This article answers “What are common cloud security challenges?” by exploring the factors that increase the cloud attack surface, the visibility gaps inherent to distributed cloud environments, and the complications introduced by dynamic, auto-scaling workloads. It also examines the significant risks posed by supply-chain attacks and cloud-focused ransomware. Readers will gain an in-depth understanding of these critical security issues and best practices to strengthen their cloud security posture.
Table of Contents
What is Cloud Security?
Cloud security is the practice of protecting data, applications and infrastructures hosted in cloud environments through a combination of policies, technologies and controls designed to guard against unauthorized access, data breaches and service interruptions. According to a 2023 Gartner report, over 85% of organizations will embrace a cloud-first principle by 2025, making cloud security an essential business priority. Security Operations Centers (SOCs) play a pivotal role in continuously monitoring cloud environments, detecting anomalies, and orchestrating timely responses to emerging threats. A well-integrated SOC—whether in-house or delivered through SOC as a Service—acts as the command center for cloud threat detection and orchestration, ensuring alignment with enterprise risk management goals. Readers will gain an in-depth understanding of these critical security issues and best practices to strengthen their cloud security posture.
Why is cloud security important?
Cloud security refers to the practices and technologies designed to protect data, applications and infrastructure in cloud computing environments from evolving security threats. As organizations shift critical workloads to public, private and hybrid cloud deployments, robust cloud security is essential to mitigate security risks such as unauthorized access, data breaches and configuration errors.
In 2022, misconfigured cloud storage led to the exposure of 5.5 million records from an Australian government agency. To address these challenges, many organizations—especially in high-risk sectors—are turning to SOC as a Service offered by leading cybersecurity companies in India, known for delivering cost-effective and scalable security operations capabilities. Such incidents illustrate the critical need for proactive cloud security practices. Organizations increasingly adopt SOC as a Service to ensure 24/7 monitoring, rapid incident response, and expert threat analysis without the overhead of maintaining an in-house security team. Also partnering with a Managed Security Service Provider (MSSP) allows organizations to outsource critical security functions such as threat monitoring, log management, and compliance reporting, reducing the operational burden on internal teams. MSSPs bring specialized expertise and advanced tooling, making them a strategic choice for enterprises lacking the resources to build and maintain a full-scale in-house security operation.
What are the benefits of cloud security?
- Scalable security controls: Cloud security solutions automatically adjust protection levels as workloads grow, ensuring consistent defense without manual appliance provisioning. A 2023 study by IBM found that organizations with mature cloud security controls experience 43% fewer security incidents on average. Partnering with a managed SOC provider further enhances this capability by delivering continuous threat monitoring and expert-led incident response tailored to complex cloud environments.
- Centralized visibility and monitoring: Integrated security information and event management (SIEM) and cloud security posture management consolidate logs and alerts across multi-cloud and on-premise systems. SIEM is a centralized platform that collects, analyzes, and correlates security event data from across an organization’s infrastructure to detect anomalies and support incident response. Understanding what is SIEM becomes crucial in cloud environments where visibility is fragmented—these platforms not only streamline threat detection but also enable SOC teams to respond swiftly to incidents with contextual awareness.
- Cost efficiency: Leveraging a cloud service provider’s shared infrastructure reduces capital expenditure on hardware appliances and maintenance.
- Rapid incident response: Automated threat detection and response workflows minimize dwell time, enhancing overall security posture.
- Improved compliance: Built-in security services and preconfigured compliance templates help enforce data security standards for regulated cloud data. Cloud-native compliance tools such as AWS Config and Google’s Assured Workloads support regulatory adherence for frameworks like HIPAA, GDPR, and FedRAMP.
How does cloud security deliver enterprise-wide protection?
Cloud security delivers comprehensive enterprise protection by unifying identity and access management, network security and data encryption within a single security architecture. Security teams can enforce least-privilege access through centralized identity controls, segment workloads with virtual network policies, and apply end-to-end encryption for data in transit and at rest.
What essential tools enable cloud security?
Effective cloud security relies on a suite of specialized security tools and platforms that work together to provide visibility, control and protection across cloud services:
Identity and Access Management (IAM) Platforms: Policy-based identity and access management (IAM) enforces who can access specific cloud services and resources through centrally defined policies. These controls:
- Leverage role-based access control (RBAC) or attribute-based access control (ABAC) to grant permissions only to authorized cloud users. In 2023, the Capital One breach was largely mitigated due to the effectiveness of its WAF system in segmenting sensitive workloads.
- Require strong authentication mechanisms—such as multi-factor authentication (MFA) and federated single-sign-on—to verify user identities before granting access to cloud computing systems.
- Automate credential rotation and session timeout policies to reduce the risk of stolen or reused credentials.
This approach ensures that each user or service account operates with the least privilege necessary, reducing security risk across public, private, and hybrid cloud deployments.
Next-Generation Firewalls and Web Application Firewalls (WAF)
Inspect and filter traffic to and from cloud applications, blocking known threats and enforcing network security rules. In 2023, the Capital One breach was largely mitigated due to the effectiveness of its WAF system in segmenting sensitive workloads.
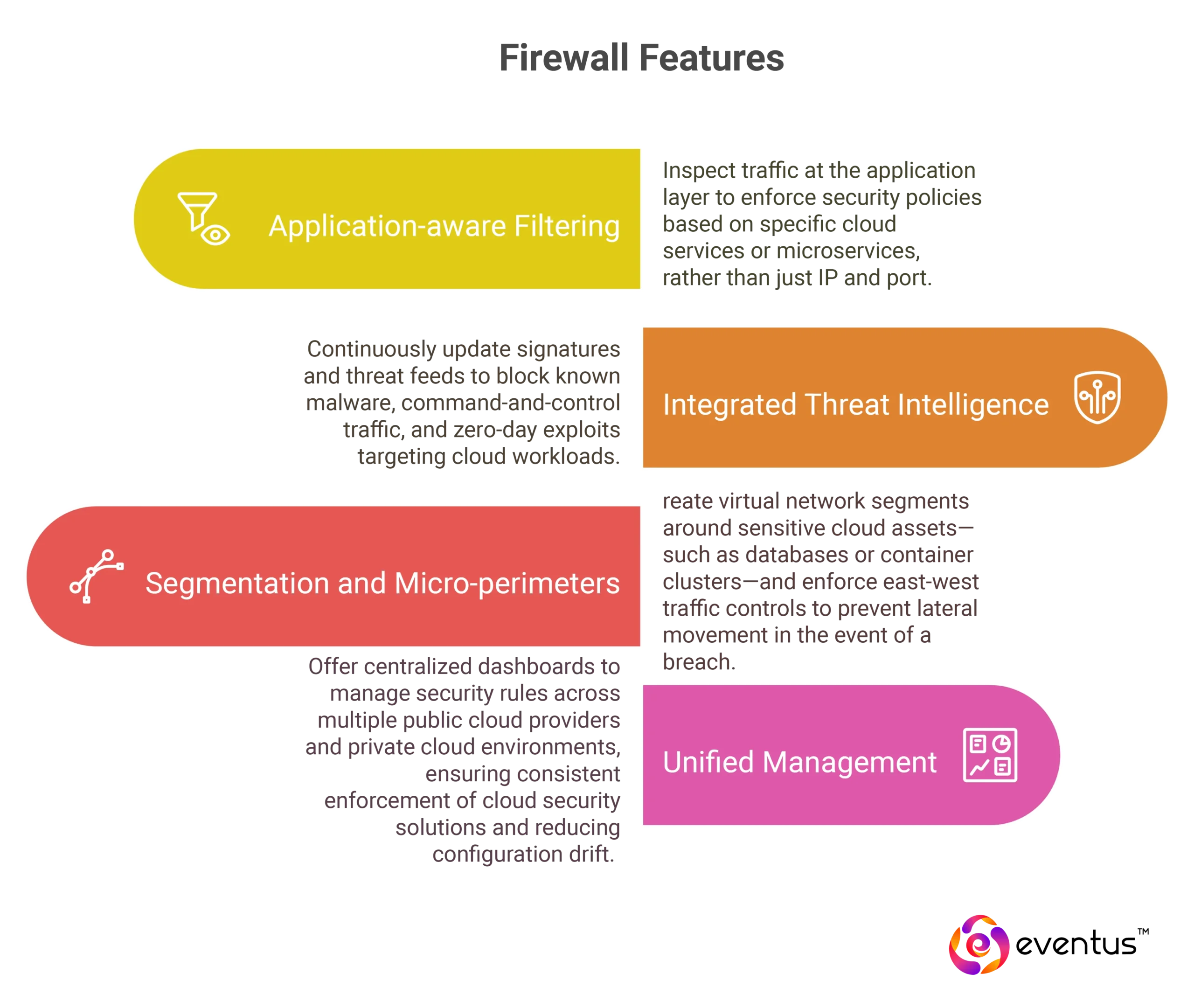
Next-generation firewalls (NGFWs) extend traditional network security tools into the cloud by providing:
- Application-aware Filtering: Inspect traffic at the application layer to enforce security policies based on specific cloud services or microservices, rather than just IP and port.
- Integrated Threat Intelligence: Continuously update signatures and threat feeds to block known malware, command-and-control traffic, and zero-day exploits targeting cloud workloads.
- Segmentation and Micro-perimeters: Create virtual network segments around sensitive cloud assets—such as databases or container clusters—and enforce east-west traffic controls to prevent lateral movement in the event of a breach.
- Unified Management: Offer centralized dashboards to manage security rules across multiple public cloud providers (e.g., AWS, Google Cloud) and private cloud environments, ensuring consistent enforcement of cloud security solutions and reducing configuration drift.
Encryption Key Management Services
Provide secure key generation, storage and rotation to support encryption of data in transit and at rest. Encryption transforms readable data into ciphertext, ensuring that even if cloud data is intercepted or accessed without authorization, it remains unintelligible. In cloud security architectures, encryption is applied both in transit—using TLS to protect data moving between users and cloud services—and at rest, where storage volumes, databases and backups are encrypted using strong algorithms (AES-256 or higher).
Implementing granular privilege and key management involves:
- Defining fine-grained IAM roles and permissions that align with job functions, so that cloud service provider consoles and APIs accept only narrowly scoped credentials.
- Employing hardware security modules (HSMs) or cloud-native key management services (KMS) to generate, store, and rotate encryption keys used for data at rest and in transit.
- Applying envelope encryption and key hierarchy models to separate data encryption keys from master keys, minimizing the blast radius if a single key is compromised.
- Auditing and logging all key usage events to maintain an immutable record of who accessed which key and when, thereby strengthening the organization’s security posture.
Endpoint Detection and Response (EDR)
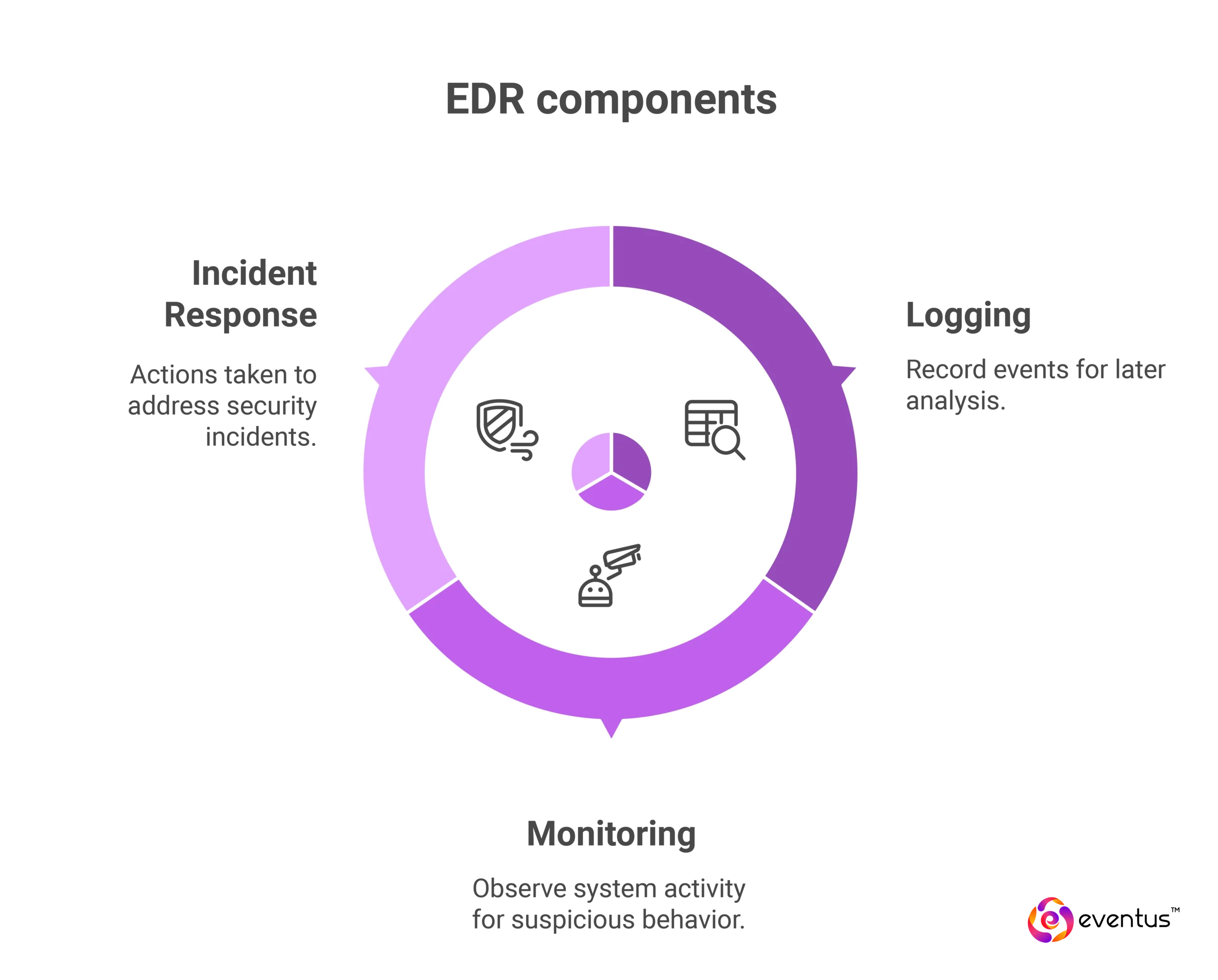
Monitors and protects virtual machines and containers running in cloud computing systems from malware and unauthorized activity. A proactive incident response strategy in the cloud combines continuous event management with automated alerting and runbooks:
- Logging: Enable and centralize logs from cloud services, network devices, and applications into a SIEM or cloud security posture management (CSPM) solution to capture authentication attempts, configuration changes, and anomalous activity.
- Monitoring: Define baselines and threat-detection rules to trigger alerts on deviations—such as unusual API calls or data-exfiltration patterns—and integrate with a security operations center (SOC) workflow.
- Incident Response: Maintain playbooks that automate initial containment actions (e.g., revoking compromised credentials, isolating affected resources) and outline manual escalation steps. Conduct regular tabletop exercises to validate the effectiveness of response procedures and refine the cloud security strategy.
How do cloud service and deployment models impact security?
Cloud service and deployment models define the division of security responsibilities and the scope of controls required to protect cloud resources. Deployment models—public, private, hybrid, and multi-cloud—carry distinct security concerns around data residency, network segmentation, and regulatory compliance, while service models—IaaS, PaaS, and SaaS—shape the shared responsibility boundaries for infrastructure in the cloud. Together, these models determine which security controls you implement, how you configure identity and access management, and the level of visibility and monitoring needed to maintain a robust cloud security posture. Netflix's hybrid cloud model is a notable example, blending AWS’s scalability with internal data centers for video rendering workloads.
- Public cloud environments offer scalability and cost efficiency but expose you to broader security threats and shared-tenant risks.
- Private cloud deployments provide greater control over security architecture and data sovereignty but require significant investment in security services and monitoring.
- Hybrid cloud architectures blend both, demanding consistent security policies, unified identity and access management, and secure connectivity (e.g., VPN or private link) between on-premises and cloud workloads.
- Multi-cloud strategies amplify complexity by introducing multiple cloud service providers, each with unique security tools, APIs, and compliance frameworks—requiring centralized cloud security posture management and cross-platform event management to detect and remediate risks promptly.
How do IaaS, PaaS, and SaaS service models differ in security requirements?
- IaaS (Infrastructure as a Service): You control the operating systems, applications, and network configuration. Security responsibilities include hardening VMs, configuring network security groups, and managing identity and access management for administrative accounts.
- PaaS (Platform as a Service): The cloud provider secures the underlying infrastructure and platform; you focus on securing your applications and data through encryption, secure coding practices, and integrating security information and event management for application logs.
- SaaS (Software as a Service): The provider manages almost all infrastructure and platform security. Your primary security duties are to configure user access controls, enforce strong authentication policies (MFA, SSO), and govern data lifecycle through classification, backup, and retention policies.
How does virtualization affect cloud security posture?
Virtualization introduces a layer of abstraction that enhances resource utilization but also broadens the attack surface. Hypervisors, virtual switches, and guest operating systems each represent potential vulnerability points. To secure a virtualized cloud environment effectively:
- Implement hypervisor hardening and regular patching to close known exploit paths.
- Enforce VM segmentation and micro segmentation to isolate workloads and limit lateral movement.
- Leverage virtualization-aware security tools—such as virtual firewalls and agent-based intrusion detection—to monitor inter-VM traffic and guest integrity.
- Maintain an updated asset inventory and continuously assess virtual machines through automated vulnerability scans and configuration checks to uphold a strong security posture.
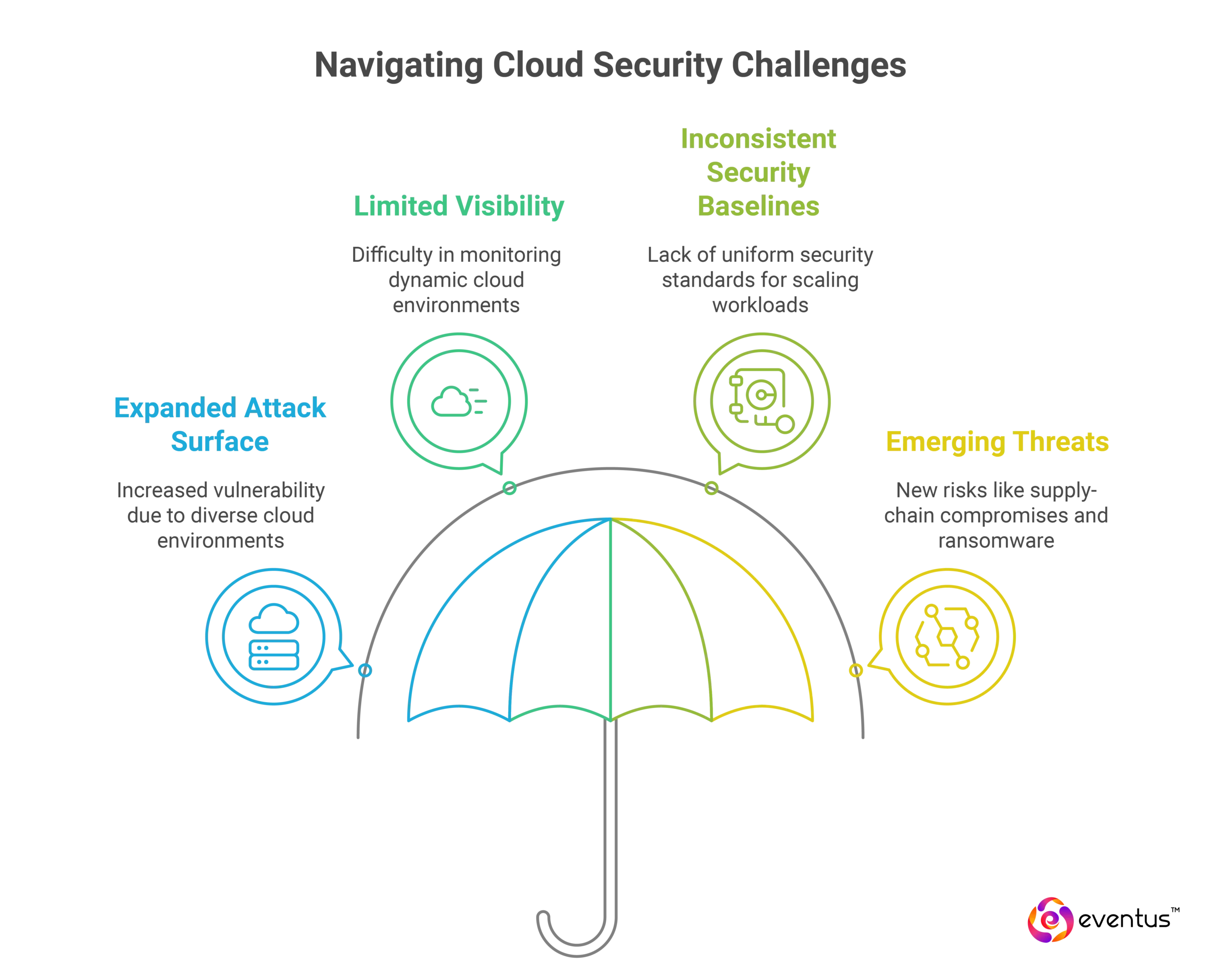
What are common cloud security challenges?
- Expanded attack surface across public, private and hybrid cloud deployments. According to Palo Alto Networks’ State of Cloud Native Security report (2023), 80% of cloud breaches are linked to misconfigurations or IAM failures.
- Limited visibility in rapidly changing cloud environments
- Inconsistent security baselines for dynamic, auto-scaling workloads
- Emerging threats such as supply-chain compromises and cloud-focused ransomware
What factors increase the cloud attack surface?
- Multiple entry points (management APIs, web consoles, third-party integrations)
- Misconfigured resources (open storage buckets, insecure security groups)
- Elastic scaling of instances or containers without standardized hardening
- Use of multiple cloud service providers (e.g., AWS, Google Cloud) under multi-cloud models
Why is visibility often lacking in cloud environments?
- Traditional on-premises security tools can’t fully map to cloud architectures
- Incomplete or decentralized logging and event aggregation
- Rapid provisioning/deprovisioning that outpaces manual inventory controls
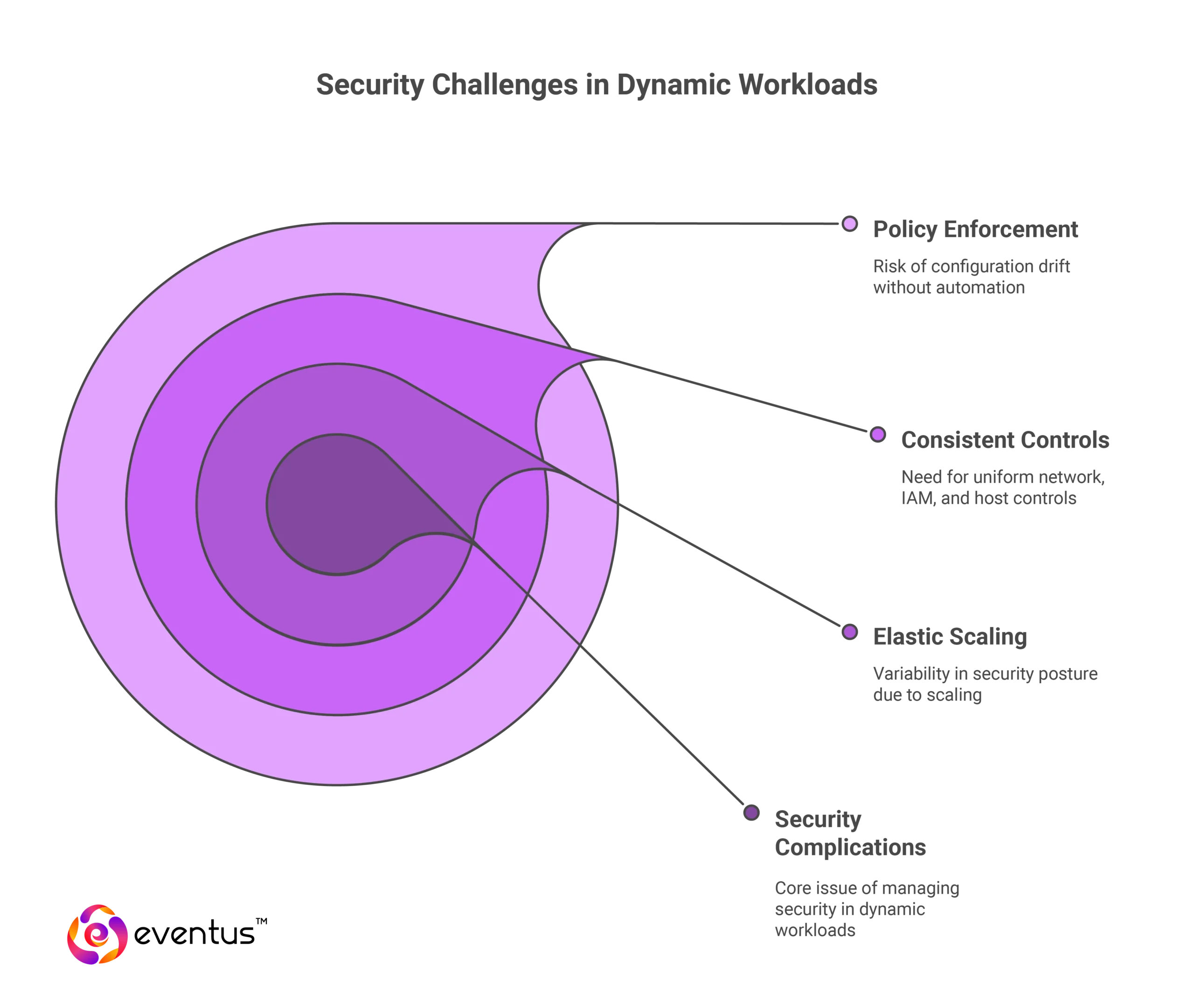
How do dynamic workloads complicate security?
- Elastic scaling introduces variability in security posture
- New compute instances must inherit consistent network, IAM, and host controls
- Lack of automated policy enforcement leads to configuration drift
What risks do supply-chain attacks and cloud ransomware pose?
- Compromised third-party software libraries can infiltrate cloud systems
- Lateral movement across cloud resources enables data exfiltration or code injection
- Ransomware targeting cloud storage can encrypt critical data and disrupt operations