Attackers do not run one campaign a year, so why should your red team? In this guide, you will see how Eventus Security delivers Red Teaming as a Service (RTaaS) as a continuous program that simulates real-world attacks against your environment around the clock. It explains what a red teaming service is, how an always-on model differs from a one-time red team engagement, and what the core components look like in practice. You will also learn how Eventus designs and runs exercises, connects outcomes into its SOC for faster detection and response, adapts scenarios to industry risk and regulatory expectations, and measures impact in a way that is usable for boards and auditors. Over time, the recurring findings help strengthen cyber resilience, raise security maturity, and improve security training and culture.
Table of Contents
What is Red Teaming as a Service (RTaaS)?
Red Teaming as a Service (RTaaS) is a managed offensive security offering where a provider’s red team continuously simulates real-world cyber attacks against an organization’s security posture using a mix of human-led red team exercises and automated red teaming tools. Unlike traditional security assessments or a one-off penetration test, it runs on an ongoing basis so that security weaknesses are discovered, validated, and fixed as environments, users, and cyber threats evolve.
How Does it Protect Organizations Around the Clock?
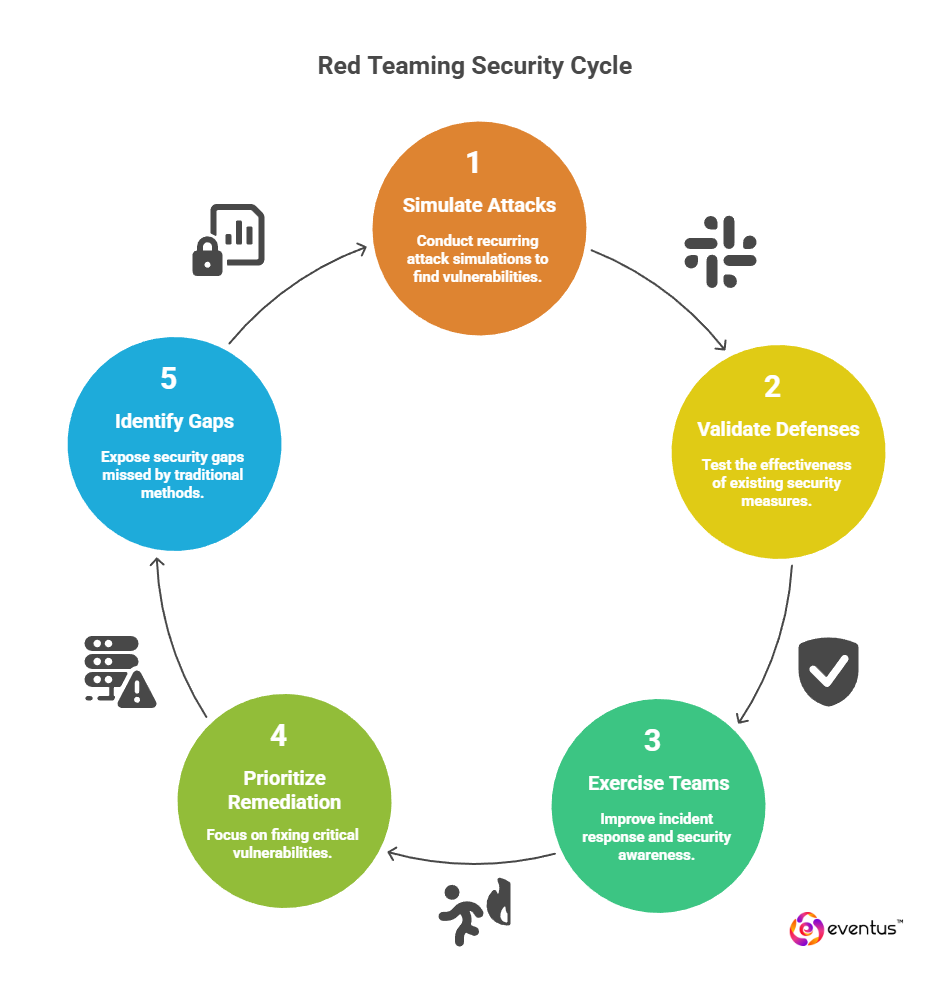
Here’s how It protects organizations around the clock by continuously stressing and improving the organization’s overall security posture:
- Continuous attack simulation: Managed red team operations run on a recurring schedule and can use continuous automated red teaming services to probe for new exposures between major campaigns. This ensures security vulnerabilities are found closer to when they are introduced, not months later during an annual test.
- Validation of real defenses, not just configurations: Red teaming services focuses on how well existing security measures, security controls, and the security team actually resist real-world cyber attacks. It goes beyond scanning to test detection, blocking, and containment in live conditions.
- Exercising blue and purple teams: When aligned with the blue team or run as a purple team teaming exercise, red teaming services shows how quickly defenders spot and respond to red team attempts. This directly improves incident response, tuning of security operations, and security awareness training.
- Prioritised remediation and measurable improvements: Each red team assessment produces evidence-driven findings that help security leaders evaluate the security of critical assets and prioritise fixes that most effectively strengthen organizational security posture and improve overall security.
- Coverage where traditional security goes blind: Because red teaming services simulates real-world attacker behaviour, it often exposes security gaps that traditional security testing and routine compliance-driven security services miss, such as flawed security policies, weak inter-team handoffs, or untested incident response playbooks.
Want a deeper technical breakdown?
Download the Eventus Security Red Teaming as a Service Guide to explore methodologies, sample attack paths, metrics, and remediation models used in real-world environments.
👉 Download the Red Teaming Guide (PDF)
See 24/7 Red Teaming as a Service
How is Red Teaming as a Service (RTaaS) Different from Traditional One Time Red Team Engagements?
Here’s how:
| Dimension | Traditional one-time red team engagement | Red Teaming as a Service (RaaS) |
| Timeframe and cadence | One-off, time-boxed project run occasionally. | Runs at an agreed recurring frequency of red team exercises, making red teaming services an ongoing process, not an event. |
| Security insight and coverage | Provides a point-in-time view of security risks and security issues. | Evaluates the environment repeatedly, helping track whether fixes still work against sophisticated cyber threats. |
| Integration with security strategy | Often sits outside routine security operations and is isolated from day-to-day information security workflows. | Each cycle’s results are used to refine the organisation’s security measures and broader security strategies. |
| Relationship with penetration testing | Red teaming services and penetration testing are tightly scoped and stop once impact is proven. | Red teaming services and penetration activities are repeated and combined to deliver comprehensive security over time. |
| Red–blue collaboration and evolution | Limits collaboration between red and blue teams to a post-exercise debrief. | Builds ongoing collaboration where red team members continuously feed gaps and improvements into SOC and IR teams. |
| Accessibility and long-term value | Requires fresh budget and planning for every engagement, so testing is sporadic. | Managed model makes red teaming more accessible and delivers recurring benefits, steadily strengthening overall posture. |
How Does Eventus Security Deliver Red Teaming as a Service (RTaaS) in Real World Environments?
Here’s how Eventus Security deliver red teaming as a service (RTaaS) in real world environments:
- Eventus Security delivers red teaming as a service (RTaaS) by turning the concept of red teaming into recurring campaigns in real production environments, led by experienced security experts who conduct a red team exercise against clearly defined, business-critical targets
- In each engagement, red teams use realistic red team activities (phishing, lateral movement, privilege abuse, application abuse) so red teaming services goes beyond scanning and shows how real attackers would navigate the client’s environment
- During and after every campaign, red teaming provides concrete evidence of detection gaps, weak security strategies, and broken processes, enabling effective red teaming outcomes that directly enhance security operations center performance rather than just producing a theoretical report
- As a managed program, Eventus Security runs multiple red teaming tests per year, adjusts scenarios as the environment and threats evolve, and feeds every round’s findings into remediation and retesting, so improvements become cumulative instead of one-off.
How Does Eventus Security Adapt Red Team Scenarios to Different Industries and Regulatory Environments?
Eventus Security adapts red team scenarios by tying every engagement to the industry’s core processes, crown-jewel assets, and regulatory controls, so each campaign behaves like the threats that target that sector.
Here’s how:
- Industry- and regulation-specific scoping: For banks and fintech, scenarios focus on payment rails, customer data, and fraud paths; for healthcare, on PHI and clinical systems; for industrial and OT, on production continuity and safety. This alignment is what makes a successful red team exercise relevant to auditors, regulators, and boards.
- Testing mandated controls in practice: Eventus Security designs paths that deliberately hit controls required by PCI-DSS, HIPAA, GDPR, ISO 27001, or NIST CSF, so red teaming services can help prove whether access control, logging, segregation of duties, and incident handling work in real conditions, not just in policy.
- Tuning intensity and cadence by sector: The red team exercises depends on operational risk tolerance: some industries get narrow and deep chains that avoid disrupting critical services, others support broader internet-facing tests. This is where red teaming vs generic, checklist-style audits becomes clear.
- Continuous evolution of scenarios: As cloud, open banking, telehealth, or industrial IoT change each sector’s risk profile, Eventus Security refreshes tools and playbooks to reflect the evolution of red teaming and attacker tradecraft to strengthen 24/7 soc services. In practice, teaming is often an iterative loop, where red team also updates scenarios every cycle to stay aligned with live threats and current regulations.
Need help with managed red teaming?
How Does Eventus Security SOC Work Together with Red Teaming to Provide Always on Protection?
Here’s how Eventus Security SOC work together with red teaming services to provide always on protection, including for organisations evaluating best soc provider companies in india:
- Eventus Security red team campaigns feed the SOC: After every red team exercise, Eventus analysts convert missed or weak alerts into new SIEM rules, SOAR playbooks, and enrichment logic, so detections reflect real red team attack chains, not just generic threat intel
- The SOC uses red teaming to test its own performance: During simulations, Eventus SOC tracks MTTD (mean time to detect) and MTTR (mean time to respond) for each scenario, then closes specific gaps in alerting, triage, and escalation before similar attacks appear in production
- Red and blue teams collaborate in structured purple-team reviews: Post-exercise debriefs between red team operators and SOC analysts align telemetry, detections, and response workflows, turning every campaign into concrete defensive changes rather than just a report.
- Red-team patterns are turned into 24/7 monitoring logic: Behaviours observed in simulations—such as lateral movement paths, credential abuse, and cloud misuse patterns—are encoded into continuous SOC detections, allowing Eventus to provide always-on protection even when no live exercise is running.
In Which Scenarios Should Organisations Use Red Teaming as a Service (RTaaS) from Eventus Security?
Organizations should use Red Teaming as a Service (RTaaS) from Eventus Security when they need to prove how their defenses hold up against real attackers, not just tools and checklists. Given below are the scenarios:
- Before high-impact launches: For a new banking app, SaaS platform, or public portal, Eventus runs red team campaigns to test internet-facing attack surface and data flows before go-live
- After major architecture changes: Following cloud migrations, zero trust rollouts, or identity/network redesigns, Eventus simulates lateral movement, privilege escalation, and data theft to validate the new security architecture
- To verify SOC, SIEM, MDR/XDR performance: When a detection and response stack is new or heavily changed, Eventus red teaming services measures what is detected, how fast (MTTD), and how well incidents are handled (MTTR).
- When regulators, customers, or the board want proof, not promises: In regulated or high-target sectors (banks, fintech, healthcare, government, OT/ICS), Eventus provides campaign-style simulations mapped to real threat actors and TTPs, creating evidence that controls work, and reinforcing response readiness through ai driven soc as a service workflows that operationalise the findings.
- When internal red team capacity is limited: If in-house teams lack scale or specialised skills (cloud, identity, OT), Eventus delivers full end-to-end red team campaigns as a managed service, turning them into a repeatable engine for measurable resilience improvements.
How Can Boards and Regulators Use Red Teaming Outcomes as Assurance of Cyber Resilience?
Boards and regulators can use red teaming outcomes as concrete proof of cyber resilience when they treat them as measurable assurance, not just technical reports. Here’s how:
- Validate critical business processes, not just systems: When red team reports show how attacks move through payments, trading, claims, or clinical workflows, boards and regulators can see whether business-critical services remain available and trusted under real attack conditions
- Map findings to control frameworks and obligations: Outcomes should be linked to specific NIST CSF, ISO 27001, PCI-DSS, DORA, RBI, GDPR or similar controls. This lets oversight bodies check whether stated policies and regulatory requirements actually hold up when tested by realistic adversary simulations
- Cross-check management assurance with red team evidence: If controls reported as “effective” in RCSA or internal audits are repeatedly bypassed in red team scenarios, that gap signals governance and assurance weaknesses, not just technical issues. Outcomes become a reality check on self-attestation and can be continuously validated with support from soc as a service providers.
- Insist on retesting to verify that lessons are implemented: True assurance comes when previously exploited attack paths are retested and shown to be blocked. Boards and regulators should expect explicit proof that findings are remediated and no longer exploitable in subsequent red team exercises.
What Methodology Does Eventus Follow for Planning, Executing, and Remediating Red Team Exercises?
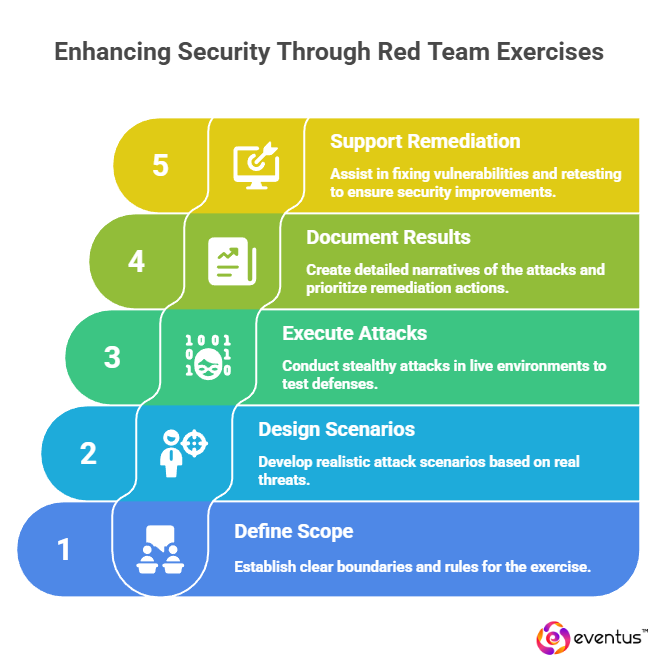
Given below are the methodologies:
- Defines scope and rules of engagement around business-critical systems and risk tolerance
- Designs threat-informed scenarios aligned to real attackers and industry context
- Executes stealthy, multi-stage attacks in live environments to test controls and response
- Documents results as attack narratives with prioritised remediation actions
- Supports remediation and retesting to confirm fixes and track measurable security improvement
How do Pricing Models, Engagement Duration, and Global Support Affect Provider Selection?
Here’s how:
- Pricing models decide testing frequency: If a provider only offers per-engagement pricing, you’ll likely run rare, ad hoc tests. Subscription or hybrid pricing makes regular red team exercises and retests financially realistic
- Engagement duration governs attack depth: Very short engagements usually cover narrow technical checks. Longer or programmatic engagements allow full kill chains, proper analysis, and remediation + retest, which is crucial for complex environments and for validating whether your best soc as a service program can detect and contain realistic attack paths end to end
- Global support affects realism and safety: A provider with only single-time-zone support cannot realistically simulate 24/7 attackers or quickly adjust rules of engagement during issues. Follow-the-sun global support is better for always-on, multi-region organizations
- Fit to your operating model is critical: The right provider is the one whose pricing, duration options, and support coverage align with your budget cycles, risk appetite, and geographic footprint.
How Can Organizations Use Recurring Red Team Results to Drive Security Culture and Training?
Here’s how:
- Turn real attacks into simple stories: After each red team campaign, create short, anonymised attack narratives (for example, “one phishing email → domain admin”) and share them in town halls or internal posts to make security culture concrete, especially when those insights are packaged into ongoing improvements by a managed soc service provider.
- Build role-based training from real failures: Use recurring red team results to design targeted training: staff get phishing and data-handling lessons, developers get secure coding and config examples, SOC/IT get detection and escalation scenarios—all based on actual weaknesses, not generic slides.
- Use metrics to show cultural progress: Track and share internal trends like fewer successful phishing clicks, faster reporting of suspicious activity, and reduced dwell time from one red team cycle to the next, so people see that their behaviour changes outcomes
- Turn findings into drills and simulations: Convert common attack paths into tabletop exercises, phishing simulations, and IR run-throughs so teams practise the exact patterns the red team used successfully
- Recognise good security behaviour publicly: When a red team attempt is stopped early (quick reporting, correct handling, good escalation), highlight that in internal comms. This reinforces that every employee’s actions matter and embeds security into day-to-day culture.
FAQs
Given below are the FAQs:
1 – Is Red Teaming as a Service (RTaaS) only Suitable for Large Enterprises?
No. Red Teaming as a Service (RTaaS) can be scoped for mid-sized organisations with critical cloud apps, payment systems, or PII. Eventus adjusts scope, cadence, and depth to match your risk profile and budget.
2 – Which Internal Teams Must be Involved for a Successful RaaS Engagement?
You typically need security leadership, IT/ops, and SOC/MDR for scoping, access, and response review. Involving app owners, DevOps, and IAM teams ensures fixes reach the right systems quickly.
3 – Will a Managed Red Team Program Disrupt Production Systems?
Properly governed engagements use rules of engagement, no-go zones, and attack windows to limit disruption. Eventus selects low-impact techniques that prove risk without corrupting data or affecting availability.
4 – How are third-party and SaaS Platforms Treated in Eventus RaaS Engagements?
Eventus focuses on how attackers would pivot through your side of integrations—SSO, APIs, vendor access—without breaching third-party contracts. Direct testing of a provider only occurs with explicit written permission.