SOC as a Service (SOCaaS) empowers organizations to combat the most critical cybersecurity threats of 2025 through proactive detection, rapid response, and AI-driven defense. It outlines where managed SOCaaS fits within the broader defense stack, how it detects and contains advanced threats, reduces ransomware risk, and secures identity systems. The discussion also highlights its role in operationalizing AI safely, integrating automation with human expertise to enhance resilience, meet compliance, and strengthen overall security posture across evolving digital environments.
Table of Contents
What are the biggest cyber threats of 2025 that SOC as a Service must counter?
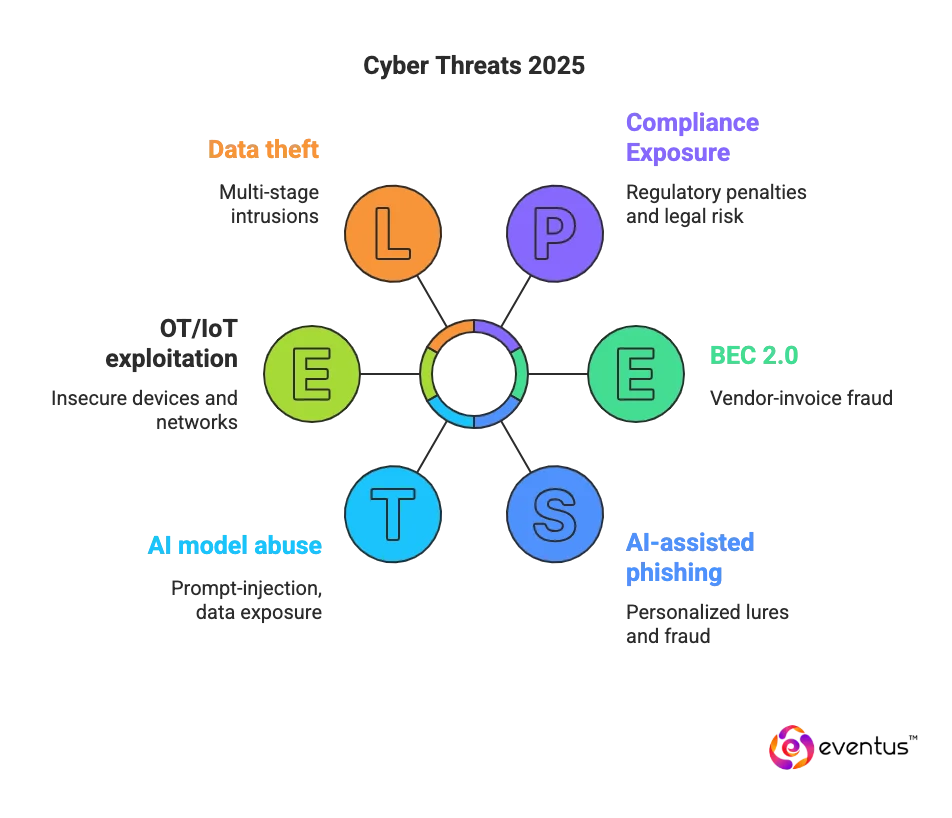
These are the priority cyber threats soc services must monitor, hunt, and counter with real-time detection and response, automation, machine learning, and proactive operations in a modern security operations center delivered by a SOC service, managed security service provider to help organizations mitigate risk and stay ahead in cybersecurity/cyber security in 2025.
- Ransomware with data theft and extortion — multi-stage intrusions that exfiltrate data before encryption to maximize leverage and cause data loss after a breach.
- Identity-centric attacks — MFA fatigue, session/token theft, OAuth abuse, and privilege escalation that bypass perimeter threat detection.
- AI-assisted phishing and deepfake fraud — highly personalized lures and synthetic voice/video that defeat user awareness and expand the 2025 threat landscape.
- Software supply-chain compromise — poisoned packages, build-pipeline tampering, and image/registry abuse that introduce vulnerability management at source.
- Cloud and SaaS misconfiguration — exposed storage, excessive IAM, shadow tenants, and stale tokens that erode security posture across multicloud.
- API exploitation — BOLA/IDOR, auth bypass, and automated scraping targeting business logic and sensitive data in microservices and GraphQL.
- Insider threats and account misuse — malicious or careless users, contractors, or compromised service accounts leading to stealthy security risks.
- Business Email Compromise (BEC) 2.0 — vendor-invoice fraud and thread hijacking that bypass malware controls and cause direct financial loss.
- Living-off-the-land exfiltration — native tools (RDP/PowerShell/CLI) and covert channels to avoid controls and enable quiet data loss.
- OT/IoT exploitation — insecure devices and converged networks in healthcare, manufacturing, and retail that impact safety and uptime.
- Zero-day and exploit-as-a-service campaigns — rapid weaponization that outpaces patch cycles despite threat intelligence sharing.
- AI model abuse and data-poisoning — prompt-injection, sensitive data exposure, and corrupted training sets impacting ai features in apps.
- Compliance exposure after incidents — regulatory penalties and legal risk from inadequate logging, retention, or safeguards (e.g., HIPAA) following a breach.
Where does “Security Operations Center as a Service” fit in the defense stack?
SOC as a Service sits in the detect-and-respond layer of the cybersecurity defense stack, orchestrating signals from preventive controls and turning them into decisive action.
- Upstream (preventive controls): IAM, EPP/EDR, email/web gateways, WAF/API gateways, CNAPP, and configuration baselines generate telemetry.
- SOCaaS core (detect + orchestrate): The soc services ingests and correlates logs and alerts, enriches with intel, performs threat hunting, and prioritizes advanced threat activity. It runs automations and guides incident response across endpoints, identities, cloud, and SaaS.
- Downstream (remediation + recovery): Playbooks isolate hosts, revoke tokens, block accounts, roll keys, quarantine mail, and enforce cloud guardrails; tickets and evidence flow to IT, SecOps, and Legal.
- Feedback loop (hardening + governance): Findings feed control tuning, attack-surface reduction, and compliance reporting; detection gaps become new rules and runbooks.
How does SOCaaS detect advanced threats before damage occurs?
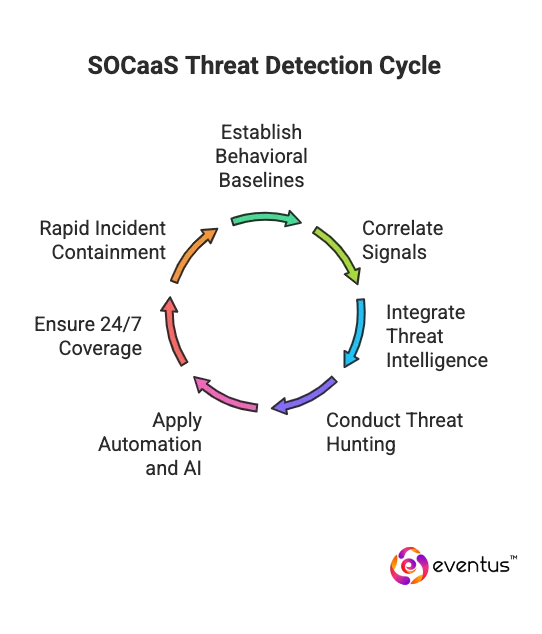
SOC security services detect advanced threats before impact by combining continuous monitoring, behavioral analytics, and automation. It extends beyond signature-based alerts to identify emerging risks in real time.
- Behavioral baselines: The SOC platform continuously learns normal patterns across users, endpoints, networks, and cloud environments. Deviations trigger immediate investigation before compromise.
- Correlation and context: Multiple weak signals—failed logins, privilege escalation, or data movement—are correlated to expose hidden attack chains early.
- Threat intelligence integration: External feeds enrich alerts with current indicators of compromise (IoCs) and tactics, improving pre-emptive visibility.
- Proactive threat hunting: Analysts search for dormant adversary behavior that evades detection tools, closing gaps unseen by automated systems.
- Automation and AI analytics: Machine learning models evaluate telemetry volume at scale, filtering noise and prioritizing real malicious activity.
- 24/7 detection coverage: Continuous cyber security operations ensure no time-based blind spots, unlike a limited in-house soc.
- Rapid incident containment: Detected anomalies automatically trigger endpoint isolation, token revocation, and other mitigation workflows.
How do they contain and eradicate attacks rapidly?
SOC as a Service contains and eradicates attacks rapidly through coordinated, automated, and intelligence-driven response workflows embedded within managed security services.
- Automated containment: When a verified threat is detected, the SOC platform isolates affected endpoints, revokes compromised credentials, disables malicious processes, and applies firewall blocks instantly to halt lateral movement.
- Integrated playbooks: Pre-approved incident playbooks standardize containment and eradication across systems—cloud, endpoint, network, and SaaS—ensuring fast, consistent actions.
- Real-time orchestration: The service integrates with EDR, SOAR, and identity systems to execute containment commands without manual delay.
- Root-cause eradication: Analysts remove persistence mechanisms, patch exploited vulnerabilities, and validate integrity through post-incident scans.
- Continuous validation: Every eradicated incident undergoes verification and lessons-learned analysis to prevent recurrence and improve response accuracy.
By aligning these capabilities under a unified best managed security service provider, SOCaaS provider reduces mean time to contain (MTTC) and mean time to recover (MTTR), restoring operations faster and minimizing business disruption.
How do they reduce ransomware risk specifically?
SOC security services reduce ransomware risk through a multi-layered defense model built around advanced threat detection, automated response, and continuous visibility. It combines security information and event management, threat hunting, and automated playbooks to disrupt every stage of the ransomware kill chain before encryption occurs.
- Early intrusion detection: Real-time correlation of logs and telemetry exposes abnormal activity such as credential abuse, lateral movement, and privilege escalation, enabling the security team to act before data is locked.
- Threat intelligence enrichment: Continuous ingestion of advanced threat intelligence and global threat feeds helps the SOC anticipate emerging threats and identify evolving threat actors targeting specific industries.
- Automated response playbooks: Predefined security protocols isolate infected endpoints, revoke compromised tokens, and disable malicious processes, ensuring containment within seconds.
- Behavioral analytics: Machine-learning models detect deviations in network traffic, encryption attempts, and anomalous file activity, providing real-time threat detection against advanced cyber threats.
- Backup and data integrity assurance: Integration with cloud security services and on-prem systems verifies backup immutability, preventing ransomware from corrupting recovery data.
- Continuous hardening: The security team analyzes incidents to fix security misconfigurations, reduce the attack surface, and refine security policies and controls.
How does SOCaaS defeat identity-centric attacks?
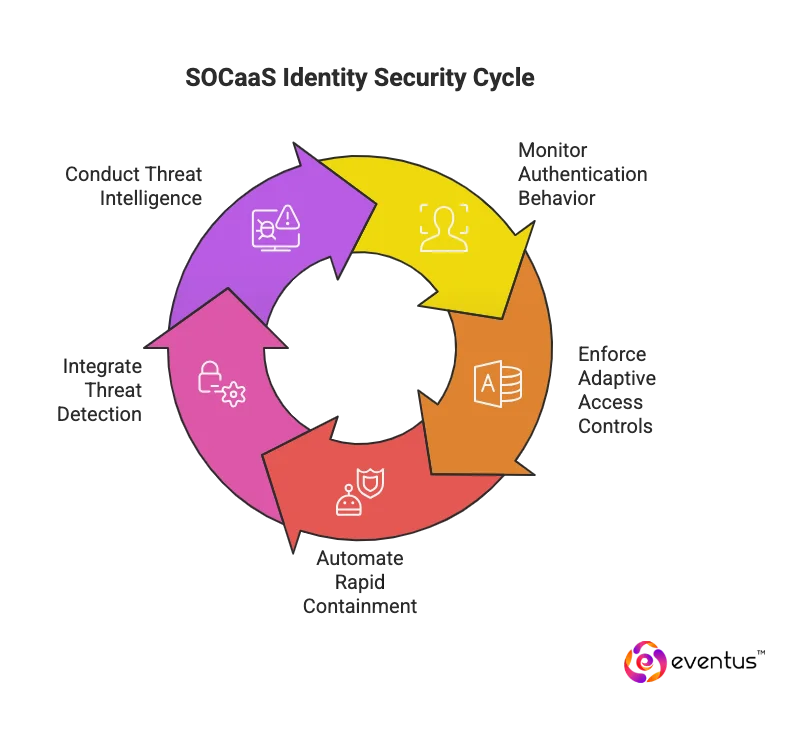
SOC as a Service defeats identity-centric attacks by continuously monitoring authentication behavior, enforcing adaptive access controls, and automating rapid containment. It integrates threat detection and response with identity governance to neutralize misuse before data exposure or privilege abuse occurs.
- Behavioral identity analytics: The managed SOC establishes normal user patterns across devices, locations, and access times. Any deviation triggers alerts to stop credential theft, session hijacking, or privilege escalation.
- Real-time monitoring: Continuous correlation of identity logs, SSO, and MFA telemetry ensures threats in real time are detected and stopped before compromise.
- Automated response workflows: Playbooks disable compromised accounts, revoke tokens, and enforce password resets instantly, maintaining data security and compliance.
- Adaptive access and segmentation: Context-based access rules and conditional policies isolate risky sessions, reducing exposure from insider misuse or lateral movement.
- Threat intelligence and hunting: Dedicated threat hunters map evolving credential-based cybersecurity threats, identify reused passwords, and detect stolen tokens on dark web marketplaces.
- Security validation: The best SOC as a service provider companies continuously tests security controls to identify security flaws and align defenses with the latest cybersecurity trends and security requirements.
How do they operationalize AI safely?
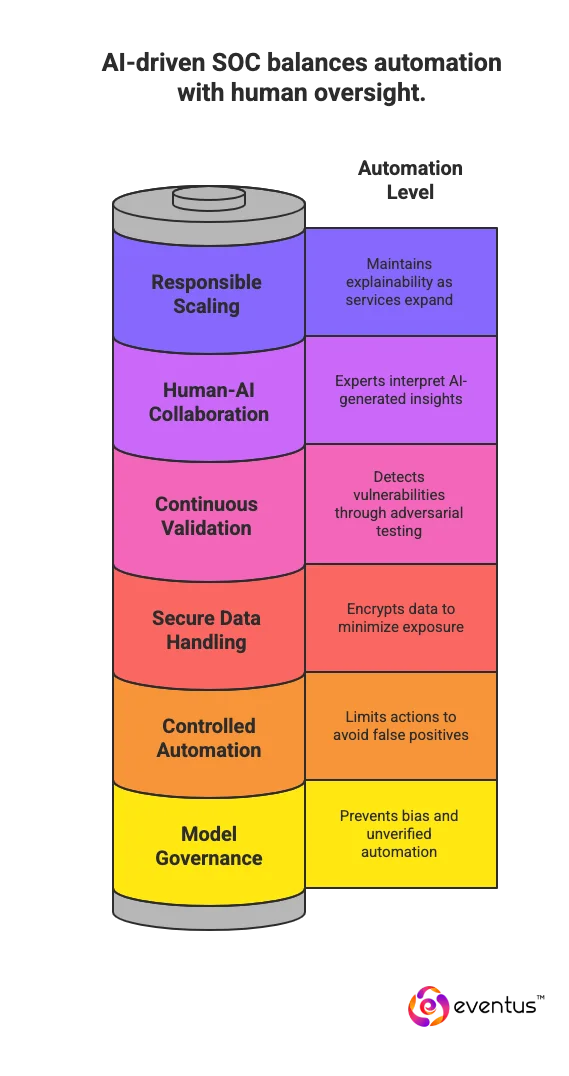
SOC as a Service operationalizes AI safely by embedding governance, transparency, and validation into every analytical and automation workflow. It ensures machine learning models strengthen organization’s security rather than introduce new cyber risks.
- Model governance and oversight: AI systems used for detection, correlation, and response follow strict review processes to prevent bias, drift, or unverified automation from impacting security measures.
- Controlled automation: AI-driven actions, such as automated containment or triage, operate within predefined limits verified by human analysts to maintain robust cybersecurity and avoid false-positive disruption.
- Secure data handling: Sensitive telemetry and user data feeding AI pipelines are encrypted, anonymized, and retained per compliance requirements, minimizing exposure during cyber incidents.
- Continuous validation: Models undergo adversarial testing and red teaming to detect vulnerabilities like model inversion or prompt injection—reducing potential attack vectors within analytics engines.
- Human-AI collaboration: The team of cybersecurity experts interprets AI-generated valuable insights, ensuring that automation aligns with contextual threat understanding.
- Responsible scaling: SOC providers scale AI capabilities securely, maintaining explainability and traceability across models as they expand scale services to meet global cybersecurity requirements.
How can organizations be future-proof with an AI driven SOC?
SOC as a Service operationalizes AI safely by embedding governance, transparency, and validation into every analytical and automation workflow. It ensures machine learning models strengthen an organization's security rather than introduce new cyber risks.
- Model governance and oversight: AI systems used for detection, correlation, and response follow strict review processes to prevent bias, drift, or unverified automation from impacting security measures.
- Controlled automation: AI-driven actions, such as automated containment or triage, operate within predefined limits verified by human analysts to maintain robust cybersecurity and avoid false-positive disruption.
- Secure data handling: Sensitive telemetry and user data feeding ai driven soc are encrypted, anonymized, and retained per compliance requirements, minimizing exposure during cyber incidents.
- Continuous validation: Models undergo adversarial testing and red teaming to detect vulnerabilities like model inversion or prompt injection—reducing potential attack vectors within analytics engines.
- Human-AI collaboration: The team of cybersecurity experts interprets AI-generated valuable insights, ensuring that automation aligns with contextual threat understanding.
- Responsible scaling: SOC providers scale AI capabilities securely, maintaining explainability and traceability across models as they expand scale services to meet global cybersecurity requirements.
FAQs
Q1. What does a typical SOCaaS onboarding timeline look like?
Most providers complete onboarding in 2–4 weeks: day 0–3 connection of identity, EDR, cloud, and SaaS; week 1 baselining and alert tuning; week 2–3 playbook approvals; week 4 live run with 24/7 monitoring and reporting.
Q2. What is SOC as a Service and why is it critical in 2025?
SOC as a Service (Security Operations Center as a Service) is a cloud-based cybersecurity model that provides 24/7 threat monitoring, detection, and response without the need for an in-house security team. In 2025, with AI-driven attacks, ransomware, and insider threats at an all-time high, SOC as a Service offers scalable, AI-powered defense that adapts in real time to new vulnerabilities — ensuring proactive protection for modern digital infrastructures.
Q3. How does SOC as a Service defend against AI-driven cyber threats?
At Eventus Security, our AI-driven SOC as a Service protects enterprises from the most complex cyber threats of 2025. AI-powered attacks can mimic user behavior and bypass traditional defenses. SOC as a Service uses machine learning algorithms, behavioral analytics, and automated response systems to identify abnormal activity patterns faster than human analysts.
This next-gen intelligence allows security teams to isolate and neutralize threats like deepfake phishing or polymorphic malware before damage occurs.
Q4.What are the top cyber threats SOC as a Service mitigates in 2025?
In 2025, the most dangerous cyber threats include:
- AI-driven phishing and deepfake scams
- Ransomware-as-a-Service (RaaS)
- Cloud infrastructure attacks
- Zero-day exploits
- IoT and endpoint vulnerabilities
SOC as a Service integrates advanced threat intelligence feeds, automated patch management, and real-time SIEM correlation to counter these evolving risks efficiently.
Q5. What procurement evidence should buyers request?
Demand SLAs (MTTD/MTTR), playbook catalog, sample reports, auditor letters (SOC 2/ISO 27001), red-team results, and named escalation contacts. Insist on a 30-day proof of value with measurable targets.
Q6. What are the business benefits of adopting SOC as a Service?
By outsourcing to a managed SOC provider, businesses can achieve enterprise-grade protection without the heavy cost of internal teams. Key benefits include:
- Continuous 24/7 monitoring
- Faster incident response and recovery
- Lower operational costs
- Compliance with evolving data privacy laws
- Access to global threat intelligence networks
This makes SOC as a Service an essential part of a future-ready cybersecurity strategy.