an acceptable level of risk through targeted mitigation measures.
What are the steps in a risk assessment process?
A comprehensive risk assessment plan should outline asset inventories, threat sources, vulnerability analyses, potential impacts, likelihood ratings, and defined roles and responsibilities. It must specify data collection methods, evaluation criteria, and review timelines. Engaging stakeholders and leveraging specialized assessment tools ensures thorough coverage. Additionally, partnering with a top SOC service provider can deliver real-time threat intelligence and expert analysis to support and validate your risk evaluation process.
An effective risk assessment framework generally follows a structured path to ensure all critical aspects of risk are covered:
- Risk Identification: Recognizing and listing all possible risk events that could affect operations.
- Risk Analysis: Assessing the level of risk by evaluating the severity and likelihood of each identified risk.
- Risk Evaluation: Prioritizing risks based on their potential impact on business goals and strategy.
- Risk Mitigation Planning: Defining appropriate measures to address high-priority risks through risk mitigation or risk transfer.
- Implementation: Executing the plan for mitigating the identified threats.
- Monitoring Risk: Continuously tracking and reviewing risk management efforts to adapt to new or evolving threats.
How do you identify and classify risks?
Risk identification is the foundation of a successful risk assessment. It involves:
- Brainstorming sessions with stakeholders to surface possible business risks.
- Reviewing historical data on past incidents and near-misses.
- Conducting interviews and surveys with subject-matter experts.
- Leveraging risk mitigation tools for automated risk detection.
Once risks are identified, classification helps in understanding the different types of risk, such as:
- Financial Risk
- Operational Risk
- Strategic Risk
- Compliance Risk
- Reputational Risk
What Are the Types of Risk Mitigation Strategies?
Understanding risk mitigation strategies is essential for building a robust risk management plan. These approaches help organizations identify potential risks, assess their severity, and implement appropriate measures to manage risk effectively. According to the ISO 31000 Risk Management Standard, risk mitigation strategies must align with an organization’s objectives, ensuring that risk responses contribute to business resilience. Let's explore the different types of risk mitigation strategies used across industries today.
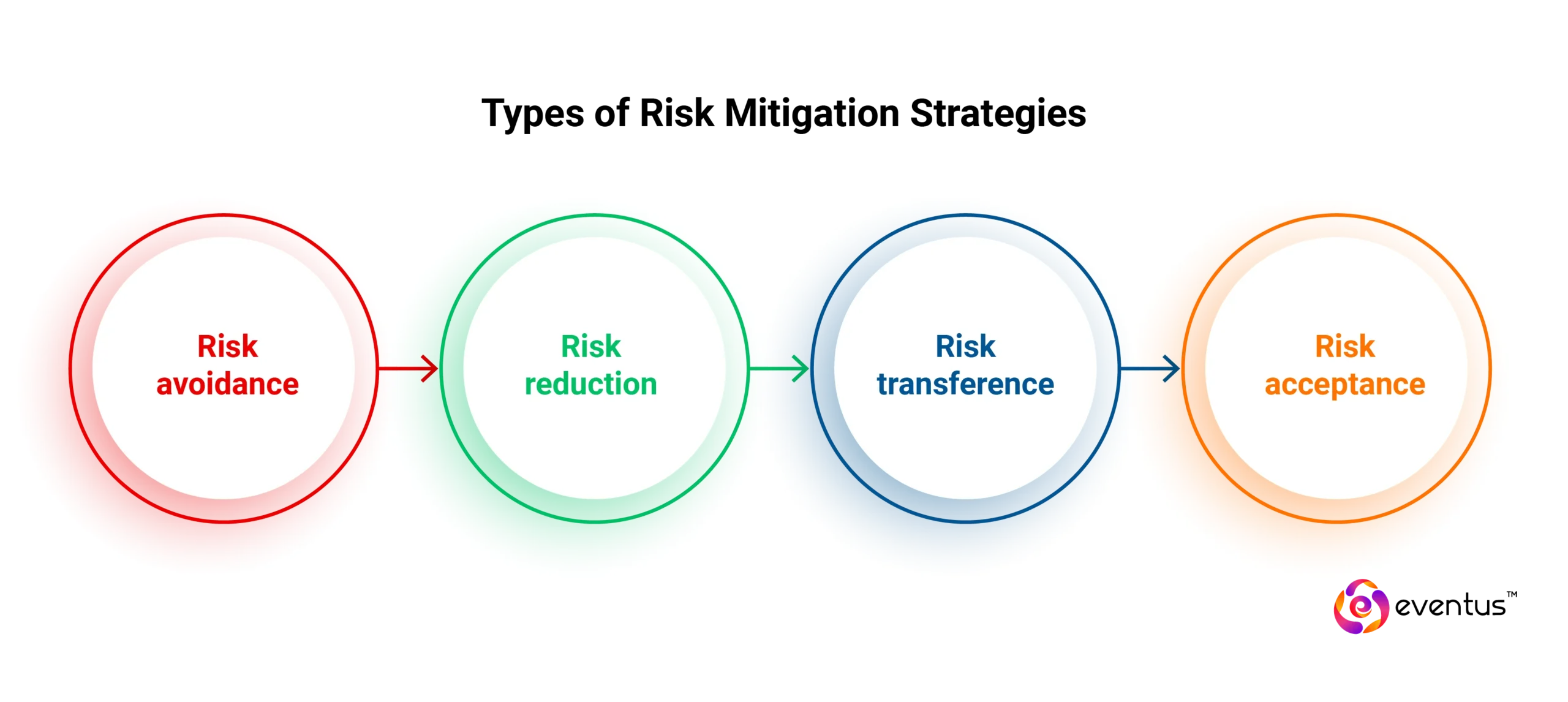
1. Risk avoidance
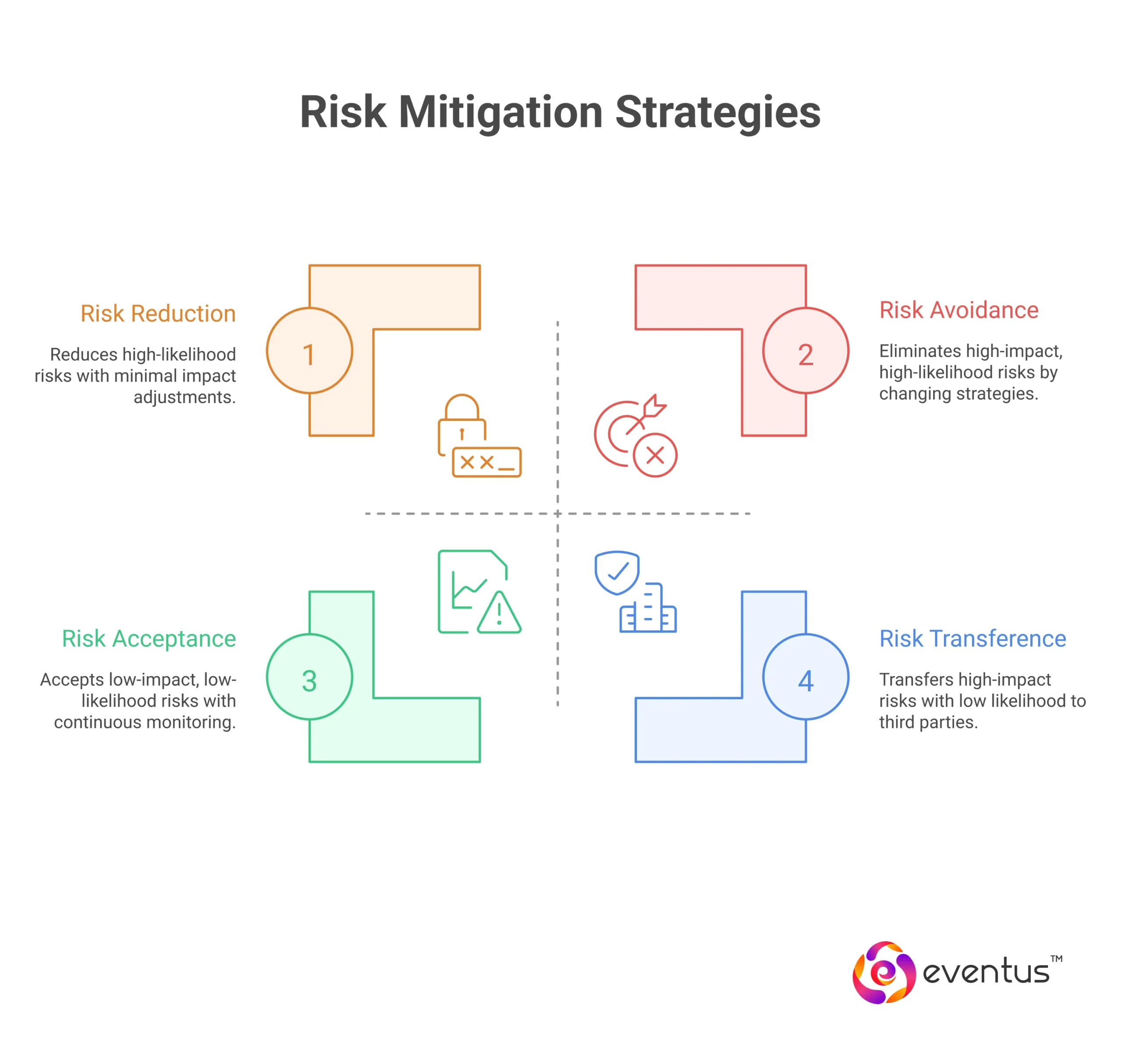
Risk avoidance is a proactive approach where the organization avoids the risk entirely by eliminating the activities or conditions that could cause it.
- It often involves changing business strategies, project scopes, or operational processes to steer clear of identified risks.
- For example, a company might decide not to launch a product in a market known for high regulatory hurdles, thus completely eliminating related risks.
2. Risk reduction
Risk reduction focuses on decreasing the likelihood or the potential impact of a risk. Installing multi-factor authentication reduces cybersecurity threats, an approach adopted by 80% of Fortune 500 companies.
- It involves implementing risk controls, safety measures, and compliance practices to reduce the impact or level of risk.
- For instance, installing advanced cybersecurity solutions can reduce the impact of data breaches on operations.
3. Risk transference
Risk transference means shifting the responsibility for a potential risk to a third party.
- This can be achieved through outsourcing, purchasing insurance, or entering into contractual agreements that transfer liability.
- A common example includes buying business insurance to cover financial losses from natural disasters or supply chain disruptions.
4. Risk acceptance
Risk acceptance occurs when a business consciously decides to accept the risk without taking immediate steps to mitigate it.
- This strategy is usually chosen when the level of risk is low, the cost of mitigation is higher than the risk itself, or when mitigation is simply impractical.
- It is crucial, however, that a risk acceptance strategy includes continuous risk monitoring to ensure that the situation does not worsen.
What Are the Latest Trends and Real-World Examples of Risk Assessment and Mitigation?
In 2025, several high-profile initiatives have demonstrated how structured, real-time risk management frameworks can prevent disruption, ensure compliance, and enhance public trust.
Here are the most notable and widely discussed examples:
1. Generative AI Risk Framework by U.S. Federal Agencies
Date: July 17, 2025
Location: United States (Washington, D.C.)
The U.S. Department of Homeland Security (DHS), in collaboration with other federal bodies, released the Playbook for Public Sector GenAI Deployment. This initiative outlines a complete risk assessment and mitigation strategy for using Generative AI in government workflows. Key actions include:
- Baseline risk modeling tied to national security, data leakage, and decision bias.
- Multi-disciplinary review boards assessing every AI pilot before launch.
- Mitigation controls like real-time audits, encryption, and zero-trust enforcement.
2. Co-op Retail Group Cyberattack Response and Mitigation
Date: July 16, 2025
Location: London, United Kingdom
Following a major cyberattack affecting 6.5 million customer profiles, the Co‑op Retail Group implemented a swift risk containment and mitigation strategy:
- Reverted to manual operations for critical services.
- Engaged law enforcement and forensic analysts within 24 hours.
- Established a public incident response timeline to maintain customer trust.
- Introduced segmentation and enhanced third-party controls to prevent recurrence.
3. Digital Risk Mitigation in Gujarat’s Industrial Sector
Date: July 17, 2025
Location: Ahmedabad, India
Over a dozen chemical, pharmaceutical, FMCG, and banking firms in Gujarat initiated what’s now referred to as the “Digital Leash Framework”—an internal security and risk mitigation protocol aimed at stopping insider threats and corporate espionage. Measures include:
- Disabling USB ports, screen captures, and location-agnostic email access.
- Role-based email permissions, with strict remote access only for top executives.
- Use of code words for sensitive documents and internal formulas.
- Real-time alerts for attempts to share regulated identifiers (e.g., PAN, Aadhaar).
How do you choose the right mitigation strategy?
Choosing the best strategy requires a thorough risk assessment and a clear understanding of organizational priorities. Consider the following best practices to make informed decisions:
- Identify and analyze each risk using a qualitative risk or quantitative risk assessment framework.
- Evaluate the severity and potential impact of each risk on operations, finances, reputation, and customer trust.
- Align the choice of mitigation strategy with overall business strategy and long-term goals.
- Ensure that the risk mitigation plan is flexible enough to adjust based on changing circumstances.
- Monitor the established plan regularly to ensure it remains effective and that any identified risks are properly managed.
What Are the Best Risk Mitigation Tools and Practices?
To achieve effective risk mitigation, a combination of risk mitigation tools and best practices is essential.
Selecting the right tools plays a critical role in minimizing the potential impact of each risk and ensuring the risk management process remains proactive.
Some of the most trusted risk mitigation tools used by businesses today include:
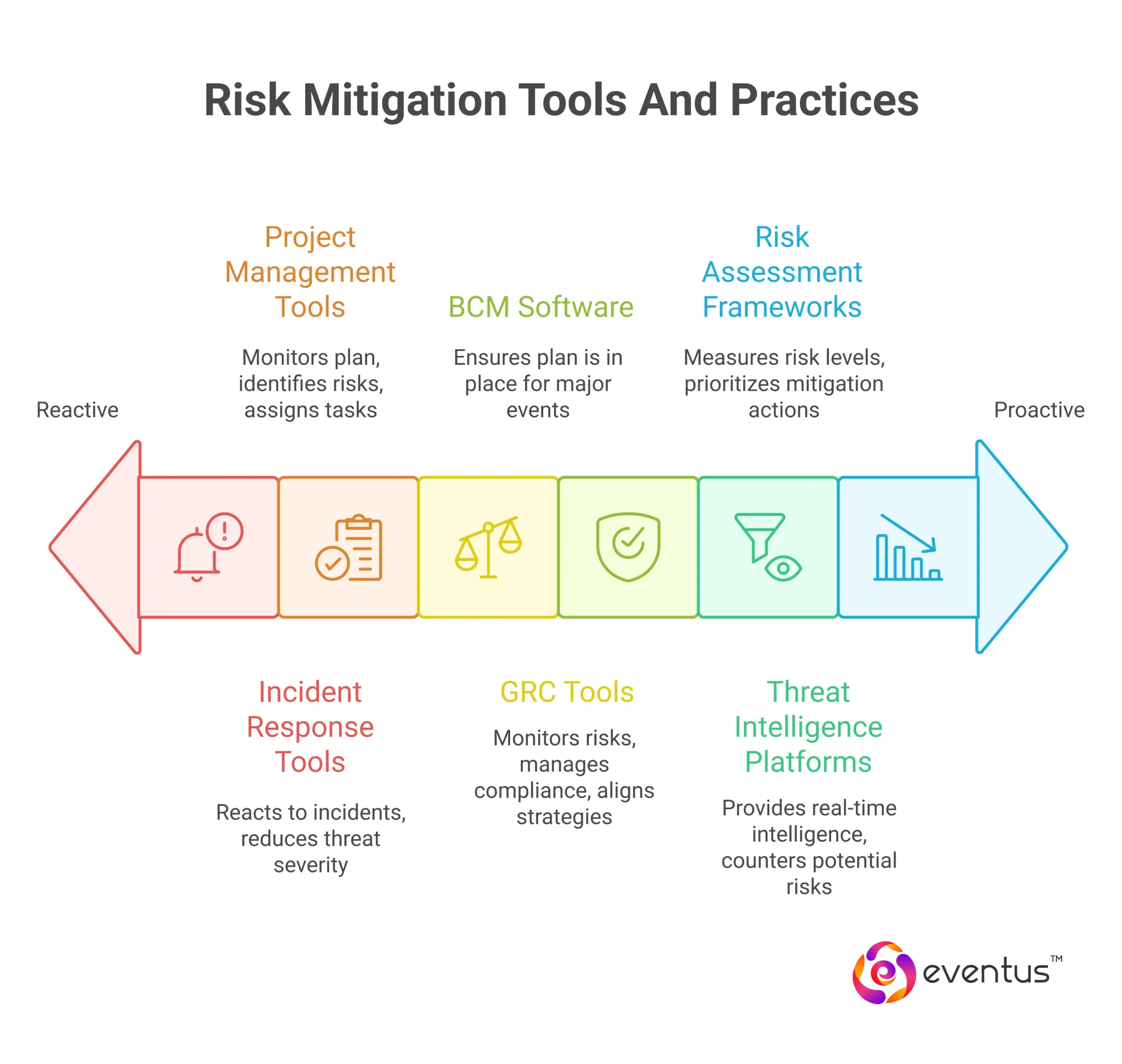
- Risk Assessment Frameworks: Structured methodologies like quantitative risk assessment and qualitative risk assessment help measure risk levels and prioritize mitigation actions.
- Business Continuity Management (BCM) Software: Assists in ensuring a plan is in place to respond to any major risk event or disruption.
- Threat Intelligence Platforms: Provide real-time security intelligence for anticipating and countering potential risks before they escalate.
- GRC Tools (Governance, Risk, and Compliance): Help businesses monitor identified risks, manage compliance, and align risk mitigation strategies with their overall business strategy.
- Project Management Tools: Platforms like Asana or Monday.com support risk identification, task assignment, and monitoring the established plan across projects.
- Incident Response and SIEM Tools: Enable continuous monitoring risk activities, helping businesses detect and react to incidents, reducing the severity of potential threats.
Leading businesses use MetricStream and RSA Archer to automate governance, risk, and compliance processes
How do tools streamline the risk mitigation process?
The right tools ensure the risk mitigation process becomes less reactive and more predictive:
- Automation of Repetitive Tasks: Risk documentation, audit trails, and alerts are managed efficiently, allowing teams to focus on strategic risk management strategies.
- Enhanced Collaboration Across Teams: Platforms enable different departments to share insights, ensuring a unified approach to managing risk.
- Clear Visualization of Risk Levels: Dashboards and analytics simplify the monitoring of risk for different areas of the business.
- Facilitation of Risk Transfer and Risk Acceptance Decisions: GRC tools provide frameworks to mitigate, accept the risk, or transfer the risk appropriately.
- Keeping the Risk Management Plan Up to Date: Real-time updates ensure that the plan in place evolves as the business and threat landscapes change.