Tired of hearing that AI will magically “fix” your SOC without anyone explaining how? This article cuts through the hype and shows, in practical terms, what an AI driven SOC actually is, how it differs from a traditional SOC, and where AI fits into your existing SIEM, SOAR, EDR, and NDR stack. You’ll see the main AI use cases inside the SOC, the real business benefits, the risks and limitations, why AI will not replace SOC analysts, and which platforms and service models make this all work.
Table of Contents
What is an AI driven SOC?
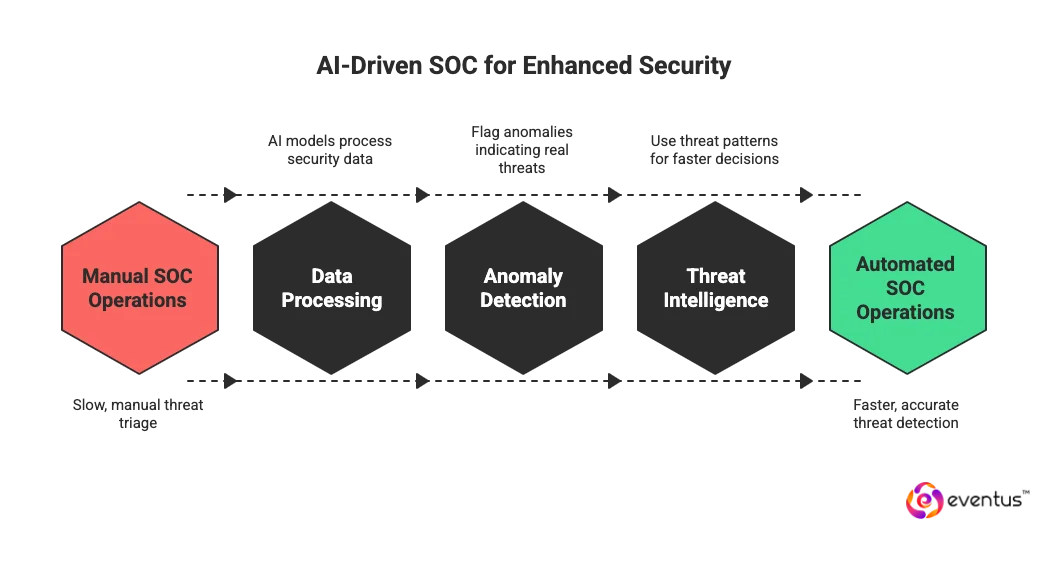
An AI driven SOC is a security operations center that uses AI, machine learning, and automation to run and improve core SOC operations such as threat detection and response, investigation, and incident response. In a typical soc platform, AI models process high volume security data from multiple security tools, correlate security alerts, and prioritize the most important security incidents so security analysts and the wider security team can focus on decisions rather than manual triage.
In an ai-driven soc, analytics and behavioral analytics learn what “normal” looks like for users, devices, and applications, then flag anomalies that may indicate real threats. These ai soc capabilities use threat intelligence, historical attack patterns, and live telemetry to make faster and more accurate threat detection decisions than manual soc operations alone, especially when implemented and fine-tuned by managed soc service providers.
Ready to see an AI driven SOC in action for your environment? Talk to our
How does an AI SOC differ from a traditional SOC?
| Aspect | Traditional SOC | AI SOC (AI-driven SOC) |
| Detection and triage | Relies on rule and signature based detection; soc analysts manually review logs and correlate alerts across tools. | ai-driven socs use machine learning to cluster related events into incidents, rank risk, and automate early triage before analysts see a case. |
| Workflows and automation | Incident response workflow is mostly manual; playbooks exist but are inconsistently followed and hard to scale. | ai-driven security operations treat each workflow as an automated pipeline, using soc solutions to automate containment, enrichment, and evidence collection. |
| Use of data and context | Security data is fragmented across tools; correlation depends on individual analyst skill and ad hoc queries. | Central engines continuously learn from combined security data, threat intelligence, and past incidents to generate context rich, prioritized recommendations. |
| Role of SOC analysts | soc analysts spend significant time on repetitive tasks such as dismissing false positives and performing basic enrichment. | Analysts focus on higher value investigation and decision making, validating AI output and refining automation and workflow logic. |
| Operational efficiency | Scaling operations mainly requires adding more people, which increases cost and complexity. | ai-driven security uses automation to scale without a linear headcount increase, so the same team can handle more complex and frequent attacks. |
| Consistency of response | Response quality varies by analyst experience; runbooks may be skipped under pressure. | ai-driven security operations enforce consistent playbook execution, with AI orchestrating standard steps and humans handling exceptions. |
| Use of advanced techniques | Limited use of advanced analytics; mostly dashboards, rules, and basic correlation queries. | Uses behavioral analytics and other AI techniques to detect subtle patterns and anomalies that traditional methods miss. |
| Adoption of generative AI | Rarely uses generative ai beyond basic reporting templates. | May embed generative ai to summarize investigations, explain attack paths, and suggest next steps, while humans retain final authority in cybersecurity decisions. |
What are the key components and architecture of an AI driven SOC?
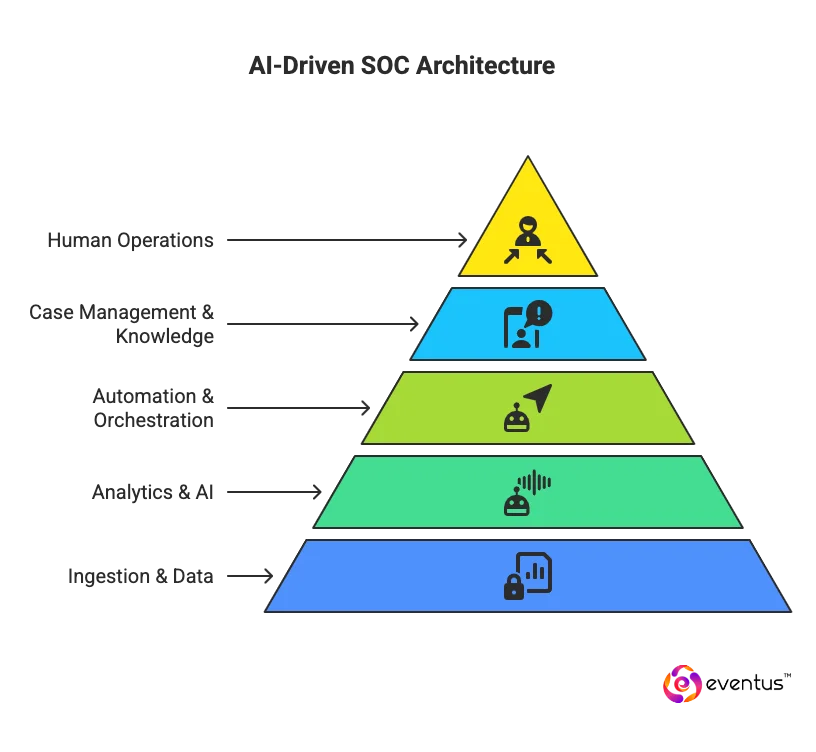
An AI driven SOC is architected as a set of tightly connected layers that turn raw telemetry into ranked, automated action while keeping humans in control, and the best soc as a service offerings replicate this model for organizations that outsource their SOC.
- At the ingestion and data layer, a modern SOC architecture collects security data (attribute) from existing security tools (value) such as EDR, firewalls, email security, and cloud platforms (predicate: into a normalized lake). This enables security teams to run consistent analytics instead of chasing disconnected logs across today’s SOC.
- At the analytics and AI layer, ai-driven soc tools apply ai-driven behavioral analytics and other ai capabilities to learn normal behavior, correlate related events, and score risk. Here, ai in soc (entity) uses machine learning (attribute) to transform soc workflows (value) from alert level noise into incident level insight (predicate: by clustering and ranking events).
- At the automation and orchestration layer, soc automation uses playbooks and ai-driven automation to automate standard response steps, such as isolating endpoints or resetting credentials. Agentic ai and ai soc agents can act as a soc co pilot, executing low risk actions while routing high impact decisions to human analysts.
- At the case management and knowledge layer, the ai-powered soc links incidents, evidence, and outcomes in a central system. This layer integrates threat intelligence so ai tools can reuse past investigations, improving soc performance and making ai-driven soc solutions more accurate over time.
- At the human operations layer, soc teams and the ai soc analyst role remain the final authority. AI enhances efficiency by preparing investigations and recommendations, but soc teams must tune models, govern ai integration, and decide how far to let ai automate within the soc.
What are the main use cases of AI in the SOC?
AI in the SOC is used to offload repetitive work, improve detection quality, and speed up response across the soc landscape. In a mature ai-driven security operations center, including those run by soc as a service providers in USA, the main use cases are:
- Automated alert triage and incident grouping
AI systems in ai soc platforms group related security alerts into single incidents and rank risk, so ai to automate triage reduces noise and helps soc analysts focus on high impact cases. - Behavioral analytics and anomaly detection
ai-powered soc tools learn normal behavior for users and assets, then flag anomalies, so ai in cybersecurity detects subtle attacks that rule based monitoring in today’s SOC would miss. - Phishing and email threat detection
For phishing attacks, ai-driven tools analyze content, links, and sender behavior together, enabling an ai-augmented soc to quarantine high risk emails automatically and cut manual review. - Threat intelligence enrichment and correlation
AI agents continuously map internal events to threat intelligence, so leveraging AI enriches incidents with likely TTPs and campaigns instead of forcing humans to pivot across multiple sources. - Automated response and orchestration
In an autonomous soc style setup, ai automation executes predefined low risk actions (for example, isolate an endpoint), while a soc co-pilot pattern keeps humans in control of critical decisions. - Proactive threat hunting and pattern discovery
Advanced AI scans historical security data to surface rare patterns and long running attack paths, which transforms SOC operations from purely reactive monitoring into continuous hunting. - Case summarization and analyst assistance with gen AI
gen ai summarizes investigations, explains attack chains, and suggests next steps, so AI assistance reduces cognitive load and ai is transforming how quickly analysts can reach decisions. - Operational analytics and SOC performance insights
AI-driven tools model backlog, MTTR, and bottlenecks within the SOC, turning soc challenges into measurable soc benefits such as lower false positives and faster resolution times.
about applying these AI-driven SOC use cases in your environment
What are the business benefits of an AI driven SOC?
An AI driven SOC delivers business value by turning security operations from a cost center into a measurable risk-reduction and resilience engine, especially when designed and operated by a trusted, enterprise-grade managed security service provider that offers AI-driven SOC-as-a-service across cloud and on-premises environments, with 24x7 coverage and continuous optimization.
- Stronger risk reduction per dollar spent
In a mature soc model, ai socs (entity) process high-volume security events (attribute) with fewer human hours (value), so the benefits of AI (predicate: lower cost per investigated incident) are directly visible in budget and risk reports. - Faster detection and response to critical incidents
For a critical SOC, security’s AI SOC uses top AI techniques to correlate signals and prioritize incidents, cutting mean time to detect and respond. That reduces the real business impact of ransomware, fraud, and data breaches, not just the number of alerts closed. - Scalable operations without linear headcount growth
A large enterprise SOC relies on automation and AI to enhance throughput so the same team can handle more alerts, assets, and regions. This prevents security performance from collapsing when the business grows faster than hiring. - Consistent decision making and fewer human errors
When ai act logic codifies playbooks, the role in SOC for analysts shifts from “remember every step” to “validate AI suggestions.” This improves consistency in containment actions, especially during high-pressure incidents. - Better executive visibility and metrics
AI to enhance analytics gives leadership clear, quantifiable metrics (for example, incident volume by type, exposure windows, MTTR by business unit). That lets boards and CISOs align security investments with real business risk instead of gut feel. - Improved employee and customer trust
As ai continues to evolve, AI driven SOCs can detect and stop more attacks before they disrupt services. Fewer major incidents mean fewer outages, less data exposure, and higher trust from customers, partners, and regulators.
What Challenges, Limitations and Risks come with AI in the SOC?
AI in the SOC introduces several concrete challenges, limitations, and risks that SOC leaders must manage explicitly.
- Model bias and blind spots
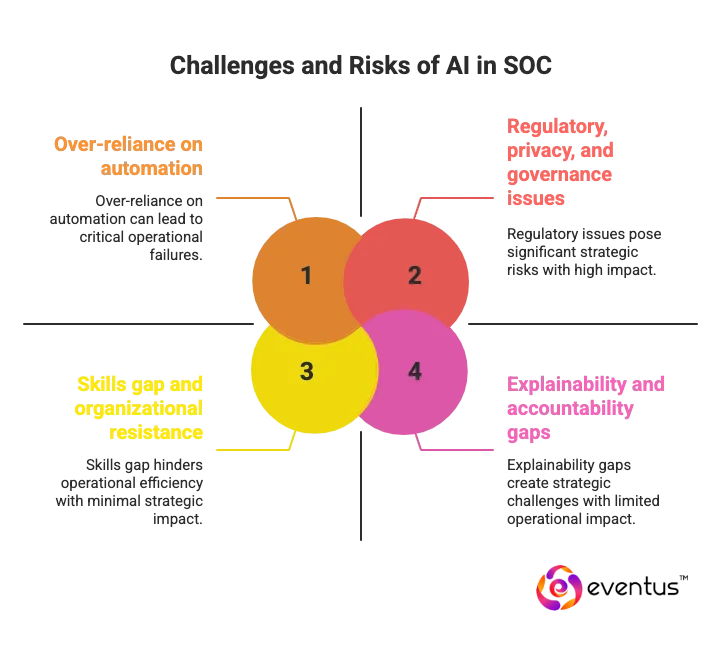
Even the best AI models (entity) learn from historical security data (attribute) that may be incomplete or skewed (value), so their detections (predicate: can overfit to known patterns and miss novel attack paths). This creates a false sense of coverage in both in-house SOCs and soc as a service environments if teams stop running independent threat hunting. - Over-reliance on automation
When a SOC delegates too many decisions to AI, analysts may stop questioning outputs, approving actions on “auto-pilot.” In a high-stakes environment like incident response, automation errors can block legitimate business activity or overlook stealthy intrusions. - Data quality and integration risks
If logs are missing, inconsistent, or poorly normalized, AI systems will propagate those errors into their correlation and scoring. Poor data engineering in the pipeline (entity) becomes a root cause (attribute) of unreliable AI detections and noisy triage (value). - Adversarial and model-evasion attacks
Attackers can deliberately craft activity that avoids AI-based detections, for example by mimicking normal user behavior or slowly spreading actions over time. AI systems themselves become targets, not just tools, which raises a new attack surface for the SOC. - Explainability and accountability gaps
Complex models often cannot explain in plain language why they flagged a session or user. When an action disrupts business—such as blocking a high-value account—weak explainability makes it harder for SOC leaders to justify decisions to auditors, regulators, and executives. - Regulatory, privacy, and governance issues
AI-driven monitoring can intersect with employee privacy, data residency, and sector-specific regulations. Without clear governance, retention policies, and access controls, AI in the SOC can increase legal and compliance risk instead of reducing it. - Skills gap and organizational resistance
SOC teams may lack the skills to evaluate models, tune thresholds, and validate outcomes. If analysts and engineers do not trust AI outputs, they either ignore them or override them, undermining the value of the entire system while still paying the cost.
Will AI replace SOCs or SOC analysts?
AI will not replace SOCs or SOC analysts. It will replace repetitive work: alert triage, correlation, and basic enrichment. Effective SOCs use AI as a co-pilot to scale detection and response, while humans handle judgment, edge cases, business context, and accountability.
How do SIEM SOAR EDR and NDR fit into an AI driven SOC?
| Tool | Primary role in an AI driven SOC | What AI adds |
| SIEM | Centralizes and normalizes logs and alerts into one data lake for the SOC. | Uses AI to correlate events, score risk, and group related alerts into incidents. |
| EDR | Monitors and controls endpoint activity (processes, files, behavior). | Uses AI to distinguish normal vs malicious behavior and trigger auto-containment. |
| NDR | Observes network traffic for lateral movement and exfiltration patterns. | Uses AI to detect stealthy network anomalies and link them to endpoint and user activity. |
| SOAR | Orchestrates playbooks and response actions across tools and teams. | Uses AI to prioritize cases, recommend next steps, and automate low-risk workflows. |
Which platforms tools and service models enable an AI driven SOC
An AI driven SOC is enabled by a stack of cloud-native platforms, AI enhanced tools, and service models that together deliver 24x7 detection and response without relying only on internal headcount.
The following points are related to platforms, tools, and service models that enable an AI driven SOC.
- AI native SOC and XDR platforms – unify telemetry, analytics, and automation into one AI driven decision layer.
- SIEM with UEBA – centralize logs and use behavior analytics to flag anomalies at scale.
- AI powered EDR, NDR, and identity tools – give deep endpoint, network, and access visibility for advanced detection.
- SOAR and automation engines – execute AI ranked playbooks for enrichment and response.
- Security data lakes – store long term telemetry to train and tune models.
- Threat intelligence and attack surface platforms – enrich detections with external context.
- SOC co pilot assistants – use gen AI to summarize cases and suggest actions.
- SOCaaS, MDR, and co managed SOC – deliver AI driven SOC outcomes as managed services.
FAQs
FAQ 1 – Is an AI driven SOC only suitable for large enterprises?
No. An AI driven SOC benefits any organization with continuous security monitoring, even mid sized firms with small security teams. A 24x7 environment with growing cloud usage and frequent security incidents (entity) gains the most value (attribute) from AI assisted detection and response (value) because it offsets limited headcount (predicate: by automating heavy analysis).
FAQ 2 – What data foundation do we need before adopting an AI driven SOC?
You need clean, centralized security telemetry from core systems: identity, endpoints, network, cloud, and email. An organization’s SOC data pipeline (entity) should at minimum normalize logs and alerts (attribute) into a SIEM or data lake (value) so AI models (predicate: can reliably learn baselines and detect anomalies).
FAQ 3 – Do we have to replace our existing SIEM and EDR to use AI in the SOC?
Not necessarily. Many AI driven SOC platforms and co pilot tools integrate with existing SIEM, EDR, and NDR, using them as data sources and enforcement points. The current security stack (entity) often becomes the control plane (attribute) that AI (value) orchestrates and augments (predicate: instead of being fully replaced).
FAQ 4 – How quickly can we expect measurable improvements from an AI driven SOC?
Most teams see early gains in noise reduction and triage efficiency once AI models finish initial training, typically within a few weeks of steady data flow. A SOC program (entity) usually needs 60–90 days (attribute) to show clear improvements in metrics like mean time to detect and mean time to respond (value) after tuning (predicate: based on real incidents).
FAQ 5 – How should we measure the ROI of an AI driven SOC?
Track hard metrics: reduction in false positives, faster incident closure, fewer critical breaches, and lower overtime or staffing pressure. A security program (entity) can express ROI (attribute) as avoided incident cost and analyst hours saved (value) per year (predicate: compared with the pre AI baseline).