This article explores zero-day vulnerabilities—unpatched software flaws exploited before developers are aware. It distinguishes between vulnerabilities, exploits, and attacks; explains exploit mechanisms and lifecycle stages; outlines detection and response strategies; and stresses proactive defenses like WAFs, ASM, input validation, and behavior analytics. Real-world examples, including Indian cases like Pegasus and CERT-In attacks, underscore the urgency of improving zero-day readiness through vulnerability scanning, incident response, and continuous system updates.
Table of Contents
How to define zero day vulnerability?
Zero day vulnerability meaning refers to a security flaw in software or hardware that is unknown to the party responsible for fixing it—typically the vendor or developer—and for which no official patch or fix exists at the time it is discovered or exploited by attackers.
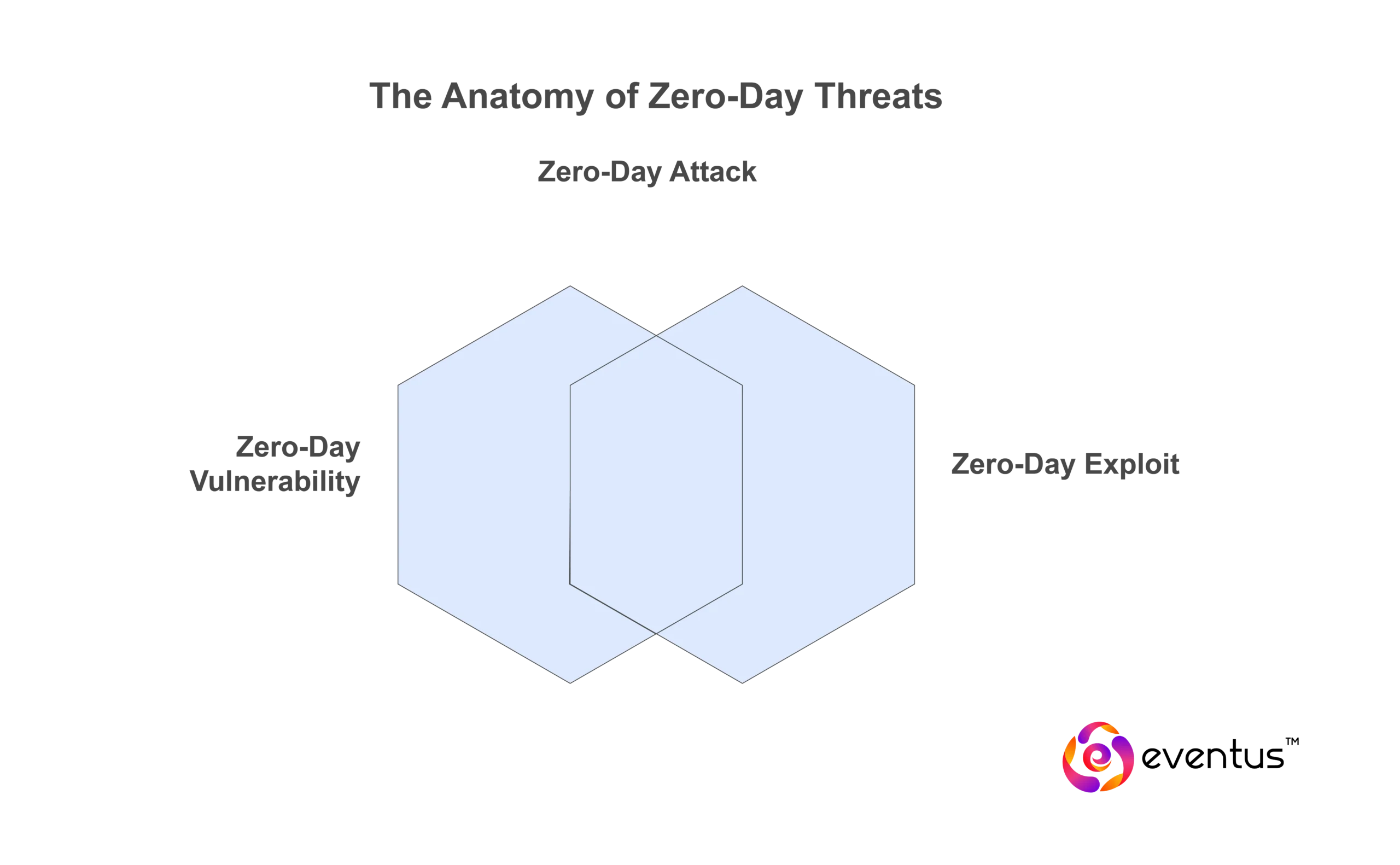
What is the difference between zero-day vulnerability, exploit, and attack?
These three terms are interrelated but distinct:
-
Zero-Day Vulnerability:An unknown or unpatched software flaw that can be targeted. Google’s Project Zero, which disclosed over 58 zero-day vulnerabilities in 2022, plays a keyrole in early detection and disclosure.
-
Zero-Day Exploit:A piece of malicious code or method used by attackers to take advantage of the zero-day vulnerability. According to FireEye's Zero-Day Report (2023), 50% of zero-day exploits targeted government and defense institutions globally.
-
Zero-Day Attack:The actual cyber incident where the exploit is used to compromise a system, often resulting in a data breach, or endpoint compromise.
For example, in the Stuxnet incident, multiple zero-day vulnerabilities in Microsoft Windows were exploited to deliver malware targeting industrial control systems—a clear case of a zero-day attack leveraging several zero-day exploits.
How Does a Zero-Day Exploit Work?
A zero-day exploit works by targeting a security flaw in software that is unknown to the vendor and unprotected by existing security software. Here's how threat actors typically leverage such exploits:
- A malicious actor identifies or obtains a zero-day vulnerability through independent discovery, vulnerability marketplaces, or illicit channels.
- Custom malicious code is created to exploit the vulnerability before it’s patched—often bypassing endpoint detection or antivirus tools.
- The exploit is deployed via phishing, drive-by downloads, or malicious websites to gain access to the vulnerable system.
- Once inside, attackers may steal data, install zero-day malware, or pivot deeper into the network before defenders are aware of the vulnerability.
Leading cybersecurity companies provide specialized tools and services—such as SIEM platforms, threat intelligence feeds, and zero-day exploit detection solutions—that enhance an organization's ability to identify and mitigate emerging threats before they cause damage.
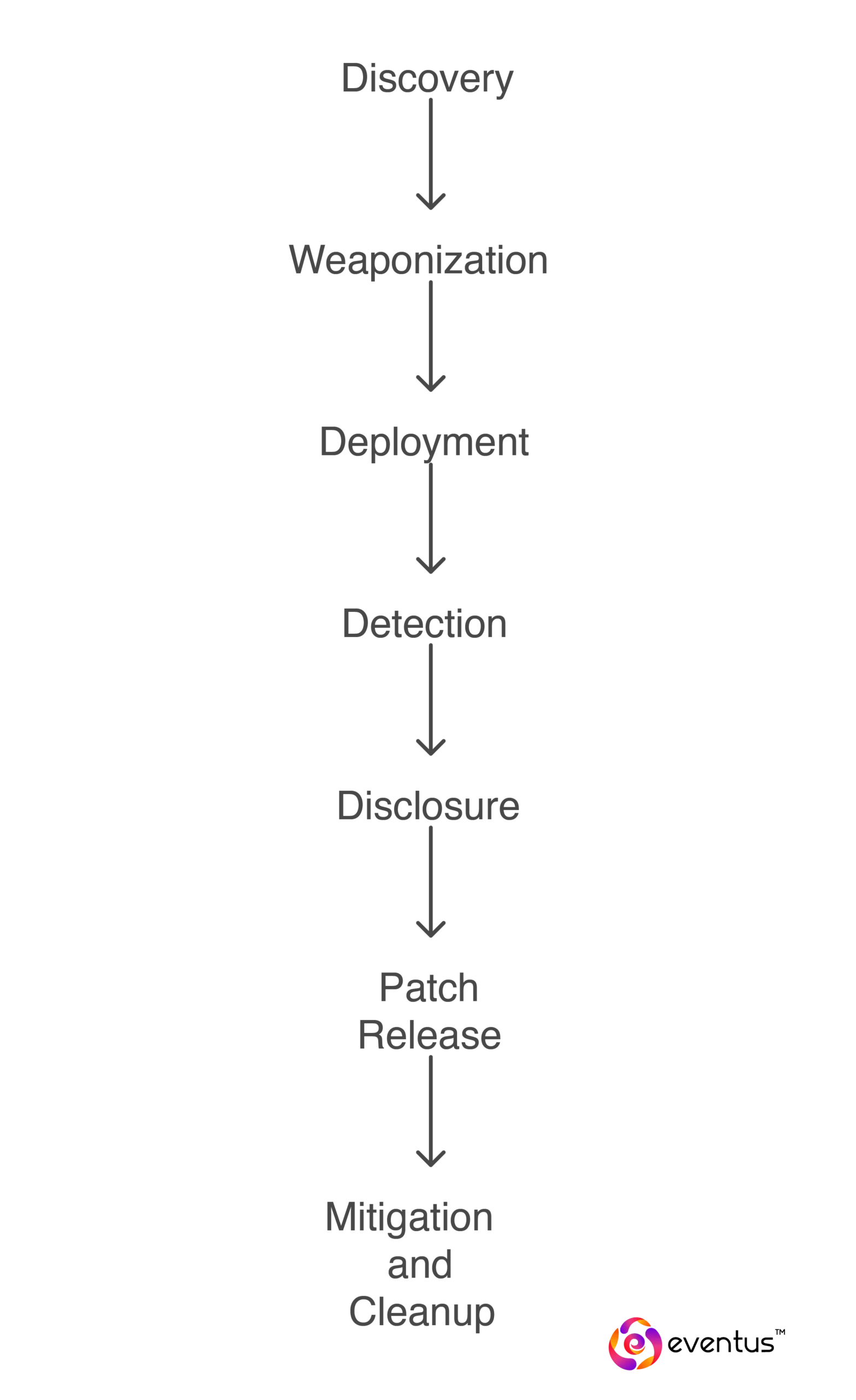
What is the Lifecycle of a Zero-Day Exploit?
The zero-day lifecycle outlines the stages from the discovery of the vulnerability to its resolution. These stages include:
1.Discovery –A hacker, researcher, or insider discovers a zero-day vulnerability that is unknown to the public or vendor. CERT-In issued an alert in August 2022 warning of zero-day attacks targeting government portals.
2.Weaponization – The flaw is used to develop a working exploit, often embedded in malware.
3.Deployment – The exploit is launched against targets before a patch is available, allowing threat actors to take advantage.
4.Detection – Security teams or third parties detect unusual activity that may indicate a zero-day attack.
5.Disclosure – The vulnerability is disclosed to the vendor or made public; this may happen responsibly (coordinated disclosure) or irresponsibly.
6.Patch Release – The software developer releases a security patch to fix the vulnerability.
7.Mitigation and Cleanup – Organizations apply patches and initiate incident response to contain and remediate damage.
What is the Window of Vulnerability?
The window of vulnerability includes not only the zero-day period, but also the time after a patch is released but not yet applied by all users. This means:
- Even after a security patch is available, systems remain at risk until it is installed.
- Poor patch management practices widen this window, giving attackers more time to exploit vulnerabilities.
- Attackers often reverse-engineer patches to identify and exploit the same flaw in unpatched systems.
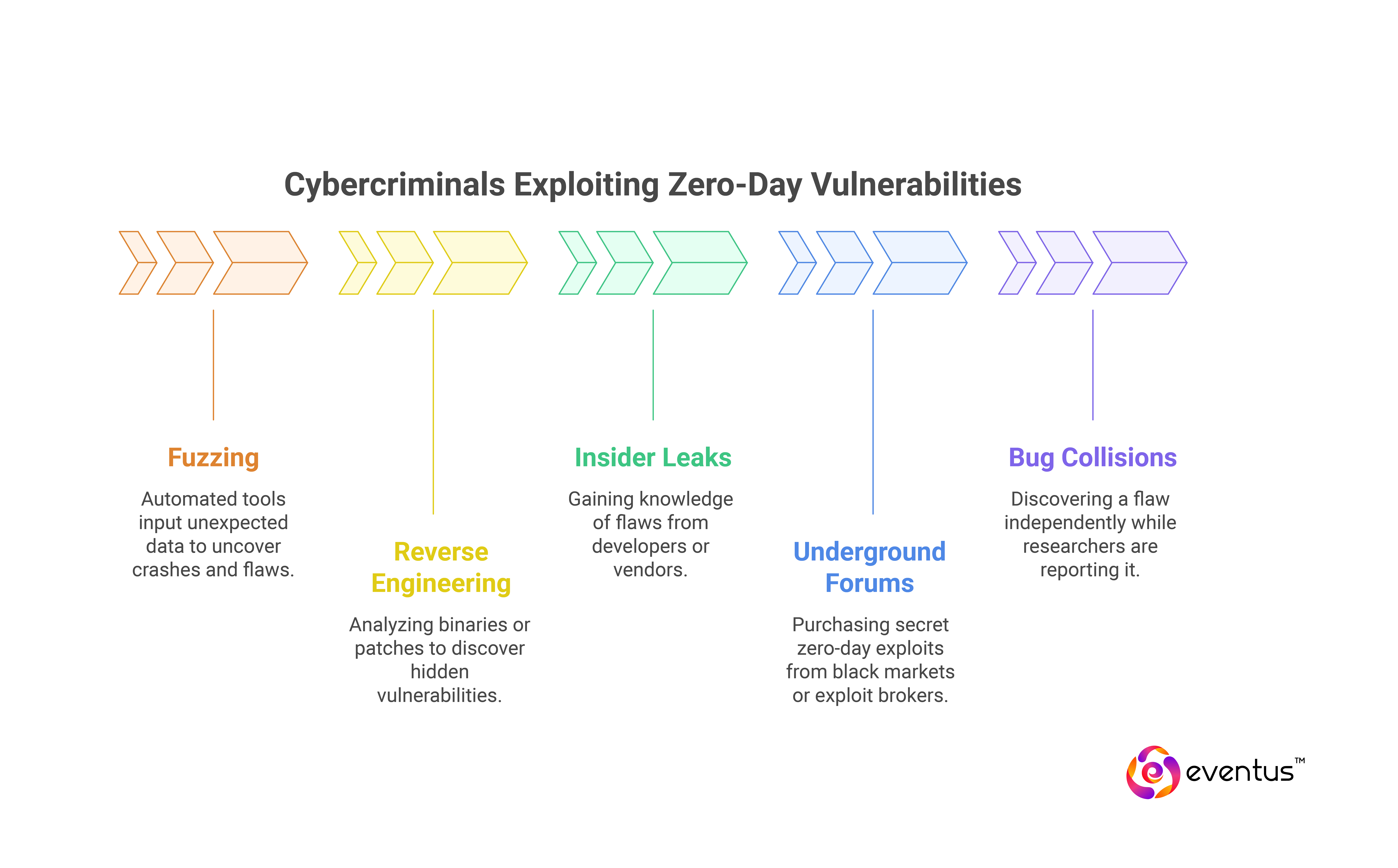
How Do Cybercriminals Find and Exploit Zero-Day Vulnerabilities?
Cybercriminals use various methods to exploit zero-day vulnerabilities, including:
- Fuzzing – Automated tools input unexpected data into software to uncover crashes and flaws.
- Reverse Engineering – Analyzing binaries or patches to discover hidden vulnerabilities.
- Insider Leaks – Gaining knowledge of flaws from developers or vendors.
- Underground Forums – Purchasing secret zero-day exploits from black markets or exploit brokers.
- Bug Collisions – Discovering a flaw independently while researchers are reporting it for responsible disclosure
Why are zero-day vulnerabilities significant?
Zero-day vulnerabilities are significant due to the following reasons:
- No immediate patch exists, increasing the likelihood of successful exploitation.
- They allow malicious actors to bypass traditional security measures such as antivirus and endpoint detection.
- They are commonly used in advanced persistent threats (APTs), targeted attacks, and espionage campaigns.
- Exploiting a zero-day vulnerability can lead to data breaches, system takeover, ransomware deployment, or theft of sensitive information.
Given their severity, organizations must proactively reduce the risk by:
- Implementing vulnerability scanning and attack surface management tools.
- Maintaining robust patch management and incident response protocols.
- Staying informed through threat intelligence feeds and collaborations with cybersecurity researchers.
What are the immediate steps to take after discovering a zero-day vulnerability?
Once a potential zero-day is identified, organizations must act fast to mitigate zero-day threats and avoid a data breach. Key actions include:
- Isolate vulnerable endpoints to prevent the exploit from spreading across the network.
- Initiate incident response procedures, ensuring the security team is fully engaged.
- Assess the scope of impact—determine whether attackers were able to gain access, steal data, or deploy malicious code.
- Preserve forensic evidence for future analysis and to understand how the attacker exploited the vulnerability.
- Apply temporary mitigation measures, such as disabling vulnerable components, restricting permissions, or blocking malicious IPs, until a patch is available.
- Notify internal stakeholders and prepare for coordinated external disclosure.
How Can Organizations Prevent Zero-Day Exploits and Attacks?
Preventing a zero-day attack requires a proactive and layered cybersecurity approach that compensates for the unknown nature of the vulnerability. Since these flaws are typically unknown to the vendor at the time of exploitation, the objective isn't always to eliminate the threat entirely but to reduce the risk and impact when a zero-day exploit occurs.
Organizations often rely on a Security Operations Center (SOC) to centralize threat monitoring, incident detection, and response.
What is SOC? A SOC is a dedicated facility or team responsible for continuously analyzing security data, managing alerts, and coordinating responses to cyber threats—including zero-day attacks. By integrating SOC capabilities with real-time threat intelligence and behavioral analytics, organizations improve their ability to detect and contain zero-day exploits before they escalate.
For organizations lacking in-house security expertise, partnering with a MSSP full form being, a Managed Security Service Provider (MSSP) can offer 24/7 monitoring, advanced threat detection, and rapid response capabilities. MSSPs often operate their own SOC infrastructure, enabling even mid-sized businesses to benefit from enterprise-grade protection against zero-day exploits and other sophisticated cyber threats.
Many SOCs and MSSPs utilize Security Information and Event Management (SIEM) systems to aggregate and analyze log data across networks, endpoints, and applications. SIEM platforms play a critical role in detecting anomalies associated with zero-day exploits by correlating events in real time and generating alerts for suspicious behavior.
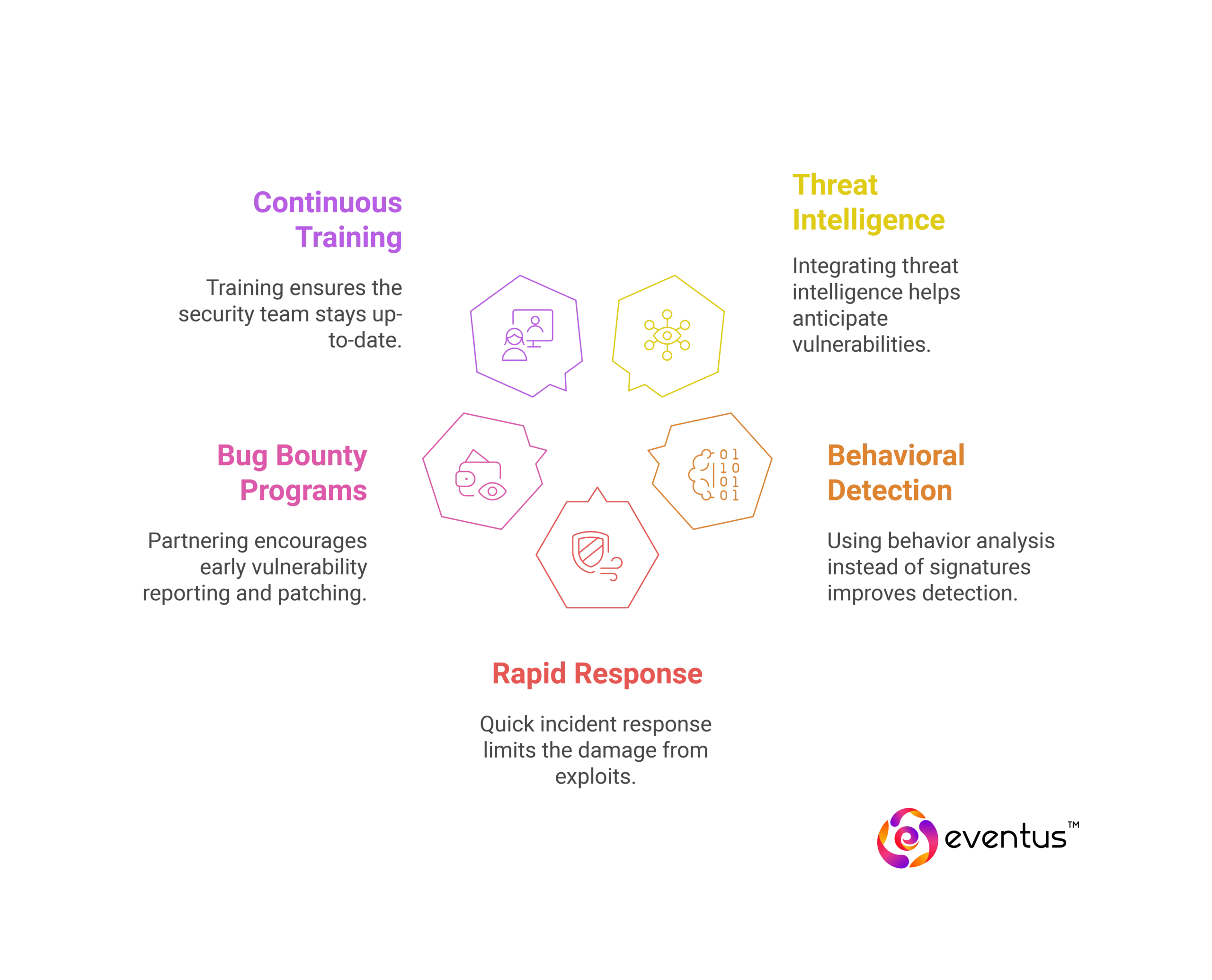
Key strategies for zero-day attack prevention include:
- Threat intelligence integration to stay ahead of emerging vulnerabilities
- Behavioral-based detection instead of relying solely on signature-based antivirus
- Rapid incident response workflows to contain exploitation
- Partnering with bug bounty programs and initiatives like the Zero Day Initiative to encourage early vulnerability disclosure
- Continuous training of the security team to adapt to new exploit tactics
1. Patch management helps reduce risk
While patch management cannot resolve undiscovered vulnerabilities, it ensures that known vulnerabilities are not left unpatched, thereby:
- Eliminating attack vectors that could otherwise be chained with zero-day exploits
- Reducing lateral movement opportunities across a vulnerable system
- Accelerating time-to-fix when a discovered vulnerability becomes public
- Coordinating with software vendors to deploy emergency security patches once available
2. Vulnerability Scanning and its working
Vulnerability scanning identifies known security flaws across systems and software configurations. It does not detect secret zero-days, but it helps:
- Detect misconfigurations that could be exploited in conjunction with a zero-day exploit
- Establish a baseline for vulnerability management
- Prioritize remediation based on critical vulnerability scoring
- Support compliance and audit readiness
3. Input Validation helps mitigate zero-day threats
Input validation defends against entire classes of exploits by:
- Preventing malicious payloads from reaching back-end systems
- Blocking SQL injections, buffer overflows, and command injection vectors—common targets of zero-day software flaws
- Acting as a first line of defense when a vulnerability exists in a parsing or rendering function
4. Role of a Web Application Firewall (WAF)
A WAF provides virtual patching and exploit mitigation by:
- Filtering malicious traffic targeting web applications
- Analyzing HTTP requests for anomalies that may exploit zero-day vulnerabilities
- Blocking known malicious actor IPs based on real-time threat intelligence feeds
- Complementing application-level defenses even before the software developer releases a fix
5. Attack surface management (ASM) assisting in zero-day defense
ASM tools help reduce exposure to potential zero-day attacks by:
- Mapping and monitoring all public-facing assets
- Identifying shadow IT and unauthorized deployments
- Alerting security teams when new endpoints or applications are exposed to the internet
- Allowing teams to proactively secure overlooked vectors that malicious actors often target
6. Impact of User Behavior Analytics on zero-day detection
User behavior analytics (UBA) leverages baseline activity data to detect deviations that may indicate a zero-day attack in progress:
- Spotting abnormal login patterns, file access, or privilege escalation
- Detecting when a vulnerability is being exploited without relying on known signatures
- Allowing for faster containment before a full data breach or lateral movement occurs
7. Role of Statistical Anomaly Detection play in prevention
Unlike signature-based detection, statistical anomaly detection looks for:
- Changes in network traffic, CPU usage, or system calls that signal exploit behavior
- Behavior consistent with exfiltration, privilege escalation, or malware deployment
- Zero-day lifecycle activity patterns that deviate from system basel
8. Frequency of system updates
Although zero-day exploits typically bypass standard update schedules, regular system updates are still critical:
- Monthly patch cycles should be enforced for known vulnerabilities
- Emergency out-of-band updates should be applied within 24–48 hours of a disclosed critical zero-day
- Firmware and operating system updates should not be neglected—many exploited four different zero-day vulnerabilities involved outdated firmware
What Are Some Real-World Examples of Zero-Day Attacks?
India has witnessed a growing number of zero-day attacks in recent years, underscoring the need for enhanced cybersecurity readiness, better vulnerability management, and faster response strategies. Below are notable Indian examples of zero-day vulnerabilities and exploits that impacted both private and public-sector infrastructure.
- Pegasus Spyware (2019, 2021): Zero-day vulnerabilities in WhatsApp and iOS were exploited to silently install Pegasus spyware on Indian journalists’ and activists’ phones, allowing full device surveillance before patches were released.
- CERT-In Government Portals (2020–2022): Critical zero-day flaws in Indian government websites and e-services allowed threat actors to inject malicious code and exfiltrate data before patches were deployed.
- Quick Heal Antivirus Exploit (2022): A critical RCE vulnerability in Quick Heal antivirus was exploited to target Indian SMBs, remaining undetected for months until responsibly disclosed and patched.
- BSNL Router Firmware Exploit (2019): Firmware-level zero-day vulnerabilities in BSNL routers enabled attackers to take remote control of devices, affecting thousands of users across rural India.
- APT36 Targeting Indian Defense: APT36 used malicious Word documents exploiting zero-day flaws to access Indian defense systems, evading detection through sophisticated spear-phishing techniques.