Zero Trust Security is transforming how organizations protect data, users, and infrastructure by eliminating implicit trust and enforcing continuous verification. This article explores its core principles, historical evolution, architectural pillars, implementation stages, supporting technologies, and real-world applications. It also highlights the benefits, compliance advantages, and operational impact of adopting a Zero Trust model across cloud, hybrid, and remote environments.
Table of Contents
What is Zero Trust Security?
Zero Trust security is a strategic approach to cybersecurity that operates on the principle of “never trust, always verify.” Zero Trust is a security strategy that eliminates implicit trust by enforcing continuous verification of every user, device, and application attempting to access network resources.
What is the History of Zero Trust Security?
The concept of Zero Trust originated in 2009, introduced by John Kindervag, a principal analyst at Forrester Research. The idea challenged the outdated perimeter-based approach and emphasized the need for strict identity verification and policy enforcement—principles that now guide many modern Security Operations Centers (What is SOC?) in detecting and containing lateral threats. SOCs operationalize Zero Trust by continuously monitoring network activity, enforcing least-privilege access policies, and correlating identity, device, and behavior data in real-time. By aligning with Zero Trust architecture, SOCs enhance an organization's ability to identify insider threats, prevent unauthorized access, and respond to breaches with greater precision.
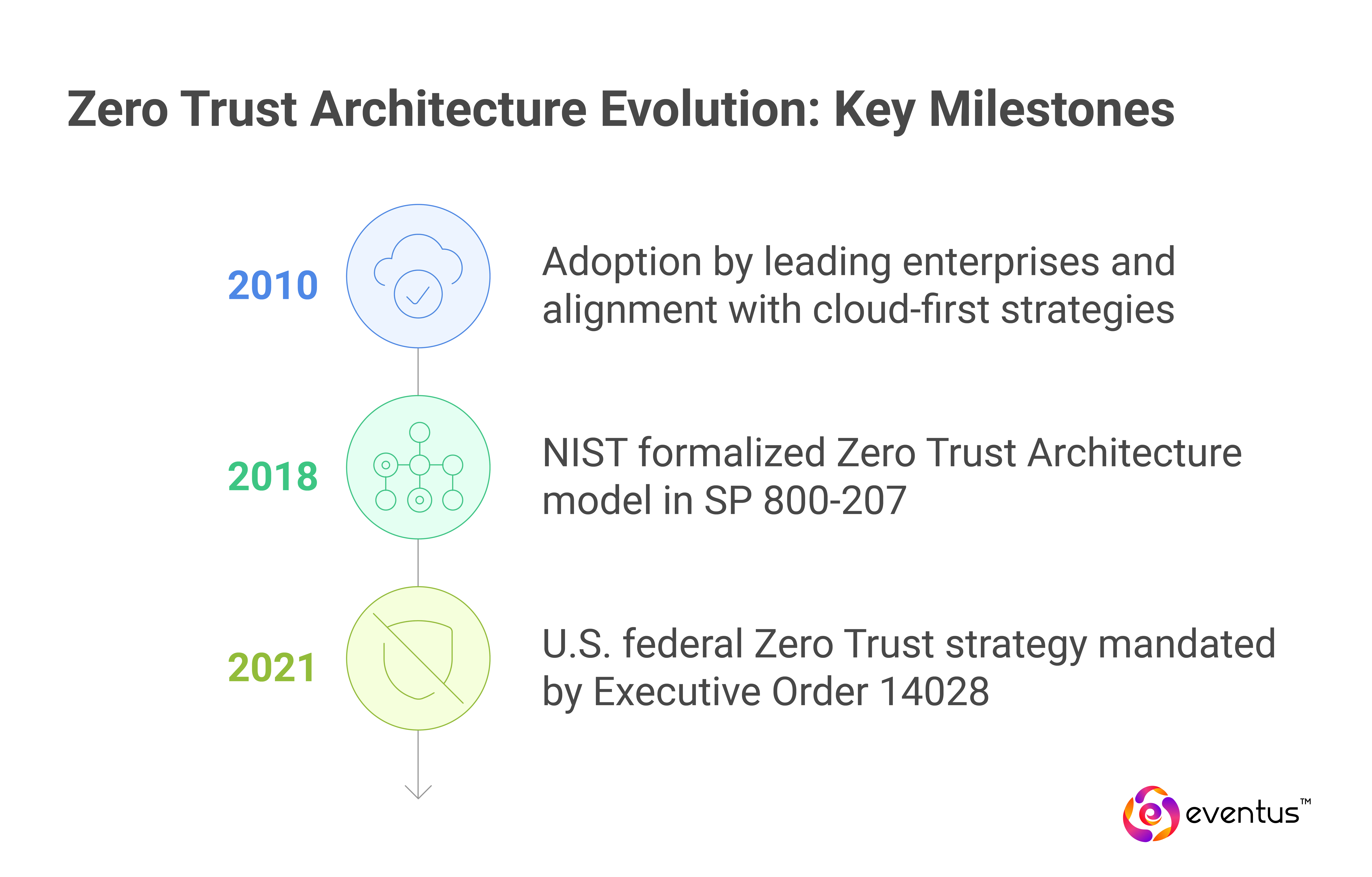
Key milestones:
-
2010: Adoption by leading enterprises and alignment with cloud-first strategies
-
2018: The National Institute of Standards and Technology (NIST) formalized the Zero Trust Architecture model in SP 800-207, establishing a standard framework for implementing Zero Trust principles across federal and enterprise environments.
-
2021: The U.S. federal Zero Trust strategy mandated by Executive Order 14028 accelerated adoption across public-sector agencies
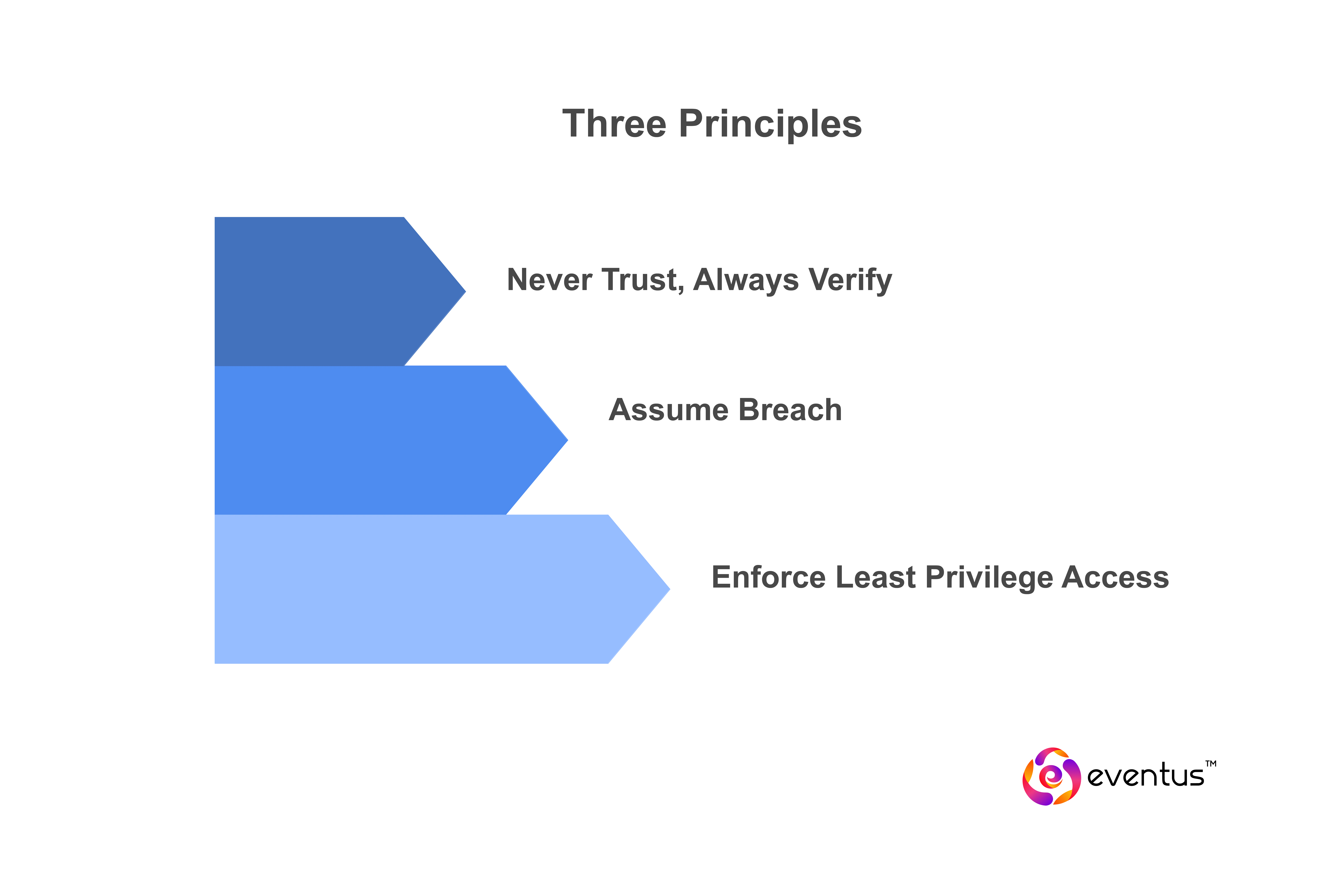
What Are the Three Principles?
The three core principles of Zero Trust establish the foundation for all Zero Trust implementations and are increasingly integrated into modern SOC as a Service. These principles also align closely with the operational mandates of any SOC service organization responsible for ensuring secure, policy-driven access across users, devices, and applications.
1. Never Trust, Always Verify
Every user, device, and application is continuously authenticated and authorized before gaining access, regardless of network location.
2. Assume Breach
Zero Trust is built on the assumption that internal or external threats already exist within the network, driving the need for containment, segmentation, and rapid response.
3. Enforce Least Privilege Access
Users and devices are granted the minimum level of access necessary to perform their tasks, significantly reducing attack surfaces and lateral movement. Organizations using ZTNA reduced lateral movement risks by 47%, according to a 2023 IBM Security report.
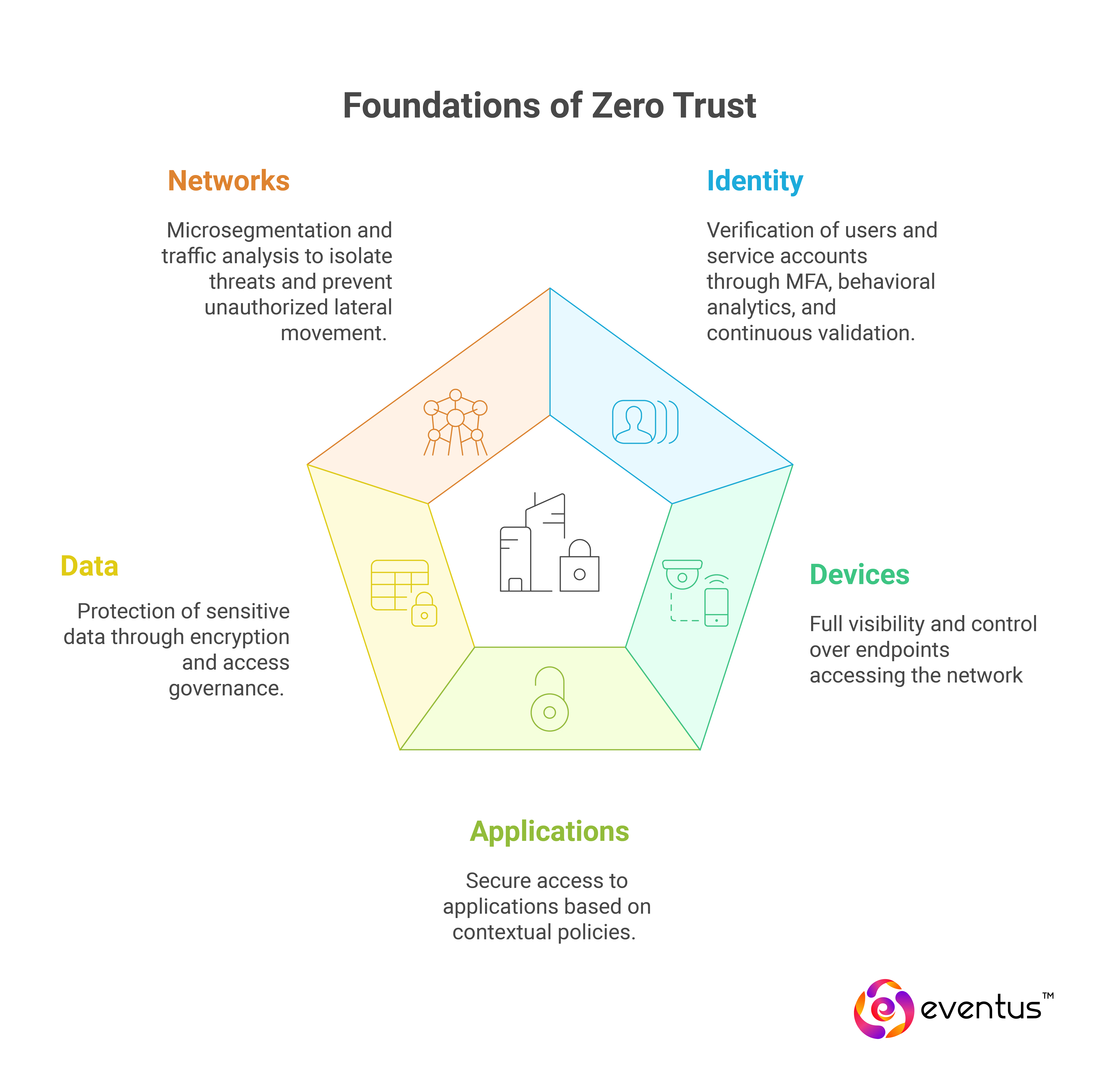
What Are the Five Pillars of Zero Trust?
While implementations may vary, five fundamental pillars support most Zero Trust architectures and serve as a baseline framework for any managed SOC provider delivering enterprise-grade threat monitoring and policy enforcement.
1.Identity– Verification of users and service accounts through MFA, behavioral analytics, and continuous validation.
2.Devices – Full visibility and control over endpoints accessing the network.
3.Applications– Secure access to applications based on contextual policies.
4.Data – Protection of sensitive data through encryption and access governance.
5.Networks – Microsegmentation and traffic analysis to isolate threats and prevent unauthorized lateral movement.
What Are the Benefits of Zero Trust?
Unlike traditional perimeter-based models, Zero Trust assumes breach by default and mandates continuous verification. This paradigm shift results in a measurable improvement in security posture, operational efficiency, and adaptability across complex enterprise environments.
1. Improves security posture
Enforces the principle of least privilege, reducing over-permissioned access and potential exploitation.
- Limits lateral movement within the network by microsegmentation and strong access control policies.
- Applies continuous authentication and authorization, ensuring access is valid at all times.
- Integrates identity and security for users, devices, and workloads across cloud and on-prem environments.
- Implements adaptive trust decisions, responding dynamically to emerging threats.
2. Reduces insider and APT threats
- Eliminates implicit trust even within the internal network, disrupting common APT kill chains.
- Reduces attack surface by enforcing Zero Trust network access (ZTNA) and isolating resources.
- Detects and contains suspicious behavior through granular visibility and behavioral analytics.
- Enables rapid deprovisioning of compromised identities or insider actors.
- Supports just-in-time and just-enough-access models, preventing unauthorized privilege escalation.
3. Compliance advantages
Supports NIST, ISO, and federal Zero Trust guidance, ensuring alignment with institutional best practices.
- Implements auditable policies for access control and data protection.
- Strengthens enforcement of security policies such as data segmentation and access logging.
- Improves readiness for audits by providing real-time access visibility and policy enforcement.
- Reduces compliance gaps caused by legacy security systems and perimeter trust models.
4. Supports remote and hybrid work
- Applies consistent security controls to remote, hybrid, and on-prem users.
- Leverages identity-based authentication, enabling secure cloud access and BYOD scenarios.
- Removes dependence on network perimeter, ensuring scalable and secure connectivity.
- Deploys Zero Trust access gateways and CASBs to monitor and secure cloud environments.
- Maintains continuous session validation, reducing risks from compromised sessions.
5. Scalability and operational resilience
- Decouples security controls from physical infrastructure, enabling flexible deployments.
- Scales horizontally across cloud and hybrid environments, supporting expansion without compromising security.
- Enhances operational continuity by segmenting systems and minimizing breach impact.
- Reduces complexity of legacy perimeter models, improving manageability and automation.
- Supports dynamic policy enforcement, allowing rapid adaptation to changing threat landscapes.
6. Enhances visibility and response time
- Monitors every access attempt across users, devices, and applications.
- Provides real-time telemetry for security teams to detect and respond to threats quickly.
- Supports SIEM and SOAR integrations, automating detection-to-response workflows.
- Improves mean time to detect (MTTD) and respond (MTTR) through data-driven insights.
- Enables contextual policy decisions, increasing the accuracy of threat identification.
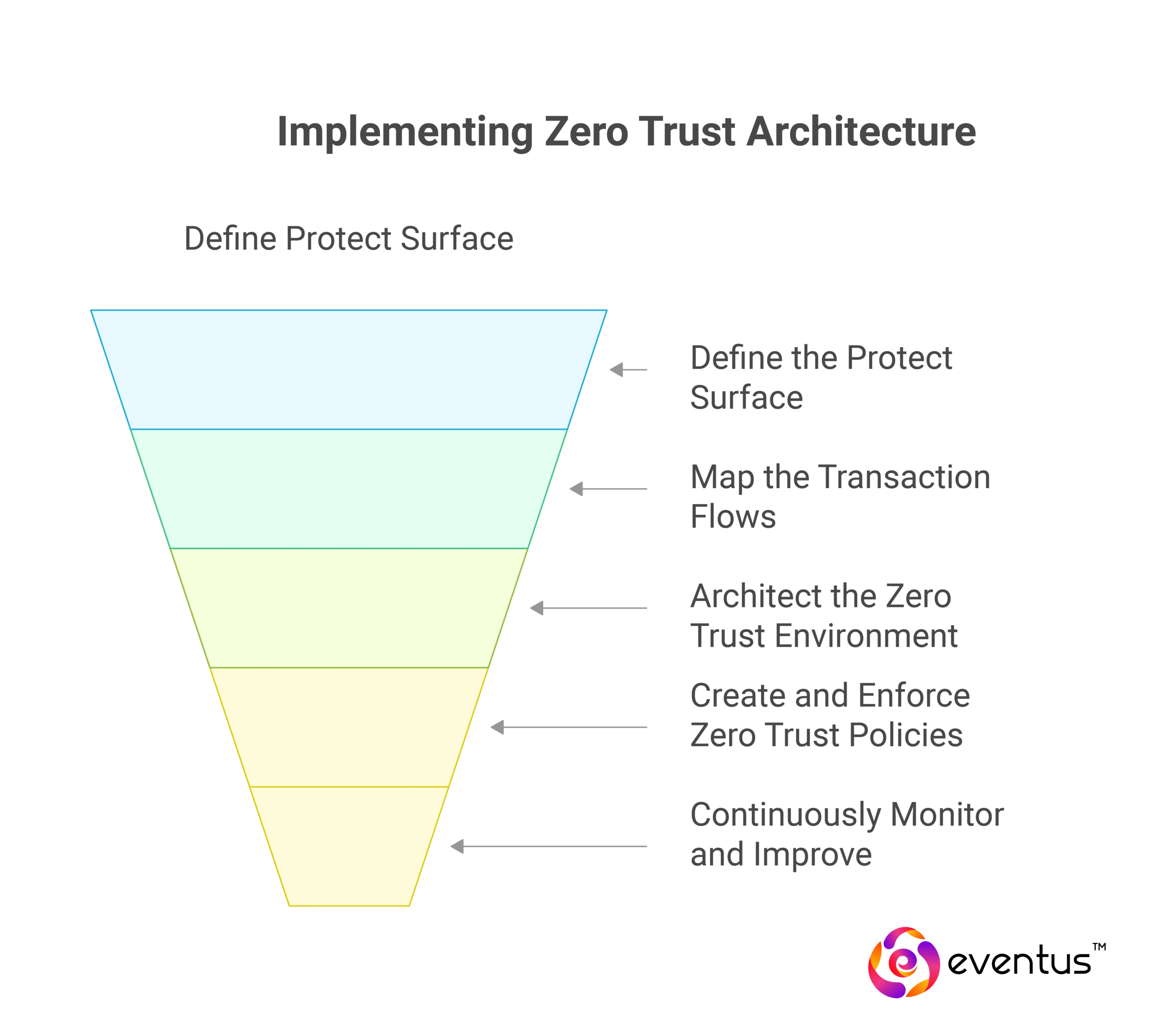
What are the key stages of Zero Trust implementation?
The process to implement Zero Trust architecture typically follows a phased model:
-
Define the Protect Surface
Identify the most critical data, assets, applications, and services (DAAS) within your network architecture.
-
Map the Transaction Flows
Document how users and devices interact with the protect surface to determine access requirements.
-
Architect the Zero Trust Environment
Design the microperimeter using identity-aware proxies, segmentation gateways, and access control policies.
-
Create and Enforce Zero Trust Policies
Implement security policies based on the principle of least privilege and context-aware trust decisions.
-
Continuously Monitor and Improve
Leverage analytics and telemetry to detect anomalies, enforce zero trust policies, and improve your security posture.
How to evaluate your current infrastructure readiness?
Before migrating toward Zero Trust, assess readiness by:
-
Conducting a Gap Analysis
Evaluate current network security architecture against Zero Trust principles.
-
Reviewing Identity and Access Management (IAM) Capabilities
Ensure the presence of directory services, identity federation, and single sign-on systems.
-
Assessing Network Visibility and Monitoring Tools
Confirm that logging, session tracking, and telemetry are in place across cloud and on-premise systems.
-
Auditing Existing Security Policies
Identify inconsistencies or overly permissive access that violate the Zero Trust approach.
-
Testing Security Controls Against Common Threat Scenarios
Simulate lateral movement or privilege escalation to validate current defense mechanisms.
What are some real-world examples of Zero Trust deployment?
Organizations across sectors have adopted Zero Trust strategies to address evolving threats:
-
Google's BeyondCorp Initiative
Google’s BeyondCorp Initiative pioneered the Zero Trust model by shifting access controls from the perimeter to user and device identity, enabling secure work from anywhere.
-
Microsoft's Zero Trust Adoption
Enforced device compliance, role-based access, and telemetry-driven access decisions across all users.
-
US Federal Zero Trust Strategy
Mandated government agencies to implement Zero Trust principles aligned with NIST standards.
-
CrowdStrike and ZTNA Integration
Combined EDR with Zero Trust Network Access to prevent lateral movement and unauthorized access.
-
Akamai’s Enterprise Access
Delivered application-layer Zero Trust security for distributed, remote, and hybrid workforces.
What Tools and Technologies Support Zero Trust?
Successful Zero Trust implementation depends on a coordinated set of tools that integrate identity, access, monitoring, and analytics capabilities. These tools enforce Zero Trust policies at every control point.
- Identity providers (IdPs) and directory services for user authentication
- Cloud Access Security Brokers (CASBs) for monitoring SaaS application use
- Endpoint Detection and Response (EDR) for validating device health
- Security Information and Event Management (What is SIEM?) systems for analytics
- Software-defined perimeters (SDPs) to isolate sensitive workloads
- Zero Trust network access (ZTNA) platforms for dynamic access control
How Does Zero Trust Apply to Devices and Workloads?
Devices and workloads represent expanding attack vectors. In a Zero Trust architecture:
- Every device is authenticated, authorized, and continuously evaluated for security compliance.
- Non-compliant or unknown devices are quarantined or denied access entirely.
- Workloads in cloud environments are secured via microsegmentation and service-to-service authentication.
- Integration with endpoint detection and response (EDR) tools ensures real-time threat visibility.
What is Zero Trust Architecture Diagram?
A Zero Trust Architecture (ZTA) diagram visually represents the framework where users, devices, applications, and data are treated as untrusted by default, regardless of location. It illustrates components like identity providers, policy enforcement points, segmentation gateways, and monitoring systems, all working together to continuously verify and authorize every access request.
Can an MSSP help implement Zero Trust Security?
Yes, a Managed Security Service Provider (MSSP) can play a critical role in helping organizations implement and manage a Zero Trust Security model. While Zero Trust is a security framework that requires strict identity verification and continuous monitoring, many businesses lack the internal expertise or resources to design and operationalize it. That’s where MSSPs come in