This article explores what cybersecurity awareness means for organizations today and why it is essential. It outlines common threats like phishing, malware, and insider risks, and provides strategies to improve awareness through targeted training and national campaigns. It also examines global initiatives, public-private collaborations, and emerging cybercrime trends—such as AI threats and Zero Trust adoption—offering a comprehensive guide to protecting information systems in 2025 and beyond. As cyber threats grow more complex, many organizations are turning to SOC as a Service to ensure continuous monitoring while reinforcing employee awareness and compliance with security protocols.
Table of Contents
What Is Cybersecurity Awareness and Why Is It Important?
Cybersecurity awareness refers to the understanding and recognition of cyber threats, security risks, and safe digital behaviors by individuals across an organization. According to the National Cybersecurity Alliance (NCSA), over 43% of cyberattacks target small businesses, underscoring why cybersecurity awareness is a critical business requirement in today’s landscape. For many enterprises, partnering with a managed SOC provider ensures continuous monitoring, rapid incident detection, and reinforcement of employee awareness across all endpoints.
Cybersecurity awareness involves educating employees, contractors, and end users about:
- Recognizing suspicious behavior, such as phishing emails or fraudulent links
- Understanding the value and sensitivity of the data they handle, including personally identifiable information (PII) and confidential internal assets
- Practicing cybersecurity best practices, such as using strong passwords, avoiding public Wi-Fi without VPNs, and not opening unknown attachments.
- Aligning user behavior with organizational policies enforced by the SOC, which monitors, analyzes, and responds to potential security incidents in real time.
A critical aspect of this process is understanding what is SIEM (Security Information and Event Management). SIEM refers to a security solution that collects and analyzes log data from across the enterprise network to detect abnormal activity and support incident response. It plays a vital role in enabling the SOC to correlate user behavior with real-time events and initiate appropriate containment actions. When integrated with awareness training, SIEM reinforces behavioral analytics and supports evidence-based threat detection.
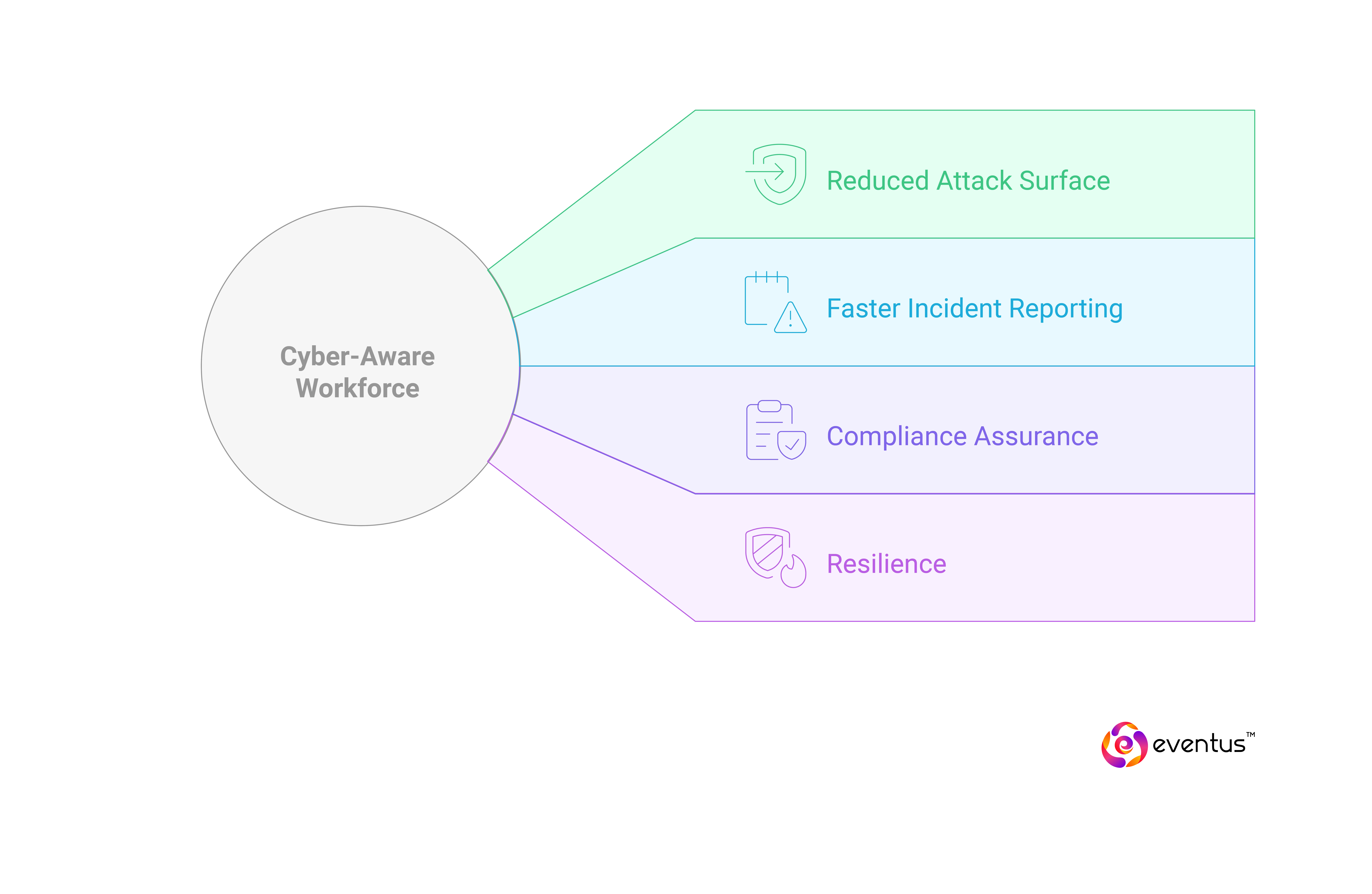
Benefits of a Cyber-Aware Workforce
A cyber-aware workforce provides measurable benefits:
- Reduced attack surface – trained users are less likely to fall for phishing or social engineering attempts
- Faster incident reporting – employees can identify and escalate suspicious activities quickly
- Compliance assurance – awareness training helps meet legal and regulatory obligations tied to data protection, privacy, and reporting
- Resilience – ongoing training programs build an organization’s capability to defend, respond, and recover from incidents.
- Support from cybersecurity companies can further strengthen these efforts by providing specialized training modules, threat simulations, and managed response services tailored to organizational needs.
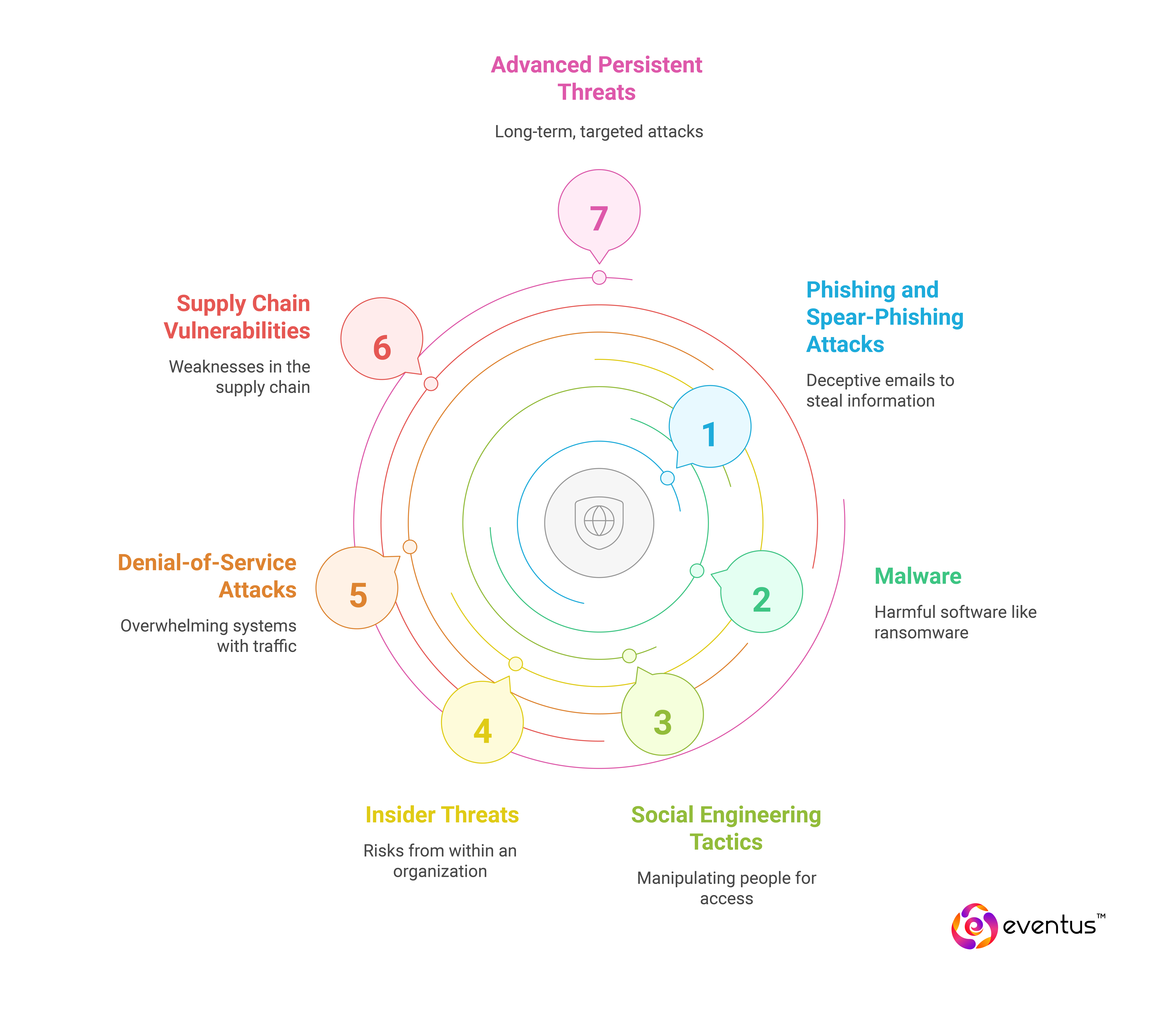
What Are the Most Common Cybersecurity Threats?
Cybersecurity threats are evolving in complexity and volume, presenting substantial risks to organizations across all sectors. These threats target vulnerabilities in people, processes, and technologies—requiring coordinated cybersecurity awareness programs, adherence to security best practices, and continuous employee training to prevent compromise of sensitive information or personally identifiable information (PII). Below are the most prevalent threats enterprises must actively mitigate as part of a broader cyber awareness strategy.
Phishing and Spear-Phishing Attacks
Phishing attacks exploit human behavior to deceive end users into disclosing confidential data, often via fraudulent emails, malicious websites, or spoofed communication channels. Spear-phishing, a more targeted variant, impersonates trusted contacts to gain unauthorized access to information systems. Verizon’s 2023 Data Breach Investigations Report found that 36% of breaches involved phishing, and 74% of all breaches included a human element—highlighting why behavior-driven training is essential.
- These attacks commonly bypass technical defenses by exploiting insufficient user awareness.
- Security training programs must educate employees to detect suspicious links, unusual sender behavior, and phishing email characteristics.
- Reporting suspected phishing to internal IT teams or law enforcement agencies is a critical preventive measure.
Malware, Including Ransomware and Spyware
Malware encompasses software designed to disrupt operations, steal data, or extort organizations. In 2022 alone, global ransomware damages exceeded $20 billion, with projections hitting $265 billion by 2031 if unmitigated
- These threats are often delivered via malicious downloads, email attachments, or compromised websites.
- Maintaining updated software and using automated endpoint detection platforms helps reduce vulnerability exposure.
- Organizations should follow CISA advisories and implement layered defenses as part of their cybersecurity strategy.
Social Engineering Tactics
Social engineering manipulates psychological triggers—urgency, fear, authority—to trick individuals into bypassing security protocols or divulging confidential information. A 2023 IBM report noted that social engineering was the most expensive initial attack vector, costing organizations an average of $4.10 million per breach.
- These tactics often complement phishing attacks or impersonation schemes.
- Cybersecurity awareness training should reinforce the importance of verifying requests, especially those involving privilege escalation or unusual access.
- Regular drills during Cybersecurity Awareness Month can help reinforce security best practices.
Insider Threats and Employee Negligence
According to the Ponemon Institute, insider threats have grown 44% over the past two years, with the average cost per incident reaching $15.4 million. Insider threats may be malicious or unintentional, but both types present serious challenges. Employee negligence, such as reusing weak passwords or unauthorized data sharing, often results from poor security awareness or inadequate training programs.
- Enforcing least privilege access and activity monitoring is essential to detect anomalous behavior.
- Regular awareness training mitigates risks stemming from human error, a leading cause of breaches in the information technology sector.
- Data classification and handling policies should be part of every organization's awareness initiative.
Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) Attacks
DoS and DDoS attacks flood network infrastructure with traffic, disrupting normal operations and disabling critical online services.
- While not directly breaching data, these attacks degrade platform reliability and damage brand trust.
- Cybersecurity best practices include deploying load balancers, firewalls, and DDoS mitigation services.
- Cross-sector collaboration and intelligence sharing, such as alerts from the U.S. Department of Homeland Security, enhance preparedness.
Supply Chain Vulnerabilities
Threat actors increasingly target vendors and third parties to infiltrate larger networks, making supply chain security a core component of modern cybersecurity awareness programs.
The SolarWinds breach in 2020 impacted more than 18,000 organizations, including U.S. federal agencies, emphasizing why third-party cybersecurity awareness is no longer optional.
- Attacks on code repositories, service providers, or device firmware can propagate malware globally.
- Organizations must enforce third-party risk assessments and require secure development practices from vendors.
- National initiatives by Congress and the National Cybersecurity Alliance stress the need to secure critical sector infrastructure through collaborative awareness efforts.
Advanced Persistent Threats (APTs)
APTs are sophisticated, stealthy, and long-duration campaigns conducted by highly skilled attackers, often backed by nation-states. Their objective is typically espionage, data exfiltration, or long-term network infiltration.
- APTs use a combination of phishing, malware, zero-day exploits, and privilege escalation to achieve persistence.
- Organizations must implement continuous monitoring, behavior analytics, and threat intelligence integration to detect and mitigate such cyberattacks.
- Multi-layered defenses and cross-departmental incident reporting protocols enhance organizational resilience.
How Can Organizations Improve Cybersecurity Awareness?
Improving cybersecurity awareness is not a one-time task—it is a continuous, structured initiative embedded within an organization’s broader information security strategy. A mature cybersecurity awareness program integrates behavior-driven training, actionable insights, and stakeholder engagement. Below are key components that ensure measurable improvement in cybersecurity posture across all user levels.
- Develop tailored cybersecurity training programs based on job roles, threat exposure, and access levels to ensure relevance and behavioral impact.
- Run simulated phishing campaigns regularly to assess employee vulnerability, track click and report rates, and tailor follow-up training.
- Measure awareness effectiveness through KPIs such as training completion, phishing report rates, policy violation trends, and quiz performance.
- Foster a culture of continuous learning by recognizing secure behavior, sharing regular insights, and embedding cybersecurity into daily routines.
- Integrate cybersecurity topics into meetings and communications to maintain awareness and align users with current threat intelligence.
- Use gamified and interactive tools like quizzes, simulations, and role-play to improve engagement and retention in awareness training.
- Provide role-specific training to departments such as IT, Finance, and HR, targeting their unique risks and data protection responsibilities.
- Stay updated on evolving threats by subscribing to CISA advisories, participating in National Cybersecurity Awareness Month, and leveraging sector-specific threat intelligence.
What Are the Key Cybersecurity Awareness Campaigns and Initiatives?
National Cybersecurity Awareness Month (NCSAM), led by the Cybersecurity and Infrastructure Security Agency (CISA) and the National Cybersecurity Alliance, is a U.S. government-backed initiative designed to raise awareness about the importance of cybersecurity across the public and private sectors. CISA’s “Secure Our World” campaign in 2023 focused on four key behaviors: password hygiene, MFA, software updates, and phishing detection—now adopted in over 1,200 organizations.
National Cybersecurity Awareness Month (NCSAM)
- Led by CISA and National Cybersecurity Alliance (U.S.)
- Runs every October with weekly cybersecurity themes
- Targets public and private sectors to raise awareness
- Reinforces password hygiene, PII protection, and threat mitigation
Cyber Swachhta Pakhwada (India)
- Run by CERT-In under MeitY
- Focus on malware removal and safe internet behavior
- Provides free tools, advisories, and training to users
- Targets SMBs and government employees with actionable education
Public-Private Partnerships
- Enable threat intelligence sharing and coordinated defense
- Drive development of enterprise-specific training platforms
- Facilitate cross-sector cybersecurity policy implementation
- Supported by CISA, DHS, vendors, MSSPs, and academic bodies
Impact of Awareness Campaigns
- Reduces phishing, ransomware, and insider threats
- Improves incident detection and reporting rates
- Enhances employee behavior and password practices
- Up to 70% reduction in user-related incidents (NICCS)
Organizational Resources & Toolkits
- CISA toolkits, CERT-In alerts, NCSA resources
- Templates for internal communication and policy rollout
- Free malware detection tools and reporting channels
- Scalable for any sector and IT security maturity level
Employee Engagement Strategies
- Gamified modules and phishing simulations
- Certificates, rewards, and internal leaderboard systems
- Role-specific content for HR, finance, and IT teams
- Automated reminders and executive endorsement drive adoption
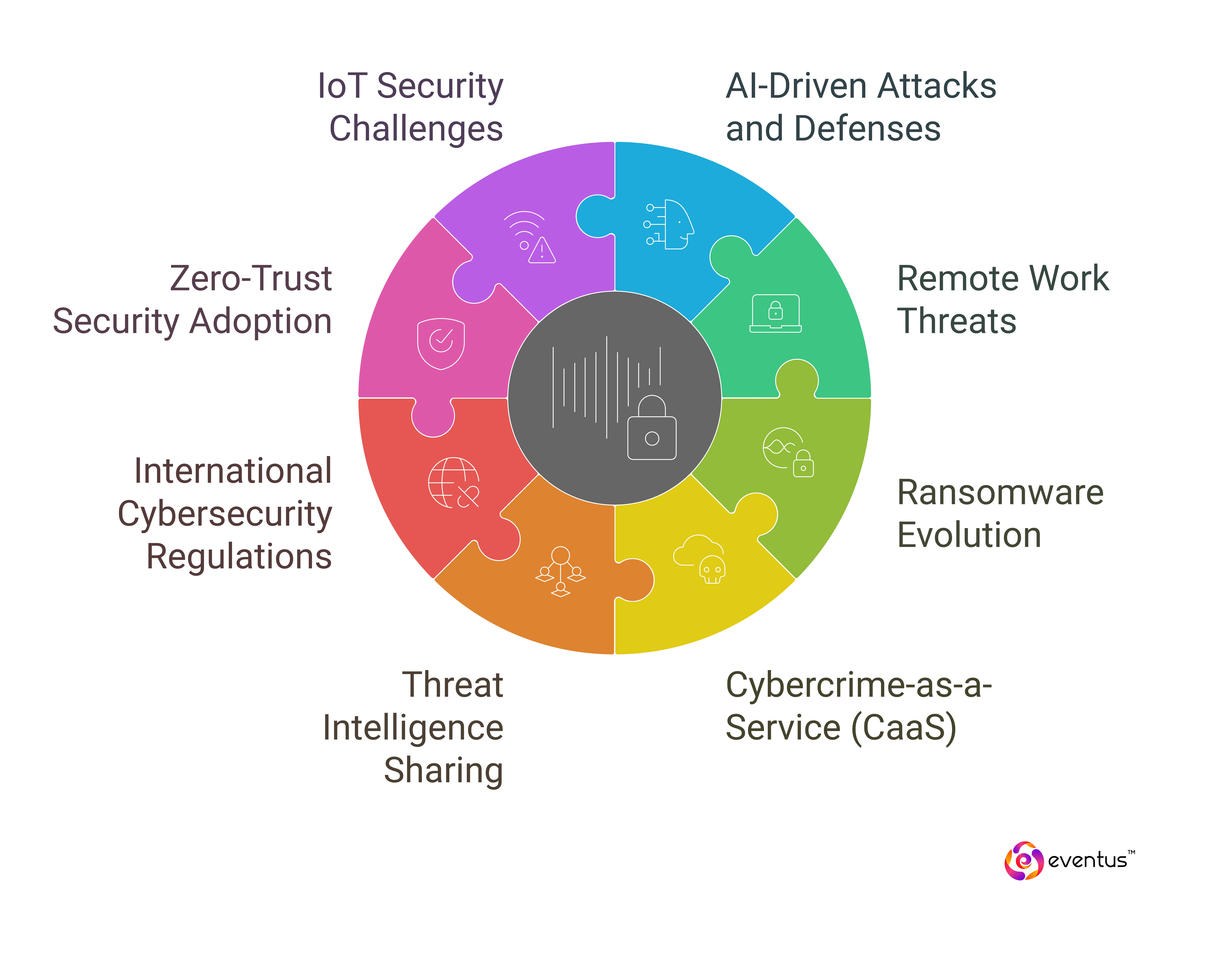
What Are the Emerging Trends in Cybercrime and Prevention?
Below are the emerging patterns shaping the global cybersecurity ecosystem, along with effective countermeasures designed to mitigate their impact.
AI-Driven Attacks and Defenses
- Adversarial AI automates phishing, evades detection, exploits vulnerabilities.
- Defensive AI enables anomaly detection, real-time incident response, behavioral analysis.
- Requires continuous updates to training programs and awareness platforms.
Remote Work Threats
- Insecure home networks, unpatched endpoints, poor end-user awareness.
- Phishing emails and weak authentication remain primary attack vectors.
- Security training must address remote access, device hygiene, and password policy.
Ransomware Evolution
- Double extortion tactics targeting critical sectors and PII.
- Emphasis on incident preparedness, strong access control, and secure backups.
- Requires coordination with law enforcement and Homeland Security.
Cybercrime-as-a-Service (CaaS)
- Low-barrier access to phishing kits, ransomware tools, and automation.
- Drives frequency and sophistication of attacks.
- Demands behavioral monitoring, employee engagement, and fast incident reporting.
Threat Intelligence Sharing
- Sector collaboration accelerates detection and response.
- Participation in ISACs, partnerships with CISA, and data-driven awareness programs.
- Enhances simulation effectiveness and training precision.
International Cybersecurity Regulations
- Global mandates like GDPR, CCPA require privacy-by-design and data protection.
- Security best practices tied to access control, reporting, and PII safeguards.
- Training and documentation now part of compliance requirements.
Zero-Trust Security Adoption
- “Never trust, always verify” with micro-segmentation and identity enforcement. According to Gartner, by 2025, 60% of organizations will phase out legacy VPNs in favor of Zero Trust Network Access (ZTNA) architectures.
- Blocks lateral movement and restricts privileged access.
- Requires user training and secure operational behavior.
IoT Security Challenges
- Legacy firmware, weak credentials, and poor visibility increase risk.
- Needs device authentication, segmentation, and onboarding protocols.
- Awareness training essential for IoT governance and threat mitigation.
What does Cyber awareness look like in 2025?
In 2025, cyber awareness is a continuous, organization-wide initiative integrating real-time threat intelligence, adaptive training, and behavior-based risk analysis. It emphasizes zero-trust principles, remote work security, and phishing resilience. AI-driven tools now personalize awareness programs to individual user risk profiles across sectors.