This article explains how AI-powered SOCs are reshaping security operations. It defines what an AI SOC is, explores the tools and models used, and highlights top use cases that reduce noise and improve threat detection. The discussion covers how AI-driven SOCs transform traditional operations, the key capabilities that define modern security programs, and how an AI SOC architecture and pipeline functions. It also examines human-AI collaboration, automation benefits, and measurable outcomes, offering a clear view of how AI is transforming the SOC landscape.
Table of Contents
What is an AI SOC?
An AI SOC (artificial intelligence Security Operations Center) is a security operations function where core workflows—telemetry collection, normalization, detection, triage, investigation, and response—are executed by AI in security operations and machine learning security operations, with humans supervising and deciding on edge cases. In an AI-powered SOC (also written ai powered soc), models continuously correlate signals across SIEM, EDR, NDR, cloud, identity, and threat intelligence to produce higher-fidelity incidents, drive security operations center automation, and guide an ai soc analyst through ai-enhanced SOC workflows.
What is AI-driven SOC?
An AI-driven SOC is a security operations center that uses machine learning and generative AI to automate high-volume tasks across SOC operations so human analysts can focus on complex cybersecurity decisions. It continuously integrates diverse data sources (including every relevant log) to improve threat detection, reduce false positives, and accelerate incident response and remediation, strengthening overall security posture for SOC teams and the broader security team.
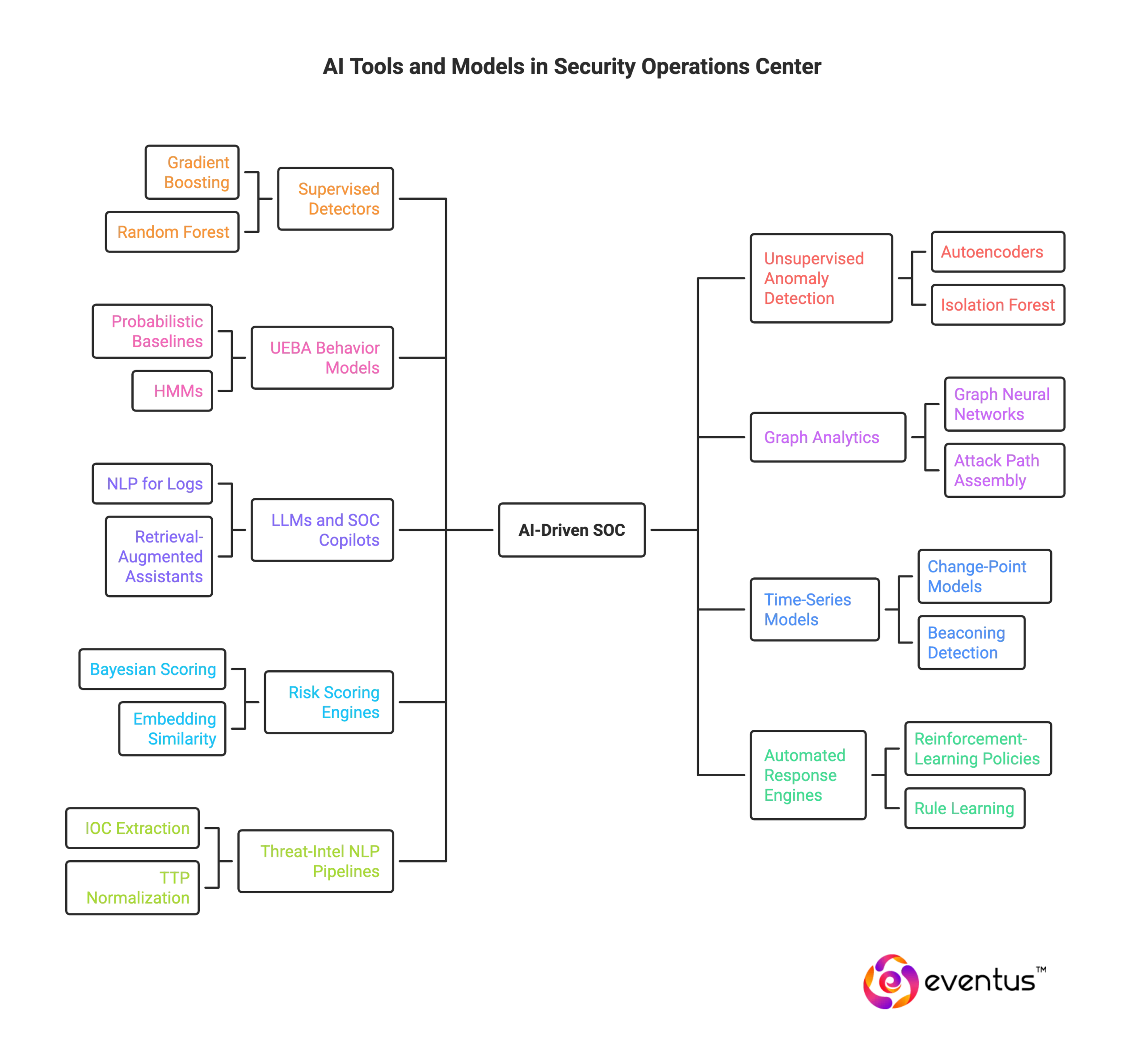
What AI tools and models are used in the SOC?
An AI-driven SOC relies on model classes and tools that cut noise, raise fidelity, and automate repetitive tasks so security analysts can handle high-impact work. Core categories:
- Supervised detectors (e.g., gradient boosting, random forest, CNNs for files/URLs): classify events and raise high-quality security alerts about specific cyber threats, reducing low-value alert churn.
- Unsupervised anomaly detection (autoencoders, isolation forest, one-class SVM): surface novel behaviors and lateral movement patterns that signature rules miss.
- UEBA behavior models (probabilistic baselines, HMMs): learn normal user/device/service activity to flag risky deviations and streamline triage and investigation.
- Graph analytics and graph neural networks: link entities across identities, hosts, and network flows to assemble attack paths and prioritize security incidents.
- LLMs and SOC copilots (NLP for logs, retrieval-augmented assistants): parse unstructured telemetry, summarize evidence, draft response steps, and augment analysts with natural-language reasoning—freeing analysts to focus on complex decisions.
- Time-series and change-point models: detect surge, drift, and beaconing while preventing “storm” security alerts.
- Risk scoring and correlation engines (Bayesian/ensemble scoring, embedding similarity): merge related alerts into incidents and rank them by probable impact.
- Automated response and policy engines (reinforcement-learning-inspired policies, rule learning): execute contain/eradicate actions with approvals, cutting manual process in repetitive containment and ticketing.
- Threat-intel NLP pipelines: extract and normalize IOCs/TTPs from reports to enrich detections and speed hunts across cyber telemetry.
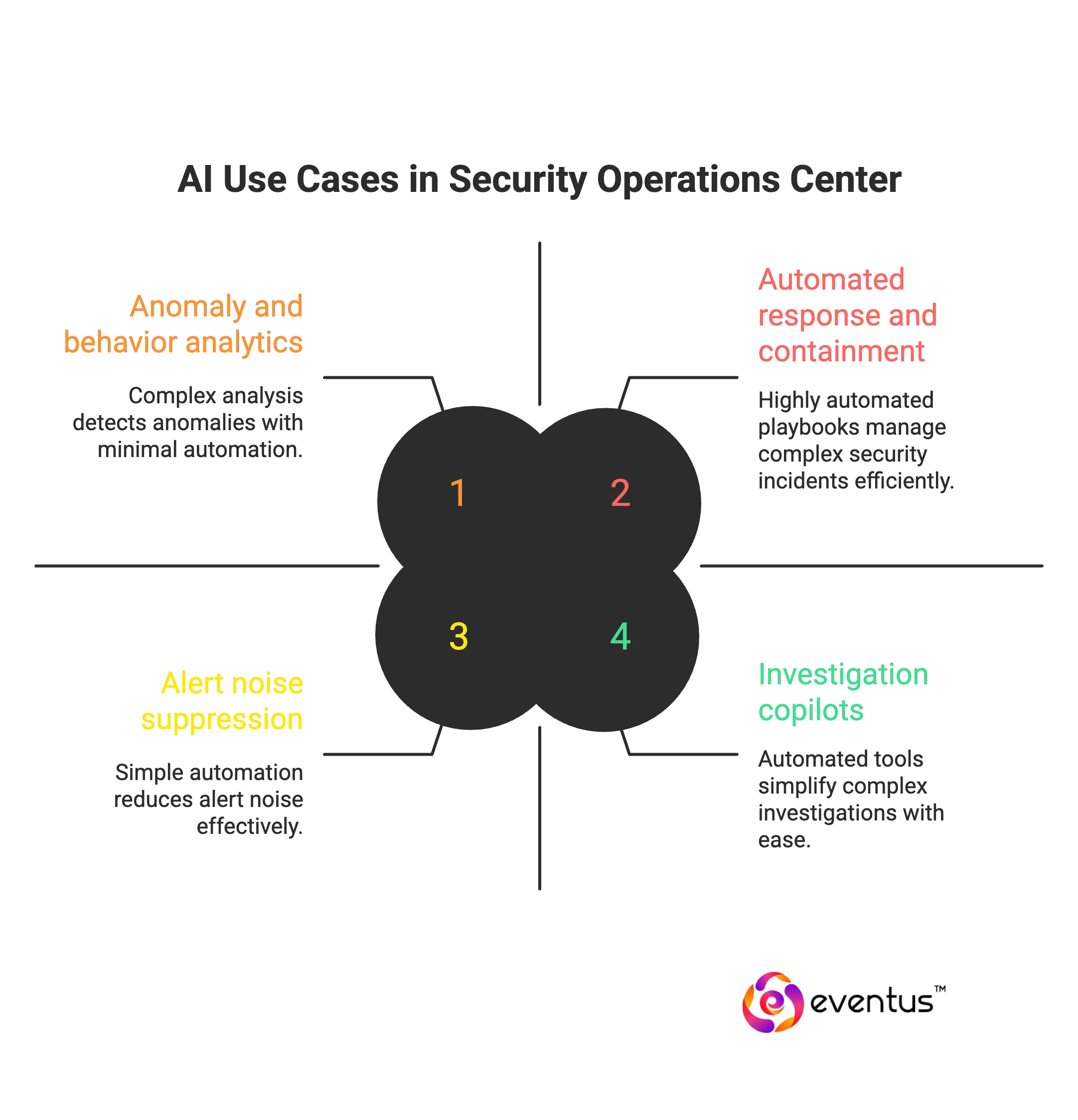
What are the top use cases for AI in the SOC?
Top use cases for AI in SOC (applicable to an AI SOC, ai-powered SOC, or ai-native SOC):
- Alert noise suppression and incident correlation
Use soc machine learning to cluster duplicates, merge related events, and promote only high-fidelity incidents—core to security operations center automation. - Anomaly and behavior analytics (UEBA)
Baseline users, devices, and services with machine learning SOC to detect insider risk, credential misuse, and lateral movement in an ai security operations center. - Automated triage and prioritization
Score risk, enrich context, and route cases so the ai SOC analyst and ai SOC analyst team can handle the most material threats first—reducing manual queue time in an ai-augmented SOC. - Investigation copilots and NL search
AI SOC copilot and soc analyst AI tools summarize evidence, answer questions over logs, and propose next steps—enabling ai-enhanced SOC workflows. - Threat intelligence enrichment
Automated IOC/TTP extraction and mapping to cases (identity, asset, geo, CVE) for faster scoping—often called ai SOC enrichment within the ai SOC architecture. - Automated response and containment
Playbooks that isolate hosts, disable accounts, block indicators, and notify stakeholders with approvals—ai SOC automation / ai powered SOC automation that cuts repetitive toil. - Phishing and email defense at scale
Classify messages, detonate attachments, and auto-remediate campaigns; escalate edge cases to a top AI SOC analyst. - Malware and endpoint analytics
Model-driven detection (process, DLL, registry, script patterns) and guided remediation across EDR—standard in a security operations center with AI. - Cloud and identity threat detection
Detect misconfigurations, privilege escalations, token abuse, and impossible travel across multi-cloud IAM in ai in security operations. - Exposure and attack-surface monitoring
Continuously inventory internet-facing assets, identities, and secrets; auto-open cases for risky findings—part of ai for SOC operations. - Hunting automation and query generation
Generate hunts from emerging TTPs; translate natural-language hypotheses into executable queries across data lakes in an ai-driven SOC. - Case summarization and reporting
Produce executive-ready incident narratives and post-incident timelines—accelerating knowledge transfer in the ai for security operations workflow. - Playbook optimization and drift detection
Learn from past outcomes to refine actions and spot detection drift—useful for ai SOC evaluation and continuous improvement. - SOC modernization and platform unification
Integrate SIEM, SOAR, UEBA, TIP, ASM into AI SOC platforms that streamline data flows and augment security analysts—the best AI features for SOC when planning how to integrate AI in SOC and broader ai for security operations center SOC modernization.
How do AI-powered SOCs transform security operations?
AI-powered SOCs transform security operations by:
- Turning security data into continuous intelligence.
AI models normalize, enrich, and correlate signals from multiple security tools, handling vast amounts of data and assembling incidents from noisy security data—a core shift from traditional security to ai-driven security operations. - Improving threat detection and response quality.
AI to enhance analytics (behavior, anomaly, graph) raises fidelity for threat detection and response, reduces alert churn, and accelerates investigation and response in today’s SOC. - Automating routine workload to raise SOC efficiency.
AI automation executes containment, ticketing, and communications for repeatable tasks—ai to handle routine actions—so security professionals spend time on higher-risk cases, cutting analyst burnout and lifting soc efficiency. - Embedding agentic assistance in analyst workflows.
AI agents and agentic AI act as copilots that summarize evidence, run queries, draft actions, and validate playbooks with guardrails; this ai-driven SOCs pattern minimizes manual handoffs and speeds decisions within the security operations team. - Enabling teams to scale without proportional headcount.
AI SOCs let SOC teams scale their operations without adding layers of process or staffing, delivering tangible soc benefits for a modern SOC and shifting the SOC landscape toward proactive, ai-driven security. - Advancing toward autonomous operations where safe.
With approvals and policy checks, low-risk tasks move toward an autonomous SOC, while humans keep authority on impact-bearing changes—clear role in SOC boundaries with the benefits of AI preserved. - Modernizing platforms and outcomes.
Unifying soc solutions into security’s AI SOC standardizes pipelines, surfaces measurable outcomes, and institutionalizes ai capabilities that transform SOC operations, enabling security teams to respond faster and more accurately.
Which capabilities define an AI-powered security operations program?
Capabilities that define an AI-powered security operations program
- Unified telemetry fabric and normalization — use AI for parsing, deduplication, and schema alignment across logs, endpoints, network, cloud, and identity, leveraging AI to prepare clean data for analytics in a critical SOC.
- Risk-based detection analytics — supervised, unsupervised, and behavior models that rank security threats by business impact; AI is transforming fidelity and coverage versus signature-only approaches.
- Incident correlation and scoring — graph and embedding methods that merge alerts into cases, prioritize urgency, and route to the available analyst automatically.
- Automated triage and enrichment — playbooks that attach asset, identity, and threat-intel context so ai enhances efficiency and reduces queue time with minimal analyst intervention.
- AI SOC agents and copilots — ai SOC agents and gen AI assistants that summarize evidence, answer questions over telemetry, propose next actions, and keep analyst-based approvals in the loop.
- Response orchestration with guardrails — ai to handle routine containment, notification, and ticketing while enforcing policy checks, simulations, and human sign-off where impact is high.
- Proactive threat hunting and hypothesis generation — natural-language query and pattern mining that turn weak signals into hunts, enabling advanced security beyond reactive alerting.
- Exposure and misconfiguration management — continuous discovery of external assets, identities, and risky settings so soc teams must address the most exploitable paths first.
- Case summarization and reporting — narrative timelines and executive briefs produced by ai-driven security operations, accelerating post-incident learning.
- Workload and staffing optimization — queue forecasting, smart escalation, and scheduling that direct work to the available analyst, easing soc challenges and burnout.
- Controls for governance and assurance — evaluation datasets, drift and bias monitoring, audit trails, and metrics that prove soc efficiency gains and sustain strategic security outcomes.
- Platform integration and extensibility — connectors and APIs that bind security tools into cohesive soc solutions, so the modern SOC can scale analytics and transforms SOC operations without re-platforming.
- Human-in-the-loop design — clear role definitions that ai to enhance analyst judgment, not replace it; imagine a SOC where automation handles toil and humans decide on risk.
How does an AI SOC architecture and pipeline work?
- Ingest telemetry from SIEM, EDR, NDR, identity, cloud, email, DNS.
- Normalize events to a common schema and remove duplicates.
- Enrich with asset, identity, geo, threat intel, and vulnerability context.
- Build features and embeddings; store them in online and offline feature stores.
- Detect with supervised, unsupervised, UEBA, time series, graph analytics, and LLMs.
- Correlate alerts into incidents; map to MITRE ATT&CK; compute business risk.
- Prioritize by risk and SLA; auto-route to the right queue.
- Orchestrate response via guarded playbooks with approvals and rollback.
- Assist analysts with summaries, queries, hypotheses, and guided actions.
- Learn from outcomes; track precision, recall, MTTD, MTTR; monitor drift and bias.
- Retain hot indexes for recent data and cold storage for history; ensure HA and backups.
FAQs
Q1: Can AI replace SOC?
Ans: No. AI cannot replace a SOC; it automates detection and response, but humans are needed for judgment, novel attacks, escalation, and compliance.
Q2: What is the role of AI in SOC?
Ans: AI’s role in a SOC is to analyze large security data sets, spot anomalies, correlate related events, and auto-prioritize or trigger playbooks to speed response.
Q3: What is SOC in AI?
Ans: “SOC in AI” means an AI-enabled Security Operations Center—a team and platform that use machine learning and automation to monitor, detect, investigate, and respond to threats.