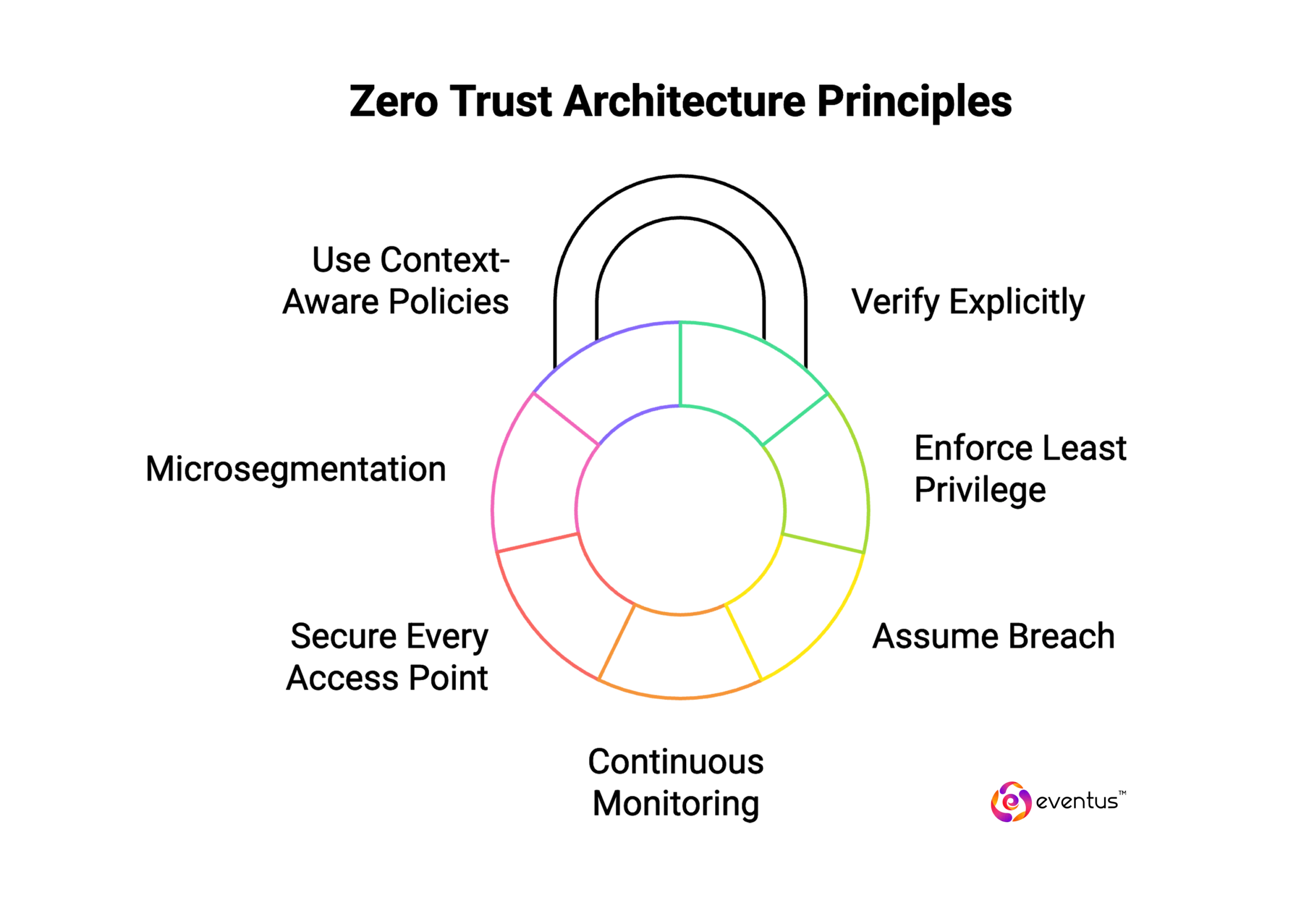Zero Trust Architecture has emerged as a modern cybersecurity framework that challenges the outdated perimeter-based security model. This article explores what Zero Trust Architecture is, how it works, and its core principles. It outlines the foundational pillars, implementation steps, benefits, and the role of devices and tools in enforcing Zero Trust. The article also examines its relation to network security architecture and highlights essential elements critical to building a Zero Trust environment. Designed for organizations seeking stronger security, it offers a comprehensive overview grounded in proven frameworks and strategies.
Table of Contents
What is Zero Trust Architecture?
Zero Trust Architecture (ZTA) is a modern security model that fundamentally redefines how organizations approach network security. Unlike the traditional network approach that implicitly trusts users and devices inside the network perimeter, Zero Trust operates on the core principle of “never trust, always verify.” It assumes that threats can originate from both outside and within the network, and therefore, every access request must be explicitly verified before being granted.
This security architecture shifts from perimeter-based defenses to a model centered around continuous verification, least privilege, and granular access control. It treats every user and device as potentially compromised, requiring proof of identity, device posture, and compliance before permitting network access.
How does Zero Trust Architecture work?
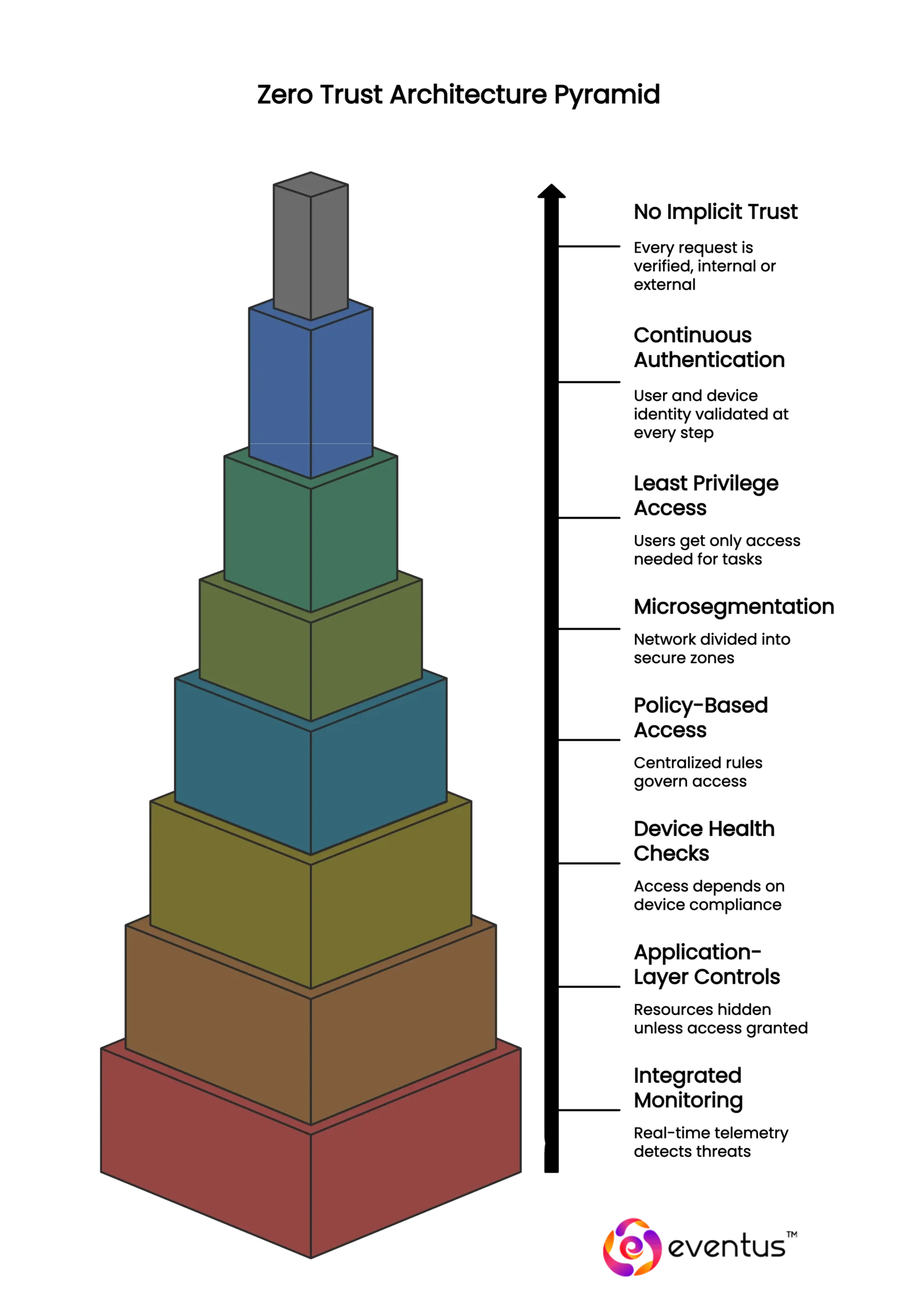
ZTA continuously validates every user and device before granting network access—regardless of location. It enforces least privilege, uses real-time access control, and reduces the attack surface by segmenting resources and monitoring traffic dynamically.
Here’s how it works:
- No implicit trust – Every request is verified, whether internal or external.
- Continuous authentication – User and device identity are validated at every step.
- Least privilege access – Users get only the access needed to perform their tasks.
- Microsegmentation – Network is divided into secure zones to prevent lateral movement.
- Policy-based access – Centralized rules govern who can access what and when.
- Device health checks – Access depends on device posture and compliance status.
- Application-layer controls – Resources are hidden unless access is explicitly granted.
- Integrated monitoring – Real-time telemetry helps detect and respond to threats.
This zero trust model combines identity, context, and continuous validation to enforce a strong security posture. It is ideal for protecting cloud services, remote users, IoT devices, and complex cybersecurity environments. Supported by frameworks like NIST, ZTA helps organizations implement Zero Trust effectively across cloud environments and hybrid infrastructure.
What are the core principles of Zero Trust Architecture?
The core principles of Zero Trust Architecture form the foundation of a modern security approach that eliminates implicit trust and enforces continuous verification. Unlike perimeter-based models, the Zero Trust security model treats every access request as potentially hostile, regardless of origin. These principles guide organizations in implementing a Zero Trust strategy that enhances visibility, control, and risk reduction across the zero trust network.
Key principles include:
- Verify Explicitly: All user access requests must be authenticated and authorized using dynamic data such as identity, device, location, and behavior.
- Enforce Least Privilege: Access is granted strictly on a need-to-know basis, minimizing exposure to sensitive assets.
- Assume Breach: Operate with the assumption that a breach has already occurred or will occur. This ensures defensive measures are active even for internal traffic.
- Continuous Monitoring: Security teams must constantly evaluate trust signals and adjust access in real time based on evolving risks.
- Secure Every Access Point: Apply security measures to every user, device, application, and data source—whether on-premises or in the cloud.
- Microsegmentation: Break the zero trust network into smaller zones to limit the lateral movement of attackers.
- Use Context-Aware Policies: Access decisions are based on a combination of contextual signals such as device compliance, workload sensitivity, and behavioral anomalies.
These Zero Trust principles support a proactive security approach that aligns with today’s dynamic threat landscape. By adopting a Zero Trust solution, organizations empower their security teams to reduce attack surfaces, control user access, and improve resilience across cyber and hybrid environments. The result is a more adaptive and defensible architecture driven by verification, policy enforcement, and ongoing assessment.
What are the benefits of implementing Zero Trust Architecture?
Implementing Zero Trust Architecture offers a significant shift from outdated perimeter-based defenses to a dynamic. This model assumes that no user, device, or system—internal or external—should be implicitly trusted without continuous verification.
The benefits of Zero Trust extend beyond technical gains to organizational resilience, compliance, and operational efficiency. By using a Zero Trust Architecture, enterprises align with the main principles behind Zero Trust while enabling robust security across evolving IT environments.
Key benefits include:
- Enhanced security through continuous verification and strict security access controls
- Microsegmentation that replaces traditional network segmentation, reducing lateral movement
- Improved policy enforcement, making it harder for users to circumvent security
- Reduced attack surface by validating identity, device, and context for every request
- Stronger compliance with mandates like federal Zero Trust and NIST-aligned Zero Trust framework
- Secure hybrid and multi-cloud environments with consistent security protocols
- Protection of high-value assets using hardware-based security and contextual access control
- Scalable maturity across the zero trust enterprise, adaptable to different use cases for Zero Trust
As Zero Trust provides continuous protection and visibility, it supports a more adaptive, future-proof defense model. For Zero Trust organizations, this approach is not just a tool—it’s a strategic shift in how trust is a security framework and how policies and security controls are applied at every layer.
What are the steps to implementing Zero Trust Architecture?
Implementing Zero Trust Architecture requires a structured transition from implicit trust to a model based on continuous verification and least-privilege access.
Here are the key steps in applying the Zero Trust approach:
- Identify users, devices, and data flows: Map all users, endpoints, applications, and traffic patterns within the environment.
- Define the protect surface: Focus on securing critical assets like sensitive data, apps, and infrastructure rather than the entire network.
- Implement Zero Trust Network Access (ZTNA): Replace perimeter-based access with identity-aware, encrypted, policy-controlled access.
- Enforce least privilege access: Grant users and devices only the permissions necessary for their roles and nothing more.
- Establish context-based policies: Set rules based on identity, location, device posture, time, and risk level.
- Monitor and analyze all activity: Use real-time monitoring to detect anomalies and refine access policies continuously.
- Continuously improve and adapt: Treat Zero Trust implementation as an ongoing process, adjusting policies and controls as the environment evolves.
What tools and technologies support Zero Trust Architecture?
To support a Zero Trust Architecture, organizations must adopt a set of integrated tools that align with the five pillars of Zero Trust—identity, device, network, application, and data. These technologies work together to enforce the principle of “never trust”, ensure contextual verification, and enable zero trust access across hybrid and multi-cloud environments.
The following tools are essential to implement Zero Trust security effectively:
- Identity and Access Management (IAM): Enforces strong authentication, authorization, and identity governance—core to zero trust protection.
- Multi-Factor Authentication (MFA): Adds an extra layer of security beyond passwords, reducing risk of security breaches.
- Zero Trust Network Access (ZTNA): Replaces legacy VPNs by granting access based on identity, device health, and real-time context.
- Endpoint Detection and Response (EDR): Monitors device behavior to detect anomalies and prevent lateral movement.
- Security Information and Event Management (SIEM): Aggregates and analyzes logs across systems to detect threats within the zero trust environment.
- Microsegmentation Tools: Breaks down traditional network segmentation into granular zones to isolate assets and reduce attack surfaces.
- Data Loss Prevention (DLP): Protects sensitive information by monitoring and controlling data transfers.
- Cloud Access Security Brokers (CASB): Provide visibility and control over security cloud applications used in hybrid cloud settings.
- Policy Engines and Automation Tools: Enforce security policies, adjust permissions dynamically, and scale enforcement across environments.
By applying Zero Trust technologies holistically, organizations can evolve their security infrastructure to a higher level of zero trust maturity. These tools support the benefits of a Zero Trust model—robust security, reduced risk, and improved compliance—while addressing the challenges associated with Zero Trust Architecture.
How does Zero Trust relate to network security architecture?
Zero Trust Architecture represents a fundamental shift in network security architecture, moving away from traditional security models that rely on static perimeters and implicit trust. Rooted in the principle of “never trust”, this concept of Zero Trust redefines how systems validate users, devices, and workloads within modern, distributed environments.
Unlike traditional network segmentation, which trusts traffic once inside the perimeter, Zero Trust is designed to enforce continuous verification and least-privilege access across all network layers. It replaces broad trust zones with microsegmentation, ensuring that access to each resource is governed by strict zero trust policies.
What is an essential element of a Zero Trust architecture?
An essential element of Zero Trust Architecture is continuous identity and context-based access control, ensuring that no user or device is inherently trusted—regardless of location or network. Rooted in the principle of “never trust,” this model applies dynamic, verifiable attributes to every access request, forming the foundation of a Zero Trust security strategy.
Unlike traditional perimeter-based defenses or SOC (Security Operations Center) models—where SOC full form in audit refers to System and Organization Controls—Zero Trust enforces fine-grained policies and microsegmentation to restrict lateral movement. While a NOC vs SOC comparison shows operational vs. security focus, Zero Trust integrates with SIEM (Security Information and Event Management) platforms and SOAR tools to enhance detection, response, and policy enforcement. This approach aligns with practices followed by an MSSP (Managed Security Service Provider) and is reinforced by frameworks that adhere to modern compliance and cyber law mandates.